SOC 2 or Security Questionnaires? Understanding the Key Differences and the Smarter Choice in 2026

Introduction
When your sales team tells you they've lost another enterprise deal because you don't have the right security documentation, the frustration is real. You know your systems are secure. You've invested in firewalls, encryption, and access controls. But proving it to potential clients? That's where things get complicated.
This is where the two terms that dominate vendor security conversations come in: SOC 2 and security questionnaires. If you're building a technology company in 2026, you'll encounter both repeatedly. Enterprise buyers want assurance that their data is safe in your hands, and these are the primary mechanisms they use to evaluate your security posture. Yet many organizations struggle to understand what each one actually means and which investment deserves priority.
Both involve detailed scrutiny of your security practices, both require substantial time and documentation, and both can determine whether a prospect becomes a customer. The difference isn't immediately obvious, especially when you're fielding your first enterprise security inquiry.
The reality is that SOC 2 and security questionnaires serve fundamentally different purposes in the trust ecosystem. One is an independent audit that provides formal verification of your controls. The other is a self-reported assessment tool that facilitates vendor evaluation. Understanding these distinctions matters because choosing the wrong path wastes resources, while choosing the right one accelerates growth.
This guide cuts through the complexity. We'll explain exactly what SOC 2 and security questionnaires are, how they differ in practice, and most importantly, which one your organization actually needs right now. Whether you're a startup facing your first security assessment or an established company optimizing your compliance strategy, you'll leave with a clear roadmap for building customer trust efficiently.
What is SOC 2?
SOC 2, which stands for System and Organization Controls 2, is a standardized auditing framework developed by the American Institute of Certified Public Accountants (AICPA). It's designed specifically for service organizations that store, process, or transmit customer data in the cloud. Unlike its predecessor SOC 1, which focuses on financial reporting controls, SOC 2 zeroes in on the security, availability, processing integrity, confidentiality, and privacy of customer information.
At its core, a SOC 2 audit is an independent, third-party examination of your organization's internal controls. A licensed CPA firm evaluates whether your systems and processes meet the rigorous criteria outlined in the AICPA's Trust Services Criteria. The result is a formal report that serves as an authoritative stamp of approval, demonstrating to clients, partners, and stakeholders that your organization takes data security seriously and has implemented effective controls.
SOC 2 comes in two flavors: Type I and Type II. A Type I report evaluates whether your controls are appropriately designed at a specific point in time, essentially a snapshot of your security posture. Type II goes further, assessing not just the design but the operating effectiveness of those controls over a period of time, typically six to twelve months. Most enterprise clients and sophisticated buyers prefer Type II reports because they demonstrate sustained commitment rather than a one-time effort.
The framework is built around five Trust Services Criteria, though not all organizations need to address every criterion. Security is mandatory for all SOC 2 audits, as it forms the foundation of the other criteria. The additional criteria; availability, processing integrity, confidentiality, and privacy are optional and should be selected based on what's relevant to your service offerings and client expectations.
What makes SOC 2 particularly powerful is its flexibility within a standardized framework. Unlike rigid compliance certifications with prescriptive requirements, SOC 2 allows organizations to design controls that fit their unique business models and risk profiles. However, this flexibility comes with responsibility. You must justify your control choices and demonstrate their effectiveness to a skeptical auditor who will examine everything from your incident response procedures to your vendor management practices.
The SOC 2 process typically spans several months and involves comprehensive documentation, evidence collection, and sometimes remediation of control gaps. Organizations often work with compliance consultants or platforms to prepare for the audit, implementing policies, procedures, and technical controls that align with the Trust Services Criteria. The investment is significant, both in terms of time and money, with costs ranging from tens of thousands to over a hundred thousand dollars depending on organizational complexity and scope.
What is a Security Questionnaire?
