SOC 2 Controls Explained: How to Build Compliance the Smart Way


Introduction
Every minute, cybercriminals launch over 2,200 attacks on businesses worldwide making robust data security not just important, but absolutely critical for survival. In this high-stakes digital environment, organizations handling sensitive customer information face mounting pressure to prove their security credentials through established compliance frameworks. This is where SOC 2 (Service Organization Control 2) becomes your strongest defense and competitive advantage.
SOC2 compliance has evolved from a nice-to-have credential into an essential business requirement, particularly for cloud-based service providers and technology companies. Major enterprises now demand SOC 2 reports before signing contracts, making this framework a gateway to lucrative business opportunities and sustainable growth.
But here's what most organizations get wrong: they approach SOC 2 control implementation as a checkbox exercise rather than a strategic security investment. Understanding and implementing a comprehensive SOC 2 control list is about building an unshakeable security foundation that protects your organization, reduces operational risks, and transforms compliance into a powerful sales tool.
Whether you're a startup preparing for your first SOC 2 audit to unlock enterprise deals or an established company looking to strengthen your compliance posture and outpace competitors, this comprehensive guide will walk you through everything you need to know about SOC 2 control lists and their strategic implementation. Ready to turn SOC 2 compliance from a burden into your biggest business accelerator?
What is SOC2 Control List?
A SOC 2 control list represents a comprehensive framework of security measures and operational procedures designed to ensure that service organizations adequately protect customer data and maintain system reliability. Developed by the American Institute of Certified Public Accountants (AICPA), the SOC 2 framework is built around five fundamental trust service criteria that form the backbone of any effective control environment.
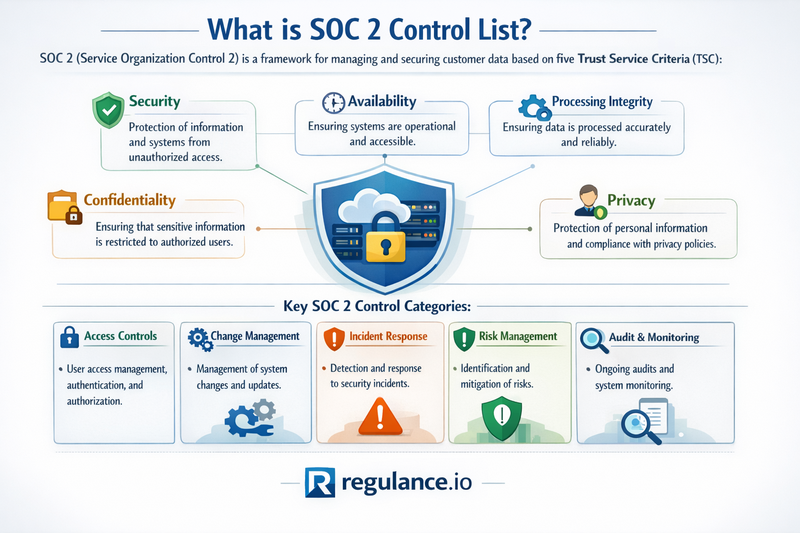
The Five Trust Service Criteria
Security forms the foundation of SOC 2 compliance, encompassing logical and physical access controls, system configurations, and data protection measures. This criterion ensures that your systems are protected against unauthorized access, both from external threats and internal vulnerabilities.
Availability focuses on system uptime and operational accessibility, ensuring that your services remain available for operation and use as committed or agreed upon. This includes disaster recovery planning, system monitoring, and incident response procedures.
Processing Integrity addresses the completeness, validity, accuracy, timeliness, and authorization of system processing. It ensures that your systems function as intended and that data processing occurs without unauthorized or unintended alterations.
Confidentiality goes beyond basic security measures to ensure that information designated as confidential remains protected according to your organization's commitments and system requirements. This criterion is particularly relevant for organizations handling sensitive personal or proprietary information.
Privacy represents the most comprehensive criterion, addressing the collection, use, retention, disclosure, and disposal of personal information in accordance with your organization's privacy notice and privacy principles.
Understanding Control Categories
SOC 2 controls are typically organized into three main categories that reflect different aspects of your security and operational framework. Entity-level controls establish the tone at the top and provide the foundation for all other security measures. These include governance structures, risk assessment processes, and organizational policies that guide decision-making across your entire operation.
Process-level controls focus on specific operational procedures and workflows, ensuring that day-to-day activities align with your security objectives. These controls address everything from user access management to data backup procedures and change management processes.
System-level controls deal with the technical safeguards implemented within your IT infrastructure, including network security configurations, database access controls, and application-level security measures.
