What is Vulnerability Scanning? A Complete Guide To Cybersecurity Defense


Introduction
Across the current interlinked business ecosystem, cybersecurity threats are becoming increasingly sophisticated and frequent. Organizations worldwide face an average of 1,248 cyberattacks per week, making proactive security measures more critical than ever. Among the most effective tools in a cybersecurity professional's arsenal is vulnerability scanning, a cornerstone practice that helps identify security weaknesses before malicious actors can exploit them.
This comprehensive guide will walk you through everything you need to know about vulnerability scanning, from basic concepts to advanced implementation strategies. Whether you're a cybersecurity novice or an experienced professional looking to refine your approach, understanding vulnerability scanning is essential for building robust defense mechanisms in our interconnected world.
What is Vulnerability Scanning?
Vulnerability scanning is an automated cybersecurity process that systematically examines computer systems, networks, applications, and infrastructure to identify security vulnerabilities, misconfigurations, and potential entry points that could be exploited by cybercriminals. Think of it as a comprehensive health checkup for your digital environment, it proactively searches for weaknesses that could compromise your organization's security posture.
Vulnerability scanning involves using specialized software tools to probe various components of an IT infrastructure. These tools compare the discovered system characteristics against extensive databases of known vulnerabilities, such as the Common Vulnerabilities and Exposures (CVE) database, which catalogs publicly disclosed cybersecurity flaws.
The scanning process doesn't just identify vulnerabilities; it also prioritizes them based on severity levels, potential impact, and exploitability. This prioritization is crucial because most organizations discover hundreds or even thousands of vulnerabilities during scans, making it impossible to address everything simultaneously. Modern vulnerability scanners use scoring systems like the Common Vulnerability Scoring System (CVSS) to help security teams focus their remediation efforts on the most critical issues first.
What makes vulnerability scanning particularly valuable in today's cybersecurity landscape is its ability to provide continuous visibility into an organization's security posture. As new vulnerabilities are discovered daily and systems constantly evolve, regular scanning ensures that security teams maintain an up-to-date understanding of their risk exposure.
Vulnerability Scanning vs Penetration Testing
While vulnerability scanning and penetration testing are both essential components of a comprehensive cybersecurity strategy, they serve distinctly different purposes and employ different methodologies. Understanding these differences is crucial for implementing an effective security program.
Vulnerability Scanning: The Automated Approach
Vulnerability scanning is primarily an automated process that quickly identifies potential security weaknesses across large-scale environments. It's like having a security guard who walks through your building with a checklist, systematically noting every unlocked door, broken window, or faulty alarm system. The process is fast, comprehensive, and can be performed regularly without significant resource investment.
Vulnerability scans typically run continuously or on scheduled intervals, providing ongoing visibility into your security posture. They excel at discovering known vulnerabilities, missing patches, misconfigurations, and compliance violations. However, they generally don't attempt to exploit the vulnerabilities they find—they simply report their existence and potential risk level.
Penetration Testing: The Human-Driven Simulation
Penetration testing, on the other hand, is a human-driven process where cybersecurity experts actively attempt to exploit discovered vulnerabilities, much like a professional burglar testing your actual defenses. Penetration testers don't just identify that a door is unlocked; they walk through it, explore what's inside, and determine what valuable assets could be compromised.
This approach provides deeper insights into the real-world impact of security vulnerabilities. Penetration tests can uncover complex attack chains, business logic flaws, and sophisticated vulnerabilities that automated tools might miss. However, they're more time-consuming, expensive, and typically performed quarterly or annually rather than continuously.
The Complementary Relationship
These two approaches work best when used together. Vulnerability scanning provides the broad, continuous coverage needed to maintain baseline security awareness, while penetration testing offers the deep, realistic assessment of actual risk. Many organizations use vulnerability scanning results to guide their penetration testing efforts, focusing manual testing on the most critical vulnerabilities discovered through automated scans.
