Why Continuous Monitoring Matters: A Practical Guide to Stronger Security


Introduction
Cyber threats don't wait for business hours, and neither should your security strategy. With cyberattacks now capable of infiltrating systems in seconds rather than days, organizations worldwide are discovering that traditional, snapshot-based security assessments leave dangerous gaps in their defense mechanisms. The shift toward real-time threat detection and continuous security monitoring has become not just a competitive advantage, but a survival necessity in our interconnected digital ecosystem.
Modern enterprises operating across cloud infrastructures, remote workforces, and multi-platform environments face an unprecedented challenge: maintaining comprehensive security visibility while scaling their digital operations. Regulatory frameworks now mandate continuous compliance monitoring, while sophisticated threat actors exploit even the smallest windows of vulnerability. This paradigm shift has elevated continuous monitoring from an optional security enhancement to a fundamental pillar of enterprise risk management.
This in-depth guide examines how continuous monitoring revolutionizes cybersecurity operations, strengthens compliance frameworks, and provides organizations with the real-time insights needed to stay ahead of evolving threats. We'll explore proven implementation strategies, industry best practices, and the transformative impact that 24/7 security monitoring can have on your organization's overall security posture and business resilience.
What is Continuous Monitoring?
Continuous monitoring represents a paradigm shift from traditional point-in-time security assessments to an ongoing, automated process of observing, analyzing, and responding to changes in an organization's risk profile. At its core, continuous monitoring involves the real-time collection and analysis of data from various sources within an IT environment to provide stakeholders with up-to-date information about security status, compliance posture, and operational health.
This approach goes beyond simple log collection or basic monitoring tools. It encompasses a holistic view of an organization's entire technology ecosystem, including network infrastructure, applications, databases, user activities, and third-party integrations. The goal is to create a comprehensive, real-time picture of the organization's security landscape that enables proactive decision-making and rapid response to emerging threats.
The National Institute of Standards and Technology (NIST) defines continuous monitoring as "maintaining ongoing awareness of information security, vulnerabilities, and threats to support organizational risk management decisions." This definition highlights the strategic nature of continuous monitoring, positioning it as a fundamental component of enterprise risk management rather than merely a technical security control.
Continuous monitoring involves several key characteristics that distinguish it from traditional monitoring approaches:
Real-time Data Collection: Information is gathered continuously from multiple sources across the IT environment, providing an up-to-the-minute view of system status and security posture.
Automated Analysis: Advanced analytics and machine learning algorithms process vast amounts of data to identify patterns, anomalies, and potential security issues without human intervention.
Risk-based Prioritization: Findings are contextualized and prioritized based on their potential impact on business operations and compliance requirements.
Actionable Insights: The monitoring system provides clear, actionable recommendations that security teams can implement to address identified issues.
What is Continuous Monitoring in Cyber Security?
In the cybersecurity context, continuous monitoring takes on additional layers of complexity and importance. Cybersecurity continuous monitoring focuses specifically on identifying, assessing, and mitigating security threats and vulnerabilities in real-time. This specialized application of continuous monitoring has become indispensable as cyber threats have grown more sophisticated and persistent.
Cybersecurity continuous monitoring encompasses several critical areas:
Threat Detection and Response: Modern monitoring systems use advanced threat intelligence, behavioral analytics, and machine learning to identify potential security incidents as they occur. This includes detecting unauthorized access attempts, malware infections, data exfiltration, and insider threats.
Vulnerability Management: Rather than relying on quarterly or annual vulnerability assessments, continuous monitoring provides ongoing identification of security weaknesses in systems, applications, and configurations. This enables organizations to address vulnerabilities before they can be exploited by attackers.
Compliance Monitoring: Many regulatory frameworks require continuous monitoring of security controls and compliance status. This includes tracking changes to system configurations, monitoring user access and privileges, and ensuring that security policies are consistently enforced.
