What Does SOC Stand for in Cybersecurity? A Comprehensive Guide to Security Operations Centers


Introduction
In the modern digital era, where cyber threats evolve at breakneck speed and data breaches make headlines daily, organizations face an unprecedented challenge in protecting their digital assets. The term "SOC" frequently surfaces in cybersecurity discussions, but what exactly does it mean, and why has it become such a cornerstone of modern security strategy?
SOC in cybersecurity stands for Security Operations Center – a centralized unit that deals with security issues on an organizational and technical level. Think of it as the nerve center of an organization's cybersecurity efforts, where skilled professionals work around the clock to monitor, detect, analyze, and respond to cybersecurity incidents using a combination of technology solutions and strong processes.
The importance of SOCs has grown exponentially as organizations recognize that cybersecurity is about having the right people, processes, and technology working together seamlessly to create a robust defense mechanism. In an era where the average cost of a data breach exceeds $4 million globally, investing in a well-structured SOC isn't just smart business – it's essential for survival.
What is SOC for Cybersecurity?
A Security Operations Center represents the heart of an organization's cybersecurity infrastructure. Unlike traditional IT support centers that focus on maintaining systems and helping users with technical issues, a SOC is specifically designed to identify, investigate, and respond to cybersecurity threats before they can cause significant damage.
Core Functions of a Cybersecurity SOC
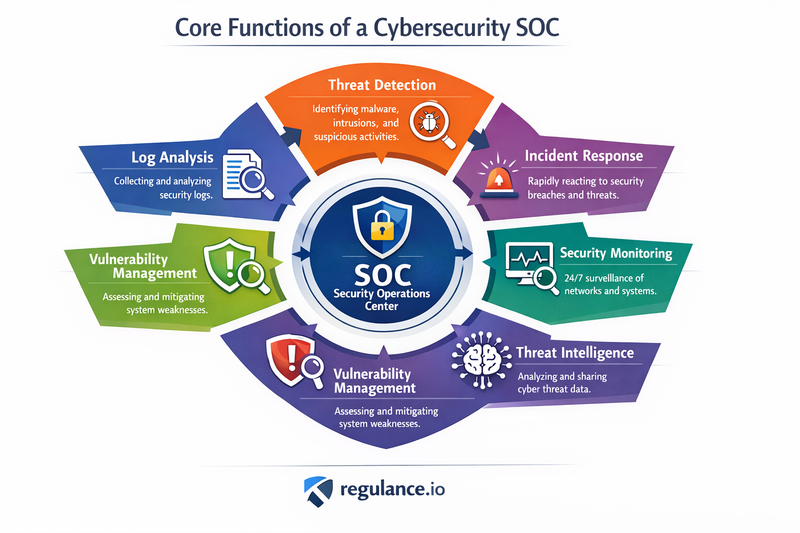
Continuous Monitoring and Detection The primary function of any SOC is to provide 24/7/365 monitoring of an organization's entire IT infrastructure. This includes networks, servers, endpoints, databases, applications, websites, and other systems. SOC analysts use sophisticated security information and event management (SIEM) systems to collect and analyze security events from across the organization's digital ecosystem.
Incident Response and Management When potential security incidents are detected, the SOC team springs into action. They follow established incident response procedures to contain threats, investigate their scope and impact, and coordinate recovery efforts. This rapid response capability can mean the difference between a minor security event and a catastrophic breach.
Threat Intelligence and Analysis Modern SOCs don't just react to threats – they proactively hunt for them. SOC teams analyze threat intelligence feeds, study attack patterns, and use advanced analytics to identify potential threats before they materialize into actual attacks. This proactive approach helps organizations stay ahead of cybercriminals.
Compliance and Reporting SOCs play a crucial role in helping organizations maintain compliance with various regulatory requirements such as GDPR, HIPAA, PCI DSS, and others. They generate detailed reports on security incidents, response times, and overall security posture, providing valuable insights for executive leadership and regulatory bodies.
