SOC 2 Compliance: A Comprehensive Guide to Get Started and Win More Business Deals


SOC 2 compliance is an easier way for online businesses and SAAS platforms to demonstrate security and instill confidence to clients and partners. Enter SOC 2 compliance - a rigorous standard designed to ensure that your service organization manages data securely, protecting the interests of both your clients and your operation. But achieving SOC 2 compliance often feels like a daunting task for many companies, especially those just starting their journey into the realm of service audits. In this comprehensive guide, we'll break down the essentials of SOC 2 compliance, simplifying the process into manageable steps. By understanding the requirements and implementing best practices, you'll not only safeguard your business but also position yourself to win more deals. Prepare to explore how SOC 2 can elevate your company’s credibility and instill confidence in prospective clients. Whether you’re a startup or a seasoned enterprise, this guide will pave the way for successful compliance and unlocking new business opportunities.
SOC 2 Compliance and Its Impact on Winning Business Deals
In the ever-evolving digital landscape, where data breaches and cybersecurity threats are rampant, organizations are under immense pressure to demonstrate their commitment to data security. SOC 2 compliance emerges as a beacon of trust, offering businesses a framework to assure their clients and partners that their data is handled with utmost care. For Software as a Service (SaaS) platforms and online businesses, achieving SOC 2 compliance is not just about meeting regulatory requirements—it's about building a competitive edge.
SOC 2 compliance serves as a testament to a company's dedication to security and operational integrity. When prospective clients evaluate service providers, one of the first criteria they consider is the provider's ability to safeguard their sensitive information. A SOC 2 report, therefore, becomes a critical factor in the decision-making process, often tipping the scales in favor of compliant companies. This certification signals to clients that the organization has undergone a rigorous audit and adheres to high standards of data protection.
The business benefits of SOC 2 compliance extend beyond just winning new deals. It fosters trust and loyalty among existing clients, reducing churn rates and increasing customer retention. By aligning with SOC 2 requirements, companies can also streamline their internal processes, enhance their security posture, and mitigate risks. Ultimately, SOC 2 compliance is an investment in the company's reputation and long-term success, positioning it as a reliable and secure partner in the eyes of both current and potential clients.
Understanding SOC 2 Compliance
SOC 2, or System and Organization Controls 2, is a framework developed by the American Institute of Certified Public Accountants (AICPA) to assess and report on the controls at a service organization relevant to security, availability, processing integrity, confidentiality, and privacy. Unlike other compliance standards that focus solely on financial reporting, SOC 2 is specifically designed for technology and cloud computing companies, making it particularly relevant for SaaS providers.
The SOC 2 framework is built on a set of criteria known as the Trust Services Criteria (TSC). These criteria provide a structured approach for evaluating the effectiveness of an organization's controls. The primary goal is to ensure that the service provider can protect the data it processes and stores on behalf of its clients. A SOC 2 report is the outcome of an independent audit conducted by a certified public accountant (CPA) or a qualified firm, which evaluates the company's adherence to the TSC.
There are two types of SOC 2 reports: Type I and Type II. A SOC 2 Type I report assesses the design of controls at a specific point in time, providing a snapshot of the company's security posture. In contrast, a SOC 2 Type II report evaluates the operating effectiveness of those controls over a period, typically ranging from six months to a year. While a Type I report can be a good starting point, most clients and partners prefer a Type II report as it offers a more comprehensive assessment of the organization's ability to maintain robust security practices over time.
