What Is AES and How Does It Strengthen PCI DSS Compliance?


Introduction
Millions of credit card transactions flow through businesses worldwide daily. Behind each swipe, tap, or online purchase lies a critical question: how do you keep that sensitive payment data safe from cybercriminals? The answer lies in two interconnected concepts that every business handling card payments must understand; AES encryption and PCI DSS compliance.
AES, or Advanced Encryption Standard, is the most trusted encryption method used globally to protect sensitive information. Meanwhile, PCI DSS (Payment Card Industry Data Security Standard) is the mandatory security framework that governs how businesses must protect payment card information.
Here's what many business owners don't realize: if you accept credit or debit cards, PCI DSS compliance isn't optional, and AES encryption sits at the heart of meeting those requirements. If you run a small coffee shop with a single card reader or manage an e-commerce platform processing thousands of transactions daily, understanding how AES works within the PCI DSS framework is critical to protecting your business.
Data breaches can cost businesses millions in fines, legal fees, and lost customer trust. But with proper AES implementation and PCI DSS compliance, you build a fortress around your customers' payment data. This article breaks down everything you need to know about AES, why it matters for PCI DSS compliance, and how it protects your business from financial and reputational disaster.
What is AES?
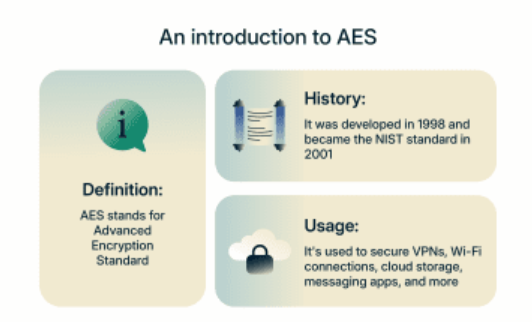
The Advanced Encryption Standard (AES) is a symmetric encryption algorithm that has become the worldwide standard for securing sensitive data. Adopted by the U.S. National Institute of Standards and Technology (NIST) in 2001, AES replaced the older Data Encryption Standard (DES), which had become vulnerable to modern computing power.
AES is an incredibly sophisticated lock and key system for your digital data. When you encrypt information using AES, you're essentially scrambling it into an unreadable format that can only be decoded with the correct encryption key. The beauty of AES lies in its mathematical complexity, it uses a series of substitution and permutation operations performed over multiple rounds to transform plain text into ciphertext.
AES operates with three different key lengths: 128-bit, 192-bit, and 256-bit. The larger the key size, the more secure the encryption, though all three variants are considered robust enough for protecting sensitive information. To put this in perspective, a 128-bit AES key has 340 undecillion possible combinations, that's a number so large it's practically incomprehensible. Even with the most powerful supercomputers available today, brute-forcing an AES-encrypted file would take longer than the age of the universe.
What makes AES particularly valuable is its versatility. It's used everywhere from encrypting files on your laptop to securing communications between your browser and websites, from protecting classified government information to safeguarding the payment data flowing through point-of-sale terminals. Its widespread adoption stems from its perfect balance of security, efficiency, and performance. Unlike some encryption methods that slow systems to a crawl, AES can process data quickly without compromising protection.
The algorithm has withstood decades of scrutiny from cryptographers, mathematicians, and security researchers worldwide. Despite countless attempts to find weaknesses, AES remains unbroken when properly implemented. This resilience is exactly why organizations worldwide trust it with their most sensitive information, and why regulatory frameworks like PCI DSS mandate its use.
What is PCI DSS?
The Payment Card Industry Data Security Standard, better known as PCI DSS, is a comprehensive set of security requirements designed to ensure that all companies that accept, process, store, or transmit credit card information maintain a secure environment. Established in 2004 by major payment card brands; Visa, Mastercard, American Express, Discover, and JCB, PCI DSS has evolved into the definitive framework for payment security.