A security questionnaire is a document containing a series of questions designed to assess an organization's security practices, policies, and technical controls. Unlike the standardized SOC 2 framework, security questionnaires vary widely in format, length, and depth. They're typically created and distributed by potential clients, partners, or customers during the vendor evaluation process as part of their third-party risk management program.
These questionnaires serve as a preliminary screening tool, allowing organizations to evaluate whether a potential vendor meets their minimum security requirements before entering into a business relationship. Think of them as a security interview; a way for buyers to understand your security posture without commissioning a full audit or conducting an on-site assessment.
Security questionnaires can range from relatively simple documents with 50 basic questions about encryption and access controls to comprehensive assessments with 300 or more detailed inquiries covering everything from physical security to business continuity planning. Some organizations create their own custom questionnaires, while others use standardized frameworks like the SIG (Standardized Information Gathering) questionnaire, the CAIQ (Consensus Assessments Initiative Questionnaire), or industry-specific templates.
Common topics covered in security questionnaires include data encryption practices, access control mechanisms, employee security training programs, incident response procedures, disaster recovery plans, compliance certifications, vulnerability management processes, and third-party vendor oversight. Many questionnaires also ask about specific technical implementations, such as whether you use multi-factor authentication, how frequently you patch systems, or what logging and monitoring capabilities you maintain.
The process of completing security questionnaires is often manual and time-consuming. For each new potential client, your team must review the questions, gather information from various departments, provide detailed responses, and often attach supporting evidence like policies, certifications, or architecture diagrams. Organizations dealing with multiple enterprise sales opportunities might find themselves completing dozens of these questionnaires annually, each slightly different from the last.
What makes security questionnaires particularly challenging is their lack of standardization. Even when using frameworks like SIG, organizations often customize questions to reflect their specific concerns, industry requirements, or risk tolerance. This means you can't simply copy and paste responses from one questionnaire to another. Each requires careful attention to ensure accuracy and relevance.
However, security questionnaires also offer advantages. They're typically faster and less expensive than formal audits, they allow for direct dialogue between buyer and vendor about specific concerns, and they can be completed at any stage of organizational maturity. You don't need to wait months or invest heavily in preparation, you can start answering security questionnaires from day one, even if your answers reveal opportunities for improvement.
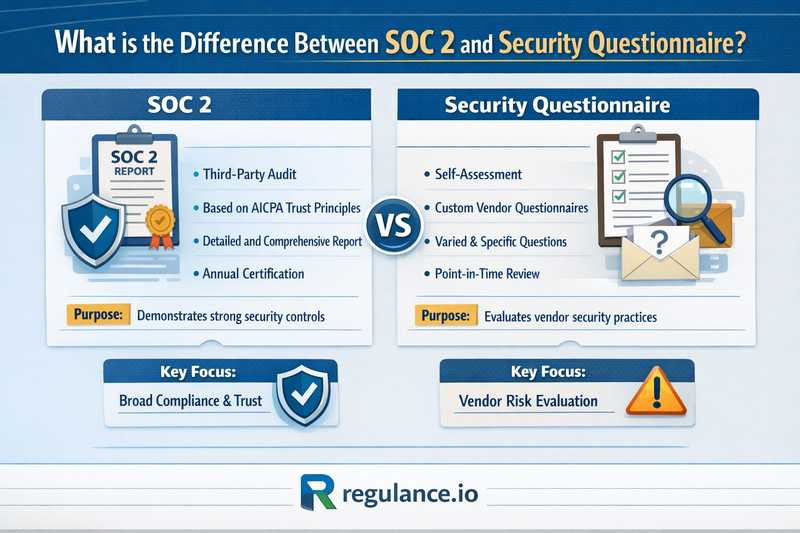
What is the Difference?
The fundamental differences between SOC 2 and security questionnaires extend far beyond their surface-level distinctions. Understanding these differences is crucial for making strategic decisions about where to invest your compliance resources.