Vulnerability Scanning vs Vulnerability Management
Another common source of confusion in cybersecurity is the distinction between vulnerability scanning and vulnerability management. While closely related, these represent different scopes of activity within an organization's security program.
Vulnerability Scanning: The Discovery Engine
Vulnerability scanning is essentially the discovery and assessment component of cybersecurity. It's the process of finding and cataloging vulnerabilities, but it stops there. Think of it as the diagnostic phase of medical care—you're identifying what's wrong, but you haven't yet treated the problem.
Vulnerability scanners excel at providing comprehensive inventories of security weaknesses, complete with severity ratings, affected systems, and remediation guidance. They answer the critical question: "What vulnerabilities exist in our environment?"
Vulnerability Management: The Complete Lifecycle
Vulnerability management, however, encompasses the entire lifecycle of dealing with security vulnerabilities. It includes vulnerability scanning as a foundational component but extends far beyond discovery to include prioritization, remediation planning, patch deployment, verification, and reporting.
A mature vulnerability management program involves establishing policies for scan frequency, defining acceptable risk levels, creating workflows for remediation activities, tracking metrics and key performance indicators, and ensuring compliance with regulatory requirements. It answers the broader question: "How do we systematically address security vulnerabilities across our organization?"
The Strategic Integration
Effective vulnerability management requires more than just running scans. It demands integration with change management processes, patch management systems, asset management databases, and risk management frameworks. Organizations with mature vulnerability management programs typically see significantly better security outcomes because they've moved beyond simply knowing about vulnerabilities to systematically addressing them.
How Does Vulnerability Scanning Work?
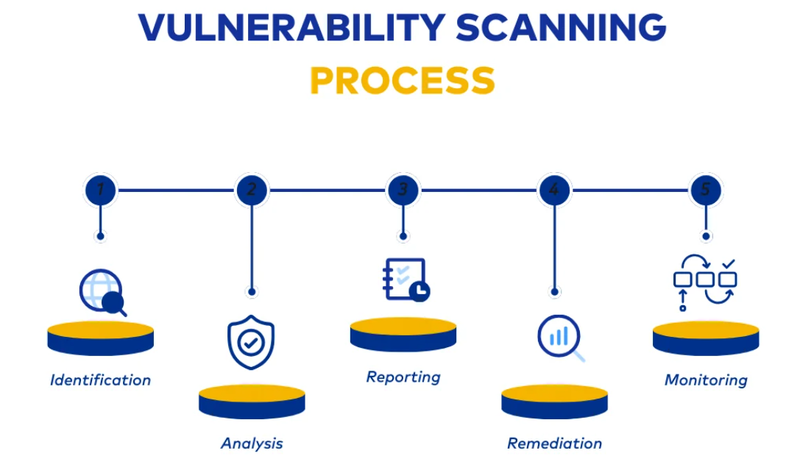
Understanding the mechanics of vulnerability scanning helps organizations implement more effective scanning strategies and interpret results more accurately. The process involves several sophisticated steps that work together to provide comprehensive security assessments.
Phase 1: Discovery and Asset Identification
The scanning lnerability scanner identifies active systems, services, and applications within the defined scope. This phase uses various techniques including ping sweeps, port scans, and service enumeration to create a comprehensive inventory of potential targets.
Modern scanners can identify a wide range of assets, from traditional servers and workstations to IoT devices, cloud instances, mobile devices, and network infrastructure components. This discovery phase is crucial because you can't secure what you don't know exists.
Phase 2: Service and Application Fingerprinting
Once systems are identified, the scanner performs detailed fingerprinting to determine exactly what services, applications, and operating systems are running. This involves analyzing service banners, application responses, and system behaviors to create detailed profiles of each discovered asset.
The accuracy of this fingerprinting directly impacts the quality of vulnerability assessment, as the scanner needs to know precisely what software is running to determine which vulnerabilities might apply.
Phase 3: Vulnerability Detection and Assessment
The core scanning phase involves testing discovered systems against extensive databases of known vulnerabilities. Modern scanners maintain databases containing hundreds of thousands of vulnerability signatures, including information from sources like the National Vulnerability Database, vendor security advisories, and proprietary research.
