What Is FedRAMP and How Does It Secure Federal Cloud Systems?


Introduction
Cloud computing has transformed how organizations operate, but when it comes to the federal government, moving sensitive data to the cloud is not as simple as signing up for a service. The U.S. government manages everything from Social Security records and tax information to national security intelligence and healthcare data. Every piece of this information demands ironclad protection, which is exactly where FedRAMP comes into play.
FedRAMP, the Federal Risk and Authorization Management Program, has become the gold standard for cloud security in government operations. Since its launch in 2011, this program has fundamentally changed how federal agencies evaluate and adopt cloud services. Instead of each agency conducting separate security reviews of the same cloud platforms, a process that was expensive, time-consuming, and inconsistent, FedRAMP created a unified approach that works across the entire government.
For cloud service providers, FedRAMP authorization unlocks access to a massive market worth billions of dollars annually. For federal agencies, it streamlines the path to modern, secure cloud solutions. For compliance professionals, it represents a comprehensive framework built on rigorous security standards that extend far beyond government use.
Understanding FedRAMP matters whether you're a technology vendor eyeing government contracts, an agency leader modernizing IT infrastructure, or simply someone curious about how the government protects digital information. This guide breaks down everything you need to know about FedRAMP, from its core requirements to its real-world impact on cloud security and compliance.
What is FedRAMP?
FedRAMP stands for the Federal Risk and Authorization Management Program. Established in 2011, it's a government-wide program that provides a standardized approach to security assessment, authorization, and continuous monitoring for cloud products and services used by federal agencies.
FedRAMP is a rigorous security certification program specifically designed for cloud service providers who want to do business with the U.S. government. Rather than requiring each of the hundreds of federal agencies to conduct their own separate security assessments of the same cloud service, FedRAMP creates a "do once, use many times" framework. Once a cloud service achieves FedRAMP authorization, any federal agency can leverage that authorization, dramatically reducing duplication of effort and accelerating cloud adoption across government.
The program is administered by the FedRAMP Program Management Office (PMO), which operates within the General Services Administration (GSA). The PMO works in collaboration with the Department of Homeland Security, the Department of Defense, and the National Institute of Standards and Technology (NIST) to maintain and evolve the program's requirements and processes.
FedRAMP implements standardized security requirements based on NIST guidelines, specifically NIST Special Publication 800-53, which provides a catalog of security and privacy controls for information systems. By applying these controls to cloud environments, FedRAMP ensures that federal data remains secure regardless of which cloud platform it resides on.
The Purpose of FedRAMP
The creation of FedRAMP addressed several critical challenges that the federal government faced during the early adoption of cloud computing technologies.
Standardizing Security Assessments
Before FedRAMP, federal agencies operated in silos when evaluating cloud services. Each agency would conduct its own security assessment using different standards, methodologies, and criteria. This approach was inefficient, inconsistent, and costly. A cloud provider might undergo dozens of separate assessments to work with multiple agencies, essentially proving the same security posture repeatedly. FedRAMP eliminated this redundancy by creating a single, standardized assessment process that all agencies recognize and accept.
Accelerating Cloud Adoption
The federal government recognized that cloud computing offered tremendous benefits in terms of cost savings, scalability, and innovation. However, the security concerns and assessment burdens were significantly slowing adoption rates. By streamlining the authorization process, FedRAMP removed a major barrier, allowing agencies to adopt cloud services more quickly while maintaining rigorous security standards.
Ensuring Consistent Security Standards
With sensitive federal data moving to the cloud, the government needed assurance that all cloud service providers met consistent, high-level security requirements. FedRAMP establishes baseline security requirements that protect federal information across different impact levels, ensuring that whether an agency is using a cloud service for low-sensitivity data or high-security applications, appropriate protections are in place.
Enabling Reusability and Reciprocity
One of FedRAMP's most important purposes is promoting reciprocity among federal agencies. When one agency authorizes a cloud service through FedRAMP, other agencies can leverage that authorization without starting from scratch. This "authorization reuse" principle saves time, money, and resources across the entire federal government.
