What Does Your Risk Posture Reveal About Your Business Readiness?


Introduction
Organizations face an unprecedented array of threats ranging from sophisticated cyberattacks to regulatory compliance challenges and operational disruptions. The way your business approaches, manages, and responds to these threats defines what experts call your "risk posture"; a critical concept that can make the difference between thriving in uncertainty and becoming another cautionary tale.
Risk posture represents the comprehensive stance your organization takes toward identifying, assessing, and managing potential threats to your operations, reputation, and bottom line. It is your business's defensive and offensive strategy combined; the overall readiness and resilience you've built to face whatever challenges come your way.
Understanding your risk posture is particularly crucial in an era where digital transformation has expanded attack surfaces, where supply chain vulnerabilities can cascade into major disruptions, and where a single data breach can cost millions in remediation and reputational damage. Whether you're a startup navigating your first compliance requirements or an established enterprise managing complex international operations, your risk posture directly impacts your ability to protect assets, maintain customer trust, and seize opportunities that more risk-averse competitors might avoid.
This guide will walk you through everything you need to know about risk posture, from its fundamental components to practical strategies for assessment and improvement. You'll discover how different risk postures align with various business strategies, learn to evaluate your current position, and explore how emerging technologies like artificial intelligence are revolutionizing risk management.
What is Risk Posture?
Risk posture is the overall position and readiness of an organization to identify, manage, and respond to potential risks and threats. It encompasses your business's collective risk management capabilities, security controls, organizational culture toward risk, and strategic approach to balancing opportunities against potential downsides.
Risk posture represents the intersection of three critical elements: your organization's risk appetite (how much risk you're willing to accept), your risk tolerance (the maximum level of risk you can handle before it threatens your objectives), and your actual risk exposure (the real threats facing your business). The alignment or misalignment of these elements determines whether your risk posture is strong, weak, or somewhere in between.
Your risk posture manifests in tangible ways throughout your organization. It's reflected in your cybersecurity infrastructure, compliance programs, business continuity plans, insurance coverage, vendor management practices, and employee training initiatives. It's also visible in less tangible aspects like your decision-making processes, leadership's attitude toward innovation versus caution, and how quickly you adapt to emerging threats.
A well-defined risk posture serves as your organization's risk management blueprint, guiding everything from daily operational decisions to long-term strategic planning. It helps you answer critical questions: Which risks should we mitigate aggressively? Which can we accept? Where should we invest limited security resources? How do we balance growth ambitions with protective measures?
Understanding that risk posture is dynamic is essential. As your business evolves, enters new markets, adopts new technologies, or faces changing regulatory landscapes, your risk posture must evolve accordingly. Regular assessment and adjustment ensure your risk posture remains aligned with your business objectives and the actual threat environment you face.
The Importance of Understanding Risk Posture
Grasping your organization's risk posture is a strategic imperative with far-reaching implications for business success and survival.
Strategic Decision-Making Enhancement
When leadership understands the organization's true risk posture, they make better-informed strategic decisions. You can pursue growth opportunities with clear eyes about the risks involved, rather than either charging blindly forward or paralyzed by unfounded fears. This clarity enables calculated risk-taking that drives innovation while maintaining appropriate safeguards.
Resource Optimization
Risk posture awareness helps you allocate limited security and compliance resources where they'll have maximum impact. Instead of spreading your budget thin across countless initiatives, you can focus investments on the vulnerabilities that pose the greatest threat to your specific business context. This targeted approach delivers better protection at lower cost.
Regulatory Compliance and Stakeholder Confidence
Demonstrating a mature, well-articulated risk posture builds trust with regulators, investors, customers, and partners. It shows you're not just checking compliance boxes but genuinely committed to responsible risk management. This confidence can translate into better insurance rates, easier access to capital, stronger customer relationships, and competitive advantages in regulated industries.
Resilience and Business Continuity
Organizations with strong risk posture awareness are simply more resilient. They've anticipated potential disruptions, planned responses, and built redundancies in critical areas. When incidents occur and they will these businesses recover faster with less damage, maintaining operations and customer trust while competitors struggle.
Competitive Advantage
In many industries, superior risk management has become a differentiator. Customers increasingly choose vendors who can demonstrate robust security and compliance postures. A well-managed risk posture enables you to win business, enter markets, and pursue opportunities that are closed to less-prepared competitors.
Understanding your risk posture transforms risk management from a defensive necessity into a strategic asset that drives business value.