Asset Discovery and Inventory: Continuous monitoring helps organizations maintain accurate, up-to-date inventories of their IT assets, including newly deployed systems, changes to existing infrastructure, and potential shadow IT resources.
The cybersecurity aspect of continuous monitoring is particularly important because cyber threats don't follow business hours or scheduled maintenance windows. Attackers often exploit periods when organizations have reduced monitoring capabilities, such as weekends, holidays, or during system maintenance. Continuous monitoring ensures that security teams maintain visibility and response capabilities 24/7/365.
Furthermore, the increasing sophistication of Advanced Persistent Threats (APTs) and state-sponsored attacks requires monitoring systems that can detect subtle, long-term intrusions that might go unnoticed by traditional security tools. These threats often involve multiple stages of compromise, reconnaissance, and lateral movement that can only be detected through comprehensive, continuous analysis of network and system activities.
Benefits of Continuous Monitoring
The implementation of continuous monitoring delivers numerous benefits that extend far beyond basic security improvements. These advantages impact various aspects of business operations, from risk management to operational efficiency.

Enhanced Security Posture: Perhaps the most obvious benefit, continuous monitoring significantly improves an organization's ability to detect and respond to security threats. By providing real-time visibility into the IT environment, security teams can identify and neutralize threats before they cause significant damage. This proactive approach reduces the average time to detection and response, minimizing the potential impact of security incidents.
Improved Compliance Management: Regulatory compliance is a major driver for continuous monitoring adoption. Many frameworks, including SOX, HIPAA, PCI DSS, and GDPR, require organizations to demonstrate ongoing compliance with security and privacy requirements. Continuous monitoring automates much of the compliance reporting process, providing auditors with real-time evidence of control effectiveness and reducing the burden on internal compliance teams.
Cost Reduction: While implementing continuous monitoring requires initial investment, it typically results in significant cost savings over time. Automated monitoring reduces the need for manual security assessments, minimizes the impact of security incidents through faster detection and response, and helps avoid costly regulatory fines and penalties.
Better Risk Management: Continuous monitoring provides organizations with the data needed to make informed risk management decisions. By understanding their current risk posture in real-time, leaders can prioritize security investments, allocate resources more effectively, and make strategic decisions about technology adoption and business expansion.
Operational Efficiency: Modern continuous monitoring platforms integrate with existing security tools and workflows, reducing the administrative overhead associated with security management. Automated reporting, alerting, and remediation capabilities free up security teams to focus on strategic initiatives rather than routine monitoring tasks.
Faster Incident Response: When security incidents do occur, continuous monitoring provides the context and forensic data needed to understand the scope and impact of the incident. This enables security teams to respond more effectively and recover more quickly from security breaches.
Business Continuity: By identifying potential issues before they impact business operations, continuous monitoring helps ensure system availability and performance. This is particularly important for organizations that depend on digital services for revenue generation or customer service.
Components of Continuous Monitoring
Effective continuous monitoring systems consist of several interconnected components that work together to provide comprehensive visibility and control over the IT environment. Understanding these components is essential for organizations planning to implement or improve their monitoring capabilities.
Data Collection Infrastructure: The foundation of any continuous monitoring system is its ability to collect data from diverse sources across the IT environment. This includes network devices, servers, applications, databases, security tools, and user endpoints. Modern monitoring platforms use APIs, log aggregation tools, network probes, and agent-based collectors to gather information from these various sources.
Data Normalization and Correlation: Raw data from different sources often comes in various formats and structures. The monitoring system must normalize this data into a consistent format and correlate events across different sources to identify relationships and patterns. This component is crucial for reducing false positives and providing meaningful insights.
Analytics and Intelligence Engine: The heart of a continuous monitoring system is its analytics capability. This component uses various techniques, including rule-based analysis, statistical modeling, machine learning, and artificial intelligence, to identify anomalies, threats, and compliance issues. Advanced systems can adapt and learn from new data, improving their accuracy over time.
