What Are the Main Types of Third-Party Risk Management and How Can They Protect Your Business?


Introduction
From cloud service providers and payment processors to logistics partners and professional consultants, third-party relationships have become the backbone of modern commerce. However, with these partnerships comes a sobering reality: your organization is only as secure as your weakest vendor link.
Consider this scenario. A major retailer experiences a devastating data breach, not because of flaws in their own security infrastructure, but because a third-party HVAC vendor had unrestricted access to their network. Millions of customer records were compromised, resulting in billions in losses and irreparable damage to the brand's reputation.
Third party risk management has evolved from a compliance checkbox to a strategic business imperative. Organizations that fail to properly assess, monitor, and mitigate risks from external partnerships expose themselves to financial losses, regulatory penalties, operational disruptions, and reputational damage. This comprehensive guide explores the various types of third party risk management, helping you build a robust framework that protects your organization while enabling productive partnerships.
What is Third Party Risk Management?
Third party risk management (TPRM) is the systematic process of identifying, assessing, monitoring, and mitigating risks associated with external entities that have access to your organization's data, systems, facilities, or operations. These third parties include vendors, suppliers, contractors, service providers, consultants, and business partners who play a role in your business ecosystem.
TPRM recognizes that when you engage with external organizations, you're essentially extending your risk profile beyond your direct control. A vendor's cybersecurity vulnerability becomes your vulnerability. A supplier's compliance failure becomes your compliance failure. A partner's operational disruption becomes your operational disruption.
The scope of third party risk management encompasses several critical dimensions. It involves conducting thorough due diligence before onboarding new vendors, continuously monitoring existing relationships for emerging risks, ensuring contractual obligations include appropriate risk controls, maintaining compliance with industry regulations and data protection laws, and establishing clear protocols for incident response when third-party failures occur.
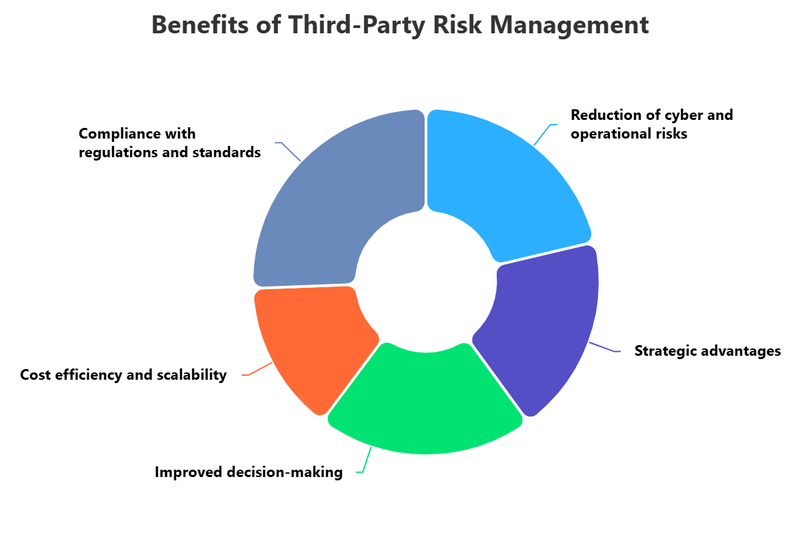
Benefits of Third Party Risk Management
Implementing a comprehensive third party risk management program delivers substantial benefits that extend far beyond risk mitigation. These advantages touch every corner of your organization, from the boardroom to operational teams.
Enhanced Security Posture
A robust TPRM program significantly strengthens your overall security framework. By thoroughly vetting vendors' cybersecurity practices, requiring regular security assessments, and monitoring for vulnerabilities, you create multiple layers of defense against cyber threats. This proactive approach helps prevent data breaches, protects intellectual property, and safeguards customer information from unauthorized access.
Regulatory Compliance and Reduced Legal Exposure
Regulatory bodies worldwide have intensified their focus on third-party oversight. From GDPR in Europe to CCPA in California, regulations increasingly hold organizations accountable for their vendors' handling of data. A structured TPRM program ensures you meet these regulatory requirements, avoiding costly penalties and legal complications. Documentation of your due diligence efforts also provides valuable evidence of good faith compliance should issues arise.
Operational Continuity and Resilience
Understanding the critical dependencies your organization has on third parties allows you to develop contingency plans and backup strategies. When you've assessed which vendors are essential to your operations and identified potential points of failure, you can implement redundancies and alternative arrangements. This preparation minimizes disruptions when vendor issues occur, ensuring your business continues functioning even during challenging circumstances.
