What Is CVE and Why Does It Matter for PCI DSS and SOC 2 Compliance?


Introduction
Cybersecurity threats evolving at an unprecedented pace and security researchers discover new vulnerabilities in software, hardware, and systems that could potentially be exploited by malicious actors. For organizations handling sensitive data whether payment card information, customer records, or proprietary business data; staying ahead of these vulnerabilities is often a compliance requirement. Understanding how CVE (Common Vulnerabilities and Exposures) impacts compliance frameworks like PCI DSS and SOC 2 has become essential for organizations seeking to protect their systems and meet regulatory obligations.
If you've ever wondered how security professionals worldwide communicate about vulnerabilities, or how compliance frameworks like PCI DSS and SOC 2 expect you to manage security risks, you're in the right place. Understanding the relationship between CVE, PCI DSS, and SOC 2 is essential for anyone responsible for organizational security, compliance, or risk management.
This clearly outlined guide will help you understand what CVE is, why it matters, and how it directly impacts your compliance obligations under PCI DSS and SOC 2 frameworks.
What is Common Vulnerabilities and Exposures (CVE)?
CVE stands for Common Vulnerabilities and Exposures, and it's essentially the industry's universal language for discussing security vulnerabilities. It's more of a comprehensive catalog or dictionary of publicly known cybersecurity vulnerabilities and exposures that affect software and hardware products.
Maintained by the MITRE Corporation and sponsored by the U.S. Department of Homeland Security's Cybersecurity and Infrastructure Security Agency (CISA), the CVE program began in 1999 to solve a fundamental problem: security professionals, vendors, and organizations were all using different names for the same vulnerabilities, creating confusion and inefficiency in addressing security threats.
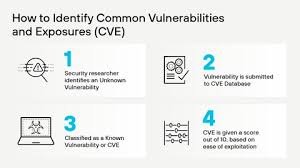
How CVE Works
Each CVE entry receives a unique identifier following a specific format: CVE-YEAR-NUMBER. For example, CVE-2024-1234 would be the 1,234th vulnerability cataloged in 2024. This standardized naming convention ensures that everyone from security researchers to system administrators is talking about the same vulnerability.
A typical CVE entry includes:
Unique Identifier: The CVE ID that serves as the permanent reference Description: A clear explanation of the vulnerability and what it affects References: Links to advisories, patches, and additional technical information Date Published: When the vulnerability was publicly disclosed Severity Rating: Often accompanied by a CVSS (Common Vulnerability Scoring System) score
The CVE Ecosystem
The CVE system operates through a network of CVE Numbering Authorities (CNAs), which are organizations authorized to assign CVE IDs to newly discovered vulnerabilities. These CNAs include major software vendors like Microsoft, Apple, and Google, as well as security research organizations and independent researchers.
When a vulnerability is discovered, it goes through a disclosure process. The discoverer typically reports it to the affected vendor or a CNA, which then assigns a CVE ID. Once the vendor has had time to develop a patch (usually following a responsible disclosure timeline), the CVE is published publicly, allowing organizations worldwide to assess their exposure and take appropriate action.
Why CVE Matters
The CVE system serves several critical purposes:
Universal Communication: Security teams can reference a CVE ID and immediately understand what vulnerability is being discussed, regardless of vendor or product names.
Tracking and Management: Organizations can track which CVEs affect their systems and monitor whether patches have been applied.
Compliance Requirements: Many regulatory and compliance frameworks explicitly require organizations to monitor and remediate CVEs, making the system central to compliance efforts.
Risk Assessment: CVE severity ratings help organizations prioritize which vulnerabilities pose the greatest risk and should be addressed first.
Tool Integration: Security tools like vulnerability scanners, patch management systems, and security information and event management (SIEM) platforms all reference CVEs, enabling automated vulnerability management.
The Relationship Between CVE and PCI DSS
What is PCI DSS?
The Payment Card Industry Data Security Standard (PCI DSS) is a set of security requirements designed to ensure that all companies that accept, process, store, or transmit credit card information maintain a secure environment. Developed by major credit card brands (Visa, Mastercard, American Express, Discover, and JCB), PCI DSS applies to any organization that handles cardholder data.
Non-compliance can result in significant consequences, including fines, increased transaction fees, loss of the ability to process credit cards, and reputational damage following a breach.