If you accept credit or debit cards in any capacity, PCI DSS applies to you. It doesn't matter if you're processing five transactions a month or five million. The standard scales based on transaction volume, with different validation requirements for different merchant levels, but compliance itself is mandatory across the board.
The current version of PCI DSS (version 4.0 as of 2024) includes 12 core requirements organized into six major objectives:
Build and Maintain a Secure Network and Systems
- Install and maintain network security controls
- Apply secure configurations to all system components
Protect Account Data
- Protect stored account data
- Protect cardholder data with strong cryptography during transmission over open, public networks
Maintain a Vulnerability Management Program
- Protect systems and networks from malicious software
- Develop and maintain secure systems and software
Implement Strong Access Control Measures
- Restrict access to cardholder data by business need-to-know
- Identify users and authenticate access to system components
- Restrict physical access to cardholder data
Regularly Monitor and Test Networks
- Log and monitor all access to system components and cardholder data
- Test security of systems and networks regularly
Maintain an Information Security Policy
- Support information security with organizational policies and programs
These requirements are contractual obligations that businesses agree to when they decide to accept payment cards. The payment card brands enforce compliance through a combination of self-assessment questionnaires, network scans, and on-site audits depending on your merchant level. Larger organizations processing millions of transactions undergo rigorous annual audits by qualified security assessors, while smaller merchants typically complete self-assessment questionnaires.
PCI DSS exists because the cost of payment card fraud is staggering. According to industry reports, card fraud losses exceed billions of dollars annually worldwide. By establishing a baseline of security controls, PCI DSS aims to reduce this fraud, protect consumers, and maintain trust in electronic payment systems. For businesses, compliance entails protecting your customers, your reputation, and your ability to accept card payments.
Why is AES Essential for Identity and Access Security?
Protecting cardholder data is made up of two critical aspects: protecting data at rest (stored data) and data in transit (data being transmitted). AES plays a pivotal role in both scenarios, but its importance extends far beyond just encrypting credit card numbers.
Identity and access management systems are the gatekeepers of your organization's most sensitive resources. These systems determine who can access what, when, and under what circumstances. The credentials, tokens, and authentication data they manage are incredibly valuable targets for cybercriminals. If an attacker gains access to this information, they don't just steal data, they can impersonate legitimate users, move laterally through your network, and cause damage that persists long after the initial breach.
AES encryption protects these identity components in several critical ways. First, it secures stored credentials. Even if your database is compromised, properly encrypted passwords and authentication tokens remain useless to attackers without the encryption keys. This is particularly important in payment environments where access credentials might grant entry to systems containing cardholder data.
Second, AES protects authentication sessions. When users log into systems, session tokens are generated to maintain their authenticated state. These tokens, if intercepted, could allow attackers to hijack active sessions. By encrypting these tokens with AES, you ensure that even intercepted session data cannot be exploited.
Third, AES safeguards privileged access credentials. In any payment environment, certain users need elevated privileges to manage systems, configure security controls, or access sensitive data. These privileged accounts are prime targets for attackers. AES encryption of privileged credentials adds a critical layer of protection, ensuring that even if systems are compromised, the most powerful access credentials remain protected.
The strength of AES also provides long-term security. In the context of identity and access security, you're not just protecting data for today; you're protecting it for years to come. Stored credentials might remain in backup systems for extended periods, and you need assurance that they'll remain secure even as computing power advances. AES's computational complexity provides this assurance.
Furthermore, AES encryption supports compliance with the principle of least privilege, a core concept in both PCI DSS and identity security. By encrypting data at granular levels, you can ensure that even users with access to encrypted storage cannot read sensitive information without proper decryption credentials. This creates layers of protection that align perfectly with PCI DSS requirements for restricting access to cardholder data.
How Does It Work?
AES is what cryptographers call a symmetric block cipher. "Symmetric" means it uses the same key for both encryption and decryption, unlike asymmetric encryption where you'd use different keys. "Block cipher" means it encrypts data in fixed-size blocks (128 bits for AES) rather than one bit at a time.
