The 7 Key GDPR Security Controls Every Business Needs to Protect Customer Data


Introduction
Data breaches make the headlines on a near-daily basis, and the effect can be devastating; not just financially, but to the reputation as well. Organizations that handle the personal information of European Union citizens have a sacred responsibility: to protect that information with robust security controls. That's where GDPR security controls become not just a legal issue, but a business imperative.
The General Data Protection Regulation (GDPR) transformed how organizations approach data security when it came into effect in May 2018. Unlike previous regulations that were often vague about technical requirements, GDPR provides clear guidance on the security controls necessary to protect personal data. It doesn't matter if you're a small startup or a multinational corporation, understanding and implementing GDPR security controls is essential for compliance, customer trust, and long-term business success.
This comprehensive guide explores the seven main GDPR security controls, why they matter, and how they can transform your organization's approach to data protection.
What is GDPR Security Control?
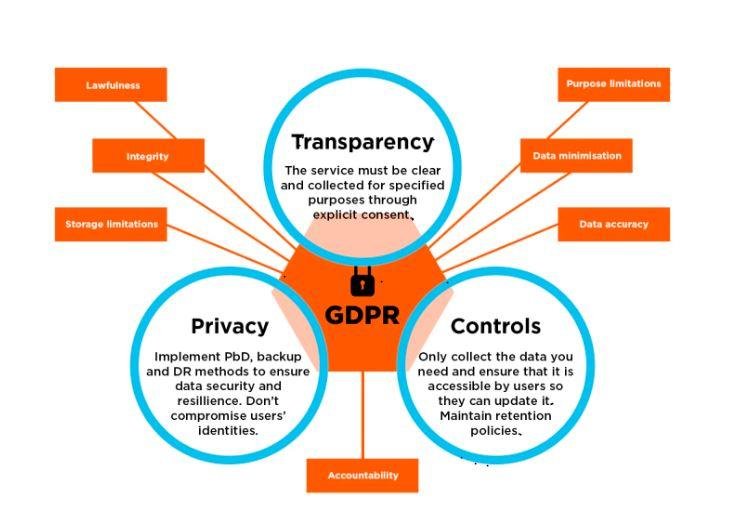
GDPR security controls are technical and organizational measures that organizations must implement to ensure the security of personal data they process. These controls are primarily outlined in Article 32 of the GDPR, which requires controllers and processors to implement "appropriate technical and organizational measures to ensure a level of security appropriate to the risk."
GDPR recognizes that different types of data and different processing activities carry different levels of risk. Processing basic contact information for a newsletter requires different security measures than processing sensitive health records or financial data. GDPR security controls must be proportionate to the risk presented by the data processing activities.
These controls encompass everything from encryption technologies and access management systems to staff training programs and incident response procedures. They represent a holistic approach to data security that considers both the technical infrastructure and the human elements that can make or break data protection efforts.
Why is GDPR Security Controls Required?
Legal Compliance and Avoiding Penalties
Implementing adequate security controls is a legal obligation under GDPR. Organizations that fail to implement appropriate security measures can face administrative fines of up to €10 million or 2% of global annual turnover (whichever is higher) under Article 83(4)(a). European data protection authorities have issued hundreds of millions of euros in fines since GDPR took effect, with many violations relating to inadequate security measures.
Protecting Fundamental Rights
GDPR security controls protect individuals' fundamental right to privacy and data protection. In the digital age, personal data represents an extension of personal identity. When this data is compromised, stolen, or misused, it can have profound impacts on individuals' lives, from identity theft and financial fraud to emotional distress and reputational damage.
Building and Maintaining Trust
In an era where consumers are increasingly aware of data privacy issues, robust security controls are essential for building customer trust. Studies consistently show that consumers are more likely to do business with organizations they trust to protect their data. A single data breach can destroy years of carefully built reputation and customer loyalty.
