What is Security Program Management: A Comprehensive Guide to Building Robust Security Frameworks


Introduction
In an era where business risks multiply faster than ever before , organizations face an unprecedented array of cybersecurity threats that can devastate operations, compromise sensitive data, and destroy years of carefully built reputation. From sophisticated ransomware attacks to data breaches that expose millions of customer records, the stakes have never been higher for businesses of all sizes. This reality has given rise to a critical discipline that serves as the backbone of organizational defense: Security Program Management.
Security Program Management represents far more than just installing firewalls and antivirus software. It's a comprehensive, strategic approach that weaves security considerations into the very fabric of an organization's operations, culture, and decision-making processes. This discipline requires a unique blend of technical expertise, business acumen, and leadership skills to create, implement, and continuously evolve security frameworks that protect against both current threats and emerging risks.
The complexity of modern business environments, with their hybrid cloud infrastructures, remote workforces, Internet of Things devices, and third-party integrations, demand a sophisticated approach to security management. Organizations can no longer rely on ad-hoc security measures or reactive responses to threats. Instead, they need structured, proactive programs that anticipate risks, implement preventive measures, and ensure rapid response and recovery when incidents occur.
Security Program Management bridges the gap between technical security implementations and business objectives, ensuring that security investments align with organizational goals while maintaining operational efficiency. It encompasses everything from risk assessment and policy development to incident response planning and compliance management, all orchestrated through a strategic lens that considers both immediate needs and long-term organizational sustainability.
What is a Security Program?
A security program is a comprehensive framework of policies, procedures, technologies, and practices designed to protect an organization's assets, information, and operations from various threats and risks. Unlike isolated security measures, a security program takes a holistic approach that integrates multiple security disciplines into a cohesive strategy aligned with business objectives.
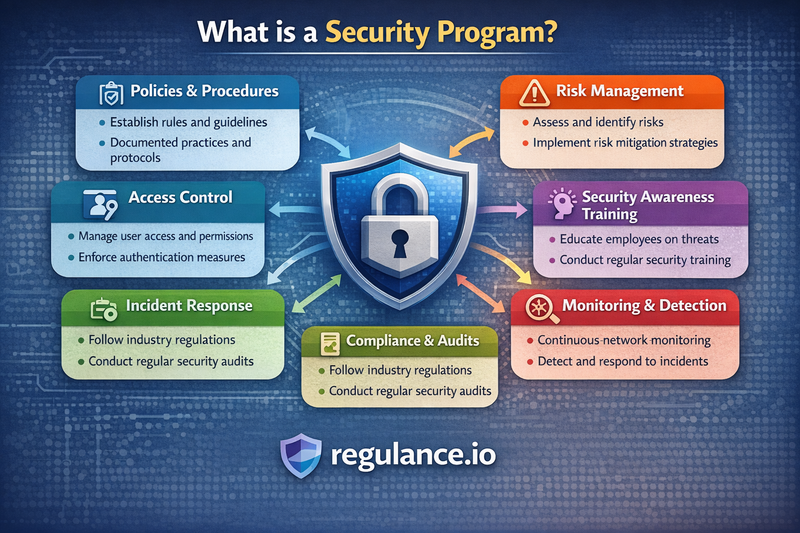
A security program serves as the organizational blueprint for managing cybersecurity risks throughout the enterprise. It establishes the foundation for consistent security practices, defines roles and responsibilities, and creates accountability mechanisms that ensure security considerations are embedded in all business processes.
Security programs typically encompass several key components that work together to create a robust defense posture. Information security policies form the cornerstone, establishing the rules and guidelines that govern how data and systems should be protected. These policies cascade down into specific procedures and standards that provide detailed instructions for implementation.
Risk management represents another critical component, involving the systematic identification, assessment, and mitigation of security risks that could impact organizational operations. This includes both technical risks, such as vulnerabilities in software systems, and operational risks, such as insider threats or supply chain compromises.
Access control mechanisms ensure that only authorized individuals can access sensitive information and critical systems. This involves identity management systems, authentication protocols, and authorization frameworks that govern user permissions and system access rights.
Incident response capabilities prepare organizations to detect, respond to, and recover from security incidents effectively. This includes establishing incident response teams, developing response procedures, and creating communication protocols that enable rapid coordination during crisis situations.