Key Principles of SOC 2: Security, Availability, Processing Integrity, Confidentiality, and Privacy
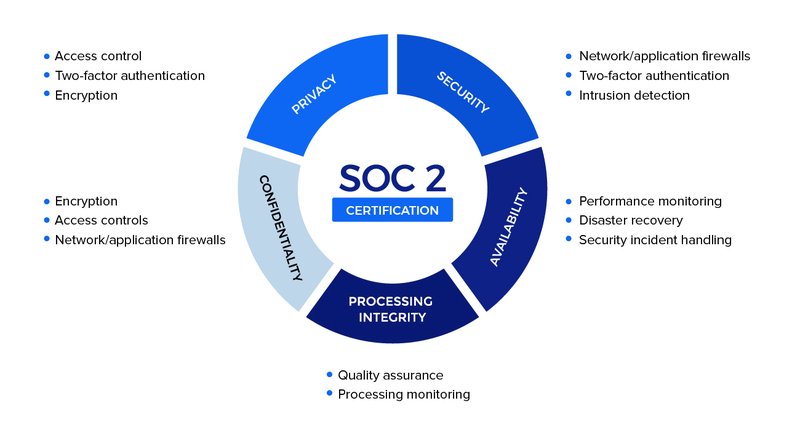
The Trust Services Criteria encompass five key principles, each addressing a different aspect of data protection and operational reliability. Understanding these principles is essential for any organization aiming to achieve SOC 2 compliance.
Security
The security principle focuses on protecting the system against unauthorized access, both physical and logical. It involves implementing controls to prevent data breaches, hacking, and other cyber threats. Security controls include firewalls, intrusion detection systems, multi-factor authentication, and regular security assessments. By demonstrating strong security measures, organizations can assure clients that their data is safe from malicious actors.
Availability
Availability ensures that the system is operational and accessible as agreed upon in service level agreements (SLAs). This principle emphasizes the importance of minimizing downtime and maintaining system performance. Controls related to availability include disaster recovery plans, redundancy, and monitoring systems to detect and address potential issues promptly. Ensuring high availability is crucial for businesses that rely on continuous access to services and data.
Processing Integrity
Processing integrity addresses the accuracy, completeness, and timeliness of data processing. It ensures that the system processes data as intended, without errors or unauthorized alterations. Controls under this principle include validation checks, error handling procedures, and quality assurance processes. Organizations must demonstrate that their systems can reliably process transactions and data, which is vital for maintaining client trust.
Confidentiality
The confidentiality principle focuses on protecting sensitive information from unauthorized access and disclosure. It involves implementing controls to ensure that confidential data, such as intellectual property, financial information, and personal data, is adequately protected. Encryption, access controls, and data classification are essential components of confidentiality. By safeguarding confidential information, organizations can prevent data leaks and maintain client confidence.
Privacy
Privacy pertains to the collection, use, retention, disclosure, and disposal of personal information in accordance with an organization's privacy notice and relevant regulations. Controls related to privacy include data minimization, consent management, and user rights management. Compliance with privacy principles is particularly important in today's regulatory environment, where data protection laws such as the GDPR and CCPA impose stringent requirements on how personal data is handled.
Steps to Achieve SOC 2 Compliance
Achieving SOC 2 compliance is a systematic process that requires careful planning, implementation, and ongoing evaluation. Here are the key steps to guide organizations through this journey.
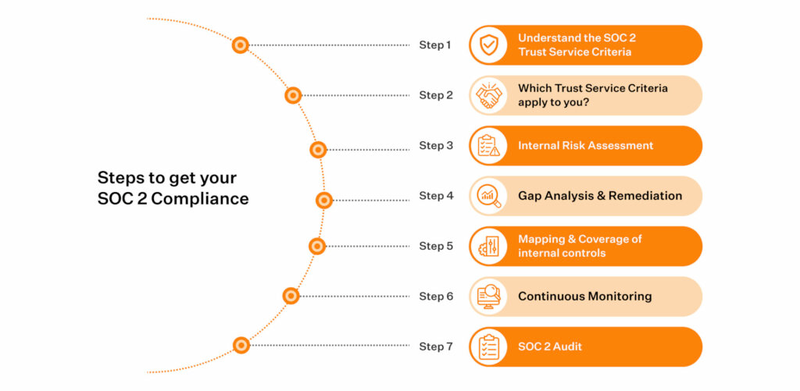
1. Conduct a Readiness Assessment
Before embarking on the SOC 2 compliance journey, it is crucial to conduct a readiness assessment. This initial step involves evaluating the current state of your organization's controls, policies, and procedures against the Trust Services Criteria. The readiness assessment helps identify gaps and areas that need improvement, providing a roadmap for achieving compliance. Engaging a qualified consultant or auditor during this phase can provide valuable insights and guidance.
