What Is P2PE in PCI DSS and How Does It Secure Your Payments?


Introduction
Every day, millions of businesses process payment card transactions, and with each swipe, dip, or tap comes an enormous responsibility to protect sensitive customer data. Data breaches cost businesses an average of millions in damages, not to mention the irreparable harm to customer trust and brand reputation. If you accept credit or debit cards, you're likely familiar with PCI DSS compliance requirements, but there's a powerful security solution that can dramatically simplify your compliance journey while strengthening your defenses: Point-to-Point Encryption, or P2PE.
P2PE is transforming the payment security landscape by encrypting cardholder data at the exact moment of card interaction, keeping it protected throughout the entire transaction process. Unlike traditional payment methods where sensitive data might be vulnerable at multiple points, P2PE ensures that card information remains encrypted from the payment terminal straight through to your payment processor's secure environment. This means your business systems never touch unencrypted payment data, significantly reducing your risk exposure.
For businesses struggling with the complexity and cost of PCI DSS compliance, P2PE offers a game-changing advantage. By implementing a validated P2PE solution, you can substantially reduce your compliance scope, cutting down on required security controls, documentation, and associated costs. If you operate a small retail shop, manage multiple locations, or run an enterprise-level operation, understanding P2PE entails building a fortress around your customers' payment information while making your life easier. This guide will break down everything you need to know about P2PE, how it works with PCI DSS, and how to implement it effectively in your business.
What is P2PE?
Point-to-Point Encryption, commonly known as P2PE, is a security standard established by the Payment Card Industry Security Standards Council (PCI SSC). P2PE is a method of encrypting payment card data from the moment a customer's card is swiped, dipped, or tapped at a payment terminal until that data reaches the secure decryption environment of the payment processor.
P2PE pauses as a secure tunnel for payment data. When a customer uses their card, the payment terminal immediately encrypts the sensitive information using sophisticated encryption algorithms. This encrypted data then travels through your business systems, networks, and potentially the internet, remaining completely unreadable to anyone who might intercept it. Only when the data reaches the authorized payment processor's secure environment can it be decrypted and processed.
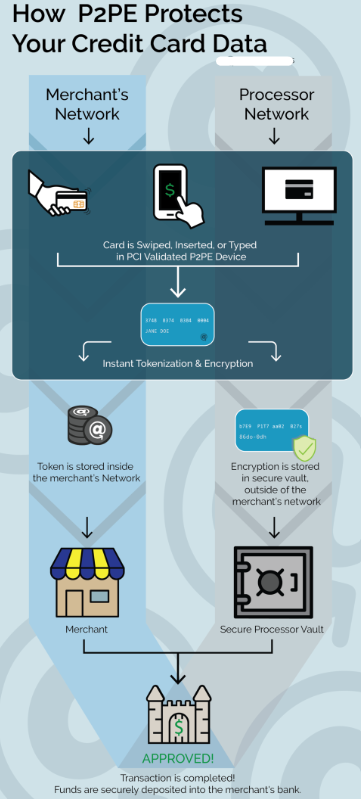
The beauty of P2PE lies in its simplicity from a merchant's perspective. The encryption happens automatically at the point of interaction, which means that businesses never have access to clear-text cardholder data. This is fundamentally different from older payment processing methods where card data might exist in readable form at various points in the transaction chain, creating multiple opportunities for criminals to steal it.
A validated P2PE solution must meet strict requirements set by the PCI SSC. These solutions use specially designed, tamper-resistant encryption devices that are listed and approved by PCI. The encryption keys used are managed according to rigorous standards, ensuring that even if someone physically compromises a device, they cannot extract usable payment data.
What Are The Benefits of P2PE?
Implementing P2PE brings a wealth of advantages that extend far beyond simple data protection. Let's explore the key benefits that make P2PE an attractive solution for businesses of all sizes.
Enhanced Security and Reduced Breach Risk
The most obvious benefit is the dramatically improved security posture. By encrypting payment data at the point of capture, P2PE eliminates the most vulnerable moment in the payment process. Even if hackers manage to infiltrate your network or intercept data transmissions, all they'll find is encrypted gibberish that's computationally infeasible to crack. This significantly reduces your risk of experiencing a costly data breach that could expose thousands of customer payment cards.
