Supply Chain Risks in 2026: What’s Driving Attacks and How Can Businesses Respond?


Introduction
The digital landscape is evolving at breakneck speed, and with it comes a sophisticated breed of cyber threats that keeps security professionals awake at night. Among these, supply chain attacks have emerged as one of the most devastating and difficult-to-defend-against tactics in the cybercriminal's arsenal. Unlike traditional hacking methods that target a single organization, supply chain attacks exploit the interconnected nature of modern business, turning trusted partnerships into dangerous vulnerabilities.
Recent years have witnessed supply chain breaches that have compromised thousands of organizations simultaneously, resulting in billions of dollars in damages and eroding trust in software and services we rely on daily. The SolarWinds breach, the Kaseya ransomware attack, and countless other incidents have demonstrated that no organization is too large or too secure to fall victim to a well-executed supply chain attack.
As we look toward 2026, understanding these threats is essential for survival in an increasingly interconnected digital ecosystem. This comprehensive guide explores what supply chain attacks are, how they work, emerging trends, and most importantly, how your organization can defend against them.
What is a Supply Chain Attack?
A supply chain attack is a sophisticated cyberattack strategy where threat actors compromise a trusted third-party vendor, supplier, or service provider to gain unauthorized access to their target's systems and data. Rather than attacking an organization's defenses directly, attackers infiltrate through the backdoor by exploiting the trust relationship between businesses and their suppliers.
For instance: your organization might have world-class security measures, firewalls, and monitoring systems in place. However, if your software vendor gets compromised and malicious code is inserted into a legitimate update you trust and install, those defenses become irrelevant. The attack comes from inside your digital walls, disguised as something safe.
Supply chain attacks are particularly insidious because they weaponize trust. Organizations inherently trust their vendors, software providers, and service partners. This trust creates blind spots that attackers eagerly exploit. When a legitimate software update contains malicious code, security systems designed to detect external threats often wave it through without question.
The supply chain encompasses every element that contributes to your organization's operations, software vendors, hardware manufacturers, cloud service providers, logistics companies, and even contractors with system access. Each represents a potential entry point for determined attackers. The complexity and interconnectedness of modern supply chains mean that a compromise at any point can cascade through multiple organizations, creating what security experts call a "waterfall effect."
How Does the Attack Work?
Understanding the mechanics of supply chain attacks reveals why they're so effective and challenging to prevent. The typical supply chain attack follows a multi-stage process that requires patience, planning, and technical sophistication.
Initial Compromise
The attack begins when cybercriminals identify a weak link in the supply chain, typically a vendor or service provider with access to multiple downstream customers. Attackers conduct extensive reconnaissance to find suppliers with less robust security measures than their ultimate targets. Smaller vendors, while trusted partners, often lack the security resources of larger enterprises, making them attractive entry points.
The initial compromise might occur through various methods: phishing campaigns targeting vendor employees, exploiting unpatched vulnerabilities in the vendor's systems, or even using insider threats. Once inside, attackers move laterally through the vendor's network, seeking access to software development environments, update servers, or communication channels with customers.
Injection Phase
After establishing control within the compromised vendor, attackers inject malicious code into legitimate products or services. This could involve:
- Software Updates: Inserting malware into software patches or updates that customers trust and automatically install
- Hardware Manipulation: Tampering with physical devices during manufacturing or shipping
- Code Libraries: Compromising open-source or proprietary code libraries that developers incorporate into applications
- Cloud Services: Injecting malicious code into cloud platforms or SaaS applications that multiple organizations use
The injected malware is often designed to remain dormant initially, avoiding immediate detection. Attackers craft their payloads carefully to bypass security scanning tools that might examine code before deployment.
Distribution and Activation
The compromised product or service is then distributed through normal, trusted channels. Organizations install updates, deploy hardware, or continue using services completely unaware that they've invited a threat actor into their environment. The malware activates according to the attacker's design, sometimes immediately, sometimes after a delay, and sometimes only when specific conditions are met.