The scanner attempts to identify vulnerable software versions, dangerous configurations, weak authentication mechanisms, and other security issues. Advanced scanners can also detect zero-day vulnerabilities through behavioral analysis and anomaly detection.
Phase 4: Risk Analysis and Prioritization
Raw vulnerability data isn't particularly useful without context and prioritization. Modern scanners analyze discovered vulnerabilities considering factors like exploitability, potential impact, asset criticality, and environmental factors. This analysis produces risk scores and prioritized recommendations for remediation.
Phase 5: Reporting and Integration
Finally, the scanner generates comprehensive reports tailored to different audiences, from technical details for system administrators to executive summaries for management. Many modern scanners integrate with other security tools, automatically creating tickets in IT service management systems or feeding data into security information and event management (SIEM) platforms.
Benefits of Vulnerability Scanning
Implementing regular vulnerability scanning provides numerous advantages that extend far beyond basic security improvements. These benefits contribute to overall organizational resilience and business continuity.
Proactive Threat Identification
The primary benefit of vulnerability scanning is its ability to identify security weaknesses before they're exploited by malicious actors. This proactive approach is significantly more cost-effective than reactive incident response. Studies show that the average cost of a data breach is $4.45 million, while implementing comprehensive vulnerability management programs costs a fraction of that amount.
Compliance and Regulatory Adherence
Many regulatory frameworks, including PCI DSS, HIPAA, SOX, and GDPR, require regular vulnerability assessments. Automated scanning helps organizations maintain compliance by providing the documentation and evidence required by auditors and regulators. This systematic approach reduces the risk of compliance violations and associated penalties.
Asset Visibility and Inventory Management
Vulnerability scans provide valuable insights into an organization's IT infrastructure, often discovering unauthorized or forgotten systems. This "shadow IT" discovery is crucial for maintaining accurate asset inventories and ensuring comprehensive security coverage.
Risk Quantification and Business Communication
Modern vulnerability scanners provide risk metrics that help translate technical vulnerabilities into business language. This capability enables more effective communication with executives and stakeholders about cybersecurity risks and the business value of security investments.
Improved Incident Response Capabilities
Regular vulnerability scanning enhances incident response capabilities by providing detailed knowledge of system configurations and potential attack vectors. When security incidents occur, this information helps response teams understand how attackers might have gained access and what systems might be affected.
Cost-Effective Security Operations
Automated vulnerability scanning scales efficiently across large environments, providing comprehensive security assessments without proportional increases in staff requirements. This efficiency allows security teams to focus human expertise on high-value activities like threat hunting and incident response rather than routine vulnerability discovery.
Types of Vulnerability Scans
Different scanning approaches serve various purposes and environments. Understanding these types helps organizations select the most appropriate scanning strategies for their specific needs and constraints.
Network-Based Vulnerability Scans
Network-based scans examine systems from an external perspective, identifying vulnerabilities in network services, open ports, and externally accessible applications. These scans simulate the view that external attackers would have of your infrastructure.
Network scans are excellent for identifying perimeter security issues, discovering unauthorized services, and assessing the security of internet-facing systems. They're typically non-intrusive and can be performed without requiring access to target systems.
Host-Based Vulnerability Scans
Host-based scans require agent software or credentials to examine systems from the inside, providing detailed insights into local configurations, installed software, and system-level vulnerabilities. This approach offers much more comprehensive assessment capabilities than network-based scanning alone.
These scans can identify missing patches, dangerous configurations, weak passwords, and compliance violations that might not be visible from network perspectives. They're essential for comprehensive security assessments but require more coordination and access management.
Application Vulnerability Scans
Specialized application scans focus on web applications, databases, and custom software, identifying vulnerabilities like SQL injection, cross-site scripting, and authentication bypass issues. These scans are crucial given that application vulnerabilities account for a significant percentage of successful cyberattacks.
