Understanding HIPAA Compliance: A Comprehensive Guide to Protecting Patient Privacy


In today's healthcare landscape, safeguarding patient privacy is more critical than ever. With the increasing digitization of health records and the growing number of cyber threats, understanding HIPAA compliance has become essential for healthcare providers, administrators, and patients alike. This comprehensive guide delves into the core principles of HIPAA (Health Insurance Portability and Accountability Act) and its pivotal role in protecting sensitive patient information. From uncovering the key regulations to offering practical strategies for achieving compliance, this guide is designed to empower you with the knowledge necessary to navigate the complexities of patient privacy. Whether you're a seasoned professional or new to the field, mastering HIPAA compliance not only promotes a culture of trust but also enhances the overall quality of care. Join us as we explore the essential steps to ensure that patient confidentiality remains a top priority in your practice.
What is HIPAA and Why is It Important?

The Health Insurance Portability and Accountability Act (HIPAA) was enacted by the U.S. Congress in 1996 with the dual purpose of ensuring the portability of health insurance coverage and protecting the privacy and security of healthcare information. Its significance has grown over the years, particularly with the advent of electronic health records (EHRs) and increased data sharing across healthcare platforms. HIPAA sets the standard for protecting sensitive patient data, ensuring that individuals' health information is properly handled and reducing the risks associated with data breaches.
HIPAA is crucial because it establishes national standards for the protection of individually identifiable health information, known as protected health information (PHI). These standards help to maintain patient confidentiality, prevent unauthorized access to medical records, and ensure that health information is used appropriately. By adhering to HIPAA regulations, healthcare providers and organizations demonstrate their commitment to patient privacy, which fosters trust and confidence among patients.
Moreover, HIPAA compliance is not just a legal requirement; it also plays a vital role in enhancing the quality of care. When patients trust that their personal health information is secure, they are more likely to disclose accurate and comprehensive information to their healthcare providers. This transparency is essential for accurate diagnosis, effective treatment, and overall better health outcomes. In essence, HIPAA serves as the backbone of patient privacy and security in the modern healthcare system.
Key Components of HIPAA Compliance
HIPAA compliance is built on several key components, each designed to address different aspects of patient privacy and data security. The first major component is the Privacy Rule, which sets national standards for the protection of PHI and outlines the rights of individuals regarding their health information. This rule applies to healthcare providers, health plans, and healthcare clearinghouses, collectively known as covered entities. It dictates how PHI can be used and disclosed, ensuring that patient information is only shared for legitimate purposes.
The second component is the Security Rule, which specifically addresses the protection of electronic protected health information (ePHI). This rule requires covered entities to implement administrative, physical, and technical safeguards to ensure the confidentiality, integrity, and availability of ePHI. Administrative safeguards include policies and procedures for managing the selection, development, and maintenance of security measures. Physical safeguards involve controlling physical access to protect against unauthorized entry, while technical safeguards focus on technology solutions to secure ePHI.
Another critical component is the Breach Notification Rule, which mandates that covered entities and their business associates notify affected individuals, the Department of Health and Human Services (HHS), and, in some cases, the media, following a breach of unsecured PHI. This rule ensures that patients are informed of any potential compromise of their health information, allowing them to take protective measures if necessary. Additionally, the Enforcement Rule outlines the penalties for HIPAA violations, ranging from monetary fines to criminal charges, emphasizing the importance of compliance.
1. The Privacy Rule: Protecting Patient Information
The Privacy Rule is a cornerstone of HIPAA, establishing national standards for the protection of PHI and granting individuals significant rights over their health information. One of the primary objectives of the Privacy Rule is to ensure that PHI is properly protected while allowing the flow of health information needed to provide high-quality healthcare and protect public health. This balance is crucial in maintaining patient trust and facilitating effective healthcare delivery.
Under the Privacy Rule, covered entities must implement appropriate safeguards to protect the privacy of PHI and limit the use and disclosure of such information. PHI includes any information that relates to an individual's past, present, or future physical or mental health condition, the provision of healthcare, or payment for healthcare, and that can identify the individual. The rule allows PHI to be used and disclosed without patient authorization for purposes such as treatment, payment, and healthcare operations, but it imposes strict requirements for other uses and disclosures.
The Privacy Rule also grants individuals several rights regarding their PHI. Patients have the right to access their health information, request corrections, and obtain an accounting of disclosures. They can also request restrictions on certain uses and disclosures and communicate with healthcare providers through alternative means or locations. These rights empower patients to take an active role in managing their health information, ensuring that they have control over their personal data and can trust that it is handled appropriately.