Here's the simplified process:
Key Expansion: The encryption key you provide (whether 128, 192, or 256 bits) goes through a process called key expansion, which generates a series of round keys. These round keys are used in the subsequent encryption rounds. For 128-bit encryption, AES performs 10 rounds; 192-bit uses 12 rounds; and 256-bit uses 14 rounds.
Initial Round: The plaintext (your original data) is combined with the first round key using a simple XOR operation. This initial step begins the transformation process.
Main Rounds: Each main round consists of four distinct operations:
- SubBytes: Each byte in the block is replaced with another byte according to a predetermined substitution table. This creates confusion in the data.
- ShiftRows: The rows of the data block are shifted cyclically, redistributing bytes across the block.
- MixColumns: Each column of the block undergoes a mathematical transformation, mixing the bytes within columns.
- AddRoundKey: The transformed data is combined with the round key for that specific round.
Final Round: The last round omits the MixColumns step and performs SubBytes, ShiftRows, and AddRoundKey operations to produce the final ciphertext.
The result is data that appears completely random and bears no resemblance to the original information. Without the correct key, reversing this process is computationally infeasible.
In a PCI DSS context, AES might be implemented in several ways. For data at rest, you might use full-disk encryption on servers storing cardholder data, or database-level encryption for specific fields containing sensitive information. For data in transit, AES typically operates within protocols like TLS (Transport Layer Security), encrypting payment information as it travels between your point-of-sale system and your payment processor.
Modern implementations often use AES in specific modes of operation such as AES-GCM (Galois/Counter Mode) or AES-CBC (Cipher Block Chaining), which add additional security features like authentication or initialization vectors to prevent patterns from emerging in encrypted data.
The key management aspect is equally critical. The strength of AES is meaningless if encryption keys are poorly managed. Keys must be generated using cryptographically secure random number generators, stored separately from encrypted data, rotated regularly, and protected with the same rigor as the data they encrypt. PCI DSS includes specific requirements for key management, recognizing that the entire security model depends on keeping these keys secure.
Why Does It Matter in PCI DSS Compliance?
PCI DSS Requirement 3.5.1 is explicit: "Cryptographic keys used to encrypt/decrypt cardholder data must be stored in one (or more) of the following forms at all times: Encrypted with a key-encrypting key, Within a secure cryptographic device, As at least two full-length key components or key shares." But the standard goes further, with Requirement 4.2 stating that strong cryptography must be used to protect cardholder data during transmission over open, public networks.
While PCI DSS doesn't exclusively mandate AES, it requires "strong cryptography" with industry-accepted algorithms, key strengths, and key management practices. AES has become the de facto standard for meeting these requirements because it checks every box: it's widely recognized, thoroughly vetted, extremely secure, and efficiently implemented.
Here's why AES specifically matters for PCI DSS compliance:
Meets the Strong Cryptography Standard: PCI DSS requires encryption that would take significant processing power and time to break. AES, particularly with 256-bit keys, exceeds this threshold by an enormous margin. Using AES demonstrates to auditors and payment brands that you're implementing genuinely robust protection.
Protects Data at Rest: PCI DSS Requirement 3.4 addresses the protection of stored cardholder data. Whether you're storing primary account numbers (PANs) in databases, log files, or backup systems, AES encryption renders this data unreadable to anyone who doesn't possess the decryption keys. This is crucial because many breaches involve attackers gaining access to stored data rather than intercepting transmissions.
Secures Data in Transit: When cardholder data travels across networks, from your e-commerce site to your payment gateway, or from your point-of-sale terminal to your acquirer, it's vulnerable to interception. AES within protocols like TLS creates secure tunnels that protect this data as it moves, satisfying PCI DSS requirements for transmission security.
Supports Scope Reduction: One of the most valuable aspects of strong encryption is its potential to reduce your PCI DSS scope. If cardholder data is encrypted using validated encryption methods, systems that only handle encrypted data may be removed from scope. This can significantly reduce compliance costs and complexity. However, this requires proper implementation and documentation.