Simplified PCI DSS Compliance
One of the most compelling reasons businesses adopt P2PE is the substantial reduction in PCI DSS compliance scope. When you use a validated P2PE solution, your business systems never handle clear-text cardholder data. This means large portions of the PCI DSS requirements simply don't apply to your environment anymore. Instead of completing the full Self-Assessment Questionnaire (SAQ D), eligible merchants can use the much shorter SAQ P2PE, which contains significantly fewer requirements. This translates to less time, effort, and cost spent on compliance activities.
Cost Savings
While implementing P2PE requires an initial investment, the long-term cost savings can be substantial. Reduced PCI DSS scope means lower costs for compliance assessments, security audits, and the ongoing maintenance of security controls. You'll also save on the infrastructure and personnel needed to protect cardholder data throughout your systems. Additionally, the reduced risk of a data breach means avoiding the astronomical costs associated with breach investigation, customer notification, regulatory fines, and reputation damage.
Customer Trust and Brand Protection
In an era where consumers are increasingly concerned about data privacy, demonstrating that you use advanced security measures like P2PE can be a competitive advantage. Customers are more likely to trust businesses that take their payment security seriously. This trust translates into customer loyalty, positive reviews, and word-of-mouth referrals. Moreover, by preventing breaches, you protect your brand from the negative publicity that can devastate customer confidence.
Operational Efficiency
P2PE solutions are designed to integrate seamlessly with existing payment workflows. Once implemented, the encryption happens automatically without requiring additional steps from cashiers or customers. This means you maintain fast checkout times while dramatically improving security. The reduced compliance burden also frees up your IT team to focus on other business priorities rather than spending countless hours on PCI DSS documentation and remediation.
Future-Proofing Your Payment Systems
As payment technology evolves and security threats become more sophisticated, P2PE provides a foundation for adapting to new requirements. Validated P2PE solutions are regularly updated to address emerging threats and comply with evolving standards, helping ensure your payment security remains robust well into the future.
What is the Relationship Between P2PE and PCI DSS?
To understand how P2PE and PCI DSS relate to each other, we first need to clarify what PCI DSS is and why it exists.
The Payment Card Industry Data Security Standard (PCI DSS) is a comprehensive set of security requirements designed to ensure that all companies that accept, process, store, or transmit credit card information maintain a secure environment. Developed by major card brands including Visa, Mastercard, American Express, Discover, and JCB, PCI DSS aims to reduce credit card fraud and protect cardholder data from theft.
PCI DSS consists of twelve high-level requirements covering areas such as network security, access control, monitoring, encryption, and security policies. All merchants and service providers that handle payment card data must comply with PCI DSS, though the validation requirements vary based on transaction volume and business model.
Here's where P2PE enters the picture. The PCI Security Standards Council, which maintains PCI DSS, recognized that one of the most effective ways to protect payment data is to ensure that merchants never have access to it in clear-text form. This insight led to the development of the P2PE standard as a complementary security solution that works within the broader PCI DSS framework.
P2PE is essentially a specialized security control that, when properly implemented using a validated solution, significantly reduces the scope of PCI DSS requirements that apply to a merchant. This relationship is symbiotic; PCI DSS establishes the overall security framework and compliance requirements, while P2PE provides a specific technical solution that helps merchants achieve compliance more easily.
When a merchant implements a validated P2PE solution listed by the PCI SSC, they're using a payment security method that the Council has thoroughly vetted and approved. This validation gives merchants and their acquiring banks confidence that the solution meets stringent security standards. In recognition of this enhanced security, the PCI SSC allows merchants using validated P2PE solutions to complete a shortened version of the compliance questionnaire.
It's important to understand that P2PE doesn't eliminate PCI DSS compliance requirements entirely; merchants still need to comply with certain aspects of the standard. However, the relationship between P2PE and PCI DSS creates a more manageable compliance pathway by removing the most burdensome requirements related to protecting stored cardholder data and securing the networks where that data might reside.
What is the Difference and Similarities Between P2PE and PCI DSS?
While P2PE and PCI DSS are closely related, they serve different purposes and operate at different levels. Understanding these differences and similarities is crucial for making informed decisions about your payment security strategy.