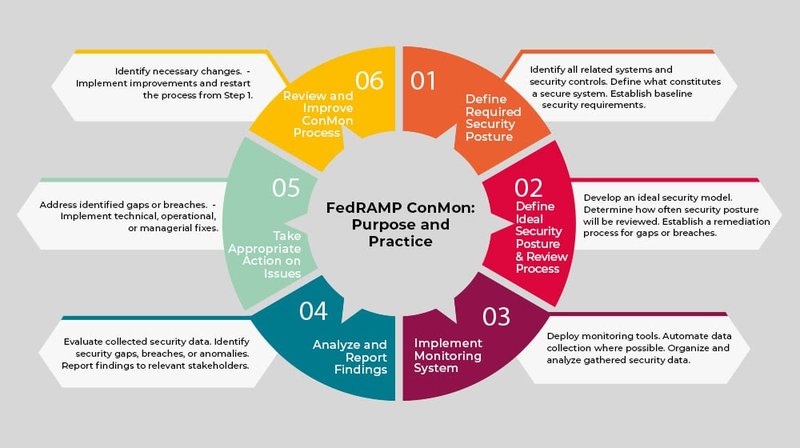
Managing Risk Continuously
Cloud environments are dynamic, with constant updates, patches, and changes. FedRAMP doesn't just assess security at a single point in time; it requires continuous monitoring to ensure that security controls remain effective as the cloud service evolves. This ongoing risk management approach keeps pace with the rapidly changing threat landscape.
Benefits of FedRAMP
FedRAMP delivers substantial benefits to multiple stakeholders in the federal cloud ecosystem. Understanding these advantages helps explain why the program has become such a critical component of government IT modernization.
For Federal Agencies
Reduced Time and Cost: Agencies can leverage existing FedRAMP authorizations instead of conducting lengthy, expensive assessments themselves. This can reduce authorization timelines from 12-18 months down to just a few months.
Increased Confidence: When an agency adopts a FedRAMP-authorized service, they have assurance that it has undergone rigorous third-party assessment and meets stringent security requirements.
Access to Innovation: By simplifying the path for cloud providers to achieve authorization, FedRAMP enables agencies to access cutting-edge cloud technologies and innovative solutions more quickly.
Standardized Security Baselines: All FedRAMP-authorized services meet the same baseline security requirements, making it easier for agencies to compare options and make informed decisions.
For Cloud Service Providers
Market Access: FedRAMP authorization opens the door to the entire federal marketplace, representing billions of dollars in potential contracts across hundreds of agencies.
Competitive Advantage: Being FedRAMP-authorized demonstrates a commitment to security and positions providers favorably when competing for government contracts.
Streamlined Authorization Process: Rather than navigating separate authorization processes for each agency, providers undergo a single standardized assessment that multiple agencies can accept.
Enhanced Security Posture: The rigorous FedRAMP process often helps providers identify and address security gaps, ultimately strengthening their overall security program beyond just federal requirements.
For Taxpayers
Better Value: By eliminating redundant security assessments, FedRAMP saves taxpayer dollars that would otherwise be spent on duplicative efforts.
Improved Security: Standardized, rigorous security requirements help protect sensitive federal data and citizen information from cyber threats.
Faster Government Services: As agencies adopt cloud technologies more quickly, they can modernize their systems and deliver better digital services to citizens.
Who Does FedRAMP Apply To?
Understanding who must comply with FedRAMP is crucial for organizations navigating the federal cloud landscape.
Cloud Service Providers
FedRAMP primarily applies to cloud service providers (CSPs) who want to offer their services to federal agencies. This includes providers of:
- Infrastructure as a Service (IaaS): Companies providing virtualized computing resources, storage, and networking capabilities.
- Platform as a Service (PaaS): Providers offering development platforms, databases, and middleware that agencies use to build and run applications.
- Software as a Service (SaaS): Organizations delivering software applications accessed through the internet, from email and collaboration tools to specialized agency applications.