Enables Secure Key Management: PCI DSS includes detailed requirements for cryptographic key management (Requirements 3.6 and 3.7). AES's mature ecosystem includes robust key management solutions that help organizations meet these requirements, including secure key generation, distribution, storage, rotation, and destruction.
Demonstrates Due Diligence: In the event of a breach, your use of strong encryption like AES demonstrates that you took reasonable security measures. While it doesn't absolve you of responsibility, it shows regulators, payment brands, and customers that you implemented industry-standard protections.
Facilitates Compliance Validation: During PCI DSS assessments, auditors will examine your encryption implementations. Using well-known, widely accepted algorithms like AES makes validation straightforward. Auditors understand AES, know how to verify its proper implementation, and recognize it as meeting compliance requirements.
It's important to understand that simply using AES doesn't guarantee compliance. The encryption must be properly implemented with appropriate key lengths, secure modes of operation, and robust key management. PCI DSS auditors will verify not just that you're using encryption, but that you're using it correctly throughout the cardholder data environment.
Why is It Important in Your Business?
Beyond regulatory compliance, AES encryption delivers tangible business value that impacts your bottom line and competitive position. Let's explore the practical business reasons why AES matters.
Customer Trust and Brand Reputation: Data breaches make headlines, and customers remember. When personal payment information is compromised, the reputational damage can persist for years. Implementing strong AES encryption demonstrates your commitment to security, giving customers confidence to transact with you. In competitive markets, this trust can be a differentiator.
Financial Protection: The direct costs of a breach are staggering. According to industry research, the average cost of a data breach runs into millions of dollars when you factor in forensic investigation, notification costs, credit monitoring for affected customers, legal fees, and regulatory fines. AES encryption significantly reduces the likelihood that stolen data can be exploited, potentially saving your business from catastrophic financial losses.
Business Continuity: Breaches don't just cost money, they disrupt operations. Compromised systems must be taken offline, investigated, cleaned, and rebuilt. Payment processing may be suspended. Customer service gets overwhelmed. AES encryption helps prevent these disruptions by protecting your data even if other security controls fail.
Competitive Advantage: Many contracts, particularly with larger enterprises or government entities, require vendors to demonstrate robust security practices. Strong encryption using AES can help you win business, qualify for RFPs, and maintain partnerships with security-conscious organizations.
Reduced Insurance Premiums: Cyber insurance has become essential for businesses handling payment data. Insurers increasingly scrutinize security practices when underwriting policies. Demonstrating proper AES implementation can lead to lower premiums and better coverage terms.
Simplified Compliance Management: AES encryption addresses multiple compliance frameworks simultaneously. Beyond PCI DSS, standards like GDPR, HIPAA, and various state privacy laws recognize encryption as a critical control. Implementing AES once serves multiple compliance needs, reducing administrative burden.
Operational Efficiency: Modern AES implementations are highly efficient, adding minimal performance overhead. You get enterprise-grade security without sacrificing system speed or user experience. This is particularly important for real-time payment processing where delays are unacceptable.
Future-Proofing: Security threats evolve constantly, but AES has proven remarkably resilient. By implementing AES today, you're building on a foundation that will remain secure for years to come, protecting your long-term investments in payment infrastructure.
Vendor and Partner Confidence: Payment processors, acquiring banks, and merchant service providers all want to work with businesses that take security seriously. Strong encryption practices facilitate these relationships and can lead to better processing rates and terms.
The business case is clear: AES encryption is an investment that pays dividends through risk reduction, competitive advantage, and operational resilience. It's a strategic security control that supports business growth.
What are the Consequences of Non-Compliance?
Failing to implement adequate encryption like AES or achieve PCI DSS compliance carries severe consequences that extend far beyond simple fines. Let's examine what's actually at stake.
Financial Penalties: Payment card brands impose fines for non-compliance that can range from $5,000 to $100,000 per month, depending on the violation's severity and duration. For significant breaches resulting from non-compliance, these fines can escalate dramatically. Acquiring banks may also levy their own penalties, further compounding the financial impact.