Key Differences
Scope and Purpose: PCI DSS is a broad security standard encompassing twelve major requirements covering everything from firewall configuration to physical security to employee training. It's designed to create a comprehensive security framework for any environment that handles payment card data. P2PE, on the other hand, is a specific technical solution focused solely on encrypting payment data from the point of capture to the payment processor.
Applicability: PCI DSS applies to all organizations that store, process, or transmit cardholder data, regardless of how they handle that data. It's mandatory for any business accepting payment cards. P2PE is an optional security solution that businesses can choose to implement. However, if a business does choose to use P2PE, it must use a validated solution to receive compliance benefits.
Implementation Approach: PCI DSS consists of requirements that organizations must meet through various means; they can choose different technologies, processes, and controls to achieve compliance. P2PE is a specific technology implementation that must use PCI-approved devices and follow defined encryption protocols. There's less flexibility in how P2PE is implemented because it must meet precise technical specifications.
Compliance Validation: PCI DSS compliance is validated through Self-Assessment Questionnaires (SAQs) for most merchants or through an onsite assessment by a Qualified Security Assessor (QSA) for larger organizations. P2PE solutions themselves undergo validation by the PCI SSC before they can be listed as approved solutions. Merchants then leverage these validated solutions to simplify their own PCI DSS compliance validation.
Key Similarities
Shared Goal: Both P2PE and PCI DSS exist for the same fundamental reason, to protect payment card data from theft and fraud. They both aim to minimize the risk of data breaches and reduce opportunities for criminals to steal cardholder information.
Governance: Both standards are managed by the PCI Security Standards Council, ensuring consistency in approach and alignment of objectives. This common governance structure means that P2PE solutions are designed specifically to support PCI DSS compliance goals.
Focus on Encryption: While PCI DSS includes encryption as one component among many security controls, P2PE is entirely focused on encryption. PCI DSS Requirement 4 specifically mandates encryption of cardholder data transmitted across open, public networks, and P2PE fulfills this requirement in a particularly robust way.
Industry Recognition: Both PCI DSS compliance and P2PE validation are recognized and respected throughout the payment card industry. Acquiring banks, payment processors, and card brands all acknowledge the value of both standards in creating a more secure payment ecosystem.
Regular Updates: Both standards evolve over time to address new threats and incorporate technological advances. The PCI SSC regularly updates PCI DSS requirements and P2PE technical specifications to keep pace with the changing security landscape.
In essence, P2PE can be thought of as a specialized tool that helps achieve specific PCI DSS objectives more effectively. PCI DSS is the comprehensive rulebook, while P2PE is an advanced strategy for winning the game according to those rules.
How Is P2PE Used?
P2PE is used by businesses that want to enhance security while simplifying compliance. To use P2PE, you first select a validated P2PE solution from the PCI SSC's list of approved solutions. These solutions come from payment processors or payment technology providers who have undergone rigorous validation.
Once you've partnered with a P2PE solution provider, they'll supply you with PCI-approved encryption devices; these might be traditional card readers, modern contactless terminals, or mobile payment acceptance devices. The provider handles the complex aspects of key management and encryption protocols behind the scenes.
From an operational standpoint, using P2PE is straightforward. Your staff processes payments just as they would with any other system; customers swipe, insert, or tap their cards, and the transaction proceeds normally. The crucial difference is that the encryption happens automatically and invisibly at the device level, before any payment data enters your network.
On the compliance side, you'll work with your payment processor or acquiring bank to validate that you're using the P2PE solution correctly. This typically involves completing the SAQ P2PE questionnaire annually, which focuses on verifying that you're using validated devices, following proper procedures, and not storing or accessing clear-text cardholder data.
How Do P2PE and PCI DSS Work Together
The most effective use of these standards comes from implementing them together strategically. Here's how this typically works in practice:
A retail business might start by assessing their current payment processing setup and determining their PCI DSS compliance obligations. They realize that achieving full compliance with SAQ D (the longest questionnaire) would require significant investment in network security, employee training, and ongoing monitoring.
By implementing a validated P2PE solution, they immediately reduce their compliance scope. Now they can use SAQ P2PE instead, which addresses only the controls relevant to their simplified environment. They still need to comply with PCI DSS, but the specific requirements are far fewer.