Authority and Credibility
SOC 2 reports carry significantly more weight because they're produced by independent, licensed CPA firms following a recognized auditing standard. The auditor's opinion is backed by rigorous examination and professional liability, making the report a trusted document in the business world. Security questionnaires, by contrast, are self-reported. While organizations typically strive for honesty, there's no independent verification of the responses, which inherently makes them less authoritative. A SOC 2 report says "a qualified professional verified this," while a questionnaire says "we're telling you this is how we operate."
Standardization vs. Customization
SOC 2 follows the AICPA's Trust Services Criteria, providing a consistent framework recognized across industries. Any organization with a SOC 2 Type II report has been evaluated against the same fundamental criteria, making it easier for clients to compare vendors and understand what the report represents. Security questionnaires lack this standardization. Even when based on frameworks like SIG, they're frequently customized, meaning responses that satisfy one client might not address another's concerns. This variability makes questionnaires more flexible but less universally applicable.
Scope and Depth
A SOC 2 audit examines your entire security program comprehensively, from governance and risk management to technical controls and operational procedures. Auditors don't just ask questions; they examine evidence, test controls, observe processes, and interview personnel. They're looking for gaps between policy and practice, and they'll note any exceptions or findings in their report. Security questionnaires typically only go as deep as the questions asked. If a questionnaire doesn't inquire about backup testing, for instance, you won't have an opportunity to demonstrate your robust backup procedures. The depth is limited by the questioner's knowledge and priorities.
Time and Resource Investment
Obtaining a SOC 2 report is a substantial undertaking that typically requires three to twelve months of preparation, followed by the audit period itself. Organizations often hire consultants, invest in new security tools, implement formal policies and procedures, and dedicate significant internal resources to readiness activities. The costs can easily reach $50,000 to $150,000 or more for the first audit. Security questionnaires, while time-consuming in aggregate, require far less upfront investment. You can complete a questionnaire in days or weeks rather than months, and the direct costs are primarily internal staff time rather than external fees.
Longevity and Reusability
A SOC 2 Type II report is typically valid for one year and can be shared with unlimited prospects and customers during that period. Once you have the report, you can use it repeatedly to satisfy security requirements for numerous potential clients, effectively amortizing the investment across many sales opportunities. Security questionnaires must be completed individually for each requesting organization. While you can leverage previous responses and build a response library over time, each questionnaire still requires customization and individual attention.
Audience and Purpose
SOC 2 reports are primarily designed for enterprise and mid-market clients who have sophisticated procurement and risk management processes. They're often required by organizations subject to regulatory requirements or those handling particularly sensitive data. Security questionnaires serve a broader audience and are used at various stages of vendor evaluation, from initial screening to ongoing monitoring. Smaller organizations without the budget or need for SOC 2 reports often rely exclusively on questionnaires for vendor assessment.
Level of Assurance
Perhaps the most significant difference lies in the assurance level provided. A SOC 2 Type II report includes an auditor's opinion on whether controls were operating effectively over a specified period. This opinion is based on testing and evidence examination, providing reasonable assurance about your security posture. Security questionnaires provide no formal assurance whatsoever. They're information-sharing tools, not verification instruments. Clients must take your responses at face value or conduct additional due diligence to verify claims.
Which One Does Your Organization Need in 2026?
Deciding between pursuing SOC 2 certification and simply responding to security questionnaires isn't always an either-or proposition, but understanding when each makes sense will help you prioritize your compliance investments strategically.
When Security Questionnaires Are Sufficient
If you're an early-stage startup still finding product-market fit, security questionnaires are likely your best starting point. You're probably facing occasional security inquiries from potential customers, but not yet seeing deals stall or close because of compliance requirements. At this stage, investing $100,000 in a SOC 2 audit might not yield sufficient return compared to spending those resources on product development or customer acquisition.
Similarly, if your target market consists primarily of small and mid-sized businesses without stringent compliance requirements, questionnaires may suffice indefinitely. Many SMB buyers want assurance that you're taking security seriously, but they're not mandating formal audits. A well-maintained security questionnaire response library, perhaps built around a framework like SIG, can effectively address these concerns while keeping costs manageable.