CVE's Central Role in PCI DSS Compliance
PCI DSS explicitly addresses vulnerability management and the remediation of known security issues. CVE is fundamental to meeting several key requirements:
Requirement 6: Develop and Maintain Secure Systems and Applications
PCI DSS Requirement 6.3.1 specifically mandates that organizations identify security vulnerabilities and patch them appropriately. The standard requires:
- Security vulnerabilities must be identified using reputable sources (CVE databases are specifically mentioned as examples)
- Vulnerabilities must be ranked according to risk, typically using CVSS scores associated with CVEs
- Critical security patches must be installed within one month of release
- All applicable security patches must be installed within an appropriate time frame
Requirement 11: Test Security of Systems and Networks Regularly
PCI DSS requires regular vulnerability scanning, both internal and external. These scans specifically look for systems vulnerable to known CVEs. Organizations must:
- Conduct quarterly external vulnerability scans using an Approved Scanning Vendor (ASV)
- Perform internal vulnerability scans quarterly and after significant changes
- Rescan systems until all "high-risk" vulnerabilities are resolved
The "high-risk" designation often directly correlates with CVE severity ratings, particularly those with CVSS scores of 4.0 or higher.
Practical Implementation for PCI DSS
To maintain PCI DSS compliance regarding CVE management, organizations should:
Establish a Vulnerability Management Program: Create formal processes for monitoring CVE databases, security advisories, and vendor notifications about new vulnerabilities affecting your systems.
Implement Risk-Based Prioritization: Not all CVEs are created equal. Use CVSS scores and consider your specific environment to prioritize which vulnerabilities to address first. PCI DSS focuses heavily on critical and high-risk vulnerabilities.
Maintain an Asset Inventory: You can't patch what you don't know about. Maintain a comprehensive inventory of all systems, software, and applications in your cardholder data environment.
Document Everything: PCI DSS assessors will want to see evidence of your vulnerability management processes, including how you track CVEs, prioritize remediation, and verify that patches have been applied successfully.
Use Automated Tools: Given the volume of CVEs published (thousands per year), manual tracking is impractical. Implement vulnerability scanning tools that automatically identify CVE exposures in your environment.
The Relationship Between CVE and SOC 2
What is SOC 2?
SOC 2 (Service Organization Control 2) is an auditing procedure that ensures service providers securely manage data to protect the interests of their clients. Developed by the American Institute of CPAs (AICPA), SOC 2 is particularly relevant for technology and cloud computing companies that store customer data in the cloud.
Unlike PCI DSS, which has specific technical requirements, SOC 2 is based on trust service criteria across five categories: Security, Availability, Processing Integrity, Confidentiality, and Privacy. Organizations can choose which categories are relevant to their business, though Security is mandatory for all SOC 2 audits.
How CVE Integrates with SOC 2
While SOC 2 doesn't explicitly mention CVE by name as frequently as PCI DSS does, vulnerability management is central to demonstrating effective security controls. Here's how CVE relates to key SOC 2 criteria:
CC7.1 - System Monitoring
This control requires organizations to monitor their systems to identify anomalies and security events. Monitoring for newly published CVEs that affect your infrastructure is a fundamental aspect of this requirement. Organizations must demonstrate:
- Processes for staying informed about new vulnerabilities (CVEs) affecting their technology stack
- Regular vulnerability scanning that identifies systems exposed to known CVEs
- Alerting mechanisms when critical CVEs are published that affect their environment
CC7.2 - System Changes
This control focuses on how organizations manage changes to systems, including applying security patches. CVE management intersects here because:
- Patches addressing CVEs must go through proper change management procedures
- Organizations must balance the urgency of security patches against the risk of system disruption
- Documentation must show how CVE severity influences patch deployment timelines
CC7.3 - Detection of Security Events
Organizations must have procedures to detect and respond to security events, including the exploitation of vulnerabilities. CVE awareness is essential because:
- Knowing which CVEs affect your systems helps you identify potential attack vectors
- Security monitoring tools should alert on exploitation attempts of known CVEs
- Incident response plans should account for CVE exploitation scenarios
Risk Assessment (CC3.2)
SOC 2 requires organizations to conduct risk assessments to identify threats. CVE databases provide crucial intelligence for these assessments:
- Identifying which published CVEs affect your specific software and hardware
- Evaluating the likelihood and potential impact of CVE exploitation
- Prioritizing security investments based on CVE risk profiles
Practical Implementation for SOC 2
Successfully demonstrating CVE management for SOC 2 compliance involves:
Documented Policies and Procedures: Create formal documentation outlining how your organization monitors for CVEs, assesses their impact, and remediates vulnerabilities. SOC 2 auditors love documentation.