How to Implement SOC2 Control List
Implementing a SOC 2 control list requires a systematic approach that combines strategic planning, tactical execution, and ongoing monitoring. The process begins long before your first audit and continues as an integral part of your operational framework.
Phase 1: Assessment and Gap Analysis
The implementation journey starts with a thorough assessment of your current security posture and operational procedures. This initial evaluation helps identify gaps between your existing practices and SOC 2 requirements, providing a clear roadmap for implementation efforts.
Begin by documenting your current processes, policies, and technical controls across all areas that will be covered in your SOC 2 scope. This includes everything from employee onboarding procedures to network architecture diagrams. Pay particular attention to how sensitive data flows through your systems and who has access to what information.
Conduct a comprehensive risk assessment to identify potential vulnerabilities and threats to your systems and data. This assessment should consider both technical risks, such as software vulnerabilities or network misconfigurations, and operational risks, such as inadequate employee training or insufficient incident response procedures.
Phase 2: Control Design and Documentation
Once you've identified the gaps in your current control environment, the next step is designing and documenting the controls needed to address these deficiencies. This phase requires careful attention to both the technical and procedural aspects of each control.
Develop comprehensive policies and procedures that clearly define roles, responsibilities, and processes for each area covered by your SOC 2 scope. These documents should be detailed enough to guide day-to-day operations while remaining flexible enough to accommodate business growth and changes in the threat landscape.
Create detailed system documentation that includes network diagrams, data flow charts, and technical specifications for all systems within your SOC 2 scope. This documentation serves not only as a reference for your internal team but also as evidence for auditors that you understand and can control your technical environment.
Establish clear ownership and accountability for each control, ensuring that specific individuals are responsible for implementation, monitoring, and maintenance. This includes defining escalation procedures for when controls fail or when potential security incidents are identified.
Phase 3: Implementation and Testing
With your controls designed and documented, the implementation phase involves putting these measures into practice across your organization. This phase typically requires coordination across multiple departments and may involve significant changes to existing processes and systems.
Start with the most critical controls first, focusing on areas that pose the highest risk to your organization or your customers' data. Implement controls in phases to avoid overwhelming your team and to allow for proper testing and refinement of each measure.
Conduct regular testing of your implemented controls to ensure they're functioning as designed. This testing should include both automated monitoring where possible and manual verification procedures. Document the results of your testing activities, as this evidence will be crucial during your SOC 2 audit.
Phase 4: Monitoring and Continuous Improvement
SOC 2 compliance requires ongoing monitoring and continuous improvement of your control environment. Establish regular review cycles to assess the effectiveness of your controls and identify areas for enhancement.
Implement automated monitoring tools where possible to provide real-time visibility into the operation of your controls. These tools can help you identify potential issues before they become significant problems and provide the documentation needed to demonstrate control effectiveness to auditors.
Establish a formal change management process that ensures any modifications to your systems or processes are properly evaluated for their impact on your SOC 2 controls. This process should include approval workflows, testing procedures, and documentation requirements.
SOC2 Control List
A comprehensive SOC 2 control list encompasses hundreds of specific control activities organized around the five trust service criteria. While the exact controls implemented will vary based on your organization's specific circumstances, certain core controls are fundamental to most SOC 2 implementations.
Governance and Risk Management Controls
Effective SOC 2 compliance begins with strong governance structures that establish clear accountability for security and privacy matters. Board and management oversight controls ensure that senior leadership takes an active role in overseeing the organization's risk management and compliance efforts.
Risk assessment controls require organizations to conduct regular evaluations of potential threats and vulnerabilities, considering both internal and external factors that could impact system security and availability. These assessments should be documented, regularly updated, and used to guide decision-making about control investments and priorities.
Policy and procedure controls establish the framework for consistent security and operational practices across the organization. These controls require that policies be regularly reviewed, updated, and communicated to relevant personnel, with clear consequences for non-compliance.
Access Controls and Identity Management
Access control represents one of the most critical areas of SOC 2 compliance, governing who can access what information and systems under what circumstances. User access provisioning controls ensure that new users receive appropriate access based on their job responsibilities and that this access is properly authorized before being granted.
Periodic access reviews require organizations to regularly evaluate user access rights to ensure they remain appropriate and necessary. These reviews should consider changes in job responsibilities, organizational structure, and system requirements.
Privileged access management controls address the additional risks associated with administrative and other high-privilege accounts. These controls typically include enhanced authentication requirements, additional monitoring, and regular reviews of privileged access activities.