Financial Protection
The financial implications of third-party failures can be staggering. Beyond direct losses from breaches or service disruptions, organizations face regulatory fines, legal settlements, remediation costs, and lost revenue. TPRM helps you avoid these expensive scenarios by identifying and addressing risks before they materialize. Additionally, understanding vendor financial stability prevents you from becoming overly dependent on partners who might suddenly cease operations.
Improved Vendor Relationships and Performance
Contrary to the perception that TPRM creates adversarial relationships, it actually fosters stronger partnerships. When expectations around security, compliance, and performance are clearly defined and regularly assessed, both parties benefit from improved communication and accountability. Vendors who demonstrate strong risk management practices become more valuable partners, while those falling short receive opportunities to improve.
Reputation Management and Brand Protection
Your reputation is intrinsically linked to the companies you partner with. A vendor's ethical lapses, security failures, or compliance violations can quickly become associated with your brand in the public consciousness. TPRM helps you select partners whose values and practices align with your standards, protecting the reputation you've worked hard to build.
Informed Decision-Making
The insights gained through TPRM processes provide valuable intelligence for strategic decision-making. Understanding the risk landscape helps executives make informed choices about which partnerships to pursue, how to structure contracts, where to allocate resources, and which vendors merit expanded relationships versus those requiring closer oversight or replacement.
Types of Third Party Risk Management
Third party risk management encompasses various specialized domains, each addressing specific categories of risk that vendors might introduce to your organization. Understanding these different types allows you to build a comprehensive risk management framework tailored to your unique business environment.
Cybersecurity Risk Management
Cybersecurity risk management focuses on protecting your organization from digital threats introduced through third-party access to your systems, networks, or data. This type of TPRM has become increasingly critical as cyberattacks grow more sophisticated and vendors require deeper integration with your IT infrastructure.
This involves assessing vendors' security architectures, encryption practices, access controls, and incident response capabilities. You'll evaluate their vulnerability management programs, penetration testing results, and security certifications like SOC 2 or ISO 27001. Continuous monitoring includes tracking vendors' patch management practices, monitoring for data breaches affecting them, and ensuring they maintain appropriate security awareness training for their staff.
The devastating consequences of cybersecurity failures through third parties make this a top priority. When vendors have access to sensitive customer data, financial information, or proprietary systems, their security becomes your security. Effective cybersecurity risk management requires technical assessments, contractual security requirements, and ongoing vigilance.
Data Privacy and Compliance Risk Management
Data privacy risk management addresses how third parties collect, process, store, and protect personal and sensitive information on your behalf. With data protection regulations becoming more stringent globally, organizations face significant penalties when vendors mishandle data.
This type of TPRM involves verifying vendors' compliance with relevant regulations like GDPR, CCPA, HIPAA, or industry-specific requirements. You'll assess their data processing agreements, cross-border data transfer mechanisms, data retention and deletion policies, and their procedures for handling data subject requests.
Key activities include mapping data flows to understand what information vendors access, conducting data protection impact assessments for high-risk processing activities, and ensuring vendors maintain appropriate technical and organizational measures to protect personal data. You'll also need to verify that vendors conduct their own third-party due diligence, as you may be held accountable for their subprocessors as well.
Financial Risk Management
Financial risk management evaluates the financial health and stability of your third-party relationships. A vendor's financial distress can disrupt your operations, result in sudden service termination, or lead to security compromises as cost-cutting measures weaken their controls.
This involves analyzing financial statements, credit ratings, and market indicators to assess vendor solvency and stability. You'll monitor for warning signs like declining revenues, mounting debt, cash flow problems, or changes in ownership that might indicate financial vulnerability.
Beyond vendor stability, financial risk management also encompasses transaction risks, such as fraud, errors in billing, unauthorized charges, and foreign exchange exposure. For critical vendors, you might establish financial covenants in contracts, require financial reporting obligations, or even secure backup vendors to ensure continuity if financial failure occurs.
Operational Risk Management
Operational risk management focuses on potential disruptions to your business processes caused by vendor performance failures, service outages, or operational deficiencies. This type of TPRM ensures that third parties can reliably deliver the services your organization depends upon.
Assessment areas include service delivery capabilities and track records, business continuity and disaster recovery plans, capacity planning and scalability, quality management systems, and key person dependencies that might create vulnerabilities. You'll evaluate vendors' operational resilience through scenario analysis, testing their backup procedures, and reviewing their history of service disruptions.
For critical vendors, establishing clear service level agreements (SLAs) with defined performance metrics creates accountability and triggers for escalation when standards aren't met. Regular performance reviews help identify degradation in service quality before it becomes critical.