For payment security, they rely on P2PE to protect customer payment data during transactions, while using other PCI DSS requirements to secure their overall business environment; maintaining firewalls, controlling physical access to systems, and training employees on security awareness.
This combined approach provides multiple layers of security while making compliance more manageable and cost-effective. The business gets the best of both worlds: robust technical security through P2PE and comprehensive organizational security through PCI DSS.
How to Implement P2PE in Your Business
Successfully implementing P2PE requires careful planning and execution. Here's a step-by-step guide to help you navigate the implementation process.
Step 1: Assess Your Current Payment Environment
Begin by thoroughly documenting how you currently accept and process payments. Identify all locations where customers can make payments, whether that's physical retail locations, mobile payment acceptance, or telephone orders. Understand your current PCI DSS compliance obligations and document the challenges you're facing in maintaining compliance.
Calculate the costs associated with your current approach, including hardware, software, compliance assessments, security tools, and staff time. This baseline will help you evaluate the return on investment for P2PE implementation.
Step 2: Research Validated P2PE Solutions
Visit the PCI Security Standards Council website and review their list of validated P2PE solutions. These solutions have undergone rigorous testing and meet all required security standards. Pay attention to which solutions support your specific payment acceptance needs; some specialize in retail environments, others in e-commerce, and some in mobile or integrated systems.
Consider factors such as the solution provider's reputation, customer support quality, integration capabilities with your existing systems, hardware options, pricing structure, and contractual terms. Don't hesitate to request demonstrations or trial periods to ensure the solution meets your operational needs.
Step 3: Engage with Solution Providers
Contact several validated P2PE solution providers to discuss your specific requirements. During these conversations, ask detailed questions about implementation timelines, training and support offerings, hardware costs and specifications, monthly processing fees, integration requirements with your POS or business management systems, and ongoing maintenance and update procedures.
Request references from businesses similar to yours who have implemented the solution. Learning from others' experiences can help you avoid common pitfalls and set realistic expectations.
Step 4: Develop an Implementation Plan
Once you've selected a P2PE solution, work with your provider to create a detailed implementation plan. This should include a timeline for hardware delivery and installation, staff training schedules, integration and testing phases, parallel running period where old and new systems operate simultaneously, cutover date for full transition, and compliance validation timeline.
Identify who within your organization will be responsible for coordinating the implementation, training staff, troubleshooting issues, and maintaining ongoing compliance.
Step 5: Install Hardware and Configure Systems
Your P2PE provider will supply validated encryption devices that you'll install at all payment acceptance points. This might involve replacing existing terminals or integrating new devices with your current POS system. Ensure that all devices are properly connected to secure networks and that any required software integrations are properly configured and tested.
During this phase, work closely with your IT team and the P2PE provider's technical support to address any connectivity or integration challenges. Thorough testing is critical; process test transactions using various payment methods to ensure everything functions correctly.
Step 6: Train Your Staff
Even though P2PE operates mostly behind the scenes, your staff needs to understand the basics of how the system works and why it's important. Provide training on how to process payments using the new devices, what to do if a device malfunctions or displays an error, security procedures to protect devices from tampering, and who to contact for technical support.
Emphasize that staff should never attempt to bypass security features or handle payment data outside the encrypted system, as doing so could compromise your compliance status.
Step 7: Validate Compliance
Once your P2PE solution is fully operational, work with your acquiring bank to validate your compliance status. You'll need to complete the SAQ P2PE questionnaire, which focuses on confirming that you're using validated devices correctly, not storing or accessing clear-text payment data, maintaining physical security of devices, and following all procedures specified by your P2PE solution provider.
Your acquiring bank may require an Attestation of Compliance (AOC) documenting your PCI DSS compliance status. Keep all documentation organized and readily available for annual validation.
Step 8: Maintain and Monitor
P2PE implementation isn't a one-time project; it requires ongoing attention to maintain security and compliance. Establish procedures for regularly inspecting devices for signs of tampering, promptly installing updates or security patches provided by your P2PE solution provider, replacing devices according to the provider's recommended schedule, conducting periodic staff training refreshers, and completing annual compliance validation.