System Operations and Monitoring
Operational controls ensure that systems function reliably and that potential issues are identified and addressed promptly. System monitoring controls require organizations to implement comprehensive monitoring of system performance, availability, and security events.
Incident response controls establish procedures for identifying, investigating, and responding to security incidents and system outages. These procedures should include clear escalation paths, communication protocols, and documentation requirements.
Change management controls govern how modifications to systems and processes are evaluated, approved, tested, and implemented. These controls help ensure that changes don't inadvertently introduce security vulnerabilities or operational issues.
Data Protection and Privacy Controls
Data protection controls address how sensitive information is collected, processed, stored, and disposed of throughout its lifecycle. Data classification controls require organizations to identify and categorize sensitive data based on its confidentiality requirements and regulatory obligations.
Encryption controls mandate the use of appropriate cryptographic measures to protect sensitive data both in transit and at rest. These controls should specify encryption standards, key management procedures, and regular reviews of cryptographic implementations.
Data retention and disposal controls establish procedures for maintaining data only as long as necessary and for securely disposing of data when it's no longer needed. These procedures should consider both regulatory requirements and business needs.
Vendor Management and Third-Party Risk
Many organizations rely on third-party vendors and service providers, creating additional risks that must be managed through appropriate controls. Vendor risk assessment controls require organizations to evaluate the security and compliance posture of their vendors before engaging their services.
Ongoing vendor monitoring controls establish procedures for regularly reviewing vendor performance and compliance with contractual security requirements. This monitoring should include regular security assessments, performance reviews, and communication of any security incidents or changes.
SOC2 Controls for Security
Security controls form the foundation of any SOC 2 implementation and are required regardless of which other trust service criteria an organization chooses to include in their audit scope. These controls address a wide range of security concerns, from basic access management to sophisticated threat detection and response capabilities.
Network Security Architecture
Network security controls establish the perimeter defenses that protect your systems from external threats while enabling legitimate business communications. Firewall controls require organizations to implement and maintain network firewalls that restrict access based on predetermined rules and regularly review these configurations for appropriateness.
Network segmentation controls involve dividing your network into separate zones based on security requirements and trust levels. This segmentation helps contain potential security breaches and limits the access that different types of users and systems have to sensitive resources.
Intrusion detection and prevention controls require organizations to implement systems that can identify and respond to potential security threats in real-time. These systems should be properly configured, regularly updated, and monitored by qualified security personnel.
Application Security
Application security controls address the risks associated with software applications, whether developed internally or obtained from third parties. Secure development lifecycle controls establish procedures for incorporating security considerations throughout the application development process, from initial design through deployment and maintenance.
Application vulnerability management controls require organizations to regularly assess applications for security vulnerabilities and implement appropriate remediation measures. This includes both automated vulnerability scanning and manual security testing procedures.
Application access controls ensure that applications properly authenticate users and authorize access to specific functions and data based on user roles and business requirements. These controls should include session management, input validation, and output encoding measures.
Endpoint Security
Endpoint security controls address the risks associated with the various devices that connect to your network, including laptops, desktops, mobile devices, and servers. Endpoint protection controls require organizations to implement and maintain anti-malware software, endpoint detection and response tools, and other security measures on all devices within their environment.
Device management controls establish procedures for managing the lifecycle of devices from procurement through disposal, including configuration management, patch management, and secure disposal procedures.
Mobile device management controls address the additional risks associated with mobile devices, including data encryption, remote wipe capabilities, and restrictions on application installation and data access.
Security Incident Response
Security incident response controls ensure that organizations can effectively identify, contain, and recover from security incidents while minimizing their impact on business operations and customer data. Incident detection controls establish procedures for identifying potential security incidents through various means, including automated monitoring, user reports, and external notifications.
Incident response procedures define the steps that must be taken when a security incident is identified, including immediate containment measures, investigation procedures, and communication requirements. These procedures should be regularly tested and updated based on lessons learned from actual incidents and industry best practices.
Post-incident analysis controls require organizations to conduct thorough reviews of security incidents to identify root causes, assess the effectiveness of response procedures, and implement improvements to prevent similar incidents in the future.
Frequently Asked Questions (FAQs)
How long does SOC2 implementation typically take?
The timeline for SOC 2 implementation varies significantly based on your organization's starting point, scope, and complexity. For most organizations, initial implementation takes between 6 to 12 months, with smaller companies often completing the process more quickly than larger, more complex organizations. The timeline includes time for gap assessment, control implementation, documentation, and the minimum three-month period of control operation before the audit can begin.
What's the difference between SOC2 Type I and Type II audits?