Organizations in certain industries or business models may also find questionnaires adequate. If you're not storing, processing, or transmitting sensitive customer data, perhaps you're selling on-premise software that customers host themselves, or providing services that don't involve data custody, the business case for SOC 2 weakens considerably.
When SOC 2 Becomes Essential
The calculus changes dramatically when you start losing deals because of compliance requirements. If sales conversations repeatedly end with "We'd love to work with you, but our procurement team requires SOC 2," you've reached an inflection point. SOC 2 has become a cost of doing business rather than a nice-to-have differentiator. This typically happens when targeting enterprise customers in regulated industries like healthcare, financial services, or government sectors.
Similarly, if you're handling sensitive data categories: personal health information, financial data, personally identifiable information at scale, stakeholders increasingly expect SOC 2 as a baseline security demonstration. The reputational risk of a breach combined with the complexity of protecting this data makes independent verification valuable not just for customers but for your own risk management.
Growth-stage companies raising Series B or later funding often pursue SOC 2 even before customers demand it. Investors view SOC 2 as a signal of operational maturity and risk management sophistication. It demonstrates that your organization has graduated from ad hoc security practices to systematized, auditable controls. This can be particularly important if you're in a competitive fundraising environment or if previous security incidents in your industry have made investors cautious.
The Hybrid Approach for 2026
Most successful organizations eventually adopt a hybrid strategy. They pursue SOC 2 to satisfy their most demanding customers and provide a strong security foundation, while continuing to complete security questionnaires for prospects who haven't yet requested SOC 2 or who have additional specific questions beyond what the audit covers.
This approach recognizes that SOC 2 significantly reduces but doesn't eliminate questionnaire volume. Even customers who accept your SOC 2 report often have supplementary questions about topics outside the audit scope, recent changes to your environment, or specific technical implementations they care about. Having both a SOC 2 report and a well-maintained questionnaire response library provides comprehensive coverage.
In 2026, we're also seeing growing sophistication in how organizations approach this hybrid model. Rather than treating SOC 2 and questionnaire management as separate activities, forward-thinking companies are using their SOC 2 preparation as the foundation for questionnaire responses. The policies, procedures, and evidence you compile for SOC 2 become your source material for questionnaire answers, creating efficiency rather than duplication.
Making the Decision
Consider pursuing SOC 2 in 2026 if you can answer "yes" to two or more of these questions: Are enterprise customers explicitly requesting SOC 2? Have you lost deals due to lack of SOC 2? Are you handling regulated or highly sensitive data? Are you raising institutional capital? Have you scaled beyond 50 employees? Is your annual revenue approaching or exceeding $10 million?
Stick with questionnaires for now if you're answering "no" to most of those questions but can answer "yes" to these: Are your current customers satisfied with questionnaire responses? Is your data exposure relatively limited? Are you pre-revenue or pre-product-market-fit? Is your buyer persona primarily SMB or mid-market?
Remember that this isn't a permanent decision. Many organizations successfully operate for years on questionnaires alone before market dynamics shift and SOC 2 becomes necessary. The key is remaining attentive to market signals and being prepared to pivot when the return on investment justifies the expense.
FAQs
How long does a SOC 2 audit take?
The SOC 2 process typically spans six to twelve months from start to finish. This includes three to six months of preparation and readiness activities, followed by a three to twelve-month observation period for Type II reports. However, organizations with mature security programs might complete Type I audits more quickly, while those starting from scratch may need additional time for remediation and control implementation.
Can I share security questionnaire responses with multiple clients?
While you can certainly reuse content and maintain a response library, most security questionnaires are client-specific and should be customized for each requester. Different organizations ask different questions, use different terminology, and have different concerns. Simply forwarding another client's completed questionnaire is generally not appropriate and may not address the specific requirements of your current prospect.