Business Continuity and Risk Management
GDPR security protects your organization from incurring heavy fines. Data breaches can result in operational disruption, loss of competitive advantage, legal costs, compensation claims, and long-term damage to business relationships. Implementing proper security controls is simply good risk management.
Competitive Advantage
Organizations that excel at data protection can use this as a competitive differentiator. Privacy-conscious consumers actively seek out businesses that demonstrate commitment to protecting personal information. GDPR compliance, done well, becomes a marketing asset rather than just a compliance burden.
7 Main GDPR Security Controls
Article 32 of GDPR outlines the framework for security controls, though it intentionally avoids prescribing specific technologies (as these evolve rapidly). Here are the seven main security controls that form the foundation of GDPR compliance:
1. Pseudonymization and Encryption of Personal Data
Pseudonymization involves replacing identifying information with artificial identifiers, while encryption transforms data into an unreadable format without the proper decryption key. These are GDPR's first line of defense against unauthorized data access.
Even if data is accessed by unauthorized parties, encryption renders it useless without the decryption keys. Pseudonymization allows you to work with data for analytics and testing while minimizing privacy risks.
Implementation examples:
- Encrypting personal data at rest using AES-256 or similar standards
- Implementing SSL/TLS certificates for data in transit
- Using tokenization for payment card information
- Separating identifying information from analytical datasets
- Implementing end-to-end encryption for communications containing personal data
Use industry-standard encryption algorithms, implement robust key management systems, regularly update encryption protocols, and ensure encryption keys are stored separately from encrypted data.
2. Ensuring Confidentiality, Integrity, Availability, and Resilience
These four pillars often abbreviated as CIAR form the foundation of information security:
- Confidentiality: Ensuring data is accessible only to authorized individuals
- Integrity: Protecting data from unauthorized alteration or corruption
- Availability: Ensuring authorized users can access data when needed
- Resilience: Building systems that can withstand and recover from attacks or failures
Data is only valuable if it's reliable, accessible when needed, and protected from tampering. These principles ensure your data protection measures are comprehensive rather than one-dimensional.
Implementation examples:
- Multi-factor authentication (MFA) for system access
- Role-based access controls (RBAC) limiting data access to job requirements
- Regular data backups stored in geographically diverse locations
- Intrusion detection and prevention systems
- Redundant systems and failover capabilities
- Digital signatures and checksums to verify data integrity
Implement defense-in-depth strategies with multiple overlapping security layers, regularly review access permissions, conduct penetration testing, and maintain business continuity plans.
3. Ability to Restore Availability and Access to Personal Data
GDPR explicitly requires the ability to restore access to personal data in a timely manner following a physical or technical incident. This recognizes that perfect prevention isn't always possible, you must also plan for recovery.
Ransomware attacks, natural disasters, hardware failures, and human error can all result in data loss or inaccessibility. The ability to quickly restore data minimizes harm to both individuals and your organization.
Implementation examples:
- Automated daily backups with version control
- Off-site and cloud backup solutions
- Documented recovery time objectives (RTO) and recovery point objectives (RPO)
- Regular restoration testing to verify backup integrity
- Incident response plans with clear escalation procedures
- Hot, warm, or cold standby systems depending on criticality
Follow the 3-2-1 backup rule (three copies of data, two different media types, one off-site), test your disaster recovery plans at least annually, and ensure backup systems are also secured against unauthorized access.
4. Regular Testing, Assessment, and Evaluation of Effectiveness
Security controls aren't "set and forget" solutions. GDPR requires ongoing testing and evaluation to ensure your security measures remain effective as threats evolve.
Cyber threats constantly evolve, and yesterday's adequate security may be today's vulnerability. Regular testing identifies weaknesses before attackers exploit them.
Implementation examples:
- Quarterly vulnerability assessments and annual penetration testing
- Regular security audits (internal and external)
- Continuous security monitoring and logging
- Data Protection Impact Assessments (DPIAs) for high-risk processing
- Security awareness testing (like simulated phishing campaigns)
- Review of security incidents and near-misses
Document all testing activities and remediation efforts, involve third-party security experts for objective assessments, create metrics to track security posture over time, and ensure testing covers both technical controls and human factors.