Risk Assessment and Scoring: Continuous monitoring systems must be able to assess the risk level associated with different findings and prioritize them accordingly. This involves understanding the business context, asset criticality, threat landscape, and regulatory requirements to provide meaningful risk scores and recommendations.
Reporting and Visualization: Effective communication of monitoring results is essential for driving action and decision-making. Modern platforms provide dashboards, reports, and visualizations that present complex data in understandable formats for different audiences, from technical teams to executive leadership.
Integration and Orchestration: Continuous monitoring systems must integrate with existing security tools, IT service management platforms, and business applications. This component enables automated response actions, ticket creation, and workflow orchestration based on monitoring findings.
Configuration and Policy Management: The system must maintain and enforce configuration standards and security policies across the IT environment. This includes monitoring for configuration drift, unauthorized changes, and policy violations.
Audit Trail and Evidence Collection: For compliance purposes, continuous monitoring systems must maintain comprehensive audit trails and collect evidence of control effectiveness. This component ensures that organizations can demonstrate compliance to auditors and regulators.
The Role of Automation in Continuous Monitoring
Automation is an absolute necessity. The scale and complexity of modern IT environments make manual monitoring approaches impractical and ineffective. Automation enables organizations to monitor thousands of systems, process millions of events, and respond to threats at machine speed.
Automated Data Collection: Modern IT environments generate enormous volumes of log data, performance metrics, and security events. Automated collection systems can gather this data from diverse sources without human intervention, ensuring consistent and comprehensive coverage. This includes automated discovery of new assets and services as they come online.
Intelligent Analysis and Pattern Recognition: Machine learning and AI algorithms can analyze vast datasets to identify patterns and anomalies that would be impossible for human analysts to detect. These systems can learn normal behavior patterns and flag deviations that may indicate security threats or compliance issues.
Automated Response and Remediation: When monitoring systems detect issues, automated response capabilities can take immediate action to contain threats, isolate compromised systems, or remediate configuration problems. This rapid response capability is essential for minimizing the impact of security incidents.
Policy Enforcement and Compliance Checking: Automated systems can continuously verify that systems and configurations comply with established policies and regulatory requirements. This includes automatically flagging policy violations and, in some cases, automatically correcting non-compliant configurations.
Reporting and Communication: Automated reporting ensures that stakeholders receive timely, accurate information about the organization's security posture and compliance status. This includes generating executive dashboards, compliance reports, and incident notifications without manual intervention.
However, automation in continuous monitoring must be implemented thoughtfully. Over-automation can lead to alert fatigue, where security teams become overwhelmed by false positives and begin ignoring alerts. The key is to implement intelligent automation that provides high-quality, actionable insights while maintaining human oversight for critical decisions.
Best Practices of Continuous Monitoring
Implementing effective continuous monitoring requires careful planning, proper execution, and ongoing optimization. Organizations that follow established best practices are more likely to achieve their monitoring objectives and realize the full benefits of their investment.
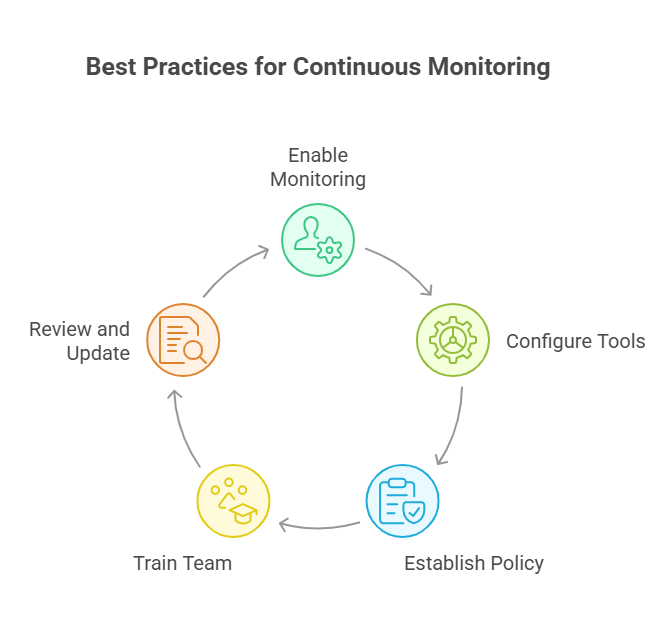
Define Clear Objectives and Requirements: Before implementing continuous monitoring, organizations must clearly define what they want to achieve. This includes identifying specific compliance requirements, security objectives, and business goals that the monitoring system should support. Clear objectives help guide technology selection, implementation planning, and success measurement.