Key Components of Risk Posture
A comprehensive risk posture comprises several interconnected components that together determine your organization's overall risk readiness.
Risk Assessment and Identification
This foundational component involves systematically identifying and evaluating the threats facing your organization. It includes vulnerability assessments, threat intelligence gathering, business impact analyses, and scenario planning. Effective risk identification looks beyond obvious cybersecurity threats to encompass operational, financial, reputational, compliance, and strategic risks.
Security Controls and Safeguards
These are the technical, administrative, and physical measures you've implemented to protect assets and mitigate identified risks. Examples include firewalls, encryption, access controls, security awareness training, incident response plans, and business continuity procedures. The comprehensiveness and effectiveness of these controls directly impact your risk posture.
Risk Governance and Policies
Your governance structure defines roles, responsibilities, and processes for risk management. This includes board-level oversight, executive accountability, clear policies and procedures, and defined escalation paths. Strong governance ensures risk management is coordinated, consistent, and aligned with business objectives rather than fragmented across departments.
Risk Culture and Awareness
Perhaps the most overlooked component, organizational culture determines how seriously employees at all levels take risk management. A strong risk culture means security awareness permeates decision-making, employees report concerns without fear, and risk considerations are embedded in workflows rather than bolted on afterward.
Monitoring and Metrics
Continuous monitoring and meaningful metrics allow you to track your risk posture over time and demonstrate improvement. Key risk indicators, security dashboards, compliance scorecards, and regular audits provide visibility into whether your risk posture is strengthening or deteriorating.
Incident Response Capabilities
Your ability to detect, respond to, and recover from security incidents and business disruptions is crucial. This component includes incident response teams, playbooks, communication protocols, forensic capabilities, and lessons-learned processes that feed continuous improvement.
Third-Party Risk Management
Modern businesses are ecosystems of vendors, partners, and suppliers. Your risk posture extends to these relationships through vendor assessments, contractual protections, ongoing monitoring, and contingency planning for supplier failures.
Types of Risk Postures
Organizations typically exhibit one of three broad risk posture types, each with distinct characteristics and implications:
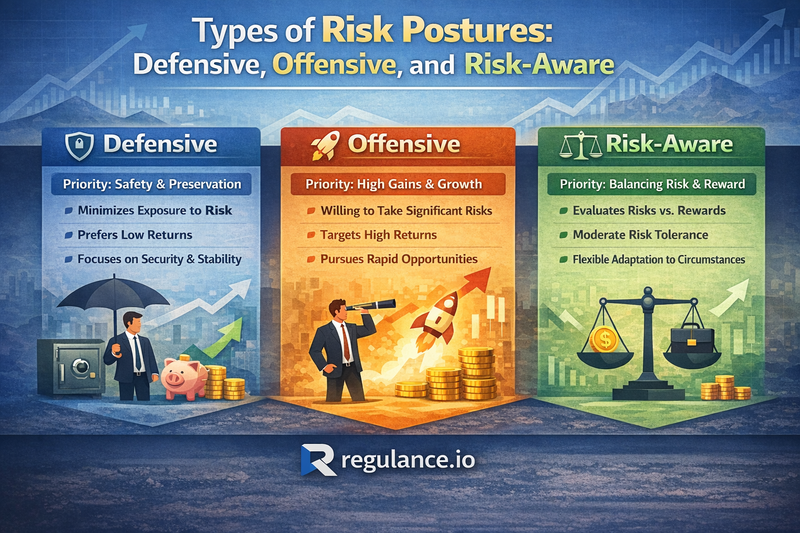
Defensive Risk Posture
A defensive posture prioritizes protection and risk avoidance above all else. Organizations with this approach implement extensive controls, enforce strict policies, and generally err on the side of caution.
Characteristics: Comprehensive security measures, conservative decision-making, extensive compliance programs, significant risk management investments, slow adoption of new technologies, and preference for proven solutions over innovation.
Advantages: Strong protection against known threats, high compliance levels, predictable outcomes, reduced incident frequency.
Disadvantages: Slower innovation, higher operational costs, potential competitive disadvantages, employee frustration with restrictive controls, and possible inability to capitalize on emerging opportunities.
Best suited for: Highly regulated industries (healthcare, finance, defense), organizations handling extremely sensitive data, businesses with low risk tolerance, or those recovering from major incidents.