Exploitation
Once activated across multiple victim organizations, attackers can pursue various objectives: stealing sensitive data, deploying ransomware, establishing persistent backdoors for future access, or using compromised systems as launching points for additional attacks. The simultaneous compromise of hundreds or thousands of organizations gives attackers unprecedented leverage and creates chaos that makes response more difficult.
Types of Supply Chain Attacks
Supply chain attacks come in various forms, each exploiting different aspects of business relationships and technology dependencies.
Software Supply Chain Attacks
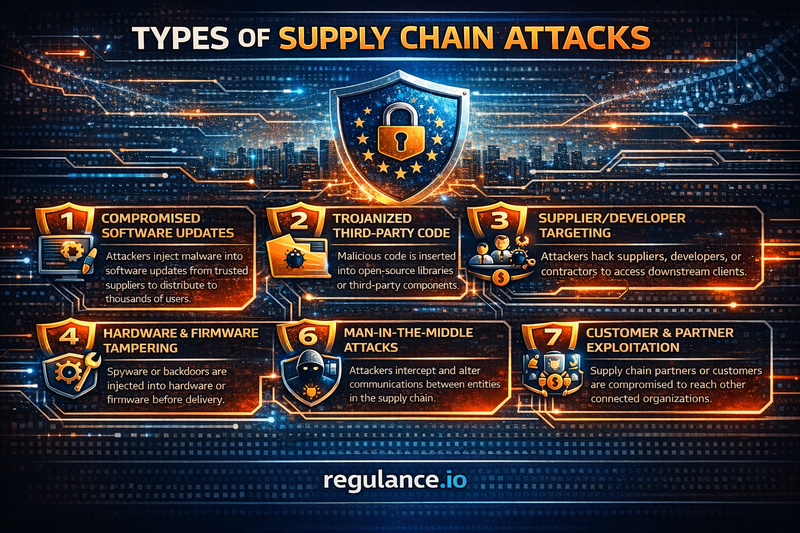
These attacks target the software development and distribution process. Attackers compromise source code repositories, build systems, or update mechanisms to inject malicious code into legitimate applications. The SolarWinds attack exemplified this approach when hackers inserted malware into the Orion platform's updates, affecting approximately 18,000 customers.
Software supply chain attacks also target open-source dependencies. Modern applications rely on numerous third-party libraries and components. Attackers sometimes create malicious packages with names similar to popular libraries, hoping developers will accidentally incorporate them—a technique called "typosquatting."
Hardware Supply Chain Attacks
Physical device compromise occurs during manufacturing, shipping, or installation. Attackers might install malicious chips or components in servers, networking equipment, or other devices before they reach customers. These hardware implants can provide persistent backdoor access that survives software reinstallation and is extremely difficult to detect.
Supplier and Service Provider Attacks
These attacks target managed service providers (MSPs), cloud hosting companies, or other service organizations that have administrative access to client systems. The Kaseya attack demonstrated this vector's power when ransomware deployed through compromised MSP management software affected over 1,500 businesses simultaneously.
Compromised Credentials
Sometimes attackers don't need to compromise code or hardware, they simply steal legitimate credentials belonging to vendors or contractors who have authorized access to target systems. Using valid credentials allows attackers to move through environments without triggering alerts designed to detect unauthorized access.
Pre-Installed Malware
Some supply chain attacks involve devices or applications that ship with malware already installed. This has occurred with mobile devices, IoT equipment, and even some consumer electronics, where manufacturers or third parties intentionally or accidentally include malicious components.
Trends for 2026
As we approach 2026, several emerging trends are reshaping the supply chain attack landscape, presenting new challenges for cybersecurity professionals.
AI-Powered Attack Sophistication
Artificial intelligence is becoming a double-edged sword in cybersecurity. While defenders use AI to improve threat detection, attackers are leveraging the same technology to create more sophisticated supply chain attacks. AI-powered reconnaissance tools help attackers identify vulnerable suppliers faster and with greater accuracy. Machine learning algorithms generate convincing phishing content that bypasses traditional detection, and automated systems manage complex, multi-stage attacks across numerous targets simultaneously.