Key Components of an Effective SOC
People – The Human Element A SOC is only as strong as its team. Typical SOC staffing includes:
- SOC Manager: Oversees operations and strategy
- Security Analysts (Tier 1, 2, and 3): Monitor, investigate, and respond to security events
- Incident Response Specialists: Handle complex security incidents
- Threat Hunters: Proactively search for advanced threats
- Forensics Experts: Conduct detailed analysis of security incidents
Processes – The Framework Well-defined processes ensure consistent and effective security operations:
- Incident classification and escalation procedures
- Standard operating procedures for common security events
- Communication protocols for different types of incidents
- Regular training and knowledge sharing sessions
Technology – The Tools Modern SOCs rely on a sophisticated technology stack:
- SIEM platforms for log collection and analysis
- Security orchestration, automation, and response (SOAR) tools
- Endpoint detection and response (EDR) solutions
- Network monitoring and analysis tools
- Threat intelligence platforms
Types of SOC Models
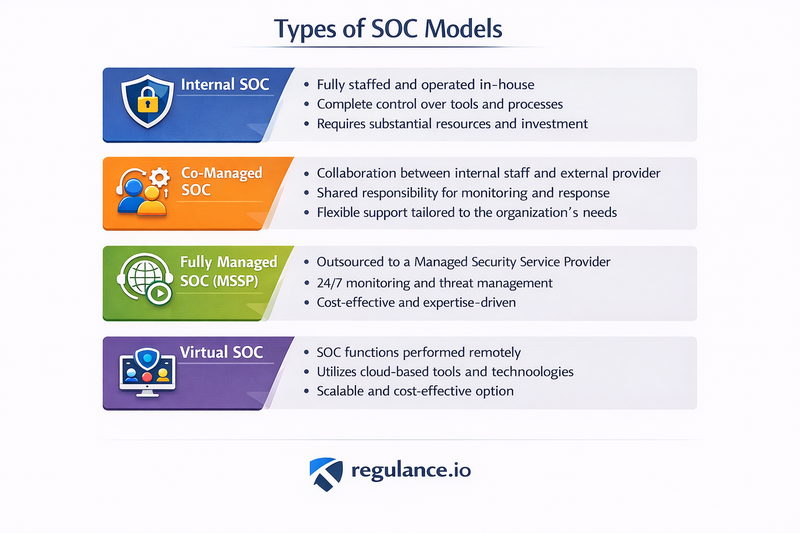
Internal SOC Organizations build and maintain their own security operations center with internal resources. This model provides maximum control but requires significant investment in people, processes, and technology.
Managed SOC (MSOC) Organizations outsource their SOC operations to a third-party security service provider. This model offers cost savings and access to specialized expertise without the overhead of building internal capabilities.
Hybrid SOC A combination approach where organizations maintain some internal SOC capabilities while outsourcing specific functions or supplementing internal resources with external expertise during peak periods or for specialized skills.
Virtual SOC A distributed model where SOC functions are performed remotely by internal or external teams, leveraging cloud-based security tools and platforms.
What's the Difference Between SOC for Cybersecurity and SOC 2?
The confusion between SOC in cybersecurity and SOC 2 is understandable, as both terms are prevalent in security discussions. However, they represent entirely different concepts that serve distinct purposes in the security landscape.
Understanding SOC 2
SOC 2, which stands for System and Organization Controls 2, is an auditing procedure developed by the American Institute of Certified Public Accountants (AICPA). It's not a security operations center but rather a compliance framework that evaluates an organization's information systems relevant to security, availability, processing integrity, confidentiality, and privacy.
Key Differences Explained
Purpose and Scope
- SOC (Security Operations Center): An operational function focused on real-time monitoring, detection, and response to cybersecurity threats
- SOC 2: A compliance audit that assesses how well an organization safeguards customer data and manages risk
Implementation Timeline
- SOC (Cybersecurity): An ongoing operational capability that functions 24/7/365
- SOC 2: A periodic audit process typically conducted annually, with two types: Type I (point-in-time assessment) and Type II (operational effectiveness over time)
Deliverables
- SOC (Cybersecurity): Continuous threat detection, incident reports, security metrics, and improved security posture
- SOC 2: An audit report that demonstrates compliance with established security controls and can be shared with customers and stakeholders
Target Audience
- SOC (Cybersecurity): Internal security teams, IT leadership, and executive management
- SOC 2: External customers, partners, investors, and regulatory bodies who need assurance about data protection practices
Cost and Resource Requirements
- SOC (Cybersecurity): Requires significant ongoing investment in personnel, technology, and infrastructure
- SOC 2: Involves periodic audit fees and preparation time, but doesn't require dedicated full-time resources
Why Organizations Need Both
Smart organizations recognize that SOC cybersecurity operations and SOC 2 compliance are complementary rather than competing priorities. A well-functioning Security Operations Center actually makes SOC 2 compliance easier to achieve and maintain by:
- Providing the continuous monitoring and incident response capabilities that auditors look for
- Generating the documentation and evidence required for SOC 2 reports
- Demonstrating operational effectiveness of security controls over time
- Ensuring that security incidents are properly detected, investigated, and resolved
Conversely, SOC 2 compliance provides a structured framework that can help organizations design and implement more effective SOC operations by establishing clear security objectives and control requirements.