2. The Security Rule: Safeguarding Electronic Health Data
As the healthcare industry increasingly relies on electronic health records and digital data exchange, the Security Rule has become a critical component of HIPAA compliance. The Security Rule establishes national standards to protect ePHI created, received, maintained, or transmitted by covered entities. Its primary goal is to ensure the confidentiality, integrity, and availability of ePHI while protecting against anticipated threats, unauthorized access, and other security risks.
The Security Rule requires covered entities to implement a combination of administrative, physical, and technical safeguards to protect ePHI. Administrative safeguards involve policies and procedures that manage the selection, development, and maintenance of security measures. This includes conducting risk analyses, training workforce members, and developing contingency plans for responding to security incidents. Administrative safeguards ensure that security measures are properly managed and integrated into the organization's operations.
Physical safeguards focus on controlling physical access to facilities and equipment that store ePHI. This includes implementing measures such as facility access controls, workstation security, and device and media controls. By restricting physical access to authorized personnel and ensuring that equipment is properly secured, covered entities can prevent unauthorized access to ePHI and protect against theft or loss of devices containing sensitive information.
Technical safeguards involve the use of technology solutions to protect ePHI. This includes implementing access controls, such as unique user identification and authentication procedures, to ensure that only authorized individuals can access ePHI. It also involves using encryption and other methods to protect ePHI during transmission and storage, as well as implementing audit controls to monitor access and activity related to ePHI. By employing these technical measures, covered entities can enhance the security of their electronic health data and reduce the risk of data breaches.
Understanding PHI: What Constitutes Protected Health Information?
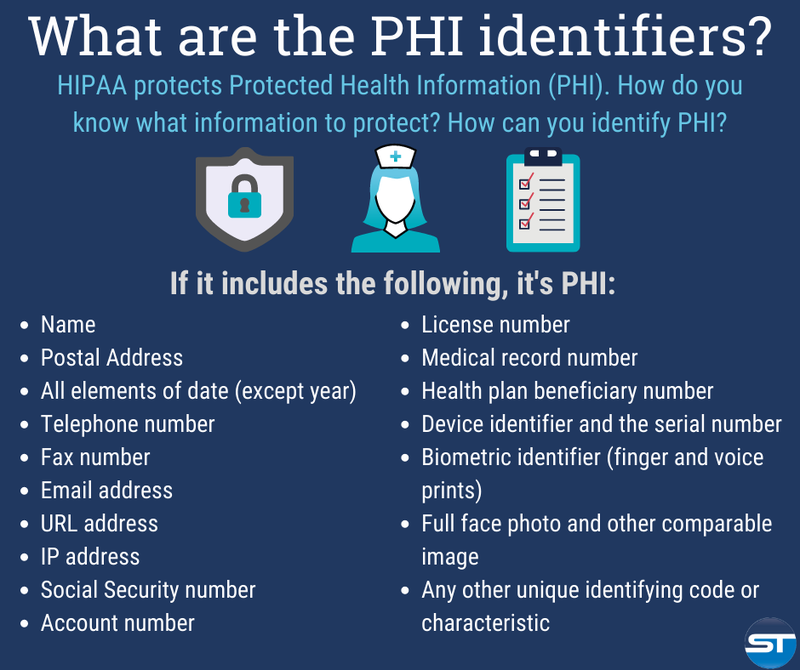
Protected Health Information (PHI) is a central concept in HIPAA compliance, as it defines the types of information that require protection under the law. PHI encompasses any information that relates to an individual's past, present, or future physical or mental health condition, the provision of healthcare, or payment for healthcare, and that can be used to identify the individual. This broad definition includes a wide range of data, from medical records and treatment plans to billing information and demographic details.
PHI includes both paper and electronic records, as well as any other form of media that contains patient information. It covers data such as names, addresses, birth dates, Social Security numbers, medical record numbers, and any other information that could be used to identify a patient. Additionally, PHI includes information about an individual's health status, diagnosis, treatment, and any other details related to their healthcare. This comprehensive scope ensures that all aspects of patient information are protected under HIPAA.
It is important to note that not all health-related information is considered PHI under HIPAA. For example, health information that has been de-identified, meaning that all identifiers have been removed to prevent the possibility of identifying the individual, is not considered PHI. De-identification requires removing specific identifiers and ensuring that there is no reasonable basis to believe that the remaining information could be used to identify the individual. This process allows for the use of health data in research, public health, and other areas without compromising patient privacy.