Expect to see AI-driven attacks that adapt in real-time to defensive measures, making them significantly harder to detect and contain. The automation capabilities AI provides will likely reduce the time between initial compromise and widespread exploitation, leaving defenders with even narrower response windows.
Open-Source Software Vulnerabilities
The open-source ecosystem faces mounting pressure as supply chain attacks increasingly target widely-used libraries and dependencies. With most modern applications incorporating dozens or hundreds of open-source components, a single compromised package can cascade through countless projects. In 2026, we'll see attackers becoming more strategic about targeting foundational open-source projects with massive downstream dependency chains.
The challenge is compounded by the volunteer-maintained nature of many open-source projects. Without dedicated security teams or resources, these essential components of the digital infrastructure remain vulnerable. Organizations will need to implement more rigorous open-source dependency management and security scanning processes.
Cloud and SaaS Targeting
As businesses accelerate cloud migration, cloud service providers and SaaS platforms become increasingly attractive targets for supply chain attacks. A successful breach of a major cloud provider could compromise thousands of organizations simultaneously. Multi-tenant cloud environments create unique challenges, as attacks might spread between customers through shared infrastructure or services.
API integrations between SaaS applications create additional attack surfaces. The extensive interconnections between cloud services mean that compromising one platform could provide pathways to numerous others. Expect to see more sophisticated attacks targeting cloud supply chains, including container repositories, serverless functions, and infrastructure-as-code systems.
IoT and Critical Infrastructure
The proliferation of Internet of Things devices and their integration into critical infrastructure creates vast new supply chain attack surfaces. Smart city systems, industrial control systems, healthcare devices, and connected vehicles all depend on complex supply chains vulnerable to compromise. In 2026, we anticipate seeing more attacks targeting IoT device manufacturers and firmware update mechanisms.
The consequences of IoT supply chain attacks extend beyond data breaches. Compromised industrial control systems could cause physical damage, safety hazards, or service disruptions affecting thousands of people. The operational technology (OT) and IT convergence creates bridges between previously isolated systems, multiplying potential impact.
Geopolitical Cyber Operations
Nation-state actors continue refining supply chain attack techniques as part of broader geopolitical strategies. Rather than direct cyberwarfare, countries are conducting sophisticated supply chain operations to establish persistent access within adversary nations' critical infrastructure, private sector organizations, and government agencies.
These state-sponsored supply chain attacks often have long-term strategic objectives rather than immediate financial goals. Dormant implants might remain inactive for years until activated during geopolitical tensions. The increasing geopolitical instability globally suggests we'll see more of these strategic supply chain compromises in 2026.
Regulatory Compliance as a Target
Interestingly, compliance requirements themselves are becoming attack vectors. Attackers are compromising organizations that provide compliance services, auditing tools, or security certifications. By infiltrating these trusted entities, they can insert backdoors while targets believe they're improving security through compliance efforts.
This trend exploits organizations' trust in audit processes and certified solutions, turning security assurance into a vulnerability. Expect regulatory bodies to respond with stricter oversight of the compliance ecosystem itself.
How to Prevent Supply Chain Attacks
While completely eliminating supply chain risk is impossible, organizations can significantly reduce their exposure through comprehensive security strategies.
Vendor Risk Management
Implementing rigorous vendor assessment processes forms the foundation of supply chain security. Before onboarding any vendor, conduct thorough security evaluations examining their cybersecurity practices, incident response capabilities, and compliance certifications. Don't simply accept vendors' security claims, verify them through third-party audits or penetration testing reports.
Establish ongoing monitoring programs rather than one-time assessments. Vendors' security postures change over time, and continuous evaluation helps identify emerging risks. Include contractual security requirements in vendor agreements, specifying security standards, breach notification timeframes, and liability provisions.
Create tiered risk classifications for vendors based on their access levels and data sensitivity. Apply more stringent security requirements to high-risk vendors with access to critical systems or sensitive information. For the highest-risk relationships, consider requiring vendors to implement specific security controls or submit to regular security audits.