Is SOC 2 required by law?
No, SOC 2 is not a legal requirement. It's a voluntary framework that has become a de facto industry standard for service organizations, particularly in the technology sector. However, certain regulations like HIPAA or PCI DSS may have requirements that align with SOC 2 controls, and some industries have adopted SOC 2 as a preferred method for demonstrating compliance with broader security obligations.
How much does a SOC 2 audit cost?
SOC 2 audit costs vary widely based on organizational size, complexity, scope, and current security maturity. Small organizations with straightforward systems might pay $30,000 to $50,000 for their first Type II audit, while larger or more complex organizations can easily exceed $100,000. These figures typically don't include preparation costs, consulting fees, or the cost of implementing new security tools and controls.
Can I complete security questionnaires without formal security policies?
Yes, you can complete questionnaires without formal documentation, though your responses may be less convincing. Many questionnaires ask whether you have written policies and procedures, and answering "no" can raise red flags with security-conscious prospects. That said, having informal but effective security practices is better than having comprehensive documentation with no implementation. Focus on building real security capabilities first, then document them as resources allow.
What happens if I fail a SOC 2 audit?
SOC 2 audits don't exactly result in "pass" or "fail" outcomes. Instead, auditors issue opinions ranging from unqualified (clean) to qualified (with exceptions) or adverse (significant issues). If material weaknesses are identified, they'll be noted in the report, and you'll need to decide whether to share that report with clients, remediate the issues and re-audit, or wait until the next audit cycle to address findings. Most organizations work closely with auditors during the process to remediate issues before the final report is issued.
How often do I need to update my SOC 2 report?
SOC 2 Type II reports are typically conducted annually, with each report covering a six to twelve-month observation period. Many organizations time their audits so they always have a current report available, sometimes with slightly overlapping periods to avoid gaps. As your report approaches expiration, you'll need to begin the next audit cycle to maintain continuous coverage.
Are there alternatives to SOC 2?
Yes, several alternatives exist depending on your industry and client base. ISO 27001 is an international information security standard that's particularly popular in Europe and with global organizations. HITRUST is common in healthcare. PCI DSS is required for organizations handling payment card data. However, in the US technology sector, SOC 2 has become the dominant framework, and alternatives may not satisfy customer requirements even if they're technically equivalent or more rigorous.
Conclusion
The choice between SOC 2 and security questionnaires entails understanding what each tool accomplishes and deploying them strategically as your organization matures. Security questionnaires offer an accessible, flexible way to communicate your security posture at any stage of growth, while SOC 2 provides the independent verification and standardized framework that enterprise clients increasingly demand.
For organizations just beginning their compliance journey, questionnaires provide an essential bridge, allowing you to compete for business while building the security foundation that will eventually support a formal audit. As you scale and target more sophisticated buyers, SOC 2 transitions from optional to essential, becoming the price of admission for enterprise deals and a powerful trust signal that can accelerate sales cycles.
The most successful organizations recognize that these tools serve complementary purposes. Your SOC 2 report becomes the cornerstone of your security assurance program, while questionnaires fill in the gaps, address specific client concerns, and maintain engagement with prospects who haven't yet requested formal audits. Together, they create a comprehensive approach to demonstrating security competence in an increasingly risk-conscious marketplace.
As we move through 2026, the bar for security assurance continues rising. Data breaches make headlines regularly, regulations proliferate, and buyers grow more sophisticated in their vendor assessment processes. Whether you're answering your first security questionnaire or preparing for your fifth SOC 2 audit, the investment you make in robust security practices and transparent communication pays dividends far beyond compliance checkboxes. It builds the trust that transforms prospects into customers and customers into long-term partners.
Ready to streamline your compliance journey? Regulance helps organizations navigate the complexities of SOC 2 preparation and security questionnaire management with expert guidance and automated workflows. Visit Regulance today to discover how we can transform your compliance from a burden into a competitive advantage.