Adopt a Risk-Based Approach: Not all assets, systems, and data are equally important to the organization. Effective continuous monitoring focuses resources on the most critical assets and highest-risk areas. This risk-based prioritization ensures that monitoring efforts align with business priorities and regulatory requirements.
Implement Comprehensive Asset Management: Continuous monitoring is only effective if organizations have accurate visibility into their IT assets. This requires implementing robust asset discovery and inventory management processes that can identify and track all systems, applications, and data across the environment.
Establish Baseline Configurations: To identify deviations and anomalies, monitoring systems need to understand what "normal" looks like. Organizations should establish and maintain baseline configurations for systems, applications, and security controls. These baselines serve as reference points for detecting changes and potential issues.
Integrate with Existing Tools and Processes: Continuous monitoring should complement and enhance existing security and IT management processes rather than replacing them entirely. This requires careful integration with security information and event management (SIEM) systems, vulnerability management tools, configuration management databases, and incident response processes.
Focus on Actionable Intelligence: The goal of continuous monitoring is to drive action, not just collect data. Organizations should tune their monitoring systems to provide high-quality, actionable intelligence that security teams can act upon. This means reducing false positives, providing context for alerts, and offering clear remediation guidance.
Implement Proper Change Management: Changes to IT systems and configurations can impact security posture and compliance status. Effective continuous monitoring includes robust change management processes that track, approve, and monitor all changes to critical systems and security controls.
Maintain Skilled Personnel: While automation plays a crucial role in continuous monitoring, human expertise remains essential. Organizations must invest in training and retaining skilled security professionals who can interpret monitoring results, make strategic decisions, and respond to complex security incidents.
Regular Review and Optimization: Continuous monitoring systems require ongoing maintenance and optimization to remain effective. This includes regularly reviewing and updating monitoring rules, refining alert thresholds, and adapting to changes in the threat landscape and business environment.
Ensure Data Quality and Integrity: The effectiveness of continuous monitoring depends heavily on the quality and integrity of the data being collected and analyzed. Organizations must implement controls to ensure data accuracy, completeness, and protection from tampering or corruption.
How Does Regulance AI Help in Achieving Continuous Monitoring?
Regulance AI represents the next generation of continuous monitoring platforms, leveraging advanced artificial intelligence and machine learning technologies to provide comprehensive, intelligent monitoring capabilities. The platform addresses many of the challenges organizations face when implementing traditional monitoring solutions.
Automated Compliance Management: The platform continuously monitors compliance with various regulatory frameworks, including SOX, HIPAA, PCI DSS, GDPR, and industry-specific regulations. Regulance AI automatically maps security controls to regulatory requirements, tracks compliance status in real-time, and generates audit-ready reports that demonstrate ongoing compliance.
Integration Capabilities: The platform integrates seamlessly with existing security tools, IT management systems, and business applications through extensive API support and pre-built connectors. This integration capability ensures that organizations can leverage their existing technology investments while gaining the benefits of advanced AI-powered monitoring.
Frequently Asked Questions (FAQs)
What is the difference between continuous monitoring and traditional monitoring?
