What Is a Cybersecurity Maturity Assessment and How Can It Strengthen Your Digital Defense?


Introduction
The digital transformation has fundamentally reshaped how organizations operate, bringing unprecedented opportunities alongside equally significant risks. Cyber threats have evolved from nuisance disruptions to existential business challenges, with the average cost of a data breach now exceeding $4.45 million globally. Despite these sobering statistics, a critical question remains unanswered in boardrooms worldwide: How mature is our cybersecurity program?
Understanding cybersecurity maturity has become essential for organizations seeking to protect their assets, maintain customer trust, and ensure regulatory compliance. Unlike traditional security audits that provide snapshot assessments, cybersecurity maturity represents your organization's capability to consistently prevent, detect, respond to, and recover from cyber threats. It measures not just what security tools you have, but how effectively you use them and how well security is embedded into your organizational culture.
However, organizations cannot defend what they cannot measure. Without a clear understanding of cybersecurity maturity levels, companies often invest resources in the wrong areas, leaving critical vulnerabilities exposed while over-investing in less important controls. This misalignment can prove catastrophic when sophisticated threat actors exploit these gaps.
This comprehensive guide demystifies cybersecurity maturity assessments, providing you with actionable insights to evaluate your security posture, identify improvement opportunities, and build a resilient defense strategy.
What is a Cybersecurity Maturity Assessment?
A cybersecurity maturity assessment is a systematic evaluation process that measures how well an organization's security practices, policies, and technologies align with industry best practices and regulatory requirements.
Unlike a simple security audit or vulnerability scan, a maturity assessment takes a holistic view of your cybersecurity program. It examines not just your technical defenses, but also your governance structures, risk management processes, incident response capabilities, and the human factors that often make or break security efforts.
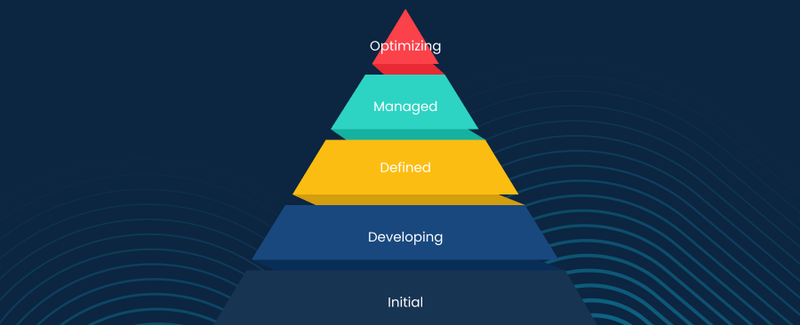
The assessment typically evaluates your organization against an established maturity model, which defines progressive levels of capability. Most models use a five-level scale:
Level 1 - Initial/Ad Hoc: Security practices are reactive, inconsistent, and poorly documented. Organizations at this level typically respond to threats as they occur with no formal processes in place.
Level 2 - Developing: Basic security policies exist, but implementation is inconsistent. There's awareness of cybersecurity needs, but practices haven't been standardized across the organization.
Level 3 - Defined: Security processes are documented, standardized, and communicated throughout the organization. There's a clear security strategy, though it may not be optimally implemented everywhere.
Level 4 - Managed: Security is proactive and data-driven. The organization continuously monitors metrics, manages risks quantitatively, and adapts based on threat intelligence.
Level 5 - Optimized: Cybersecurity is embedded in organizational culture. Continuous improvement is the norm, with advanced automation, predictive capabilities, and industry-leading practices in place.
Understanding your current maturity level provides a baseline for improvement and helps prioritize security investments where they'll have the greatest impact.
Components of Cybersecurity Maturity Assessment
A comprehensive cybersecurity maturity assessment examines multiple dimensions of your security program. While specific frameworks may vary, most assessments evaluate these core components:
Governance and Risk Management
This component evaluates how cybersecurity is governed at the organizational level. It looks at board-level oversight, risk appetite definition, policy frameworks, and how security aligns with business objectives. Strong governance ensures that cybersecurity is a business responsibility owned at the highest levels.
Asset Management
This component assesses how well your organization identifies, classifies, and manages its digital assets; from hardware and software to data and intellectual property. Mature organizations maintain comprehensive, up-to-date asset inventories and understand the criticality and interdependencies of their systems.
Access Control and Identity Management
This examines how your organization manages user identities, authentication mechanisms, and authorization processes. It evaluates whether you're following the principle of least privilege, implementing multi-factor authentication, and properly managing user lifecycles from onboarding to offboarding.