If your cloud service will store, process, or transmit federal data, FedRAMP authorization is required before federal agencies can legally use your service.
Federal Agencies
All executive branch federal agencies must use FedRAMP when authorizing cloud services. This requirement stems from the Federal Information Security Management Act (FISMA) and subsequent Office of Management and Budget (OMB) policies.
Agencies can either leverage existing FedRAMP authorizations or sponsor a cloud service provider through the agency authorization process. However, they cannot use cloud services that handle federal data unless those services have achieved FedRAMP authorization at the appropriate impact level.
Third-Party Assessors
FedRAMP also applies to Third-Party Assessment Organizations (3PAOs), which are independent entities accredited to assess cloud service providers against FedRAMP requirements. These assessors must meet specific qualifications and maintain accreditation to perform FedRAMP assessments.
Exemptions and Special Cases
Certain situations may not require FedRAMP authorization:
- Cloud services that don't store, process, or transmit federal information
- On-premises solutions that aren't delivered as cloud services
- Certain intelligence community or Department of Defense systems that use alternative frameworks (though these often align closely with FedRAMP)
FedRAMP Requirements: What It Takes to Achieve Authorization
Achieving FedRAMP authorization is a significant undertaking that requires careful planning, substantial resources, and deep commitment to security. The requirements vary based on the impact level of the data the cloud service will handle.
Impact Levels
FedRAMP defines three impact levels based on FIPS 199 standards, which categorize the potential impact if federal information is compromised:
Low Impact: Information where the loss of confidentiality, integrity, or availability would have limited adverse effects. Low-impact authorization requires implementing 125 security controls.
Moderate Impact: Information where compromise could have serious adverse effects on operations, assets, or individuals. This is the most common authorization level and requires 325 security controls.
High Impact: Information where compromise could have severe or catastrophic adverse effects, such as loss of life or serious damage to national security. High-impact authorization requires 421 security controls.
Core Security Control Families
The security controls required by FedRAMP span 17 control families derived from NIST SP 800-53:
- Access Control
- Awareness and Training
- Audit and Accountability
- Security Assessment and Authorization
- Configuration Management
- Contingency Planning
- Identification and Authentication
- Incident Response
- Maintenance
- Media Protection
- Physical and Environmental Protection
- Planning
- Personnel Security
- Risk Assessment
- System and Services Acquisition
- System and Communications Protection
- System and Information Integrity
Each control family contains specific requirements that cloud service providers must implement and document.
Authorization Paths
Cloud service providers can pursue FedRAMP authorization through three primary paths:
JAB Provisional Authorization (P-ATO): The FedRAMP Joint Authorization Board, consisting of representatives from the Department of Defense, Department of Homeland Security, and General Services Administration, reviews and grants provisional authorizations for cloud services with wide federal applicability. This is considered the "gold standard" and involves rigorous evaluation.
Agency Authorization (ATO): A federal agency can sponsor a cloud service provider through the authorization process and grant an Authority to Operate specific to that agency. Other agencies can then leverage this authorization.
CSP Supplied Package: Providers can work with an accredited Third-Party Assessment Organization to prepare a complete security assessment package and submit it to the FedRAMP PMO for inclusion in the marketplace, making it available for agency review and use.
The Authorization Process
Regardless of the path chosen, achieving FedRAMP authorization typically involves these key steps:
- Preparation: Document your system architecture, define system boundaries, and identify which controls apply to your service.
- Security Assessment Plan (SAP): Develop a comprehensive plan for how security controls will be tested and validated.
- Third-Party Assessment: An accredited 3PAO conducts an independent assessment of your security controls, testing their implementation and effectiveness.
- Security Assessment Report (SAR): The 3PAO produces a detailed report documenting the assessment results, including any control deficiencies.
- Plan of Action and Milestones (POA&M): Create a remediation plan for any deficiencies or gaps identified during assessment.
- Authorization Decision: The JAB or sponsoring agency reviews all documentation and makes an authorization decision.
