What is a SOC Audit? The Complete Guide to Compliance and Business Credibility


Introduction
When potential clients evaluate service providers today, security and compliance credentials often determine who gets the contract and who gets left behind. A SOC audit has emerged as the gold standard for organizations seeking to prove their commitment to security, reliability, and operational excellence.
A SOC audit provides independent verification that your organization's internal controls are designed and operating effectively, giving clients the assurance they need when entrusting you with their sensitive information and critical business functions. For service organizations handling everything from payroll processing to cloud hosting, this third-party validation is often a prerequisite for securing enterprise contracts and maintaining competitive advantage.
But SOC audit benefits extend beyond client acquisition. These comprehensive evaluations help organizations identify operational weaknesses, strengthen internal controls, and demonstrate compliance with industry standards and regulatory requirements. Whether you're a SaaS provider, data center operator, or professional services firm, understanding how a SOC audit works and which type best suits your needs is crucial for long-term business success.
This comprehensive guide will walk you through everything you need to know about SOC audits, from the different types available to the preparation process and ongoing benefits for your organization.
What is a SOC Audit?
A SOC audit, or Service Organization Control audit, is a comprehensive examination of an organization's internal controls related to security, availability, processing integrity, confidentiality, and privacy. Think of it as a thorough health check for your business operations, conducted by independent auditors who assess how well your organization protects client data and maintains operational excellence.

The SOC audit framework was developed by the American Institute of Certified Public Accountants (AICPA) to provide standardized reporting on service organizations' control activities. These audits are particularly crucial for companies that provide services to other businesses, such as cloud providers, data centers, payroll processors, and software-as-a-service (SaaS) companies.
What makes SOC audits unique is their focus on trust services criteria the fundamental principles that underpin secure and reliable business operations. Unlike generic security assessments, SOC audits follow established standards that are recognized globally, making them invaluable for businesses operating in multiple jurisdictions or serving enterprise clients with strict compliance requirements.
How Does a SOC Audit Work?
The SOC audit process is methodical and thorough, typically unfolding over several months. Understanding this process helps organizations prepare effectively and set realistic expectations.
Planning and Scoping Phase
The journey begins with defining the scope of the audit. This involves identifying which systems, processes, and controls will be examined. The auditor works closely with your organization to understand your business model, identify relevant trust services criteria, and establish the audit period. This phase is crucial because it sets the foundation for everything that follows.
Risk Assessment and Control Identification
Next, auditors conduct a comprehensive risk assessment to understand potential threats to your operations. They identify the controls you've implemented to mitigate these risks and evaluate whether these controls are appropriately designed. This includes policies, procedures, and human processes that contribute to your overall control environment.
Testing and Evidence Collection
The heart of the SOC audit involves rigorous testing of your controls. Auditors examine evidence, interview personnel, observe processes in action, and verify that controls are operating effectively. For Type II audits, this testing occurs over a specified period, typically 6-12 months, to ensure controls are consistently effective over time.
Documentation and Reporting
Finally, auditors compile their findings into a detailed SOC report. This document becomes your organization's credential, demonstrating to clients and stakeholders that your controls have been independently verified. The report includes the auditor's opinion on the design and operating effectiveness of your controls, along with any identified deficiencies and management responses.
What is the Difference Between SOC 1, SOC 2, and SOC 3?
Understanding the distinctions between SOC 1, SOC 2, and SOC 3 reports is essential for choosing the right audit type for your organization's needs and objectives.