SOC for Cybersecurity Requirements
Building an effective Security Operations Center requires careful planning and significant investment across multiple dimensions. Understanding these requirements is crucial for organizations considering implementing SOC capabilities.
Staffing Requirements
Skill Sets and Expertise A successful SOC requires a diverse range of skills and expertise levels:
- Technical Skills: Network security, incident response, malware analysis, digital forensics, scripting and automation, cloud security, and vulnerability management
- Analytical Skills: Threat hunting, log analysis, pattern recognition, risk assessment, and critical thinking
- Communication Skills: Technical writing, presentation abilities, and cross-functional collaboration
- Continuous Learning: The cybersecurity landscape evolves rapidly, requiring team members who can adapt and learn new technologies and techniques
Staffing Models and Coverage SOCs typically operate using tiered staffing models:
- Tier 1 Analysts: Handle initial triage of security alerts, perform basic incident classification, and escalate complex issues
- Tier 2 Analysts: Conduct deeper investigation of security incidents, perform threat analysis, and coordinate response efforts
- Tier 3 Analysts/Specialists: Handle advanced threat hunting, forensic analysis, and complex incident response
For 24/7 operations, organizations typically need 8-12 full-time equivalent positions to provide adequate coverage across all shifts, including vacation and sick leave coverage.
Technology Infrastructure Requirements
Core Technology Stack Modern SOCs require sophisticated technology infrastructure:
- SIEM Platform: Centralized log collection, correlation, and analysis capabilities with real-time monitoring dashboards
- Network Monitoring Tools: Deep packet inspection, network flow analysis, and behavioral monitoring capabilities
- Endpoint Protection: Advanced endpoint detection and response tools with behavioral analysis and automated response capabilities
- Threat Intelligence Platforms: Integration with multiple threat intelligence feeds and analysis capabilities
- Security Orchestration Tools: Automated playbooks and response capabilities to handle routine tasks and improve response times
Infrastructure Considerations
- Scalability: Systems must handle growing data volumes and organizational expansion
- Redundancy: Critical systems require backup and failover capabilities
- Integration: All tools must work together seamlessly to provide a unified view of security posture
- Performance: Systems must process and analyze data in real-time without introducing delays
Process and Procedure Requirements
Incident Response Procedures Well-defined incident response processes are crucial:
- Incident Classification: Clear criteria for categorizing different types of security incidents
- Escalation Procedures: Defined triggers and processes for escalating incidents to appropriate stakeholders
- Communication Protocols: Standardized methods for communicating about security incidents internally and externally
- Documentation Requirements: Comprehensive incident documentation for legal, compliance, and learning purposes
Standard Operating Procedures SOCs require detailed procedures for:
- Daily operational tasks and responsibilities
- Tool configuration and maintenance
- Report generation and distribution
- Training and onboarding new team members
- Quality assurance and performance measurement
Physical and Logical Security Requirements
Physical Security SOC facilities require enhanced physical security measures:
- Restricted access controls with multi-factor authentication
- Surveillance and monitoring systems
- Secure storage for sensitive equipment and documentation
- Environmental controls for equipment protection
Logical Security Digital security measures for SOC operations:
- Network segmentation to protect SOC systems
- Privileged access management for SOC tools and systems
- Encryption for data in transit and at rest
- Regular security assessments of SOC infrastructure
Budget and Financial Requirements
Initial Investment Setting up a SOC requires significant upfront investment:
- Technology licensing and hardware costs ($500K-$2M+ depending on organization size)
- Facility setup and security measures ($100K-$500K)
- Initial staffing and training costs ($1M-$3M+ annually for personnel)
- Professional services for implementation and setup ($100K-$500K)
Ongoing Operational Costs Annual operational expenses include:
- Personnel costs (typically 60-70% of total SOC budget)
- Technology maintenance and licensing renewals
- Training and certification programs
- Facility and operational expenses
Benefits of Getting a SOC for Cybersecurity Report
The value of implementing a Security Operations Center extends far beyond simple threat detection. Organizations that invest in SOC capabilities realize significant benefits across multiple dimensions of their business operations.
Enhanced Security Posture and Threat Detection
Proactive Threat Identification SOCs transform organizations from reactive to proactive security postures. Instead of waiting for security incidents to cause damage, SOC teams continuously hunt for threats, analyze suspicious activities, and identify potential security issues before they escalate. This proactive approach significantly reduces the likelihood of successful cyberattacks and minimizes their potential impact.