Training and awareness programs ensure that employees understand their security responsibilities and can recognize potential threats. Since human error remains one of the leading causes of security incidents, these programs play a crucial role in strengthening the overall security posture.
Compliance management ensures that the organization meets all relevant regulatory requirements and industry standards. This is particularly important for organizations operating in regulated industries such as healthcare, finance, or government contracting.
Qualities of a Good Security Program
Effective security programs share several fundamental qualities that distinguish them from mediocre or failing initiatives. Understanding these characteristics is essential for organizations seeking to build robust security frameworks that deliver tangible value.
Alignment with Business Objectives stands as perhaps the most critical quality of successful security programs. Rather than existing as an isolated function, effective programs integrate seamlessly with business strategy, supporting organizational goals while managing risks. This alignment ensures that security investments receive adequate support and resources while avoiding unnecessary friction with business operations.
Risk-Based Approach characterizes mature security programs that prioritize their efforts based on actual risk levels rather than generic best practices. These programs conduct thorough risk assessments to identify the most critical threats and vulnerabilities, then allocate resources accordingly. This approach ensures that limited security budgets generate maximum protective value.
Comprehensive Coverage ensures that security programs address all relevant aspects of organizational security, from physical security and personnel screening to cybersecurity and business continuity. Effective programs recognize that security vulnerabilities in any area can compromise the entire organization.
Continuous Improvement drives successful security programs to evolve constantly in response to changing threats, new technologies, and business developments. These programs establish feedback mechanisms, conduct regular assessments, and update their approaches based on lessons learned and emerging best practices.
Clear Governance Structure provides the framework for decision-making, accountability, and oversight within security programs. This includes defined roles and responsibilities, escalation procedures, and reporting mechanisms that ensure appropriate visibility and control.
Measurable Outcomes enable security programs to demonstrate their value and effectiveness through key performance indicators, metrics, and regular reporting. These measurements help justify continued investment and identify areas requiring improvement.
Cultural Integration ensures that security becomes part of the organizational DNA rather than an external imposition. Effective programs foster a security-conscious culture where employees understand their roles and actively contribute to organizational protection.
Flexibility and Adaptability allow security programs to respond effectively to changing circumstances, whether driven by business growth, technological evolution, or emerging threats. Rigid programs often fail when faced with unexpected challenges.
The Emergence of Security Program Management
Security Program Management emerged as a distinct discipline in response to the growing complexity and strategic importance of organizational security. This evolution reflects broader changes in how businesses view and approach cybersecurity challenges.
During the early days of computing, security was primarily a technical function handled by IT departments as an operational concern. Organizations focused on protecting individual systems and networks through technical controls such as firewalls, antivirus software, and access controls. Security decisions were often made reactively, in response to specific incidents or technical requirements.
As businesses became increasingly dependent on digital technologies and interconnected systems, the scope and impact of security risks expanded dramatically. High-profile data breaches and cyberattacks demonstrated that security failures could have catastrophic business consequences, including financial losses, regulatory penalties, and reputational damage.
This realization led to a fundamental shift in how organizations approached security. Rather than viewing it as purely a technical issue, business leaders began recognizing security as a critical business function that required strategic planning, resource allocation, and executive oversight. This transformation created the need for Security Program Management as a discipline that could bridge technical security implementation with business strategy.
The regulatory environment also played a significant role in driving the emergence of Security Program Management. Legislation such as the Sarbanes-Oxley Act, HIPAA, and GDPR created specific requirements for security controls and risk management processes. Organizations needed structured approaches to ensure compliance while managing the complexity of multiple regulatory frameworks.
The rise of enterprise risk management as a business discipline further contributed to the development of Security Program Management. Organizations began recognizing that security risks needed to be managed within the broader context of enterprise risk, requiring integration with other risk management functions and alignment with overall business objectives.
Cloud computing, mobile technologies, and remote work arrangements introduced new complexities that traditional security approaches couldn't adequately address. These developments required more sophisticated program management approaches that could coordinate security efforts across diverse technology environments and organizational boundaries.
The Attributes that Characterize Security Program Management
Security Program Management is distinguished by several key attributes that differentiate it from traditional security administration or technical security implementation. These characteristics define the scope, approach, and value proposition of effective security program management.
Strategic Perspective represents perhaps the most fundamental attribute of Security Program Management. Rather than focusing solely on technical implementations or operational tasks, security program managers take a comprehensive view that considers how security initiatives support broader business objectives and organizational strategy.
