Why Is ISO 27001 Essential for Cybersecurity and Data Protection?


Introduction
As organizations worldwide embrace digital transformation and increasingly rely on interconnected systems to drive business operations, the cybersecurity challenge has reached unprecedented complexity and urgency. Organizations worldwide are seeking comprehensive frameworks to protect their digital assets, maintain customer trust, and comply with regulatory requirements. Among the various cybersecurity standards available, ISO 27001 stands out as the gold standard for information security management systems (ISMS).
ISO 27001 is a strategic framework that transforms how organizations approach cybersecurity. This internationally recognized standard provides a systematic approach to managing sensitive company information, ensuring it remains secure through a comprehensive set of policies, procedures, and controls. As cyber-attacks become increasingly sophisticated and regulatory scrutiny intensifies, understanding why ISO 27001 is crucial for cybersecurity has become essential for business leaders, IT professionals, and security practitioners alike.
The growing importance of ISO 27001 in cybersecurity stems from its holistic approach to information security management. Unlike traditional security measures that focus on specific technologies or threats, ISO 27001 addresses the entire information security ecosystem within an organization. This comprehensive approach ensures that security isn't treated as an afterthought but is embedded into the very fabric of business operations, creating a culture of security awareness and continuous improvement.
The Importance of ISO 27001 in Cybersecurity
ISO 27001 serves as the cornerstone of modern cybersecurity strategy, providing organizations with a structured methodology to identify, assess, and mitigate information security risks. The standard's significance in cybersecurity extends far beyond mere compliance - it fundamentally reshapes how organizations perceive and manage their security posture.
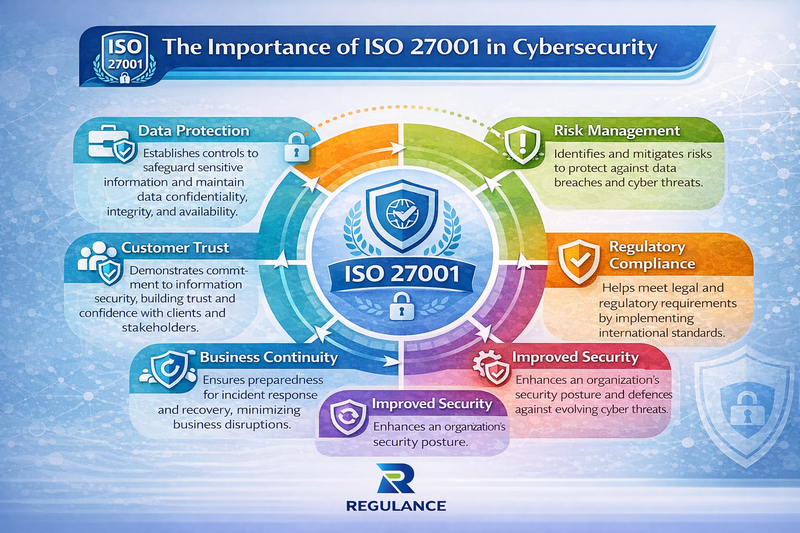
The primary importance of ISO 27001 lies in its risk-based approach to cybersecurity. Rather than implementing a one-size-fits-all security model, the standard requires organizations to conduct thorough risk assessments, identifying specific threats and vulnerabilities that could impact their unique business operations. This tailored approach ensures that security investments are directed toward the most critical areas, maximizing protection while optimizing resource allocation.
Furthermore, ISO 27001 establishes a culture of continuous improvement within organizations. The standard's Plan-Do-Check-Act (PDCA) cycle ensures that cybersecurity measures evolve alongside emerging threats and changing business requirements. This dynamic approach is particularly crucial in today's rapidly evolving threat landscape, where yesterday's security measures may prove inadequate against tomorrow's attack vectors.
The standard also bridges the gap between technical security measures and business objectives. By requiring senior management involvement and establishing clear governance structures, ISO 27001 ensures that cybersecurity becomes a business enabler rather than a hindrance. This alignment between security and business goals is essential for organizations looking to maintain a competitive advantage while protecting their digital assets.
ISO 27001's global recognition adds another layer of importance to its role in cybersecurity. As organizations increasingly operate across international borders and engage with global supply chains, having a universally recognized security framework becomes invaluable. The standard provides a common language for discussing security requirements with partners, customers, and regulatory bodies worldwide.
Understanding the ISO 27001 Certification

ISO 27001 certification represents formal recognition that an organization has implemented and maintains an effective information security management system according to international standards. This certification process involves rigorous evaluation by accredited certification bodies, ensuring that organizations meet the highest standards of information security management.