Increased Transaction Fees: Non-compliant merchants often face elevated transaction processing fees. Payment processors charge premium rates to offset the increased risk of handling transactions for businesses without adequate security controls. Over time, these increased fees can amount to substantial costs.
Loss of Payment Processing Privileges: This is the nuclear option, but it happens. Payment brands can prohibit non-compliant merchants from accepting their cards. For most businesses, losing the ability to process credit card payments is an existential threat. Even temporary suspension can cause irreparable damage.
Breach-Related Costs: If inadequate encryption contributes to a breach, you'll face a cascade of expenses: forensic investigation (often $50,000-$200,000 or more), notification costs (several dollars per affected customer), credit monitoring services, legal fees, regulatory response, and potential lawsuits from affected customers. These costs quickly reach millions of dollars for significant breaches.
Regulatory Enforcement Actions: Beyond payment brand penalties, regulators may pursue enforcement actions. State attorneys general have become increasingly aggressive in pursuing data breach cases. The Federal Trade Commission has authority to act against businesses with inadequate security practices. International regulators under frameworks like GDPR can impose fines reaching 4% of global annual revenue.
Legal Liability: Customers affected by breaches increasingly file class-action lawsuits. While class actions have had mixed success, they create legal expenses, management distraction, and additional reputational damage. Even if you ultimately prevail, defending these cases is costly and time-consuming.
Brand Damage: The reputational cost of a breach can eclipse direct financial losses. Customer trust, once broken, is difficult to rebuild. Studies show that businesses suffering breaches experience customer attrition, reduced customer lifetime value, and difficulty acquiring new customers. The brand damage can persist for years.
Operational Disruption: Breach response requires enormous resources. IT teams must conduct forensics, rebuild compromised systems, and implement enhanced controls. Management attention shifts to crisis response. Normal business operations suffer. For some businesses, particularly smaller organizations, this disruption proves fatal.
Partner and Vendor Consequences: Breaches affect your entire business ecosystem. Partners may terminate relationships. Suppliers may demand enhanced security guarantees or refuse to extend credit. The ripple effects extend throughout your value chain.
Insurance Implications: Cyber insurance policies typically include compliance clauses. Non-compliance with PCI DSS may void coverage, leaving you financially exposed precisely when you need protection most. Future insurance becomes more expensive and difficult to obtain.
Personal Consequences for Leadership: In some cases, executives and board members have faced personal liability for security failures. Shareholders have sued corporate leadership for breach-related losses. Professional reputations can be permanently damaged.
Market Value Impact: For publicly traded companies, breaches typically result in stock price declines. The market punishes companies that demonstrate inadequate security practices, and recovery can take quarters or years.
The sobering reality is that the cost of implementing proper AES encryption and achieving PCI DSS compliance is a fraction of the cost of non-compliance. Organizations that treat security as an afterthought inevitably discover, usually at the worst possible moment, that cutting corners on encryption was a catastrophically expensive decision.
FAQs
Q: Is AES-128 sufficient for PCI DSS compliance, or should I use AES-256?
A: Both AES-128 and AES-256 are acceptable for PCI DSS compliance, as both meet the standard's requirements for strong cryptography. However, many organizations implement AES-256 as a best practice, particularly for long-term data storage. The practical security difference is minimal. Both would take longer than the age of the universe to crack with current technology but AES-256 provides an extra margin of future-proofing as computing power increases.
Q: Does encrypting cardholder data with AES mean I don't need other PCI DSS controls?
A: Absolutely not. While AES encryption is critical, PCI DSS is a comprehensive framework with 12 main requirements covering network security, access controls, monitoring, testing, and policies. Encryption addresses specific requirements around protecting stored and transmitted data, but you still need firewalls, access controls, vulnerability management, logging, and all other applicable controls. Think of encryption as one essential component of a complete security program.
Q: Can I use open-source AES implementations for PCI DSS compliance?