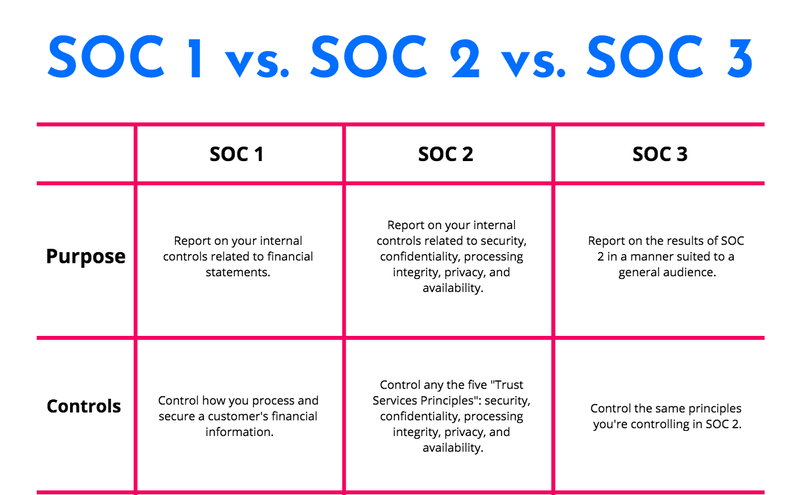
SOC 1: Financial Reporting Focus
SOC 1 audits focus specifically on controls that could impact your clients' financial reporting. These are designed for service organizations whose activities directly affect their clients' internal control over financial reporting. For example, a payroll processing company or a cloud provider hosting financial applications would typically undergo SOC 1 audits.
SOC 1 reports are intended for a limited audience; primarily your clients' auditors and management teams who need to understand how your controls might affect their financial statements. The controls tested are directly related to financial processes and reporting accuracy.
SOC 2: Security and Operational Excellence
SOC 2 audits take a broader view, examining controls related to security, availability, processing integrity, confidentiality, and privacy; the five trust services criteria. This makes SOC 2 the go-to choice for most technology service providers, cloud companies, and organizations that handle sensitive data.
What sets SOC 2 apart is its flexibility. Organizations can choose which of the five trust services criteria are relevant to their operations. A cloud storage provider might focus on security and availability, while a healthcare technology company might include privacy and confidentiality as well.
SOC 2 reports come in two varieties: Type I (point-in-time assessment of control design) and Type II (assessment of control design and operating effectiveness over a period of time). Type II reports are generally more valuable because they demonstrate sustained control effectiveness.
SOC 3: Public-Facing Trust
SOC 3 reports are the public version of SOC 2 reports. They contain the same trust services criteria but present the information in a format suitable for general distribution. Think of SOC 3 as the marketing-friendly version; you can share these reports on your website, include them in sales presentations, and use them in marketing materials without revealing sensitive details about your operations.
While SOC 3 reports are less detailed than SOC 2 reports, they serve an important purpose in building public trust and can be particularly valuable for organizations that serve a broad customer base or operate in consumer-facing markets.
Who Performs a SOC Audit?
SOC audits must be conducted by independent Certified Public Accountants (CPAs) who specialize in attestation services. These are professionals with specific expertise in evaluating internal controls and assessing operational risks.
Qualifications and Expertise
The auditors conducting your SOC audit should have extensive experience with service organization controls and a deep understanding of your industry. Many specialize in specific sectors, such as technology, healthcare, or financial services, bringing valuable industry knowledge to the audit process.
These professionals must maintain their independence from your organization, ensuring that their assessment remains objective and credible. They're bound by professional standards and ethical requirements that govern their conduct and the quality of their work.
Choosing the Right Audit Firm
Selecting the right audit firm is crucial for a successful SOC audit experience. Look for firms with proven experience in your industry, strong references from similar organizations, and a track record of helping clients achieve their compliance objectives. The best audit firms don't just evaluate your controls—they provide valuable insights and recommendations for improvement.
Consider factors such as the firm's approach to the audit process, their communication style, and their ability to work within your timeline and budget constraints. Remember, this is likely to be an ongoing relationship, as most organizations undergo annual SOC audits to maintain their compliance posture.
What are SOC Controls?
SOC controls are the policies, procedures, and activities that organizations implement to achieve the trust services criteria. These controls form the backbone of your SOC audit and demonstrate your commitment to protecting client interests.