Offensive Risk Posture
An offensive posture emphasizes agility, innovation, and calculated risk-taking. These organizations accept higher risk levels in pursuit of competitive advantage and rapid growth.
Characteristics: Fast decision-making, early technology adoption, streamlined approval processes, entrepreneurial culture, minimal bureaucracy, and willingness to enter uncertain markets.
Advantages: Rapid innovation, market leadership, competitive advantages, employee empowerment, and ability to seize first-mover opportunities.
Disadvantages: Higher vulnerability to threats, potential compliance gaps, greater incident likelihood, possible reputational damage from failures, and difficulty attracting risk-averse customers or partners.
Best suited for: Startups, technology companies, organizations in rapidly evolving markets, businesses where speed-to-market is critical, or industries with lower regulatory burdens.
Risk-Aware Posture
This balanced approach combines defensive protections with offensive agility. Risk-aware organizations implement strong foundational controls while maintaining flexibility to pursue opportunities and innovate.
Characteristics: Data-driven risk decisions, proportional controls based on actual threat levels, continuous risk assessment, adaptive security, balanced innovation with protection, and cultural emphasis on risk intelligence.
Advantages: Optimal resource allocation, flexibility to respond to changing conditions, sustainable long-term approach, ability to compete effectively while maintaining strong defenses.
Disadvantages: Requires sophisticated risk management capabilities, demands ongoing assessment and adjustment, needs strong risk culture throughout organization.
Best suited for: Most mid-to-large enterprises, organizations balancing growth with protection, businesses facing diverse risk landscapes, companies undergoing digital transformation.
Most successful organizations ultimately evolve toward a risk-aware posture that enables both protection and progress.
Assessing Your Business's Current Risk Posture
Understanding your current risk posture requires systematic assessment across multiple dimensions:
Conduct a Comprehensive Risk Assessment
Begin with a thorough inventory of your assets, processes, and systems. Identify and catalog potential threats, from cyberattacks and data breaches to supply chain disruptions and regulatory changes. Evaluate your existing controls and their effectiveness. Map dependencies and single points of failure.
Evaluate Security Maturity
Benchmark your security practices against established frameworks like NIST Cybersecurity Framework, ISO 27001, or industry-specific standards. Assess maturity across domains including governance, asset management, access control, data protection, incident response, and recovery capabilities. Identify gaps between current state and desired state.
Review Historical Incidents and Near-Misses
Analyze past security incidents, breaches, compliance violations, and near-misses. What patterns emerge? Which risks materialized? How effective were your responses? What weaknesses were exposed? This historical perspective reveals blind spots and recurring vulnerabilities.
Assess Risk Culture
Survey employees about their risk awareness and attitudes. Do they understand their role in risk management? Do they feel comfortable reporting concerns? Are security measures viewed as obstacles or enablers? Cultural assessment reveals whether your policies translate into actual behaviors.
Conduct Penetration Testing and Vulnerability Scanning
Technical assessments identify exploitable weaknesses in your systems, applications, and infrastructure. Regular penetration testing, vulnerability scanning, and configuration reviews provide objective data about your technical security posture.
Evaluate Third-Party Risks
Assess the risk posture of critical vendors and partners. Review their security practices, compliance certifications, financial stability, and incident histories. Understand how their vulnerabilities could impact your operations.
Compare Against Peers and Best Practices
Benchmark your risk posture against industry peers and leaders. How do your security investments, incident rates, and control effectiveness compare? Where are you ahead? Where are you falling behind?
This assessment should produce a clear picture of your current risk posture, including strengths to maintain, weaknesses to address, and priorities for improvement.
Factors Influencing Risk Posture
Numerous internal and external factors shape your organization's risk posture:
Industry and Regulatory Environment
Heavily regulated industries like healthcare, financial services, and critical infrastructure face stricter requirements that drive more defensive postures. Your industry's threat landscape, whether you're a frequent target of nation-state actors, cybercriminals, or activists also influences your stance.
Organizational Size and Complexity
Larger organizations typically have more resources for risk management but also more complex attack surfaces. Smaller businesses may lack resources but have simpler environments to protect. Geographic distribution, merger and acquisition activity, and organizational structure all impact risk posture complexity.
Business Model and Digital Dependence
Organizations heavily dependent on digital systems, those handling sensitive customer data, or businesses operating exclusively online require stronger security postures than traditional brick-and-mortar operations with limited digital footprints.