A: Yes, reputable open-source AES implementations (like those in OpenSSL or cryptographic libraries from established providers) are acceptable for PCI DSS compliance, provided they're properly configured and maintained. What matters is that the implementation correctly follows the AES specification, uses appropriate key lengths and modes, and includes proper key management. Your QSA (Qualified Security Assessor) will verify the implementation meets standards regardless of whether it's open-source or commercial.
Q: How often do I need to rotate AES encryption keys?
A: PCI DSS Requirement 3.6.4 addresses cryptographic key changes. While the standard doesn't mandate a specific rotation schedule, it requires key changes when keys have reached the end of their cryptoperiod as defined by your key management procedures, when key integrity has been weakened, or when an employee with key knowledge leaves the company. Many organizations rotate encryption keys annually or when personnel changes occur, but your specific requirements depend on your risk assessment and key management policies.
Q: If I store only the last four digits of card numbers, do I still need AES encryption?
A: The last four digits alone don't constitute full cardholder data and don't require encryption. However, if you store any other sensitive authentication data (full track data, CAV2/CVC2/CVV2/CID, or PINs), that information must be encrypted. Additionally, if you store truncated PANs alongside other data that could be used to reconstruct full card numbers, encryption may still be necessary. Always consult your QSA about your specific data environment.
Q: Does AES encryption slow down transaction processing?
A: Modern AES implementations are highly optimized and add minimal latency to transaction processing. Most processors include hardware acceleration for AES, making encryption and decryption nearly instantaneous. The performance impact is generally negligible—measured in milliseconds and far outweighed by network latency and other processing steps. Proper implementation should have no noticeable impact on customer experience.
Q: What happens if my AES encryption keys are compromised?
A: Key compromise is a serious incident requiring immediate response. You must immediately rotate the affected keys, re-encrypt all data that was protected by the compromised keys, investigate how the compromise occurred, implement controls to prevent recurrence, and notify your acquiring bank and payment brands if cardholder data was potentially exposed. This is precisely why PCI DSS requires robust key management practices including secure storage, strict access controls, and separation of duties.
Q: Can I decrypt cardholder data for analytics or reporting purposes?
A: Yes, but with strict controls. PCI DSS allows decryption for legitimate business purposes, but requires that decrypted data be protected with equivalent controls, access be restricted based on business need-to-know, and all access be logged and monitored. Many organizations use tokenization instead, replacing sensitive card numbers with non-sensitive tokens for analytics, avoiding the need to decrypt actual cardholder data.
Conclusion
In the complex landscape of payment security, AES encryption stands as a fundamental pillar protecting the cardholder data that flows through your business every day. It's not merely a technical requirement buried in compliance documentation; it's a proven, battle-tested defense against the very real threats that target payment environments worldwide.
The intersection of AES and PCI DSS compliance represents more than regulatory obligation. It represents a commitment to your customers, a protection of your business assets, and a foundation for sustainable growth in an increasingly digital economy. Every encrypted transaction, every protected database field, every secured transmission channel reinforces the trust that makes electronic commerce possible.
Understanding AES and implementing it correctly within the PCI DSS framework requires expertise, diligence, and ongoing commitment. The threat landscape evolves continuously, compliance requirements become more sophisticated, and the stakes continue to rise. But the core principle remains constant: strong encryption using proven algorithms like AES is non-negotiable for any organization handling payment card data.
The question is not whether you can afford to implement robust AES encryption and achieve PCI DSS compliance. The question is whether you can afford not to. The consequences of inadequate security, financial, reputational, and operational far exceed the investment required to get it right.
As you evaluate your current security posture, assess your compliance status, and plan your path forward, remember that you don't have to navigate these challenges alone.
Contact Regulance today to schedule a consultation and discover how we can help you transform PCI DSS compliance from a burden into a competitive advantage.
Don't wait for a breach to discover the gaps in your security. Let Regulance help you build the robust, compliant payment security infrastructure your business deserves.