Software Composition Analysis
Modern applications contain extensive third-party code through libraries, frameworks, and dependencies. Software composition analysis (SCA) tools inventory these components, identifying known vulnerabilities and tracking versions. Implement SCA throughout your development lifecycle, not just during initial development but continuously as new vulnerabilities are discovered.
Establish processes for rapidly updating vulnerable dependencies when patches become available. Create software bills of materials (SBOMs) for all applications, providing complete transparency into what code you're running. These inventories become invaluable during supply chain incidents, allowing quick identification of affected systems.
Monitor for suspicious dependency changes or unexpected updates in open-source packages your organization uses. Establish trusted repositories and implement verification mechanisms ensuring downloaded packages match their legitimate versions.
Zero Trust Architecture
Traditional perimeter-based security assumes anything inside the network is trusted—an assumption supply chain attacks exploit. Zero trust architecture eliminates this assumption, requiring continuous verification of every user, device, and application attempting to access resources, regardless of their location or source.
Implement micro-segmentation dividing networks into small, isolated segments with specific access controls. This limits lateral movement if attackers compromise systems through supply chain vectors. Apply least-privilege access principles, granting users and systems only the minimum permissions necessary for their functions.
Use multi-factor authentication universally, eliminating reliance on passwords alone. Deploy endpoint detection and response (EDR) solutions providing visibility into system behaviors and detecting anomalous activities that might indicate compromise.
Code Signing and Verification
Digital code signing provides cryptographic assurance that software hasn't been tampered with since the developer signed it. Implement policies requiring verification of digital signatures before installing any software updates or patches. This helps detect malicious code injected into legitimate updates.
Organizations distributing their own software should implement robust code signing processes protecting private signing keys with hardware security modules (HSMs) or other secure key management systems. Compromised signing keys can enable attackers to distribute malware that appears legitimate to customers.
Incident Response Planning
Develop specific incident response procedures addressing supply chain compromises. These scenarios differ from typical breaches because they might affect numerous organizations simultaneously, creating resource constraints for vendors, security firms, and investigators.
Your incident response plan should include procedures for rapidly identifying all systems using a compromised vendor's products or services. Establish communication protocols for coordinating with vendors during incidents and make decisions about isolating affected systems, which might disrupt operations but prevent further damage.
Conduct tabletop exercises simulating supply chain attack scenarios. These exercises reveal gaps in your response capabilities and improve coordination between technical teams, leadership, and external partners. Include vendors in these exercises when appropriate, testing communication channels and joint response procedures.
Network Monitoring and Anomaly Detection
Deploy comprehensive monitoring solutions providing visibility into network traffic, system behaviors, and user activities. Advanced threat detection platforms using behavioral analytics can identify anomalous patterns that might indicate supply chain compromise, even when attackers use legitimate credentials or tools.
Establish baselines for normal operations, making deviations more apparent. Monitor for unusual outbound connections, unexpected data transfers, or atypical system behaviors. Since supply chain attacks often introduce subtle changes, sophisticated monitoring becomes essential for early detection.
Supply Chain Mapping
Create comprehensive maps of your supply chain, documenting all vendors, their access levels, data flows, and dependencies between systems and suppliers. This visibility enables better risk assessment and faster response during incidents. Many organizations lack complete awareness of their supply chain relationships, creating blind spots attackers exploit.
Include fourth-party vendors in your mapping the suppliers of your suppliers. These indirect relationships can create unexpected vulnerabilities. Understanding your extended supply chain ecosystem helps identify concentration risks where multiple critical services depend on single vendors.
FAQs
What's the difference between a supply chain attack and a regular cyberattack?
Traditional cyberattacks directly target an organization's defenses attempting to breach firewalls, exploit vulnerabilities, or phish employees. Supply chain attacks are indirect, compromising trusted third-party vendors or suppliers to gain access to the ultimate target. Instead of attacking strong defenses head-on, attackers exploit trust relationships, making supply chain attacks harder to detect and potentially affecting thousands of organizations through a single compromised vendor.