Security Controls
Security controls protect against unauthorized access to your systems and data. These include access management procedures, network security measures, vulnerability management programs, and incident response protocols. Effective security controls ensure that only authorized individuals can access sensitive information and that threats are promptly identified and addressed.
Availability Controls
Availability controls ensure that your systems and services remain accessible when needed. This includes redundancy measures, backup and recovery procedures, capacity management, and monitoring systems. For service providers, availability is often critical to client operations, making these controls essential.
Processing Integrity Controls
Processing integrity controls ensure that system processing is complete, valid, accurate, and timely. These controls prevent errors, detect processing failures, and ensure that data is handled correctly throughout its lifecycle. They're particularly important for organizations that process transactions or handle data transformations.
Confidentiality and Privacy Controls
Confidentiality controls protect sensitive information from unauthorized disclosure, while privacy controls ensure that personal information is collected, used, retained, and disclosed in accordance with applicable privacy laws and regulations. These controls are increasingly important as privacy regulations become more stringent worldwide.
Benefits of SOC Audit
The benefits of SOC audits extend far beyond compliance, creating tangible value for organizations across multiple dimensions.
Enhanced Market Credibility
SOC compliance serves as a powerful differentiator in competitive markets. When prospects are evaluating service providers, SOC reports provide independent validation of your control environment. This third-party assurance can be the deciding factor in winning new business, particularly with enterprise clients who have strict vendor assessment requirements.
Risk Management and Operational Improvement
The SOC audit process itself drives operational improvements by identifying control deficiencies and opportunities for enhancement. Many organizations find that preparing for and undergoing SOC audits helps them mature their control environment and improve overall operational effectiveness.
Regulatory Compliance Support
While SOC audits aren't regulatory requirements themselves, they often support compliance with various regulations and industry standards. Many regulatory frameworks recognize SOC reports as evidence of effective controls, potentially reducing the scope of other compliance activities.
Cost Efficiencies
SOC reports can streamline vendor assessments for your clients, reducing the need for individual security questionnaires and site visits. This efficiency benefits both you and your clients, making the business relationship more productive and cost-effective.
Insurance and Financial Benefits
Many organizations find that SOC compliance positively impacts their cyber insurance premiums and terms. Insurance providers often view SOC-compliant organizations as lower risk, potentially resulting in better coverage options and reduced costs.
How to Prepare for a SOC Audit
Successful SOC audit preparation requires careful planning, stakeholder alignment, and systematic control implementation. Starting early and taking a structured approach can make the difference between a smooth audit experience and a stressful scramble.
Conduct a Readiness Assessment
Begin by conducting an honest assessment of your current control environment. Map your existing controls against the relevant trust services criteria and identify gaps that need to be addressed. This internal assessment helps you understand the scope of work required and develop a realistic timeline for audit preparation.
Develop and Document Policies and Procedures
Comprehensive documentation is the foundation of SOC compliance. Develop clear, detailed policies and procedures that address each relevant control area. These documents should be more than just compliance exercises; they should reflect how your organization actually operates and provide practical guidance for your team members.
Implement Control Activities
Controls must be more than just written policies; they need to be actively implemented and operating effectively. This might involve deploying new security tools, implementing monitoring procedures, establishing review processes, or training staff on new protocols.
Establish Evidence Collection Processes
SOC audits require substantial evidence of control operation. Establish systematic processes for collecting and organizing this evidence throughout the audit period. This includes maintaining logs, preserving documentation of control activities, and ensuring that evidence is readily accessible when auditors need it.
Engage Stakeholders Early
SOC audit success requires collaboration across multiple departments and functions. Engage key stakeholders early in the process, ensuring they understand their roles and responsibilities. This cross-functional alignment is crucial for maintaining controls and supporting the audit process.
How Regulance AI Can Help You Prepare for a SOC Audit
Modern SOC audit preparation can be complex and resource-intensive, but artificial intelligence is revolutionizing how organizations approach compliance. Regulance AI offers innovative solutions that streamline the preparation process and enhance ongoing compliance management.