- Continuous Monitoring: After authorization, ongoing monitoring ensures that security controls remain effective as the system evolves.
Documentation Requirements
FedRAMP requires extensive documentation, including:
- System Security Plan (SSP) detailing all security controls and their implementation
- Security Assessment Plan and Report
- Plan of Action and Milestones
- Continuous Monitoring deliverables (monthly POA&M updates, annual assessments, significant change requests)
- Incident response procedures
- Contingency and disaster recovery plans
The documentation burden is substantial, often requiring dedicated resources and several months to complete properly.
How Does FedRAMP Affect Compliance?
FedRAMP has far-reaching implications for compliance efforts, both for cloud service providers and federal agencies. Understanding these effects helps organizations navigate the complex regulatory landscape.
Alignment with Other Frameworks
FedRAMP is built on NIST SP 800-53, which forms the foundation for many other compliance frameworks. This alignment means that achieving FedRAMP authorization often helps organizations meet requirements for:
FISMA Compliance: FedRAMP is the standard path for federal agencies to meet their FISMA obligations when using cloud services.
StateRAMP: Many state governments have adopted StateRAMP, which closely mirrors FedRAMP requirements, making it easier for providers to extend their compliance efforts to state markets.
NIST Cybersecurity Framework: The controls in FedRAMP map to the NIST Cybersecurity Framework, supporting broader cyber risk management efforts.
ISO 27001: While distinct, ISO 27001 and FedRAMP share many common security objectives, and evidence from one can often support the other.
Continuous Compliance Requirements
Unlike one-time certifications, FedRAMP requires ongoing compliance demonstration through continuous monitoring. Cloud service providers must:
- Submit monthly POA&M updates showing progress on remediating any control deficiencies
- Conduct annual security assessments to revalidate controls
- Report significant changes to the system that might affect security
- Respond to incidents and vulnerabilities promptly
- Maintain documentation reflecting the current state of security controls
This continuous monitoring approach ensures that security doesn't degrade over time and that providers remain accountable for maintaining their security posture.
Impact on Vendor Management
For federal agencies, FedRAMP simplifies vendor security assessments but doesn't eliminate them entirely. Agencies must still:
- Verify that a provider's FedRAMP authorization covers their specific use case
- Ensure the impact level matches their data classification
- Conduct agency-specific risk assessments
- Negotiate appropriate security requirements in contracts
- Monitor vendor compliance throughout the contract period
FedRAMP provides a strong foundation, but agencies retain responsibility for making appropriate risk-based decisions about cloud adoption.
Supply Chain Considerations
FedRAMP addresses supply chain security by requiring cloud service providers to assess and document their external service dependencies. If a provider relies on other cloud services (such as using AWS or Azure as an underlying infrastructure), those dependencies must also be FedRAMP-authorized at an appropriate impact level.
This cascading compliance requirement ensures security throughout the entire service delivery chain and prevents gaps where data might be exposed through less-secure third-party services.
Implications for Hybrid and Multi-Cloud Strategies
As federal agencies increasingly adopt hybrid and multi-cloud strategies, FedRAMP authorization becomes even more critical. Each cloud component that handles federal data must be properly authorized, which can create complexity when integrating multiple services.
Organizations must carefully architect their solutions to maintain clear boundaries between authorized and unauthorized components and ensure data flows remain within FedRAMP-authorized environments.
Frequently Asked Questions (FAQs)
Q: How long does it take to achieve FedRAMP authorization?
A: The timeline varies significantly depending on your starting point, the authorization path you choose, and the impact level you're pursuing. On average, the process takes 12-18 months from initial preparation through final authorization. Organizations with mature security programs may move faster, while those needing significant remediation might take longer. The JAB P-ATO path typically takes longer than agency authorization because of the more extensive review process.
Q: How much does FedRAMP authorization cost?
A: Costs vary widely based on several factors, including your system's complexity, impact level, and current security maturity. Organizations typically spend between $250,000 and $1,000,000 to achieve initial authorization, with ongoing annual costs of $50,000 to $300,000 for continuous monitoring. Major cost drivers include third-party assessment fees, consultant support, security tool implementation, dedicated staff time, and documentation development.