2. Define the Scope
Defining the scope of the SOC 2 audit is essential to ensure that all relevant systems, processes, and services are included. The scope should align with the services provided to clients and the specific Trust Services Criteria being addressed. Clearly defining the scope helps streamline the audit process and ensures that all critical areas are covered. It is also important to communicate the scope to the audit team and relevant stakeholders to set clear expectations.
3. Implement Controls and Policies
Based on the findings of the readiness assessment, organizations need to implement the necessary controls and policies to address identified gaps. This step involves developing and documenting security policies, procedures, and protocols that align with the Trust Services Criteria. Controls may include access management, incident response, data encryption, and regular security training for employees. Effective implementation of controls is critical to achieving SOC 2 compliance and demonstrating a commitment to data security.
4. Perform Internal Testing
Before undergoing the formal SOC 2 audit, it is advisable to perform internal testing to evaluate the effectiveness of the implemented controls. Internal testing involves conducting mock audits, vulnerability assessments, and penetration testing to identify potential weaknesses and areas for improvement. This proactive approach allows organizations to address issues before the official audit, increasing the likelihood of a successful outcome.
5. Engage a Third-Party Auditor
Engaging a qualified third-party auditor is a crucial step in the SOC 2 compliance process. The auditor will conduct an independent assessment of your organization's controls and issue the SOC 2 report. It is important to select an auditor with experience in SOC 2 audits and a thorough understanding of the Trust Services Criteria. The auditor will review documentation, conduct interviews, and perform testing to evaluate the effectiveness of controls. Clear communication and collaboration with the auditor are essential throughout the audit process.
6. Address Audit Findings
Following the audit, the auditor will provide a report detailing any findings and recommendations for improvement. Organizations must address these findings promptly and implement corrective actions to rectify any deficiencies. This may involve updating policies, enhancing controls, and providing additional training to employees. Addressing audit findings demonstrates a commitment to continuous improvement and strengthens the organization's security posture.
7. Maintain Ongoing Compliance
Achieving SOC 2 compliance is not a one-time effort but an ongoing commitment. Organizations must establish processes for continuous monitoring, periodic reviews, and regular updates to controls and policies. This includes conducting internal audits, staying informed about emerging threats, and adapting to changes in the regulatory landscape. By maintaining ongoing compliance, organizations can ensure that they consistently meet the requirements of SOC 2 and provide clients with the assurance of robust data security.
The Role of Third-Party Auditors in SOC 2 Compliance
Third-party auditors play a pivotal role in the SOC 2 compliance process, providing an independent and objective assessment of an organization's controls. These auditors are typically certified public accountants (CPAs) or firms with expertise in information security and compliance. Their involvement is essential to ensure the credibility and reliability of the SOC 2 report.
Objective Assessment
One of the primary responsibilities of third-party auditors is to conduct an objective assessment of the organization's controls. They evaluate the design and operating effectiveness of controls based on the Trust Services Criteria. This involves reviewing documentation, conducting interviews with key personnel, and performing testing procedures. The auditor's independent perspective helps identify any weaknesses or gaps in the organization's security practices, providing valuable insights for improvement.
Issuing the SOC 2 Report
The culmination of the SOC 2 audit is the issuance of the SOC 2 report. This report provides a detailed evaluation of the organization's controls and their alignment with the Trust Services Criteria. It includes a description of the controls, the results of the auditor's testing, and any findings or recommendations. The SOC 2 report serves as a valuable tool for demonstrating compliance to clients, partners, and stakeholders. It provides assurance that the organization has implemented robust controls to protect data and maintain operational integrity.
Enhancing Credibility
Engaging a reputable third-party auditor enhances the credibility and trustworthiness of the SOC 2 report. Clients and partners rely on the auditor's expertise and independence to validate the organization's security practices. A well-respected auditor with a proven track record in SOC 2 audits can instill confidence in the report's findings, making it a powerful tool for winning new business deals. The auditor's reputation and experience add an extra layer of assurance, reinforcing the organization's commitment to data security.