How can small businesses protect themselves from supply chain attacks?
Small businesses should focus on fundamentals: thoroughly vet vendors before granting system access, implement multi-factor authentication, maintain updated software inventories, and establish basic monitoring for unusual activities. While resource constraints are real, free and low-cost security tools can provide significant protection. Consider cyber insurance covering supply chain incidents and establish incident response procedures appropriate to your organization's size. Joining information sharing groups provides threat intelligence without major investment.
Are supply chain attacks becoming more common?
Yes, supply chain attacks are increasing in both frequency and sophistication. Attackers recognize that compromising one vendor can provide access to hundreds or thousands of downstream targets simultaneously. As organizations improve their direct cybersecurity defenses, attackers naturally shift toward supply chain vectors offering better return on investment. The interconnected nature of modern business, cloud services adoption, and extensive software dependencies create expanding attack surfaces that cybercriminals actively exploit.
What should I do if my vendor experiences a supply chain attack?
Act quickly but thoughtfully. First, isolate systems using the compromised vendor's products or services to prevent lateral movement. Contact the vendor for specific guidance about their incident and recommended actions. Assess what data the vendor accessed and whether that information was compromised. Review logs for suspicious activities occurring through vendor access points. Notify stakeholders, customers, or regulators as required by legal obligations. Document everything for potential investigations. Finally, reevaluate your relationship with the vendor, considering whether their security practices meet your requirements.
Can supply chain attacks be completely prevented?
Complete prevention is impossible given the interconnected nature of modern business and technology. However, organizations can significantly reduce their risk through comprehensive vendor management, continuous monitoring, zero trust architectures, and incident response planning. The goal is reducing your attack surface, detecting compromises early, and minimizing impact when incidents occur. A layered security approach acknowledging that supply chain compromise is a matter of when, not if, positions organizations to respond effectively and recover quickly.
How long do supply chain attacks typically remain undetected?
Detection timeframes vary enormously from days to years. Some high-profile attacks remained undetected for months or even years because malicious code was carefully designed to blend with legitimate activities. The average dwell time for supply chain compromises tends to exceed traditional breaches because attacks come through trusted channels that receive less security scrutiny. This emphasizes the importance of continuous monitoring, behavioral analytics, and regular security assessments that might reveal long-standing compromises.
Conclusion
Supply chain attacks represent one of the most significant cybersecurity challenges facing organizations today and will continue dominating the threat landscape as we move through 2026. Their sophistication, scale, and exploitation of trust relationships make them particularly dangerous and difficult to defend against. The interconnected nature of modern business with extensive vendor relationships, cloud dependencies, open-source software, and global supply chains creates vast attack surfaces that determined adversaries actively exploit.
However, understanding these threats and implementing comprehensive security strategies can significantly reduce your organization's risk. Rigorous vendor risk management, software composition analysis, zero trust architectures, continuous monitoring, and incident response planning create defense-in-depth approaches that make successful attacks far more difficult. While perfect security remains elusive, organizations taking supply chain security seriously position themselves to detect compromises earlier, respond more effectively, and recover faster when incidents occur.
The trends emerging for 2026 AI-powered attacks, open-source targeting, cloud exploitation, IoT vulnerabilities, and geopolitical operations underscore the evolving nature of these threats. Staying informed about emerging attack techniques, adapting security strategies accordingly, and fostering security awareness throughout your organization and supply chain partners becomes essential for resilience in this challenging environment.
Remember that supply chain security is about relationships, processes, and culture. Building security partnerships with vendors, fostering open communication about threats and incidents, and creating organizational cultures that prioritize security awareness all contribute to stronger supply chain defenses.
Take action today. Contact Regulance to schedule a comprehensive supply chain security assessment and discover how we can help you build resilient defenses against tomorrow's threats. Your supply chain's security is only as strong as its weakest link; let Regulance help you strengthen every connection.