HIPAA Compliance Requirements for Healthcare Providers
Healthcare providers, as covered entities under HIPAA, have a range of compliance requirements that they must meet to protect patient privacy and secure PHI. These requirements encompass various aspects of their operations, from administrative procedures to technical safeguards, and are designed to ensure that PHI is handled appropriately at all times. By adhering to these requirements, healthcare providers can mitigate risks, prevent data breaches, and maintain patient trust.
One of the primary requirements for healthcare providers is to implement comprehensive policies and procedures that address the protection of PHI. These policies should cover areas such as access controls, data encryption, workforce training, and incident response. Healthcare providers must conduct regular risk assessments to identify potential vulnerabilities and develop strategies to address them. This proactive approach helps to ensure that security measures are up-to-date and effective in protecting patient information.
Healthcare providers are also required to provide training to their workforce members on HIPAA regulations and the proper handling of PHI. This training should be conducted regularly and should cover topics such as patient privacy rights, data security practices, and procedures for reporting security incidents. By educating their staff on HIPAA compliance, healthcare providers can reduce the risk of accidental or intentional breaches and ensure that everyone is aware of their responsibilities regarding patient information.
In addition to administrative and training requirements, healthcare providers must implement physical and technical safeguards to protect PHI. Physical safeguards include measures such as securing facilities, controlling access to workstations, and properly disposing of paper records. Technical safeguards involve the use of technology solutions to secure electronic health data, such as encryption, access controls, and audit logs. By combining these safeguards, healthcare providers can create a robust security framework that protects patient information from various threats.
The Role of Business Associates in HIPAA Compliance
Business associates play a critical role in HIPAA compliance, as they provide services to covered entities that involve the use or disclosure of PHI. A business associate is any individual or organization that performs functions or activities on behalf of a covered entity that involve access to PHI, such as billing services, IT support, legal services, and data storage providers. Under HIPAA, business associates are required to comply with the same standards and regulations as covered entities to ensure the protection of patient information.
To formalize the relationship between covered entities and their business associates, HIPAA mandates the use of Business Associate Agreements (BAAs). These agreements outline the responsibilities of the business associate regarding the protection of PHI and specify the permissible uses and disclosures of such information. BAAs also require business associates to implement safeguards to prevent unauthorized access to PHI and to report any security incidents or breaches to the covered entity. By establishing clear expectations and accountability, BAAs help to ensure that business associates adhere to HIPAA regulations.
Business associates must also conduct their own risk assessments and implement appropriate security measures to protect PHI. This includes developing policies and procedures for handling PHI, providing training to their workforce, and implementing administrative, physical, and technical safeguards. Business associates are subject to the same enforcement actions and penalties as covered entities for HIPAA violations, emphasizing the importance of compliance in their operations.
Collaboration between covered entities and business associates is essential for effective HIPAA compliance. Covered entities should conduct due diligence when selecting business associates, ensuring that they have the necessary safeguards in place to protect PHI. Regular audits and monitoring of business associates' compliance can help to identify and address potential risks. By working together, covered entities and business associates can create a comprehensive approach to protecting patient privacy and securing health information.
Consequences of HIPAA Violations
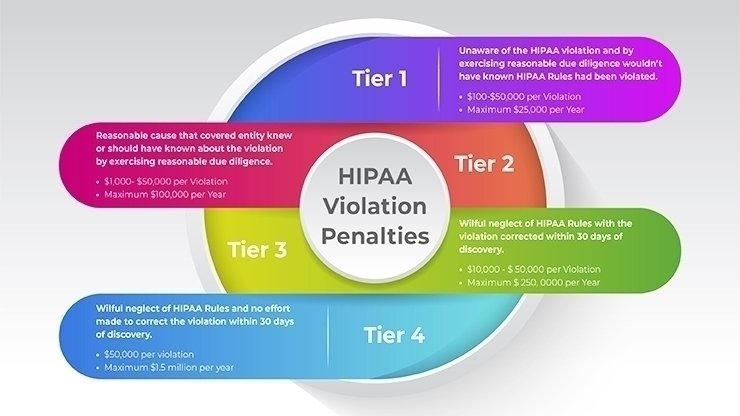
HIPAA violations can have serious consequences for healthcare providers, business associates, and individuals whose PHI is compromised. The Department of Health and Human Services (HHS) Office for Civil Rights (OCR) is responsible for enforcing HIPAA regulations and investigating potential violations. When a violation is identified, the OCR can impose a range of penalties, including monetary fines, corrective action plans, and, in severe cases, criminal charges.