Stay informed about changes to PCI standards and your P2PE solution's capabilities. Your provider should notify you of important updates, but it's wise to proactively monitor relevant industry news.
FAQs
Q: Is P2PE required for PCI DSS compliance?
A: No, P2PE is not required for PCI DSS compliance. It's an optional security solution that makes compliance easier by reducing scope. Merchants can achieve PCI DSS compliance through various means without using P2PE, though it generally requires more extensive security controls and documentation.
Q: How much does P2PE cost?
A: P2PE costs vary significantly depending on your business size, transaction volume, and chosen solution provider. Expect initial costs for encryption devices, which can range from a few hundred to several thousand dollars per terminal. There may also be implementation fees, monthly service fees, and per-transaction fees. However, many businesses find that the reduced compliance costs offset these expenses over time.
Q: Can I use any encryption device for P2PE compliance benefits?
A: No. To receive PCI DSS scope reduction benefits, you must use a validated P2PE solution listed on the PCI Security Standards Council website. Using non-validated encryption doesn't provide the same compliance advantages because it hasn't undergone the rigorous testing required for validation.
Q: Does P2PE eliminate all PCI DSS requirements?
A: No. While P2PE significantly reduces your PCI DSS scope, it doesn't eliminate compliance requirements entirely. You'll still need to comply with requirements related to physical device security, employee training, incident response, and other controls outlined in SAQ P2PE.
Q: What happens if a P2PE device is compromised or tampered with?
A: Validated P2PE devices are designed to detect tampering attempts and will typically cease functioning if compromised. If you discover a device has been tampered with, immediately remove it from service, contact your P2PE solution provider, and follow your incident response procedures. The device's encryption keys are protected in a way that makes extracting usable payment data extremely difficult even if someone physically compromises the device.
Q: Can P2PE work with my existing POS system?
A: Most validated P2PE solutions are designed to integrate with common POS systems, but compatibility varies. When evaluating P2PE solutions, specifically ask about integration with your current systems. Some solutions offer extensive integration options, while others may require you to modify or replace your POS software.
Q: How often do I need to validate my P2PE compliance?
A: PCI DSS compliance validation is required annually. This means you'll need to complete the SAQ P2PE questionnaire once per year and submit an Attestation of Compliance to your acquiring bank. However, you should be maintaining compliance continuously throughout the year, not just during the annual validation period.
Q: What's the difference between P2PE and tokenization?
A: P2PE encrypts payment data as it travels from the point of capture to the payment processor, protecting data in transit. Tokenization replaces sensitive payment data with a non-sensitive token that can be stored for future use without PCI DSS implications. Many merchants use both technologies together, P2PE protects data during initial capture and transmission, while tokenization protects data if you need to store it for recurring payments or customer convenience.
Conclusion
Protecting payment card data is about maintaining customer trust, safeguarding your business reputation, and avoiding the potentially devastating costs of a data breach. Point-to-Point Encryption represents one of the most effective security technologies available to businesses of all sizes, offering a powerful combination of enhanced security and simplified compliance.
By encrypting payment data from the moment a card is presented until it reaches your payment processor's secure environment, P2PE eliminates the most vulnerable points in the payment process. Your business systems never have access to clear-text cardholder data, dramatically reducing your risk exposure. The relationship between P2PE and PCI DSS creates a pathway to more manageable compliance, allowing you to focus your resources on growing your business rather than struggling with complex security requirements.
Implementing P2PE does require an investment of time and resources, but the long-term benefits include: reduced compliance costs, enhanced security posture, customer confidence, and operational efficiency; make it a worthwhile consideration for any business serious about payment security. As payment technologies continue to evolve and security threats become more sophisticated, P2PE provides a foundation for staying ahead of emerging risks.
If you're a small retailer processing dozens of transactions daily or a large enterprise handling millions of payments, understanding P2PE and its relationship to PCI DSS is essential for making informed decisions about your payment security strategy. By following the implementation steps outlined in this guide and working with reputable validated solution providers, you can leverage P2PE to create a more secure, efficient, and compliant payment environment.
Contact Regulance today for a free consultation and discover how we can transform your payment security from a compliance burden into a competitive advantage. Visit our website or call us to schedule your assessment and take the first step toward robust payment security that protects your business and your customers.