Reputational Risk Management
Reputational risk management addresses the potential damage to your organization's brand and standing that can result from third-party actions or associations. In an era of social media amplification and heightened stakeholder expectations, reputational damage can occur swiftly and prove difficult to repair.
This involves assessing vendors' own reputational standing, reviewing their history of controversies or negative publicity, evaluating their corporate social responsibility practices, examining their ethical standards and business practices, and monitoring their public perception among customers and stakeholders.
Key considerations include vendors' labor practices, environmental impact, treatment of data and privacy, transparency and honesty in communications, and response to past incidents. You'll want to understand whether vendors' values align with your organization's commitments, particularly around issues your stakeholders care about deeply.
Social media monitoring, news tracking, and stakeholder feedback mechanisms help you stay aware of emerging reputational concerns before they escalate. Contractual provisions around conduct standards and communication protocols during incidents provide important protections.
Strategic Risk Management
Strategic risk management examines how third-party relationships might affect your organization's long-term objectives, competitive position, and strategic flexibility. This forward-looking approach considers whether vendor partnerships enable or constrain your strategic vision.
Assessment areas include vendor lock-in and dependency risks, alignment of vendor strategy with your business direction, innovation capabilities and technology roadmaps, market position and competitive dynamics, and merger and acquisition activities that might change the relationship.
This type of risk management involves deeper strategic conversations with key vendors about their future plans, ensuring transparency around product development, geographic expansion, or pivot strategies that might affect your partnership. You'll evaluate whether growing dependence on specific vendors creates negotiating disadvantages or limits your ability to adopt emerging technologies.
Legal and Contractual Risk Management
Legal risk management focuses on contractual terms, liability allocation, intellectual property protections, and legal compliance across your vendor portfolio. Poorly structured agreements can leave your organization exposed to unexpected liabilities or without adequate recourse when problems occur.
This involves reviewing and negotiating contract terms around indemnification clauses, liability caps and carve-outs, warranty provisions and remedies, termination rights and transition assistance, insurance requirements, and audit rights to verify compliance.
You'll assess vendors' legal and regulatory compliance across relevant jurisdictions, ensuring they maintain proper licenses, permits, and certifications. Understanding jurisdictional issues becomes particularly important with international vendors, where differing legal frameworks create complexity around dispute resolution, enforcement, and data handling.
Fourth-Party Risk Management
Fourth-party risk management extends your oversight to your vendors' vendors, the subcontractors and service providers that your direct third parties rely upon. Since your vendors' dependencies can introduce risks to your organization, comprehensive TPRM includes understanding and managing this extended ecosystem.
This requires ensuring your vendors conduct appropriate due diligence on their subcontractors, obtaining transparency into critical fourth-party relationships, including contractual flow-down requirements that extend your risk standards, and monitoring for concentration risks where multiple vendors depend on the same fourth parties.
Fourth-party risk management acknowledges that modern supply chains are deeply interconnected. A failure several layers removed from your direct relationships can still cascade into significant disruption for your operations.
Third Party Risk Management Best Practices
Implementing effective third party risk management requires more than understanding different risk types. Success depends on following proven best practices that create sustainable, scalable programs aligned with your organization's risk appetite and strategic objectives.
Establish Executive Sponsorship and Governance
Strong third party risk management begins at the top. Executive leadership must champion TPRM initiatives, allocate adequate resources, and integrate risk considerations into strategic decision-making. Establish a cross-functional governance committee with representatives from procurement, legal, IT, compliance, and business units to oversee the program. This ensures TPRM isn't siloed within a single department but represents enterprise-wide priorities.
Define clear roles and responsibilities across your organization. Who conducts initial vendor assessments? Who approves high-risk engagements? Who monitors ongoing compliance? Document these responsibilities in policies and procedures that create accountability.
Implement Risk-Based Vendor Classification
Not all vendors present equal risk. Applying the same rigorous assessment to a low-value office supply vendor as to your cloud infrastructure provider wastes resources and creates inefficiency. Develop a classification methodology that categorizes vendors based on factors like data access levels, criticality to operations, regulatory implications, financial exposure, and reputational impact.
This risk-based approach allows you to focus intensive due diligence on high-risk vendors while streamlining processes for lower-risk relationships. Typically, organizations use tiering systems, critical vendors receiving comprehensive annual assessments, moderate-risk vendors getting periodic reviews, and low-risk vendors undergoing light-touch monitoring.
Standardize Due Diligence Processes
Create standardized assessment questionnaires, evaluation criteria, and scoring methodologies that ensure consistency across vendor evaluations. These tools should address all relevant risk types for your industry while remaining adaptable to specific vendor contexts.