Monetary fines for HIPAA violations are tiered based on the level of culpability and the extent of the harm caused. Fines can range from $100 to $50,000 per violation, with an annual maximum of $1.5 million for identical provisions. The OCR considers factors such as the nature and extent of the violation, the harm caused to individuals, and the organization's history of compliance when determining penalties. In addition to financial penalties, organizations may be required to implement corrective action plans to address the deficiencies that led to the violation.
HIPAA violations can also result in significant reputational damage for healthcare providers and business associates. Data breaches and unauthorized disclosures of PHI can erode patient trust and lead to negative publicity. Patients may be less likely to seek care from organizations with a history of privacy violations, impacting the organization's patient base and revenue. Rebuilding trust after a HIPAA violation can be a lengthy and challenging process, emphasizing the importance of proactive compliance.
In severe cases, HIPAA violations can lead to criminal charges. Individuals who knowingly obtain or disclose PHI in violation of HIPAA regulations can face criminal penalties, including fines and imprisonment. Criminal charges are typically reserved for cases involving intentional misconduct, such as theft of PHI for personal gain or malicious purposes. These severe consequences highlight the importance of adhering to HIPAA regulations and implementing robust safeguards to protect patient information.
Best Practices for Achieving and Maintaining HIPAA Compliance
Achieving and maintaining HIPAA compliance requires a comprehensive and proactive approach to protecting patient information. Healthcare providers and business associates can adopt several best practices to ensure that they meet HIPAA requirements and safeguard PHI. These practices involve a combination of administrative, physical, and technical measures that address various aspects of data security and privacy.
One of the most important best practices is conducting regular risk assessments. Risk assessments help organizations identify potential vulnerabilities and assess the effectiveness of their security measures. By regularly evaluating their security posture, healthcare providers and business associates can identify areas for improvement and implement strategies to address potential risks. Risk assessments should be documented and reviewed periodically to ensure that they remain relevant and effective.
Employee training is another critical component of HIPAA compliance. Workforce members should receive regular training on HIPAA regulations, data security practices, and the proper handling of PHI. Training should cover topics such as patient privacy rights, access controls, incident reporting, and the use of technology solutions to protect ePHI. By educating their staff, organizations can reduce the risk of accidental or intentional breaches and ensure that employees are aware of their responsibilities regarding patient information.
Implementing robust administrative, physical, and technical safeguards is essential for protecting PHI. Administrative safeguards include developing and enforcing policies and procedures, conducting risk assessments, and providing employee training. Physical safeguards involve securing facilities, controlling access to workstations, and properly disposing of paper records. Technical safeguards include using encryption, access controls, and audit logs to protect electronic health data. By combining these safeguards, organizations can create a comprehensive security framework that addresses various threats and vulnerabilities.
Regular monitoring and auditing of compliance activities are also important for maintaining HIPAA compliance. Organizations should conduct internal audits to assess their adherence to HIPAA regulations and identify any areas of non-compliance. Monitoring activities, such as reviewing access logs and conducting security assessments, can help detect potential security incidents and ensure that security measures are effective. By continuously evaluating and improving their compliance efforts, healthcare providers and business associates can maintain a high level of security and protect patient information.
Conclusion: The Future of HIPAA and Patient Privacy
As the healthcare industry continues to evolve, the importance of HIPAA compliance and patient privacy will remain paramount. Advances in technology, such as telemedicine, wearable health devices, and artificial intelligence, present new opportunities for improving patient care but also introduce new challenges for protecting PHI. Healthcare providers, business associates, and regulators must stay vigilant and adapt to these changes to ensure that patient information remains secure.
The future of HIPAA will likely involve updates and enhancements to address emerging threats and technologies. Regulatory bodies may introduce new guidelines and standards to address the unique challenges posed by digital health innovations. Healthcare organizations will need to stay informed about these changes and adjust their compliance strategies accordingly. By staying proactive and adaptable, organizations can continue to protect patient privacy in an increasingly digital healthcare environment.
Ultimately, the principles of HIPAA - protecting patient privacy, ensuring data security, and promoting patient trust - will continue to guide the healthcare industry. By adhering to HIPAA regulations and implementing best practices for data protection, healthcare providers and business associates can create a culture of privacy and security that enhances the overall quality of care. As technology and healthcare continue to evolve, the commitment to protecting patient information will remain a cornerstone of effective and ethical healthcare delivery.
Get started with your HIPAA today using our compliance management service. Regulance uses AI to automate compliance and helps you to get things done properly and faster. Schedule a demo here with our compliance experts to learn more.