Collaboration and Guidance
Throughout the audit process, third-party auditors collaborate closely with the organization, providing guidance and support. They help interpret the Trust Services Criteria, clarify audit requirements, and offer recommendations for strengthening controls. This collaborative approach fosters a positive relationship between the auditor and the organization, facilitating a smooth and efficient audit process. By working together, organizations can leverage the auditor's expertise to achieve and maintain SOC 2 compliance effectively.
Common Challenges in the SOC 2 Compliance Process
While SOC 2 compliance brings significant benefits, organizations often encounter various challenges during the process. Understanding these challenges and proactively addressing them can help streamline the compliance journey and ensure a successful outcome.
Resource Allocation
One of the primary challenges organizations face is allocating sufficient resources to achieve SOC 2 compliance. The process involves extensive documentation, implementation of controls, and ongoing monitoring, which can be resource-intensive. Smaller companies or startups may struggle to allocate the necessary time, budget, and personnel to meet the compliance requirements. It is crucial to plan and allocate resources effectively, considering the long-term benefits of SOC 2 compliance.
Complexity of Controls
The Trust Services Criteria encompass a wide range of controls, each requiring careful implementation and monitoring. Organizations often find it challenging to navigate the complexity of these controls and ensure they are adequately documented and enforced. The interdependencies between different controls and the need for consistent application across various systems and processes can add to the complexity. Engaging experienced consultants or auditors can help simplify the process and provide guidance on control implementation.
Evolving Threat Landscape
The cybersecurity landscape is constantly evolving, with new threats and vulnerabilities emerging regularly. Keeping up with these changes and adapting controls accordingly can be a significant challenge for organizations. SOC 2 compliance requires continuous monitoring and updating of controls to address emerging risks. Staying informed about the latest security trends, conducting regular risk assessments, and implementing proactive measures are essential to mitigate the impact of evolving threats.
Employee Awareness and Training
Achieving and maintaining SOC 2 compliance requires a strong culture of security awareness and employee training. Employees play a critical role in implementing and adhering to security controls. However, organizations often face challenges in ensuring that all employees are adequately trained and aware of their responsibilities. Regular training programs, clear communication of security policies, and fostering a security-conscious mindset are crucial to overcome this challenge.
Documentation and Evidence Collection
SOC 2 compliance involves extensive documentation and evidence collection to demonstrate the effectiveness of controls. Organizations may struggle with maintaining accurate and comprehensive documentation, especially when controls are spread across different departments and systems. It is essential to establish robust documentation processes, maintain up-to-date records, and ensure that evidence is readily available for audit purposes. Leveraging automation tools and centralized documentation repositories can streamline this process and reduce the administrative burden.
Best Practices for Maintaining SOC 2 Compliance
Maintaining SOC 2 compliance requires ongoing effort and a commitment to continuous improvement. Implementing best practices can help organizations sustain their compliance posture and effectively manage security risks.
Establish a Compliance Team
Forming a dedicated compliance team is a crucial step in maintaining SOC 2 compliance. This team should include representatives from various departments, such as IT, legal, and operations, to ensure a comprehensive approach to compliance. The compliance team is responsible for overseeing the implementation and maintenance of controls, conducting regular audits, and staying informed about regulatory changes. By having a dedicated team, organizations can ensure that compliance remains a top priority and that responsibilities are clearly defined.
Conduct Regular Risk Assessments
Regular risk assessments are essential to identify and mitigate potential security threats. These assessments help organizations understand their risk landscape, evaluate the effectiveness of existing controls, and implement additional measures as needed. Risk assessments should be conducted at least annually or whenever significant changes occur, such as the introduction of new systems or processes. By proactively identifying and addressing risks, organizations can maintain a robust security posture and ensure ongoing compliance with SOC 2 requirements.
Implement Continuous Monitoring
Continuous monitoring is a key component of maintaining SOC 2 compliance. It involves real-time tracking of security events, system performance, and control effectiveness. Implementing automated monitoring tools and security information and event management (SIEM) systems can help organizations detect and respond to potential security incidents promptly. Continuous monitoring ensures that controls remain effective and allows organizations to identify and address issues before they escalate.