Leverage industry-standard frameworks like the Shared Assessments SIG questionnaire, NIST Cybersecurity Framework, or ISO standards rather than creating entirely custom assessment tools. This reduces vendor fatigue from answering different questions from every client and allows you to benchmark results against industry norms.
Due diligence should occur before contract execution, with risk findings informing contract negotiations, pricing discussions, and go/no-go decisions. Establish clear criteria for acceptable risk levels and escalation paths for exceptions.
Build Continuous Monitoring Capabilities
A vendor deemed low-risk today might experience a data breach, financial difficulty, or leadership change tomorrow. Implement continuous monitoring using technology solutions that track vendors' security posture, financial health, regulatory compliance, and reputational standing.
Automated monitoring tools can flag concerning developments like credit rating downgrades, data breach disclosures, executive departures, regulatory actions, or negative news coverage. Combine automated monitoring with periodic reassessments—annual reviews for critical vendors, biennial for moderate-risk relationships.
Performance monitoring through SLA tracking, incident management, and stakeholder feedback provides additional visibility into vendor reliability and service quality.
Foster Collaborative Vendor Relationships
View TPRM as a partnership rather than a policing activity. Communicate clearly with vendors about your risk requirements and expectations from the outset. When assessments reveal gaps, work collaboratively to develop remediation plans rather than immediately terminating relationships.
Many organizations implement vendor risk management portals where partners can submit documentation, complete assessments, and track remediation activities. This transparency builds trust and reduces administrative burden for both parties.
Regular business reviews with critical vendors should include risk discussions alongside performance and strategic topics. This integration demonstrates that risk management supports business objectives rather than obstructing them.
Maintain Comprehensive Documentation
Document all aspects of your TPRM program; policies and procedures, risk assessments and scores, contract terms and amendments, incidents and responses, and remediation plans and progress. This documentation serves multiple purposes: demonstrating regulatory compliance, supporting audit requirements, enabling institutional knowledge retention, informing future vendor decisions, and providing evidence in legal disputes.
Implement a centralized vendor risk management system or platform that consolidates this information, making it accessible to stakeholders who need it while maintaining appropriate confidentiality controls.
Prepare for Incidents and Exits
Despite best efforts, vendor incidents will occur. Establish clear incident response procedures that address vendor-related events, including notification requirements to ensure vendors alert you promptly, assessment protocols to understand impact, containment and remediation steps, communication plans for stakeholders and regulators, and lessons learned processes to prevent recurrence.
Similarly, plan for vendor relationship terminations. Contracts should include clear exit provisions covering data return or destruction, transition assistance periods, knowledge transfer requirements, and post-termination support obligations. For critical vendors, consider maintaining exit readiness through documented transition plans and identified alternative providers.
Invest in Training and Awareness
TPRM effectiveness depends on people across your organization understanding their roles. Provide training for procurement teams on identifying risk considerations during vendor selection, business unit leaders on escalation requirements, contract managers on key risk terms, IT staff on technical assessment capabilities, and executives on strategic risk implications.
Create awareness campaigns that help employees recognize red flags in vendor interactions and understand reporting mechanisms for concerns.
Leverage Technology and Automation
Modern TPRM programs increasingly rely on technology to manage scale and complexity. Consider solutions that offer vendor inventory management, automated risk assessments, continuous monitoring, workflow automation for approvals, centralized documentation repositories, and reporting and analytics capabilities.
Technology shouldn't replace human judgment but rather enhance efficiency, consistency, and coverage. Even sophisticated organizations balance automation with relationship-based oversight for their most critical vendors.
How Can Regulance Help with Third Party Risk Management
Regulance offers specialized expertise in building and optimizing third party risk management programs tailored to your organization's unique risk profile and industry requirements. Their services encompass program design and implementation, helping establish comprehensive TPRM frameworks aligned with regulatory expectations and business objectives.
The Regulance team provides technology enablement support, assisting with vendor risk platform selection and integration that streamlines assessment workflows and monitoring capabilities. They offer ongoing advisory services, including policy development, vendor assessment facilitation, and remediation guidance that keeps your program effective as your vendor ecosystem evolves.
With deep regulatory knowledge across multiple jurisdictions and industries, Regulance helps organizations navigate complex compliance landscapes while maintaining productive vendor relationships that support business growth.
FAQs
What is the difference between third-party and fourth-party risk management?
Third-party risk management focuses on risks from vendors and partners you directly contract with, while fourth-party risk management extends to your vendors' subcontractors and suppliers. Essentially, fourth parties are your vendors' vendors. Since failures in these extended relationships can still impact your organization, comprehensive TPRM programs increasingly address fourth-party risks through contractual flow-down requirements and transparency provisions.