Financial Resources
Budget constraints directly impact the comprehensiveness of your security controls, the sophistication of your monitoring capabilities, and your ability to attract skilled security talent. However, effective risk management is more about smart allocation than absolute spending levels.
Leadership Attitudes and Culture
Executive commitment to risk management, board-level oversight, and cultural values around security fundamentally shape your risk posture. Organizations where leadership treats security as strategic priority develop stronger postures than those viewing it as an IT problem.
Competitive Pressures
Market dynamics influence risk tolerance. Companies facing intense competition may accept higher risks to maintain pace with rivals. Conversely, market leaders in mature industries may adopt conservative postures to protect established positions.
Technology Adoption Patterns
Early adopters of emerging technologies like cloud computing, artificial intelligence, and Internet of Things face different risk profiles than late adopters using proven technologies. Your technology strategy directly impacts your risk exposure and required controls.
Previous Incidents and Lessons Learned
Organizations that have experienced significant breaches or disruptions often develop stronger risk postures as a result assuming they learn appropriate lessons rather than overcorrecting or becoming paralyzed.
Strategies for Improving Your Risk Posture
Strengthening your risk posture requires strategic, sustained effort across multiple fronts:
Establish Clear Risk Governance
Create or strengthen board-level risk oversight committees. Define clear accountability for risk management throughout the organization. Establish regular risk reporting to leadership. Develop comprehensive policies and procedures that are enforced consistently.
Implement a Risk Management Framework
Adopt established frameworks like NIST, ISO 27001, or COBIT that provide structured approaches to identifying, assessing, treating, and monitoring risks. These frameworks ensure comprehensive coverage and facilitate continuous improvement.
Invest in Security Awareness and Training
Human error remains the leading cause of security incidents. Implement ongoing security awareness programs that engage employees, use realistic scenarios, and measure behavioral change. Make risk awareness part of onboarding, performance reviews, and organizational culture.
Adopt Zero Trust Architecture
Move from perimeter-based security to zero trust principles that verify every access request, assume breach, and limit lateral movement. This modern approach significantly reduces risk in today's borderless, cloud-based environments.
Enhance Monitoring and Detection
Implement security information and event management (SIEM) systems, endpoint detection and response (EDR) tools, and security operations center (SOC) capabilities that provide real-time visibility into your environment and enable rapid threat detection.
Strengthen Incident Response
Develop, test, and regularly update incident response plans. Conduct tabletop exercises and simulations. Establish relationships with external resources like forensic investigators and legal counsel before you need them. Build muscle memory for effective crisis response.
Embrace Continuous Improvement
Treat risk management as an ongoing journey, not a destination. Conduct regular assessments, track meaningful metrics, learn from incidents, and adapt to emerging threats. Build feedback loops that drive continuous enhancement.
Collaborate and Share Intelligence
Join industry information sharing and analysis centers (ISACs), participate in threat intelligence communities, and collaborate with peers. Learning from others' experiences accelerates your own risk posture improvement.
Balance Prevention and Resilience
While preventing incidents is ideal, assuming perfect prevention is unrealistic. Balance preventive controls with resilience capabilities that enable rapid detection, response, and recovery when incidents occur.
The Role of AI in Managing Risk Posture
Artificial intelligence is transforming risk management, enabling capabilities previously impossible at scale:
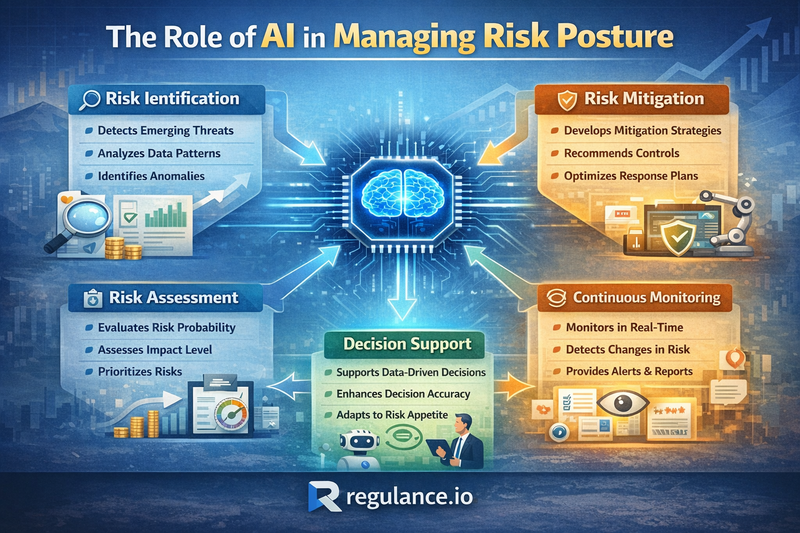
Automated Threat Detection
AI-powered systems analyze vast amounts of data to identify threats, anomalies, and attack patterns in real-time. Machine learning models detect subtle indicators of compromise that human analysts might miss, dramatically improving detection speed and accuracy.