Q: Can small businesses achieve FedRAMP authorization?
A: Yes, though it's challenging. FedRAMP recognizes that smaller cloud service providers face unique resource constraints and has initiatives to support them. The FedRAMP Accelerated process offers a faster path for low-impact authorizations, which can be more accessible for small businesses. Many small providers partner with consultants or managed service providers to navigate the process more efficiently.
Q: What happens if a FedRAMP-authorized service has a security incident?
A: FedRAMP requires immediate incident reporting and response. Providers must notify affected agencies and the FedRAMP PMO within strict timeframes, typically within hours of incident detection. The provider must conduct an investigation, document lessons learned, and implement corrective actions. Depending on the severity, the incident could trigger additional assessments or, in extreme cases, suspension of authorization. However, FedRAMP recognizes that security incidents happen and focuses on appropriate response and remediation rather than punitive measures for good-faith efforts.
Q: Do I need FedRAMP authorization to sell to state or local governments?
A: Not necessarily, but it increasingly helps. Many state governments have adopted StateRAMP, which closely aligns with FedRAMP requirements. Some states accept FedRAMP authorization directly, while others have their own specific requirements. Even for jurisdictions without formal requirements, having FedRAMP authorization demonstrates a strong security posture that can provide a competitive advantage in government procurement processes.
Q: What's the difference between FedRAMP and DoD's Cloud Computing Security Requirements Guide (SRG)?
A: While FedRAMP covers civilian federal agencies, the Department of Defense uses its own Cloud Computing SRG for defense-related systems. The frameworks are similar and based on the same underlying NIST controls, but DoD's requirements include additional controls specific to defense needs. Some cloud services hold both FedRAMP and DoD authorizations, while others focus on one or the other based on their target market.
Q: Can a FedRAMP-authorized service be revoked?
A: Yes, FedRAMP authorizations can be suspended or revoked if a provider fails to maintain required security controls, doesn't meet continuous monitoring obligations, experiences significant security incidents without proper response, or makes material misrepresentations about their security posture. However, the FedRAMP PMO typically works with providers to remediate issues before taking such drastic action.
Q: What's the difference between FedRAMP Ready, FedRAMP In Process, and FedRAMP Authorized?
A: These designations indicate different stages in the authorization journey. FedRAMP Ready means a provider has worked with an accredited assessor to demonstrate readiness and has a complete security package prepared for review, but hasn't yet received authorization. FedRAMP In Process indicates that the JAB has accepted a provider into its review process and authorization work is underway. FedRAMP Authorized means the provider has completed the process and received either a JAB P-ATO or Agency ATO, allowing federal agencies to use the service.
Conclusion
FedRAMP represents a fundamental shift in how the federal government approaches cloud security and authorization. By creating a standardized, rigorous framework for assessing and monitoring cloud services, the program has enabled federal agencies to harness the power of cloud computing while maintaining the high security standards necessary to protect sensitive government data.
For cloud service providers, achieving FedRAMP authorization opens doors to significant market opportunities within the federal government. While the journey requires substantial investment in time, resources, and security improvements, the payoff extends beyond just federal contracts. The security discipline and documentation rigor required by FedRAMP often strengthens a provider's overall security posture, making them more competitive in commercial markets as well.
For federal agencies, FedRAMP simplifies and accelerates cloud adoption by eliminating redundant security assessments and providing confidence that authorized services meet consistent security standards. This efficiency allows agencies to focus their resources on mission delivery rather than duplicative security reviews.
As cloud technology continues to evolve and cyber threats become increasingly sophisticated, FedRAMP will remain an essential framework for securing federal information in cloud environments. The program continues to adapt, incorporating lessons learned, addressing emerging technologies, and streamlining processes to balance security with the need for innovation and agility.
Don't let compliance complexity slow your growth. Partner with Regulance and transform compliance from a challenge into a competitive advantage.