How often should we reassess vendor risks?
Assessment frequency should be risk-based. Critical vendors typically warrant annual comprehensive reassessments, moderate-risk vendors might be reviewed every two years, and low-risk vendors could be reassessed every three years or upon significant changes. Additionally, implement continuous monitoring that flags concerning developments between formal assessments, and conduct ad-hoc reviews when vendors undergo major changes like mergers, leadership transitions, or security incidents.
What are the biggest challenges in implementing third party risk management?
Organizations commonly struggle with resource constraints limiting their ability to assess all vendors adequately, vendor fatigue from repetitive assessment requests across their client base, lack of executive support treating TPRM as a compliance checkbox rather than strategic priority, poor integration between TPRM and procurement processes, limited visibility into vendor ecosystems and fourth parties, and difficulty balancing thoroughness with business velocity. Overcoming these challenges requires executive sponsorship, risk-based prioritization, standardized assessments, and appropriate technology enablement.
Do small businesses need third party risk management programs?
Absolutely. While small businesses may implement simpler, scaled-down versions compared to enterprise programs, the fundamental need remains. Small businesses often face proportionally greater impact from vendor failures since they typically have less resilience and fewer backup options. A basic TPRM approach for small businesses might include standardized vendor questionnaires, clear contract terms addressing key risks, periodic vendor performance reviews, and monitoring for significant vendor changes or incidents. The principles remain the same even if the processes are lighter-weight.
What role does artificial intelligence play in modern TPRM?
AI and machine learning increasingly enhance TPRM capabilities through automated analysis of vendor assessment responses to identify inconsistencies or concerns, continuous monitoring of vast data sources for vendor risk signals, predictive analytics identifying vendors likely to experience future problems, natural language processing to review contracts and identify problematic terms, and risk scoring algorithms that provide consistent, data-driven vendor classifications. While AI augments TPRM efficiency and coverage, human expertise remains essential for interpreting results, making nuanced judgment calls, and managing vendor relationships.
How do we handle vendors who refuse to complete security assessments?
First, clearly communicate why assessments are necessary, framing them as partnership enablers rather than obstacles. Offer to accept alternative evidence like existing certifications, recent audits for other clients, or industry-standard frameworks they've already completed. For critical vendors, consider escalating discussions to executive levels or making assessment completion a contractual requirement. If vendors remain unwilling and alternatives exist, you may need to select different partners. However, if the vendor provides unique capabilities, work with risk and legal teams to implement compensating controls, enhanced monitoring, or contractual protections that mitigate the elevated risk.
Conclusion
Third party risk management has evolved from a niche compliance function to a strategic imperative that touches every aspect of modern business operations. As organizations increasingly rely on external partners for critical capabilities; from cloud infrastructure and payment processing to logistics and customer service, the risks these relationships introduce can no longer be treated as afterthoughts.
The various types of third party risk management discussed in this guide reflect the multifaceted nature of modern vendor relationships. Cybersecurity risks threaten your data and systems. Financial risks jeopardize operational continuity. Reputational risks damage the brand you've worked years to build. Legal risks create unexpected liabilities. Each demands specific attention within your comprehensive TPRM framework.
Implementing effective third party risk management involves building the confidence and assurance that allow your organization to pursue strategic partnerships boldly, knowing you understand the risks involved and have measures in place to manage them. The best TPRM programs balance thoroughness with business enablement, applying risk-based approaches that focus intensive oversight where it matters most.
The investment in third party risk management pays dividends through prevented incidents, maintained compliance, protected reputation, and operational resilience. As regulatory expectations continue tightening and stakeholders demand greater accountability, organizations with mature TPRM capabilities will find themselves better positioned competitively, able to demonstrate the trustworthiness that customers, partners, and regulators increasingly require.
Building a comprehensive third party risk management program takes time, resources, and commitment. Start with executive sponsorship and clear governance. Classify your vendors by risk level. Implement standardized assessment processes. Leverage technology for efficiency and scale. Foster collaborative relationships with your partners. Document everything. Prepare for incidents.
Ready to Strengthen Your Third Party Risk Management Program?
Regulance has the expertise to guide you every step of the way.
Take action today:
- Schedule a consultation to assess your current third party risk exposure
- Get expert guidance on implementing industry-leading TPRM best practices
- Leverage proven frameworks that align with your business objectives and regulatory obligations
- Transform vendor relationships from potential liabilities into strategic assets
Contact Regulance now to discover how a robust third party risk management program can protect your organization while enabling confident business growth.