Reduced Mean Time to Detection and Response Studies consistently show that organizations with mature SOC capabilities detect and respond to security incidents much faster than those without. The average time to identify a breach drops from 287 days (industry average) to under 30 days for organizations with effective SOCs. Similarly, containment times improve dramatically, often from weeks to hours or minutes.
Comprehensive Visibility SOCs provide organizations with unprecedented visibility into their security posture. Through centralized monitoring and analysis, security teams can identify patterns, trends, and anomalies that might otherwise go unnoticed. This comprehensive view enables better decision-making and more effective security investments.
Business Continuity and Risk Mitigation
Minimized Business Disruption By detecting and responding to threats quickly, SOCs help minimize business disruption from security incidents. Faster incident response means less downtime, reduced data loss, and quicker recovery to normal operations. This translates directly to preserved revenue and reduced business impact.
Regulatory Compliance Support SOCs play a crucial role in helping organizations maintain compliance with various regulatory requirements. They provide the monitoring, documentation, and reporting capabilities required by regulations such as PCI DSS, HIPAA, GDPR, and industry-specific compliance frameworks.
Risk Quantification and Management SOC operations generate valuable data about an organization's security posture and risk profile. This information enables better risk management decisions and helps executives understand the true cybersecurity risks facing their organization.
Cost Benefits and Return on Investment
Reduced Incident Costs The cost of implementing and operating a SOC is typically far less than the potential cost of a major security incident. With average breach costs exceeding $4 million globally, even preventing a single major incident can justify SOC investments.
Insurance Benefits Many cyber insurance providers offer reduced premiums for organizations with mature SOC capabilities. The improved security posture and reduced risk profile that SOCs provide make organizations more attractive to insurers.
Operational Efficiency SOCs automate many routine security tasks, freeing up other IT personnel to focus on strategic initiatives. This improved efficiency can lead to cost savings across the broader IT organization.
Competitive Advantages and Customer Trust
Customer Confidence Organizations with robust SOC capabilities can demonstrate their commitment to cybersecurity to customers and partners. This enhanced trust can lead to competitive advantages, particularly when dealing with security-conscious customers or partners.
Vendor and Partner Requirements Many large organizations now require their vendors and partners to demonstrate mature cybersecurity capabilities, including SOC operations. Having a SOC can open up business opportunities that might otherwise be unavailable.
Brand Protection By preventing or minimizing security incidents, SOCs help protect organizational reputation and brand value. In an era where security breaches can cause lasting reputational damage, this protection is invaluable.
Strategic Business Benefits
Digital Transformation Enablement SOCs provide the security foundation necessary for organizations to confidently pursue digital transformation initiatives. With robust security monitoring and response capabilities in place, organizations can adopt new technologies and business models with reduced security risk.
Informed Decision-Making SOC operations generate rich data about security threats, trends, and organizational vulnerabilities. This information enables more informed security investment decisions and helps organizations prioritize their cybersecurity efforts effectively.
Scalable Security Well-designed SOCs can scale with organizational growth, providing consistent security capabilities as organizations expand their digital footprint, enter new markets, or acquire new companies.
Conclusion
The Security Operations Center represents a fundamental shift in how organizations approach cybersecurity, from reactive defense to proactive protection. As cyber threats continue to evolve in sophistication and frequency, SOCs have become not just beneficial but essential for organizations serious about protecting their digital assets and maintaining business continuity.
Understanding what SOC stands for in cybersecurity – Security Operations Center – is just the beginning. The real value comes from recognizing that SOCs represent a comprehensive approach to cybersecurity that combines people, processes, and technology in a coordinated effort to detect, investigate, and respond to security threats.
The distinction between SOC for cybersecurity and SOC 2 compliance is important for organizations to understand. While they serve different purposes, both are valuable components of a comprehensive security strategy. SOC cybersecurity operations provide the ongoing monitoring and response capabilities that keep organizations secure, while SOC 2 compliance demonstrates to stakeholders that appropriate security controls are in place and operating effectively.
The requirements for implementing SOC capabilities are significant, spanning staffing, technology, processes, and budget considerations. However, the benefits far outweigh the costs for most organizations. Enhanced security posture, reduced incident response times, improved compliance capabilities, and competitive advantages all contribute to a compelling return on investment.
As we look to the future, SOCs will continue to evolve, incorporating artificial intelligence, machine learning, and automation to become more efficient and effective. Organizations that invest in building mature SOC capabilities today will be better positioned to handle the cybersecurity challenges of tomorrow.
Unlock the power of SOC with Regulance AI—start strengthening your cybersecurity today.