Cross-Functional Coordination enables security program managers to work effectively across organizational boundaries, collaborating with various departments and stakeholders to implement security measures that span the entire enterprise. This requires strong communication skills and the ability to translate technical security concepts into business language.
Risk-Driven Decision-Making guides security program managers to prioritize initiatives and allocate resources based on risk assessments rather than compliance checklists or technical preferences. This approach ensures that security investments deliver maximum value in terms of risk reduction.
Lifecycle Management encompasses the ability to manage security initiatives from conception through implementation, operation, and eventual retirement or replacement. This includes project management skills, change management capabilities, and the ability to maintain long-term perspectives while addressing immediate needs.
Stakeholder Management involves building and maintaining relationships with various stakeholders, including executives, business unit leaders, technical teams, and external partners. Effective security program managers can communicate security value propositions to different audiences and gain support for security initiatives.
Performance Measurement includes the development and maintenance of metrics and reporting mechanisms that demonstrate program effectiveness and identify areas for improvement. This requires analytical skills and the ability to translate security activities into business-relevant measurements.
Compliance Orchestration involves coordinating security activities to meet multiple regulatory requirements and industry standards while avoiding duplication of effort and unnecessary complexity. This requires a deep understanding of various compliance frameworks and the ability to create integrated approaches.
Continuous Improvement drives security program managers to regularly assess and enhance their programs based on changing threats, new technologies, business developments, and lessons learned from security incidents or near-misses.
Resource Optimization ensures that security programs make efficient use of available resources, including budget, personnel, and technology assets. This involves making difficult trade-off decisions and finding creative solutions to resource constraints.
Four Major Stages of Security Program Management
Security Program Management typically evolves through four distinct stages, each characterized by different levels of maturity, capability, and organizational impact. Understanding these stages helps organizations assess their current position and plan their development trajectory.
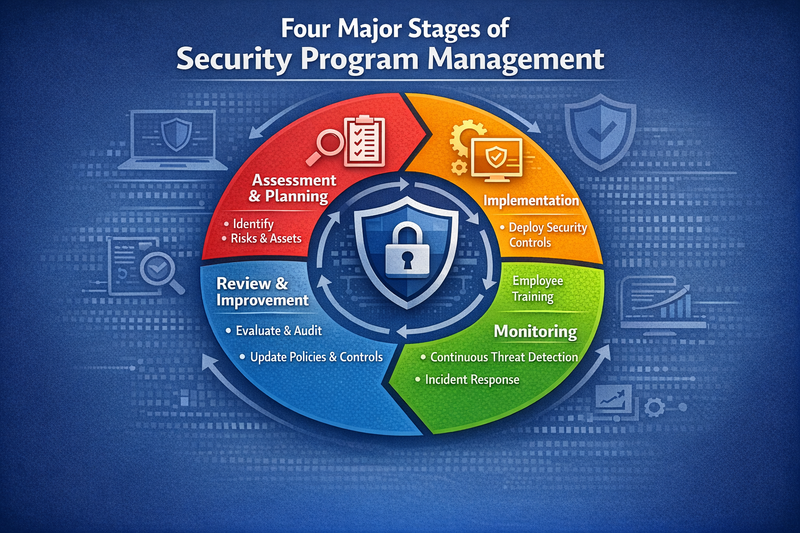
Stage 1: Reactive Security Management
The first stage represents the most basic level of security program management, characterized by reactive approaches that respond to immediate threats or compliance requirements without comprehensive planning or strategic integration.
Organizations in this stage typically implement security measures in response to specific incidents, audit findings, or regulatory requirements. Security decisions are often made in isolation, without considering broader implications or integration with other security initiatives. The focus remains primarily on technical implementations rather than program-level coordination.
Security program managers at this stage often function more as project coordinators than strategic leaders, managing individual security initiatives without comprehensive oversight or long-term planning. Metrics and reporting tend to be limited, focusing on technical measurements rather than business impact or risk reduction.
Common characteristics of reactive security management include fragmented security tools and processes, limited integration between security functions, minimal executive visibility into security programs, and frequent firefighting to address urgent security issues.
While reactive approaches can address immediate needs, they often result in inefficient resource utilization, security gaps, and difficulty demonstrating value to business stakeholders. Organizations typically recognize the need to advance beyond this stage as security challenges become more complex and business impacts more significant.