Threat Detection and Monitoring
How quickly can you detect a security incident? This component assesses your monitoring capabilities, security information and event management (SIEM) systems, threat intelligence integration, and the effectiveness of your security operations center (if you have one).
Incident Response and Recovery
When a breach occurs and statistics suggest it's a matter of when, not if; how prepared are you? This component evaluates your incident response plans, testing frequency, communication protocols, and business continuity capabilities. It also assesses how well you learn from past incidents to prevent future ones.
Data Protection and Privacy
With regulations like GDPR, CCPA, and numerous industry-specific requirements, data protection has never been more critical. This component examines encryption practices, data classification, privacy controls, and compliance with relevant regulations.
Third-Party Risk Management
This component assesses how you vet, monitor, and manage cybersecurity risks from suppliers, contractors, and other external parties who have access to your systems or data.
Security Awareness and Training
This component evaluates your security awareness programs, training effectiveness, phishing simulation exercises, and overall security culture. Mature organizations recognize that every employee is part of the security team.
Application and Infrastructure Security
This technical component examines secure development practices, vulnerability management, patch management, network segmentation, and the security of both on-premises and cloud infrastructure.
Compliance and Audit
Finally, this component assesses how well your organization maintains compliance with relevant regulations and standards, manages audit processes, and demonstrates security effectiveness to stakeholders and regulators.
How to Conduct a Cybersecurity Maturity Assessment
Conducting an effective cybersecurity maturity assessment requires careful planning and systematic execution. Here's a step-by-step approach to get you started:
Step 1: Define Your Scope and Objectives
Begin by determining what you want to assess and why. Are you focusing on your entire organization or specific business units? Are you preparing for regulatory compliance, responding to a board mandate, or planning security investments? Clear objectives will guide the entire assessment process and ensure you get actionable results.
Step 2: Select an Appropriate Framework
Choose a maturity model that aligns with your industry, regulatory requirements, and organizational needs. Popular frameworks include the NIST Cybersecurity Framework, CMMC (Cybersecurity Maturity Model Certification) for defense contractors, ISO/IEC 27001, and C2M2 (Cybersecurity Capability Maturity Model) for critical infrastructure sectors. Each framework has its strengths, so select one that resonates with your specific context.
Step 3: Assemble Your Assessment Team
A thorough assessment requires diverse perspectives. Include representatives from IT security, operations, legal, compliance, risk management, and key business units. Consider whether to conduct the assessment internally, hire external consultants, or use a combination approach. External assessors bring objectivity and experience but may lack deep organizational knowledge that internal teams possess.
Step 4: Gather Documentation and Evidence
Collect existing security policies, procedures, incident reports, audit findings, risk assessments, and technology inventories. This documentation provides the foundation for understanding your current state. Be prepared for this phase to reveal gaps in documentation itself which is valuable information.
Step 5: Conduct Interviews and Observations
Documentation tells part of the story, but reality often differs from policy. Interview key personnel across different levels and functions to understand how security is actually practiced. Observe processes in action when possible. This qualitative data is essential for accurate maturity assessment.
Step 6: Perform Technical Evaluations
Complement your interviews with technical assessments of your security controls. This might include configuration reviews, vulnerability scans, penetration testing results, and security tool effectiveness evaluations. The goal isn't to conduct a full penetration test but to validate that controls described on paper actually function as intended.
Step 7: Analyze and Score Results
Map your findings to your chosen maturity model. For each component, determine your current maturity level based on the evidence gathered. Be honest and objective, overestimating maturity creates false confidence that can be dangerous. Document the scores, the evidence and reasoning behind them.
Step 8: Identify Gaps and Prioritize Improvements
Compare your current state to your target maturity level. Identify gaps between where you are and where you need to be. Prioritize remediation efforts based on risk, regulatory requirements, resource availability, and potential impact.
Step 9: Develop a Roadmap
Create a practical improvement roadmap with specific initiatives, timelines, resource requirements, and success metrics. Break down large improvements into achievable milestones. Ensure executive sponsorship and secure necessary budget and resources.
Step 10: Report and Communicate Results
Prepare findings for different audiences. Executives need high-level insights with business impact and resource requirements. Technical teams need detailed findings and remediation guidance. Tailor your communication to resonate with each stakeholder group.
Step 11: Implement and Monitor
Execute your improvement roadmap while monitoring progress against defined metrics. Cybersecurity maturity isn't a one-time achievement but an ongoing journey. Plan for regular reassessments annually at minimum, or more frequently if you're in a rapidly changing environment or high-risk industry.