The certification process begins with gap analysis, where organizations assess their current security posture against ISO 27001 requirements. This initial evaluation helps identify areas requiring improvement and provides a roadmap for implementation. Organizations must then develop comprehensive documentation, including security policies, procedures, and controls that address all aspects of information security management.
The heart of ISO 27001 certification lies in the implementation of 114 security controls organized across 14 domains, including access control, cryptography, physical security, incident management, and business continuity. However, organizations aren't required to implement every control, they must justify their selection based on their specific risk assessment and business requirements.
External auditing forms a critical component of the certification process. Independent auditors evaluate the organization's ISMS implementation, testing both the design and operational effectiveness of security controls. This third-party validation provides assurance to stakeholders that the organization's security measures meet international standards and are operating effectively.
Maintaining ISO 27001 certification requires ongoing commitment and continuous improvement. Organizations must conduct regular internal audits, management reviews, and external surveillance audits to ensure their ISMS remains effective and aligned with evolving threats and business requirements. This continuous monitoring approach ensures that certification represents current security posture rather than a historical snapshot.
The certification also includes a Statement of Applicability (SoA), which documents which controls the organization has implemented and justifies any exclusions. This document serves as a blueprint for the organization's security approach and provides transparency about their security posture to stakeholders and auditors.
Key Benefits of Implementing ISO 27001 Standards
Implementing ISO 27001 standards delivers numerous benefits that extend far beyond basic cybersecurity compliance. These advantages create tangible value for organizations while strengthening their overall security posture and business resilience.
Enhanced Security Posture and Risk Management
The most immediate benefit of ISO 27001 implementation is the significant improvement in overall security posture. The standard's comprehensive approach ensures that organizations address security from multiple angles, including technical, physical, and administrative controls. This holistic coverage reduces security gaps that cybercriminals often exploit, creating a robust defense against various attack vectors.
The risk-based approach inherent in ISO 27001 enables organizations to prioritize their security investments effectively. By identifying and assessing risks specific to their business context, organizations can allocate resources to areas where they'll have the greatest impact on reducing security exposure. This strategic approach to risk management often results in better security outcomes at lower costs compared to ad-hoc security implementations.
Regulatory Compliance and Legal Protection
ISO 27001 implementation significantly eases the burden of regulatory compliance across multiple jurisdictions. Many regulations, including GDPR, HIPAA, and SOX, recognize ISO 27001 as evidence of adequate security controls, reducing audit complexity and demonstrating due diligence in security management. This recognition can provide legal protection in the event of security incidents by demonstrating that the organization followed internationally recognized best practices.
The standard's emphasis on documentation and evidence collection also supports legal and regulatory requirements for maintaining records of security activities. This documentation proves invaluable during regulatory audits, legal proceedings, or insurance claims related to security incidents.
Competitive Advantage and Market Access
ISO 27001 certification provides significant competitive advantages in today's security-conscious marketplace. Many large organizations now require their suppliers and partners to demonstrate adherence to recognized security standards, making certification a prerequisite for business relationships. This requirement is particularly prevalent in sectors such as finance, healthcare, and government contracting.
The certification also opens doors to new markets and customers who prioritize security in their vendor selection processes. Organizations with ISO 27001 certification often find themselves preferred vendors when competing against non-certified alternatives, as the certification provides third-party validation of their security capabilities.
Improved Incident Response and Business Continuity
ISO 27001's requirements for incident management and business continuity planning significantly improve organizational resilience. The standard mandates the development of comprehensive incident response procedures, ensuring that organizations can quickly detect, respond to, and recover from security incidents. This preparedness reduces the impact of security breaches and minimizes business disruption.
The business continuity aspects of ISO 27001 ensure that organizations maintain critical operations even during security incidents or other disruptions. This resilience is increasingly important as organizations become more dependent on digital systems and face growing threats from cybercriminals and natural disasters.
Cost Reduction and Insurance Benefits
While implementing ISO 27001 requires an initial investment, the long-term cost benefits are substantial. The standard's systematic approach to security often reveals inefficiencies in existing security programs, allowing organizations to optimize their security spending. Additionally, the reduced risk of security incidents translates directly to lower potential costs from data breaches, system downtime, and regulatory penalties.
Many cyber insurance providers offer reduced premiums for organizations with ISO 27001 certification, recognizing the lower risk profile associated with certified organizations. Some insurers also provide more favorable coverage terms and faster claim processing for certified organizations.