Predictive Risk Analytics
AI analyzes historical data, industry trends, and emerging threats to predict future risks before they materialize. This forward-looking capability enables proactive rather than reactive risk management, allowing you to address vulnerabilities before exploitation.
Intelligent Automation
AI automates routine security tasks like log analysis, vulnerability prioritization, patch management, and initial incident triage. This automation frees skilled professionals for higher-value strategic work while ensuring consistent, error-free execution of repetitive tasks.
Enhanced Decision Support
AI provides risk-based recommendations for policy decisions, resource allocation, and control implementation. By processing far more variables than humans can simultaneously consider, AI helps leaders make more informed, data-driven risk decisions.
Adaptive Security Posture
AI enables dynamic security that automatically adjusts controls based on changing threat levels, user behavior, and contextual factors. This adaptive approach maintains strong protection while minimizing friction for legitimate users.
Improved Compliance Management
AI monitors regulatory changes, maps requirements to controls, identifies compliance gaps, and automates evidence collection for audits. This capability is particularly valuable for organizations facing multiple regulatory regimes.
However, AI also introduces new risks including algorithmic bias, adversarial attacks on AI systems, and over-reliance on automated decisions. Effective AI integration requires human oversight, ethical guidelines, and transparency about AI's role in risk decisions.
Organizations leveraging AI thoughtfully gain significant advantages in managing increasingly complex risk landscapes.
FAQs
What's the difference between risk posture and cybersecurity posture?
Cybersecurity posture is a subset of overall risk posture focused specifically on information security and cyber threats. Risk posture encompasses cybersecurity but also includes operational, financial, reputational, compliance, strategic, and other risk categories.
How often should we assess our risk posture?
Conduct comprehensive assessments at least annually, with more frequent reviews (quarterly or semi-annually) of critical areas. Additionally, reassess whenever significant changes occur; new technologies, major acquisitions, regulatory changes, or after security incidents.
Can small businesses benefit from understanding risk posture?
Absolutely. While small businesses may lack enterprise resources, understanding risk posture helps them prioritize limited budgets, demonstrate credibility to larger customers, and build resilience against threats that could prove fatal to smaller operations.
What role does cyber insurance play in risk posture?
Cyber insurance is a risk transfer mechanism that complements but doesn't replace good risk management. Insurers increasingly assess your risk posture during underwriting, with stronger postures earning better rates and coverage. Insurance also provides financial protection and incident response resources when needed.
How do we measure improvement in risk posture?
Track key risk indicators like time-to-detect threats, incident frequency and severity, vulnerability remediation times, compliance audit scores, security awareness test results, and percentage of assets with current protections. Compare these metrics over time and against industry benchmarks.
Conclusion
Understanding and actively managing your risk posture has evolved from a compliance necessity to a strategic imperative that directly impacts business success. Your risk posture determines not just how well you're protected against threats, but how effectively you can pursue opportunities, innovate, and compete in an uncertain world.
The journey to a strong risk posture requires honest assessment of your current state, clear-eyed recognition of the factors shaping your risk environment, and committed execution of improvement strategies tailored to your specific business context. Whether you adopt a defensive, offensive, or risk-aware approach, the key is ensuring conscious alignment between your risk posture and your business objectives.
Technology, particularly artificial intelligence, offers powerful tools for managing increasingly complex risk landscapes. However, technology alone cannot create a strong risk posture. Success requires the right combination of governance, culture, processes, controls, and people working in concert toward shared risk management goals.
In the recent threat environment, hoping for the best is not a strategy. Organizations that proactively shape their risk posture position themselves to thrive despite uncertainty, while those that neglect risk management invite preventable disasters.
Ready to transform your organization's risk management from reactive scrambling to strategic advantage? Contact Regulance today for a complimentary risk posture assessment and discover how we can help you build resilience, and confidence through superior risk management.