Importance of a Cybersecurity Maturity Assessment
Understanding why cybersecurity maturity assessments matter can transform how you approach organizational security. Here are the compelling reasons why this process is critical:
Provides Objective Visibility
Many organizations operate with a false sense of security, believing they're more protected than they actually are. A maturity assessment cuts through assumptions and provides objective, evidence-based visibility into your actual security posture. This clarity is essential for making informed decisions about risk and investment.
Enables Risk-Based Prioritization
A maturity assessment helps you understand which security gaps pose the greatest risk to your organization, allowing you to prioritize improvements where they'll have the most significant impact on reducing risk.
Supports Regulatory Compliance
For organizations in regulated industries; healthcare, finance, energy, defense, and many others demonstrating cybersecurity maturity is mandatory. Many regulators now expect organizations to conduct regular maturity assessments and show continuous improvement. Having this documentation can be invaluable during audits or after incidents.
Facilitates Board-Level Communication
Boards and executives often struggle to understand cybersecurity in concrete terms. Maturity levels provide a common language for discussing security posture that doesn't require technical expertise. Saying "We're at maturity level 2 and need to reach level 3" is far more meaningful to business leaders than technical jargon about firewalls and encryption protocols.
Benchmarks Against Industry Standards
A maturity assessment allows you to compare your organization's security posture against industry peers and best practices. This benchmarking can reveal whether you're lagging behind competitors, meeting industry norms, or leading in security excellence, valuable intelligence for strategic planning.
Improves Vendor Risk Management
When evaluating third-party vendors and partners, asking about their cybersecurity maturity level provides a standardized way to assess their security capabilities. Many organizations now require vendors to complete maturity assessments as part of procurement and ongoing relationship management.
Reduces Cyber Insurance Costs
Cyber insurance has become essential but increasingly expensive. Insurers are scrutinizing applicants' security postures more carefully. Organizations that can demonstrate higher cybersecurity maturity levels often qualify for better coverage terms and lower premiums, providing tangible ROI for security investments.
Strengthens Incident Response
Higher maturity levels correlate with better incident response capabilities. Organizations that regularly assess and improve their maturity are better prepared when breaches occur, resulting in faster detection, more effective containment, and reduced business impact.
Attracts Customers and Partners
In B2B relationships, prospective customers increasingly demand evidence of strong cybersecurity before signing contracts. Being able to demonstrate high maturity levels can be a competitive differentiator that opens business opportunities and builds trust with clients.
How Regulance.io Helps You Conduct Cybersecurity Maturity Assessment
Navigating the complexities of cybersecurity maturity assessment can be daunting, especially for organizations without dedicated security teams or those new to formal security frameworks. This is where Regulance.io transforms the process from overwhelming to manageable.
Streamlined Assessment Platform
Regulance.io provides an intuitive, centralized platform that guides you through the entire maturity assessment process. Rather than juggling spreadsheets, documents, and email threads, everything happens in one place. The platform walks you through each assessment component with clear questions, helpful guidance, and examples that make even complex security concepts accessible to non-experts.
Automated Evidence Collection
One of the most time-consuming aspects of maturity assessments is gathering and organizing evidence. Regulance.io automates much of this process by integrating with your existing security tools and systems. It can automatically collect configuration data, policy documents, scan results, and other evidence, dramatically reducing manual effort while improving assessment accuracy.
Collaborative Workflows
Cybersecurity assessments require input from multiple stakeholders across your organization. Regulance.io's collaborative features make it easy to assign tasks, track progress, and gather insights from different teams. Security leaders maintain visibility into the entire process while individuals can focus on their specific areas of responsibility.
Intelligent Gap Analysis
Once your assessment is complete, Regulance.io doesn't just show you a score, it provides intelligent gap analysis that identifies exactly where you're falling short and why. The platform compares your current state against best practices and your target maturity level, highlighting priority areas for improvement with clear, actionable recommendations.
Executive Reporting and Dashboards
Communicating assessment results to executives and boards is effortless with Regulance.io's sophisticated reporting capabilities. Generate polished, professional reports that present findings in business terms with visual dashboards, trend analysis, and clear recommendations. Technical details are available for those who need them, but high-level stakeholders get the strategic insights they require.
Continuous Monitoring
Rather than conducting point-in-time assessments that quickly become outdated, Regulance.io enables continuous monitoring of your cybersecurity maturity. As you implement improvements and your environment evolves, the platform tracks changes and updates your maturity level accordingly. This provides always-current visibility into your security posture.