Stage 2: Organized Security Management
The second stage represents a significant advancement in security program maturity, characterized by more structured approaches that establish consistent processes and governance frameworks.
Organizations at this stage begin implementing formal security policies, procedures, and standards that provide consistency across security activities. Security program managers establish governance structures that define roles, responsibilities, and decision-making processes for security initiatives.
Risk assessment processes become more systematic, enabling better prioritization of security investments and more strategic resource allocation. Organizations begin developing comprehensive security architectures that guide technology decisions and integration efforts.
Metrics and reporting capabilities expand to include business-relevant measurements and regular communication with executive stakeholders. Security program managers begin building relationships across the organization and establishing security as a recognized business function.
Common characteristics of organized security management include standardized security processes and procedures, established governance structures and oversight mechanisms, regular risk assessments and security planning cycles, improved integration between security functions, and enhanced visibility into security program performance.
This stage represents a critical transition point where organizations move from ad-hoc security activities to structured program management approaches that can scale with business growth and complexity.
Stage 3: Integrated Security Management
The third stage represents advanced security program maturity, characterized by comprehensive integration of security considerations throughout the organization and alignment with business strategy.
Organizations at this stage have fully integrated security into their business processes, ensuring that security considerations are embedded in all major decisions and initiatives. Security program managers function as strategic advisors who influence business direction and help optimize organizational risk posture.
Risk management becomes enterprise-wide, with security risks managed within the broader context of business risk. Organizations develop sophisticated threat intelligence capabilities that inform proactive security measures and strategic planning.
Performance measurement systems provide comprehensive visibility into security program effectiveness and business impact. Organizations establish strong security cultures where employees actively contribute to security objectives and understand their roles in protecting organizational assets.
Common characteristics of integrated security management include security considerations embedded in all business processes, comprehensive threat intelligence and risk management capabilities, strong security cultures and employee engagement, sophisticated performance measurement and reporting systems, and strategic influence on business decisions and direction.
Organizations at this stage typically demonstrate strong resilience against security threats and can adapt quickly to changing risk environments while maintaining operational efficiency.
Stage 4: Optimized Security Management
The fourth and most advanced stage represents security program excellence, characterized by continuous optimization, innovation, and industry leadership in security practices.
Organizations at this stage have achieved security program maturity that enables them to anticipate and prepare for emerging threats while continuously improving their security posture. Security program managers function as strategic leaders who drive innovation and best practices throughout the industry.
These organizations typically serve as benchmarks for security program effectiveness and often share their expertise through industry forums, research initiatives, and thought leadership activities. They maintain strong relationships with security vendors, research organizations, and government agencies that provide early insight into emerging threats and technologies.
Performance measurement systems at this stage provide predictive capabilities that enable proactive adjustments to security strategies based on changing risk environments. Organizations demonstrate exceptional resilience and recovery capabilities that enable them to maintain operations even during significant security incidents.
Common characteristics of optimized security management include industry leadership in security practices and innovation, predictive security capabilities and proactive threat response, exceptional resilience and recovery capabilities, strong external partnerships and threat intelligence sharing, and continuous optimization based on advanced analytics and performance measurement.
Organizations at this stage often influence industry standards and best practices while maintaining security programs that adapt dynamically to changing threat landscapes and business requirements.
Conclusion
Security Program Management has evolved from a tactical necessity into a strategic business discipline that plays a crucial role in organizational success and sustainability. As cyber threats continue to grow in sophistication and frequency, the importance of structured, comprehensive approaches to security management will only increase.
The journey from reactive security management to optimized security programs requires commitment, resources, and patience, but organizations that make this investment position themselves for long-term success in an increasingly dangerous digital environment. By understanding the qualities of effective security programs and the stages of program development, organizations can chart courses toward security excellence that protect their assets while enabling business growth and innovation.
The future of Security Program Management will likely be shaped by emerging technologies such as artificial intelligence, quantum computing, and advanced analytics, but the fundamental principles of strategic thinking, risk-based decision making, and business alignment will remain constant. Organizations that master these principles while adapting to technological change will build security programs that provide sustainable competitive advantages in the digital economy.
Transform your Security Program Management from cost center to strategic advantage. Partner with Regulance AI to build integrated security frameworks that align with your business objectives. Explore our services today.