Automated Control Monitoring
Regulance AI can continuously monitor your control environment, automatically collecting evidence and identifying potential issues before they become audit findings. This proactive approach reduces manual effort while improving control effectiveness and audit readiness.
Gap Analysis and Remediation Planning
Advanced AI algorithms can analyze your current controls against SOC requirements, identifying gaps and recommending specific remediation actions. This targeted approach helps you focus your preparation efforts on the areas that matter most.
Documentation and Evidence Management
AI-powered platforms can help organize and maintain the extensive documentation required for SOC audits. From policy management to evidence collection, these tools ensure that information is properly categorized, version-controlled, and accessible when needed.
Risk Assessment and Prioritization
Regulance AI can help identify and assess risks across your organization, providing data-driven insights that support control design and implementation decisions. This intelligence helps you build a more effective and efficient control environment.
Ongoing Compliance Monitoring
Beyond initial audit preparation, AI solutions provide continuous monitoring capabilities that help maintain compliance between audits. This ongoing vigilance reduces the risk of control failures and makes subsequent audits more efficient.
Frequently Asked Questions
How long does a SOC audit take?
The duration of a SOC audit varies depending on the scope and complexity of your organization, but most SOC 2 Type II audits take 3-6 months from planning to report issuance. The actual fieldwork portion typically lasts 2-4 weeks, while the planning and reporting phases extend the overall timeline.
How much does a SOC audit cost?
SOC audit costs vary significantly based on factors such as organizational size, complexity, scope, and the audit firm chosen. Costs typically range from $15,000 to $100,000 or more for comprehensive SOC 2 Type II audits. While this represents a significant investment, most organizations find that the business benefits justify the cost.
Can small businesses get SOC audits?
Absolutely. While SOC audits were once primarily the domain of large enterprises, increasing numbers of small and medium-sized businesses are pursuing SOC compliance to compete for enterprise clients and demonstrate their commitment to security and operational excellence.
What happens if controls fail during a SOC audit?
Control failures don't necessarily mean audit failure. Auditors will note deficiencies in their report, and organizations have the opportunity to provide management responses explaining how they plan to address these issues. Many successful SOC reports include some findings; what matters is how organizations respond to and remediate these issues.
How often should SOC audits be performed?
Most organizations pursue annual SOC audits to maintain current compliance status. However, the frequency can vary based on client requirements, industry standards, and business objectives. Some organizations opt for more frequent audits during periods of significant change or growth.
Do SOC reports expire?
While SOC reports don't technically expire, their value diminishes over time. Most clients and stakeholders expect SOC reports to be no more than 12-18 months old. This expectation drives the common practice of annual SOC audits.
Conclusion
SOC audits represent a strategic investment in your organization's credibility, operational excellence, and competitive positioning. As businesses become increasingly reliant on service providers and data security concerns continue to grow, SOC compliance has evolved from a nice-to-have into a business imperative.
The journey to SOC compliance may seem daunting, but the benefits; enhanced market credibility, improved operational controls, streamlined client assessments, and competitive differentiation make it a worthwhile investment for organizations serious about sustainable growth.
Success in SOC auditing requires careful preparation, ongoing commitment, and the right combination of people, processes, and technology. Whether you're considering your first SOC audit or looking to optimize your existing compliance program, remember that this is a journey of continuous improvement rather than a one-time destination.
By embracing SOC compliance as a core business strategy rather than just a regulatory requirement, organizations can transform what might seem like a burden into a powerful competitive advantage. In today's trust-driven economy, that advantage can make all the difference in achieving your business objectives and building lasting client relationships.
The investment in SOC compliance pays dividends not just in client trust and business growth, but in the operational discipline and risk management maturity that comes with maintaining effective controls. As you embark on or continue your SOC journey, remember that you're building the foundation for sustainable business success in an increasingly complex and interconnected world.
Build trust with confidence; let Regulance AI guide you through SOC audit compliance excellence.