Challenges in Implementing ISO 27001
Despite its numerous benefits, implementing ISO 27001 presents several challenges that organizations must navigate carefully to achieve successful certification and ongoing compliance. Understanding these challenges helps organizations prepare adequately and develop strategies to overcome potential obstacles.
Resource Requirements and Organizational Commitment
One of the most significant challenges in ISO 27001 implementation is the substantial resource commitment required. Organizations must allocate sufficient personnel, time, and financial resources to develop, implement, and maintain their ISMS. This commitment extends beyond the initial implementation phase, as maintaining certification requires ongoing resource allocation for monitoring, auditing, and continuous improvement activities.
Securing leadership buy-in and organizational commitment poses another challenge, particularly in organizations where security is traditionally viewed as a cost center rather than a business enabler. Leaders must understand that ISO 27001 implementation requires cultural change and long-term commitment, not just technical implementations.
Complexity of Documentation and Process Management
ISO 27001 requires comprehensive documentation of security policies, procedures, and controls. Creating this documentation from scratch can be overwhelming, particularly for organizations with limited experience in formal security management systems. The challenge lies not just in creating the documentation but ensuring it accurately reflects actual business processes and remains current as the organization evolves.
Managing the interrelationships between different processes and controls adds another layer of complexity. Organizations must ensure that their ISMS operates as a coherent system rather than a collection of individual controls, requiring careful coordination and integration across multiple business functions.
Technical Implementation and Integration Challenges
Implementing the technical aspects of ISO 27001 controls often requires significant changes to existing IT infrastructure and security systems. Organizations may need to upgrade or replace legacy systems, implement new security technologies, or reconfigure existing systems to meet the standard's requirements. These technical changes can be disruptive to business operations and may require significant downtime or user training.
Integrating new security controls with existing business processes presents additional challenges. Organizations must ensure that security controls enhance rather than hinder business operations, requiring careful balance between security requirements and operational efficiency.
Skills Gap and Training Requirements
Many organizations struggle with skills gaps when implementing ISO 27001. The standard requires expertise in risk management, security controls implementation, audit procedures, and ongoing management system maintenance. Organizations often find that their existing staff lacks the necessary knowledge and experience to implement and maintain an effective ISMS.
Training existing staff or hiring qualified personnel can be expensive and time-consuming. Organizations must invest in developing internal capabilities while potentially relying on external consultants during the implementation phase.
Ongoing Maintenance and Continuous Improvement
Maintaining ISO 27001 certification requires continuous effort and vigilance. Organizations must conduct regular risk assessments, monitor control effectiveness, manage security incidents, and continuously improve their ISMS. This ongoing commitment can be challenging to maintain, particularly as initial implementation enthusiasm wanes and competing business priorities emerge.
The dynamic nature of cybersecurity threats means that organizations must continuously adapt their security measures to address new risks and vulnerabilities. This requirement for constant evolution can strain resources and challenge organizations to maintain their security posture while managing day-to-day business operations.
Conclusion
ISO 27001 has established itself as the definitive standard for information security management, providing organizations with a comprehensive framework to address the complex cybersecurity challenges of the modern digital era. The standard's importance extends far beyond compliance requirements, fundamentally transforming how organizations approach security risk management and creating sustainable competitive advantages in an increasingly security-conscious marketplace.
The benefits of implementing ISO 27001 standards are substantial and multifaceted, ranging from enhanced security posture and regulatory compliance to improved business resilience and competitive positioning. Organizations that successfully implement and maintain ISO 27001 certification demonstrate their commitment to protecting sensitive information and maintaining the trust of customers, partners, and stakeholders.
While the challenges associated with ISO 27001 implementation are significant, they are not insurmountable. Organizations that approach implementation with adequate preparation, sufficient resources, and strong leadership commitment can successfully navigate these challenges and realize the substantial benefits that certification provides. The emergence of AI-powered automation solutions like Regulance AI further reduces implementation barriers by streamlining compliance processes and reducing the administrative burden associated with maintaining certification.
As cyber threats continue to evolve and regulatory requirements become more stringent, ISO 27001 will remain a critical component of an effective cybersecurity strategy. Organizations that invest in ISO 27001 implementation today position themselves for long-term success in an environment where security excellence is not just desirable but essential for business survival and growth. The standard's emphasis on continuous improvement ensures that certified organizations remain adaptive and resilient in the face of emerging threats, making ISO 27001 certification a strategic investment in organizational future-readiness and cybersecurity excellence.
Explore why ISO 27001 matters for cybersecurity and how it can give your organization a security edge.