Regular Vulnerability Assessments: Conduct vulnerability scans on a regular schedule (monthly or quarterly is common) and document the results. Show that you're identifying CVEs present in your environment.
Patch Management Process: Document your patch management procedures, including how quickly different categories of CVEs are addressed. Many organizations use risk-based approaches, patching critical CVEs within days or weeks, while lower-severity issues may have longer timelines.
Evidence of Remediation: Maintain records showing that identified CVEs have been addressed, either through patching, mitigating controls, or documented risk acceptance for edge cases.
Vendor Management: If you rely on third-party vendors, document how you ensure they're managing CVEs in the systems they provide or manage for you.
Frequently Asked Questions (FAQs)
How many CVEs are published each year?
The number of CVEs has grown dramatically over time. In recent years, between 20,000 and 25,000 new CVEs are published annually. This increasing volume makes automated vulnerability management tools essential rather than optional.
Do I need to patch every CVE that's published?
No. You only need to address CVEs that affect systems in your environment. This is why maintaining an accurate asset inventory is crucial—you need to know what software and versions you're running to determine which CVEs are relevant to you. Additionally, you should prioritize based on severity and potential impact to your specific business.
What's a CVSS score and why does it matter?
CVSS (Common Vulnerability Scoring System) is a standardized method for rating the severity of security vulnerabilities. Scores range from 0.0 to 10.0, with higher scores indicating more severe vulnerabilities. Both PCI DSS and SOC 2 auditors expect you to use these scores (or similar risk ratings) to prioritize remediation efforts. Generally, scores of 9.0-10.0 are critical, 7.0-8.9 are high, 4.0-6.9 are medium, and 0.1-3.9 are low severity.
How quickly do I need to patch vulnerabilities?
The timeline depends on severity and your compliance requirements. For PCI DSS, critical vulnerabilities must be patched within one month. Many security professionals recommend patching critical CVEs (CVSS 9.0+) within 15 days and high-severity CVEs (CVSS 7.0-8.9) within 30 days. For SOC 2, you define your own timelines, but they should be reasonable and consistently followed.
Can I fail a PCI DSS or SOC 2 audit due to unpatched CVEs?
Yes. Unaddressed high or critical CVEs are among the most common reasons for failing compliance audits. For PCI DSS, unpatched critical vulnerabilities can result in audit failure. For SOC 2, while there's more flexibility, a pattern of unaddressed vulnerabilities would likely result in qualified or adverse audit opinions.
Conclusion
In a technological advanced world where cyber threats are increasingly sophisticated and prevalent, CVE serves as an indispensable tool for organizations striving to maintain robust security postures while meeting compliance obligations. Far from being merely a technical database, CVE represents the foundation of modern vulnerability management practices and plays a central role in both PCI DSS and SOC 2 compliance frameworks.
For organizations handling payment card data, PCI DSS provides clear, prescriptive requirements for managing CVEs, with specific timelines and expectations that must be met to avoid penalties and maintain the ability to process payments. The standard's emphasis on timely patching and vulnerability scanning creates a structured framework that, when followed diligently, significantly reduces security risk.
SOC 2, while more flexible in its approach, equally emphasizes the importance of vulnerability management through its trust service criteria. The framework's principle-based nature allows organizations to design CVE management programs that fit their specific contexts, but the expectation of effective, consistent, and well-documented practices remains paramount.
The common thread between both frameworks is clear: organizations must proactively monitor for vulnerabilities, assess their potential impact, prioritize remediation based on risk, and maintain comprehensive documentation of their efforts. CVE makes all of this possible by providing a standardized language and reference system that enables efficient communication and action across the security community.
As the volume of published CVEs continues to grow year after year, organizations cannot afford to approach vulnerability management reactively or manually. Investing in automated vulnerability scanning tools, patch management solutions, and security monitoring platforms is about building a security-first culture that protects your organization, your customers, and your reputation.
By understanding the relationship between CVE, PCI DSS, and SOC 2, you're taking an important step toward building a more secure and compliant organization. The frameworks provide the roadmap, CVE provides the intelligence, and your commitment provides the momentum to keep your organization protected in an ever-evolving threat landscape.
Don’t let vulnerabilities put your compliance at risk. Use Regulance AI to turn CVE data into actionable steps for PCI DSS and SOC 2 success.