5. Access Control and Authorization Management
Controlling who can access what data is fundamental to data protection. Access control ensures that only authorized personnel can access personal data, and only to the extent necessary for their job functions.
Insider threats whether malicious or accidental represent a significant portion of data breaches. Proper access controls minimize these risks while maintaining productivity.
Implementation examples:
- Principle of least privilege (users only have minimum necessary access)
- Role-based access control systems
- Regular access reviews and deprovisioning of former employees
- Privileged access management for administrative accounts
- Separation of duties for sensitive operations
- Just-in-time access provisioning
Implement strong password policies, use multi-factor authentication universally, log all access to sensitive data, conduct quarterly access reviews, and immediately revoke access when employees change roles or leave the organization.
6. Data Minimization and Retention Controls
While sometimes overlooked as a security control, data minimization is explicitly mentioned in GDPR's security provisions. The principle is simple: data you don't collect or retain can't be stolen or misused.
Every piece of personal data you hold represents a potential liability. Reducing data collection and implementing clear retention schedules minimizes your attack surface and compliance burden.
Implementation examples:
- Privacy by design in system development
- Automated data deletion based on retention schedules
- Data mapping and inventory management
- Regular data audits to identify and purge unnecessary information
- Anonymization of data when identification is no longer needed
- Purpose limitation enforcement
Document retention requirements based on legal obligations and business needs, implement automated deletion processes, regularly review data holdings against business purposes, and ensure marketing teams aren't collecting data "just in case."
7. Staff Training and Awareness
Technology alone cannot protect data, people are both the strongest link and the weakest link in your security chain. GDPR implicitly requires that staff handling personal data are properly trained and aware of their responsibilities.
Most data breaches involve human error clicking phishing links, misconfiguring systems, or accidentally sending data to wrong recipients. Well-trained staff are your first line of defense.
Implementation examples:
- Mandatory GDPR and data protection training for all staff
- Role-specific training for staff handling sensitive data
- Regular security awareness campaigns
- Simulated phishing exercises
- Clear policies and procedures documentation
- Incident reporting training and non-punitive reporting culture
- Privacy champions program
Make training engaging rather than boring compliance exercises, refresh training annually with updated threat information, track training completion rates, test comprehension rather than just attendance, and ensure executives lead by example.
Strategic Benefits of GDPR Security Controls
Enhanced Data Governance and Operational Efficiency
Implementing GDPR security controls forces organizations to understand what data they hold, where it's stored, who accesses it, and how it flows through the organization. This data mapping exercise often reveals inefficiencies, redundancies, and unnecessary data silos. The result is streamlined operations, reduced storage costs, and better data quality.
Competitive Advantage and Market Differentiation
In markets where trust is a key differentiator such as financial services, healthcare, legal services demonstrating robust data protection can win customers. Many RFPs now include detailed questions about data security practices. Organizations with mature GDPR controls can respond more confidently and comprehensively.
Reduced Risk of Costly Breaches
The average cost of a data breach globally exceeded $4.45 million in 2023, according to IBM's Cost of a Data Breach Report. GDPR security controls significantly reduce the likelihood and potential impact of breaches. The investment in preventive controls is substantially less than the potential costs of a breach.
Improved Vendor and Partner Relationships
Organizations with strong security controls find it easier to establish partnerships and meet vendor security requirements. Many large organizations now require GDPR compliance and specific security controls before doing business with suppliers and partners.
Global Market Access
GDPR security controls align with many international data protection frameworks and regulations. Organizations that meet GDPR standards find it easier to expand into other markets and satisfy various regulatory requirements globally.
Increased Stakeholder Confidence
Investors, board members, and shareholders increasingly recognize data protection as a material business risk. Demonstrating mature security controls increases confidence in your organization's risk management and governance.