Modern application scanners can test both static code and running applications, providing comprehensive coverage of application security risks. They're particularly important for organizations with significant web application footprints.
Authenticated vs. Unauthenticated Scans
Authenticated scans use provided credentials to log into systems and perform detailed internal assessments, while unauthenticated scans assess systems from an external perspective without special access privileges.
Authenticated scans provide more comprehensive results and can identify issues that aren't visible externally. However, they require careful credential management and may have greater impact on system performance.
Internal vs. External Scans
Internal scans assess systems from within the organization's network perimeter, identifying vulnerabilities that might be exploited by insider threats or attackers who have already gained network access. External scans examine systems from internet perspectives, focusing on perimeter security and internet-facing services.
Both perspectives are important for comprehensive security assessment, as they reveal different types of vulnerabilities and attack vectors.
Vulnerability Scanning Tools
The vulnerability scanning tool landscape includes numerous options ranging from open-source solutions to enterprise-grade commercial platforms. Selecting the right tools depends on organizational requirements, budget constraints, and technical capabilities.
Commercial Enterprise Solutions
Leading commercial vulnerability scanners like Tenable Nessus, Qualys VMDR, and Rapid7 InsightVM offer comprehensive features including extensive vulnerability databases, advanced reporting capabilities, integration options, and enterprise-grade scalability. These solutions typically provide the most comprehensive coverage and best support for large-scale environments.
Enterprise tools often include features like asset discovery, compliance reporting, patch management integration, and advanced analytics. They're designed for organizations that need robust, reliable scanning capabilities with professional support.
Open-Source Alternatives
Open-source tools like OpenVAS, Nuclei, and Nmap provide cost-effective options for organizations with limited budgets or specific technical requirements. While these tools may require more technical expertise to implement and maintain, they offer flexibility and customization options that commercial solutions might not provide.
Open-source scanners are particularly valuable for organizations with specialized environments or those that need to customize scanning capabilities for specific use cases.
Cloud-Native Scanning Solutions
Cloud-focused scanners like AWS Inspector, Azure Security Center, and Google Cloud Security Command Center provide integrated vulnerability assessment capabilities specifically designed for cloud environments. These tools understand cloud-specific configurations and can assess both infrastructure and application vulnerabilities in cloud deployments.
Specialized Scanning Tools
Certain environments require specialized scanning approaches. Web application scanners like OWASP ZAP and Burp Suite focus specifically on application security testing. Container scanners like Twistlock and Aqua Security address the unique challenges of containerized environments.
Tool Selection Considerations
When selecting vulnerability scanning tools, organizations should consider factors like coverage breadth, accuracy levels, integration capabilities, reporting features, scalability requirements, and total cost of ownership. The best tool for any organization depends on their specific environment, requirements, and constraints.
Conclusion
Vulnerability scanning represents a fundamental pillar of modern cybersecurity strategy, providing organizations with the visibility and insights necessary to maintain strong security postures in an increasingly complex threat landscape. As cyber threats continue to evolve and multiply, the importance of systematic vulnerability identification and management only grows more critical.
The key to successful vulnerability scanning lies not just in running scans, but in implementing comprehensive programs that integrate scanning with broader vulnerability management processes. Organizations that treat vulnerability scanning as part of a holistic security strategy rather than a standalone activity, consistently achieve better security outcomes and demonstrate greater resilience against cyber threats.
Effective vulnerability scanning requires understanding the different types of scans, selecting appropriate tools, and implementing processes that turn vulnerability discovery into actionable security improvements. The investment in robust vulnerability scanning capabilities pays dividends through reduced risk exposure, improved compliance posture, and enhanced organizational security maturity.
Vulnerability scanning will continue evolving with advances in artificial intelligence, machine learning, and automation. However, the fundamental principle remains unchanged: you cannot effectively protect what you do not understand. Vulnerability scanning provides that understanding, making it an indispensable component of any serious cybersecurity program.
Boost your cybersecurity today! Discover how Regulance AI makes vulnerability scanning smarter, faster, and more effective.