Vendor Risk Assessment Integration
Regulance.io extends beyond internal assessments to help you evaluate third-party cybersecurity risk. Use the platform to send security questionnaires to vendors, track their maturity levels, and monitor changes over time. This ensures that your supply chain security receives the same rigorous attention as your internal controls.
Compliance Automation
For organizations facing regulatory requirements, Regulance.io maps your maturity assessment to relevant compliance obligations. The platform helps you demonstrate compliance, prepare for audits, and maintain the documentation that regulators expect, all while reducing the administrative burden on your team.
Expert Support
Behind the technology is a team of cybersecurity experts who understand the real-world challenges organizations face. Regulance.io customers benefit from expert guidance throughout the assessment process, from initial scoping to remediation planning. This combination of powerful technology and human expertise ensures you get the most value from your maturity assessment efforts.
Frequently Asked Questions (FAQs)
How often should we conduct a cybersecurity maturity assessment?
Most organizations should conduct a comprehensive maturity assessment annually at minimum. However, you might need more frequent assessments if you operate in a high-risk industry, undergo significant organizational changes, experience a security incident, or face new regulatory requirements. Many mature organizations conduct continuous assessments with quarterly reviews.
What's the difference between a maturity assessment and a security audit?
A security audit typically focuses on compliance with specific standards or regulations at a point in time, it's a pass/fail evaluation. A maturity assessment takes a broader, developmental view, evaluating your capabilities along a maturity continuum and focusing on improvement opportunities. Think of audits as compliance checks and maturity assessments as strategic planning tools.
How long does a cybersecurity maturity assessment take?
The duration varies based on organizational size, complexity, and assessment scope. A focused assessment for a small organization might take 2-4 weeks, while a comprehensive assessment for a large, complex enterprise could take 2-3 months. Using platforms like Regulance.io can significantly reduce this timeline through automation and streamlined workflows.
Do we need external consultants to conduct a maturity assessment?
Not necessarily. Organizations with strong internal security expertise can conduct self-assessments, especially when using structured platforms. However, external assessors provide objectivity, bring experience from multiple organizations, and may be required for certain regulatory purposes. Many organizations find a hybrid approach,an internal team with external validation works best.
What maturity level should we target?
There's no one-size-fits-all answer. Your target maturity level should align with your risk profile, regulatory requirements, industry norms, and resource availability. Not every organization needs to be at level 5 across all components. Focus on achieving higher maturity in areas most critical to your business and risk profile.
How much does improving cybersecurity maturity cost?
Investment requirements vary dramatically based on your starting point, target maturity level, and organizational size. However, maturity assessments help you prioritize investments for maximum impact. Many improvements, better policies, training programs, process changes don't require massive technology spend. The key is strategic, risk-based investment rather than trying to do everything at once.
Can small businesses benefit from maturity assessments?
Absolutely. While small businesses might use simplified frameworks, the benefits of understanding your security posture, prioritizing improvements, and demonstrating security competence to customers apply regardless of size. In fact, small businesses often benefit most because they have limited resources and need to invest wisely.
How do we maintain maturity after the assessment?
Cybersecurity maturity requires ongoing effort. Implement your improvement roadmap, measure progress against defined metrics, maintain documentation, continue training and awareness programs, and plan regular reassessments. Using continuous monitoring tools helps you track maturity in real-time rather than waiting for the next formal assessment.
Conclusion
In an era where cyber threats evolve daily and digital trust is currency, understanding your organization's cybersecurity maturity is a necessity. A comprehensive cybersecurity maturity assessment provides the foundation for everything else: strategic planning, risk management, regulatory compliance, and building stakeholder confidence.
The journey from initial assessment to optimized cybersecurity maturity requires commitment, resources, and persistence. But organizations that embrace this journey position themselves not just to defend against threats, but to thrive in an increasingly digital world. They turn cybersecurity from a cost center into a competitive advantage, from a source of anxiety into a foundation for innovation and growth.
cybersecurity maturity involves continuous improvement and staying ahead of evolving threats. Every step up the maturity ladder makes your organization more resilient, more trusted, and better prepared for whatever digital challenges lie ahead.
Start Your Cybersecurity Maturity Assessment Today
Regulance.io streamlines the entire maturity assessment process with automated tools, expert guidance, and actionable insights.
Don't wait for a breach to expose your vulnerabilities.
Regulance.io to start your cybersecurity maturity assessment, schedule a demo, or speak with our security experts. Transform your cybersecurity from reactive to proactive today.