Regularly Review and Update Policies
Security policies and procedures should be reviewed and updated regularly to reflect changes in the threat landscape, regulatory requirements, and organizational processes. This includes reviewing access control policies, incident response plans, and data classification guidelines. Regular policy reviews ensure that controls remain relevant and effective, and that employees are aware of their responsibilities. It is also important to communicate any policy changes to all employees and provide necessary training to ensure compliance.
Foster a Culture of Security Awareness
Creating a culture of security awareness is essential for maintaining SOC 2 compliance. Employees should be educated about security best practices, potential threats, and their role in safeguarding data. Regular training sessions, awareness campaigns, and simulated phishing exercises can help reinforce security awareness and ensure that employees remain vigilant. Encouraging a security-conscious mindset across the organization reduces the risk of human error and strengthens the overall security posture.
Leverage Technology Solutions
Leveraging technology solutions can streamline the compliance process and enhance security controls. Automation tools can help with documentation, evidence collection, and monitoring, reducing the administrative burden on compliance teams. Security solutions such as encryption, multi-factor authentication, and intrusion detection systems can enhance the effectiveness of controls. By adopting the right technology, organizations can improve their compliance efforts and ensure robust data protection.
Engage External Expertise
Engaging external expertise, such as consultants or auditors, can provide valuable insights and guidance on maintaining SOC 2 compliance. External experts bring a fresh perspective and can help organizations identify areas for improvement and implement best practices. Regularly engaging auditors for independent assessments ensures that controls remain effective and that compliance efforts are aligned with industry standards. External expertise can also help organizations stay informed about regulatory changes and emerging threats.
Document and Retain Evidence
Maintaining comprehensive documentation and retaining evidence is crucial for demonstrating compliance during audits. Organizations should establish processes for documenting controls, policies, procedures, and security events. Evidence should be collected and stored in a centralized repository, ensuring that it is readily available for audit purposes. Regularly reviewing and updating documentation ensures accuracy and completeness, reducing the risk of audit findings.
Stay Informed about Regulatory Changes
The regulatory landscape is constantly evolving, with new requirements and standards emerging regularly. Organizations must stay informed about these changes and adapt their compliance efforts accordingly. Subscribing to industry newsletters, participating in compliance forums, and engaging with regulatory bodies can help organizations stay up to date. By proactively addressing regulatory changes, organizations can ensure ongoing compliance and avoid potential penalties.
Conduct Internal Audits
Regular internal audits are essential for maintaining SOC 2 compliance. Internal audits help organizations identify potential weaknesses, evaluate the effectiveness of controls, and implement corrective actions. Conducting internal audits on a periodic basis or whenever significant changes occur ensures that compliance efforts remain on track. Internal audits also provide an opportunity to review documentation, test controls, and address any gaps before the formal SOC 2 audit.
Conclusion: Taking the First Steps Towards SOC 2 Compliance
Achieving SOC 2 compliance is a journey that requires careful planning, dedication, and ongoing effort. By understanding the key principles of SOC 2, conducting a readiness assessment, and implementing robust controls, organizations can demonstrate their commitment to data security and operational integrity. Engaging a qualified third-party auditor and addressing audit findings further enhances credibility and trustworthiness.
While the SOC 2 compliance process may present challenges, organizations can overcome them by allocating resources effectively, fostering a culture of security awareness, and leveraging technology solutions. Regular risk assessments, continuous monitoring, and internal audits ensure that compliance efforts remain effective and aligned with industry standards.
Taking the first steps towards SOC 2 compliance not only safeguards the organization but also positions it to win more business deals. Clients and partners seek reliable and secure service providers, and a SOC 2 report acts as a powerful testament to the organization's commitment to data protection. By embracing SOC 2 compliance, organizations can elevate their credibility, instill confidence in prospective clients, and unlock new business opportunities.
Whether you are a startup or an established enterprise, the journey to SOC 2 compliance is a valuable investment in your organization's future. By following the steps outlined in this guide and implementing best practices, you can navigate the compliance process with confidence and achieve long-term success. Remember, SOC 2 compliance is not just a checkbox - it's a continuous commitment to excellence in data security and operational integrity.
Get started with your SOC 2 today using our compliance management service. Regulance uses AI to automate compliance and helps you to get things done properly and faster. Schedule a demo here with our compliance experts to learn more.