Traditional monitoring typically involves periodic assessments, scheduled scans, and reactive responses to known threats. Continuous monitoring, on the other hand, provides real-time, ongoing observation and analysis of the IT environment. It uses automation and AI to detect anomalies, threats, and compliance issues as they occur, enabling proactive response rather than reactive remediation.
How much does continuous monitoring cost?
The cost of continuous monitoring varies significantly based on factors such as organizational size, complexity of the IT environment, regulatory requirements, and chosen solution architecture. While there are upfront implementation costs, most organizations find that continuous monitoring provides positive ROI through reduced incident response costs, avoided regulatory fines, and improved operational efficiency.
Can continuous monitoring replace traditional security assessments?
Continuous monitoring complements rather than replaces traditional security assessments. While continuous monitoring provides ongoing visibility and real-time threat detection, periodic comprehensive assessments remain valuable for strategic planning, compliance validation, and thorough security architecture reviews.
What types of data does continuous monitoring collect?
Continuous monitoring systems collect various types of data, including network traffic logs, system event logs, application logs, user activity data, configuration information, vulnerability scan results, and threat intelligence feeds. The specific data collected depends on the organization's requirements and the capabilities of the monitoring platform.
How does continuous monitoring impact network performance?
Modern continuous monitoring solutions are designed to minimize impact on network and system performance. They use efficient data collection methods, intelligent sampling techniques, and optimized network protocols to gather necessary information without significantly affecting normal operations.
Is continuous monitoring suitable for small businesses?
Yes, continuous monitoring solutions are available for organizations of all sizes. Cloud-based monitoring services have made advanced monitoring capabilities accessible to small and medium-sized businesses that may not have the resources to implement on-premises solutions.
How long does it take to implement continuous monitoring?
Implementation time varies based on organizational complexity and requirements. Basic continuous monitoring capabilities can often be deployed within weeks, while comprehensive enterprise implementations may take several months. The key is to start with critical assets and high-risk areas, then expand coverage over time.
What skills are required to manage continuous monitoring systems?
Effective continuous monitoring requires a combination of technical and analytical skills, including cybersecurity expertise, data analysis capabilities, and knowledge of regulatory requirements. Many organizations choose to work with managed security service providers or invest in training for their existing staff.
Conclusion
Continuous monitoring has evolved from an advanced security technique to a fundamental business requirement in today's threat landscape. Organizations that embrace continuous monitoring gain significant advantages in terms of security posture, compliance management, and operational efficiency. The ability to detect and respond to threats in real-time, maintain ongoing compliance with regulatory requirements, and make data-driven security decisions provides a substantial competitive advantage.
The key to successful continuous monitoring implementation lies in understanding that it's about transforming how organizations approach risk management and security operations. This transformation requires careful planning, proper tool selection, skilled personnel, and ongoing optimization to achieve desired outcomes.
As cyber threats continue to evolve and regulatory requirements become more stringent, the importance of continuous monitoring will only increase. Organizations that invest in comprehensive continuous monitoring capabilities today will be better positioned to address future challenges and opportunities in the digital landscape.
The integration of artificial intelligence and machine learning technologies, exemplified by platforms like Regulance AI, represents the future of continuous monitoring. These advanced capabilities enable organizations to move beyond simple monitoring and alerting to intelligent, proactive security management that adapts to changing conditions and emerging threats.
For organizations considering continuous monitoring implementation, the message is clear: the question is not whether to implement continuous monitoring, but how quickly and effectively it can be done. The organizations that act decisively to implement robust continuous monitoring capabilities will be the ones that thrive in an increasingly complex and dangerous digital environment.
By following the best practices outlined in this guide and selecting appropriate technology solutions, organizations can build continuous monitoring programs that not only meet their immediate security and compliance needs but also provide a foundation for long-term success in the digital age. The investment in continuous monitoring is an investment in the future resilience and competitiveness of the organization.
Take the complexity out of continuous monitoring with Regulance AI; automate compliance, detect threats in real time, and keep your business secure.