Foundation for Digital Transformation
Strong data protection practices enable organizations to confidently pursue digital transformation initiatives, cloud migration, and new data-driven business models without creating unacceptable risks.
Cultural Transformation
Implementing comprehensive security controls often catalyzes broader cultural change, fostering a security-conscious mindset throughout the organization. This cultural shift benefits the organization far beyond GDPR compliance.
Frequently Asked Questions (FAQs)
Q: Do GDPR security controls apply to small businesses?
A: Yes, GDPR applies to all organizations that process personal data of EU residents, regardless of size. However, the principle of proportionality means smaller organizations with lower-risk processing can implement simpler controls. A small business collecting basic contact information needs different security measures than a healthcare provider processing sensitive medical records.
Q: How do I know if my security controls are "appropriate"?
A: GDPR requires security "appropriate to the risk." Consider factors like the nature of data (sensitive vs. non-sensitive), volume of data subjects affected, potential harm from a breach, and state-of-the-art technology. A Data Protection Impact Assessment (DPIA) helps determine appropriate controls for high-risk processing.
Q: Can cloud services help with GDPR security controls?
A: Yes, reputable cloud providers often offer security features that help implement GDPR controls encryption, backup systems, access controls, and compliance certifications. However, you remain responsible for ensuring controls are properly configured and that your cloud provider meets GDPR requirements through appropriate contracts.
Q: How often should security controls be reviewed?
A: At minimum, annually. However, you should review controls more frequently when there are significant changes (new systems, new processing activities, after security incidents) or when new threats emerge. Continuous monitoring provides ongoing assurance.
Q: What happens if we suffer a breach despite having controls?
A: Having demonstrable, appropriate security controls in place can significantly reduce potential fines. GDPR recognizes that no security is perfect. Supervisory authorities consider whether you took reasonable measures and responded appropriately to the incident.
Q: Do we need a Data Protection Officer (DPO) to implement these controls?
A: A DPO is only mandatory for public authorities, organizations whose core activities involve large-scale systematic monitoring, or large-scale processing of special category data. However, many organizations benefit from appointing a DPO or data protection specialist to oversee implementation of security controls.
Q: How do GDPR security controls differ from ISO 27001?
A: There's significant overlap. ISO 27001 is a comprehensive information security management system standard that covers many GDPR security requirements. Organizations with ISO 27001 certification are well-positioned for GDPR compliance, though some GDPR-specific requirements (like data subject rights) go beyond ISO 27001.
Q: Can we outsource GDPR security controls?
A: You can outsource implementation and operation of technical controls to processors or security service providers, but you cannot outsource accountability. Controllers remain responsible for ensuring processors implement appropriate security measures through careful vendor selection and contractual requirements.
Conclusion
GDPR security controls represents a comprehensive framework for protecting what may be your organization's most valuable asset: the trust of individuals whose data you process. The seven main security controls which include: pseudonymization and encryption, ensuring CIAR principles, restoration capabilities, regular testing, access controls, data minimization, and staff training work together to create a robust defense against both external threats and internal vulnerabilities.
The organizations that thrive in our data-driven economy aren't those that view GDPR security controls as a burden, but those that recognize them as an investment in sustainability, trust, and competitive advantage. These controls provide a proven framework for responsible data stewardship that benefits individuals, organizations, and society.
Implementation can be challenging and the landscape continuously evolves. But with a strategic approach, appropriate resources, and commitment from leadership, organizations of all sizes can implement effective GDPR security controls that not only achieve compliance but drive genuine business value.
Ready to Transform GDPR Compliance from Burden to Business Advantage?
Regulance turns GDPR compliance into your competitive edge. We identify your vulnerabilities, build practical roadmaps, and implement security controls that actually work, no checkbox exercises, no wasted resources.
The cost of getting it wrong? Up to €10 million in fines, damaged reputation, lost customers.
Contact Regulance for your complimentary GDPR security assessment. Discover your gaps before regulators or hackers do.