SOC 2 Type I audits focus on the design of controls at a specific point in time, evaluating whether controls are properly designed to meet their stated objectives. Type II audits examine both the design and operating effectiveness of controls over a period of time, typically three to twelve months. Type II audits are generally preferred by customers and partners as they provide greater assurance about the ongoing effectiveness of security measures.
How much does SOC2 compliance cost?
SOC 2 compliance costs vary widely depending on factors such as organization size, scope, existing control maturity, and chosen auditor. Typical costs include internal resource allocation (often the largest component), external consulting fees, audit fees, and technology investments. Small to medium organizations might expect to invest between $50,000 to $200,000 in their first year, while larger organizations may invest significantly more.
Can we implement SOC2 controls without external help?
While it's possible to implement SOC 2 controls without external assistance, most organizations benefit from expert guidance, particularly during their first implementation. External consultants can help accelerate the implementation process, ensure comprehensive coverage of requirements, and provide valuable insights from experience with similar organizations. However, organizations with strong internal security expertise may choose to handle implementation internally.
How often do we need to conduct SOC2 audits?
SOC 2 audits are typically conducted annually to maintain current compliance status. However, the specific frequency may depend on customer requirements, regulatory obligations, and business needs. Some organizations choose to conduct audits more frequently, particularly in highly regulated industries or when significant changes occur to systems or processes.
What happens if we fail a SOC2 audit?
Audit failures, while concerning, are not uncommon, especially for first-time audits. Failed audits result in management letter comments or qualified opinions that identify specific deficiencies. Organizations can address these deficiencies and undergo remediation procedures or wait for the next audit cycle. The key is to view audit results as opportunities for improvement rather than failures.
How do we choose the right SOC2 auditor?
Selecting an appropriate auditor is crucial for a successful SOC 2 engagement. Consider factors such as the auditor's experience with your industry, size of organization, and specific technology stack. Evaluate their approach to the audit process, communication style, and ability to provide valuable insights beyond basic compliance. Cost should be considered but shouldn't be the primary factor in your decision.
What documentation is required for SOC2 compliance?
SOC 2 compliance requires extensive documentation including policies and procedures, system documentation, risk assessments, incident reports, monitoring evidence, training records, and vendor agreements. The documentation serves both as operational guidance and audit evidence. Organizations should establish document management procedures to ensure information remains current and accessible.
How do we maintain SOC2 compliance after achieving it?
Maintaining SOC 2 compliance requires ongoing attention to control operation, monitoring, and improvement. Establish regular review cycles, maintain comprehensive monitoring systems, ensure prompt remediation of identified issues, and keep documentation current. Consider SOC 2 compliance as an ongoing operational requirement rather than an annual audit event.
Can SOC2 compliance help with other regulatory requirements?
SOC 2 compliance often provides a strong foundation for meeting other regulatory and compliance requirements such as GDPR, HIPAA, or industry-specific standards. While SOC 2 doesn't automatically ensure compliance with other regulations, the control framework and operational maturity developed through SOC 2 implementation typically makes it easier to address additional compliance requirements.
Conclusion
Implementing a comprehensive SOC 2 control list is an investment in your organization's long-term security posture and customer trust. The framework provides a structured approach to identifying, implementing, and maintaining the security and operational controls necessary to protect sensitive data and ensure system reliability.
Success with SOC 2 implementation requires commitment from leadership, engagement across the organization, and a long-term perspective on security and risk management. While the initial implementation can be challenging and resource-intensive, the benefits extend far beyond compliance, including improved operational efficiency, enhanced security posture, and increased customer confidence.
The key to successful SOC 2 compliance lies in treating it as an ongoing operational discipline rather than a one-time project. Organizations that integrate SOC 2 controls into their regular business processes and continuously improve their control environment are best positioned to maintain compliance while deriving maximum value from their investment.
As the cybersecurity landscape continues to evolve and customer expectations for data protection increase, SOC 2 compliance becomes not just a nice-to-have credential but a business necessity. Organizations that proactively implement comprehensive SOC 2 control lists position themselves for sustainable growth and competitive advantage in an increasingly security-conscious marketplace.
Remember that SOC 2 compliance is a journey, not a destination. The most successful organizations view their initial audit as the beginning of a continuous improvement process that evolves with their business needs, threat landscape, and regulatory environment. By maintaining this perspective and committing to ongoing investment in security and operational excellence, your organization can achieve not just SOC2 compliance but a robust, resilient, and trusted operational framework that supports long-term business success.
Ready to master SOC2 compliance? Let Regulance transform your audit process from overwhelming to effortless. Start your compliance journey today!