PCI DSS Cardholder Data Environment Explained: Compliance Made Simple


Introduction
Every day, millions of payment card transactions flow through digital systems worldwide, creating a massive web of sensitive financial data. At the heart of this ecosystem lies the PCI DSS Cardholder Data Environment (CDE); a critical infrastructure that determines whether your customers' payment information remains secure or becomes vulnerable to cybercriminals.
For businesses processing card payments, mastering the CDE is about building an impenetrable fortress around your most valuable digital assets while maintaining the seamless payment experiences customers expect.
This comprehensive guide demystifies the PCI DSS Cardholder Data Environment, revealing how smart businesses transform compliance challenges into competitive advantages through strategic security implementation.
Understanding the Cardholder Data Environment (CDE)
The PCI DSS Cardholder Data Environment is a complex, interconnected ecosystem comprising technology infrastructure, business processes, physical locations, and human resources that collectively store, process, transmit, or otherwise handle payment card data in any form. This environment serves as the digital fortress protecting some of the most valuable and sought-after information in the cybercriminal underworld.
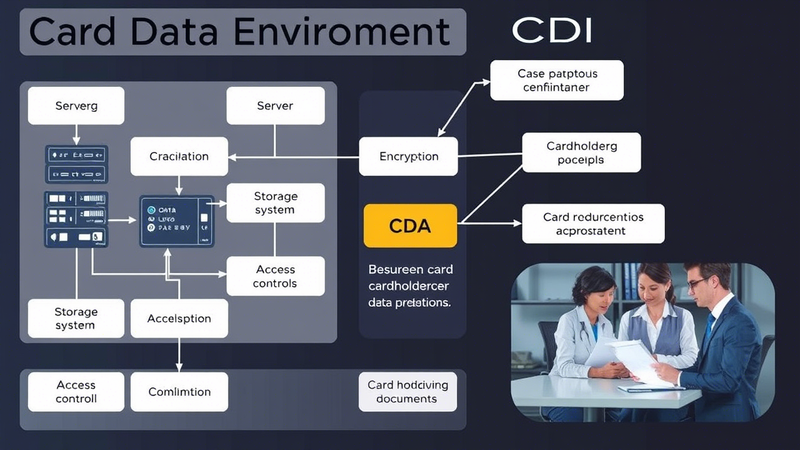
Typical elements that comprise a comprehensive CDE include:
Payment Processing Infrastructure: This foundational layer includes payment terminals, point-of-sale (POS) systems, mobile payment devices, online payment gateways, and any hardware or software directly involved in capturing and processing payment card transactions. These systems serve as the primary entry points for cardholder data into your environment.
Data Storage Systems: Databases, file servers, cloud storage platforms, backup systems, and archive solutions where cardholder data is stored, whether permanently or temporarily. These repositories often contain the largest concentrations of sensitive payment information and represent high-value targets for cybercriminals.
Network Infrastructure: The digital highways that carry sensitive payment information between systems, including routers, switches, wireless access points, load balancers, and any network equipment that transmits cardholder data. The security of these communication pathways is crucial for maintaining data integrity during transit.
Security Control Systems: Firewalls, intrusion detection and prevention systems (IDS/IPS), security information and event management (SIEM) platforms, vulnerability scanners, and other security technologies deployed to monitor, detect, and prevent unauthorized access to cardholder data.
Supporting Applications and Services: Payment processing applications, customer relationship management (CRM) systems, enterprise resource planning (ERP) platforms, reporting tools, and any software that processes or has access to payment card information as part of its functionality.
Why Businesses Handling Payments Must Understand the CDE
For any business that accepts card payments whether through traditional in-person transactions, e-commerce platforms, mobile applications, or emerging payment technologies, developing a deep understanding of their PCI DSS Cardholder Data Environment is absolutely non-negotiable.
Regulatory Compliance and Legal Obligations: Payment card brands (Visa, Mastercard, American Express, Discover, JCB) and acquiring banks universally require PCI DSS compliance as a condition of accepting their cards. This is a contractual obligation that carries significant legal and financial implications. Organizations that fail to maintain compliance face a cascading series of penalties, including substantial fines that can reach millions of dollars, increased transaction processing fees, mandatory audits at the organization's expense, and ultimately the potential revocation of payment processing privileges. Losing the ability to accept card payments in today's cashless economy can effectively cripple or destroy a business overnight.
Comprehensive Risk Reduction: A weak, poorly designed, or inadequately managed PCI DSS Cardholder Data Environment dramatically increases an organization's exposure to data breaches, payment fraud, identity theft, and related cybercrimes. The ripple effects of a payment data breach extend far beyond the immediate incident, often resulting in years of legal proceedings, regulatory investigations, customer lawsuits, remediation costs, and ongoing monitoring requirements. By properly securing the CDE, organizations can significantly reduce their risk profile and avoid the devastating financial and operational consequences associated with payment data compromises.
Customer Trust and Brand Reputation: In an era where data breaches make headline news and consumers are increasingly aware of privacy and security risks, customers actively seek out businesses that demonstrate genuine commitment to protecting their sensitive information. Organizations with strong PCI DSS compliance records and robust cardholder data protection practices enjoy competitive advantages in customer acquisition and retention. Conversely, businesses that experience payment data breaches often suffer long-lasting reputation damage that can take years or even decades to repair, if recovery is possible at all.
Operational Efficiency and Cost Management: By clearly identifying and properly segmenting their PCI DSS Cardholder Data Environment, businesses can significantly streamline their compliance efforts, focusing security investments and resources on the systems and processes that truly matter most. This targeted approach not only improves security effectiveness but also reduces compliance costs, minimizes operational disruptions, and enables more efficient allocation of IT and security resources.
Insurance and Risk Management Benefits: Many cyber liability insurance policies offer reduced premiums or enhanced coverage options for organizations that maintain demonstrable PCI DSS compliance. Additionally, some insurance providers require proof of compliance as a prerequisite for coverage, making CDE security not just a regulatory requirement but also a business continuity necessity.
The CDE's Role in the Payment Security
The PCI DSS Cardholder Data Environment serves as the critical foundation of your organization's payment security infrastructure. Think of it as the secure vault where your most sensitive customer information, credit card numbers, expiration dates, and other payment details are processed, stored, or transmitted.
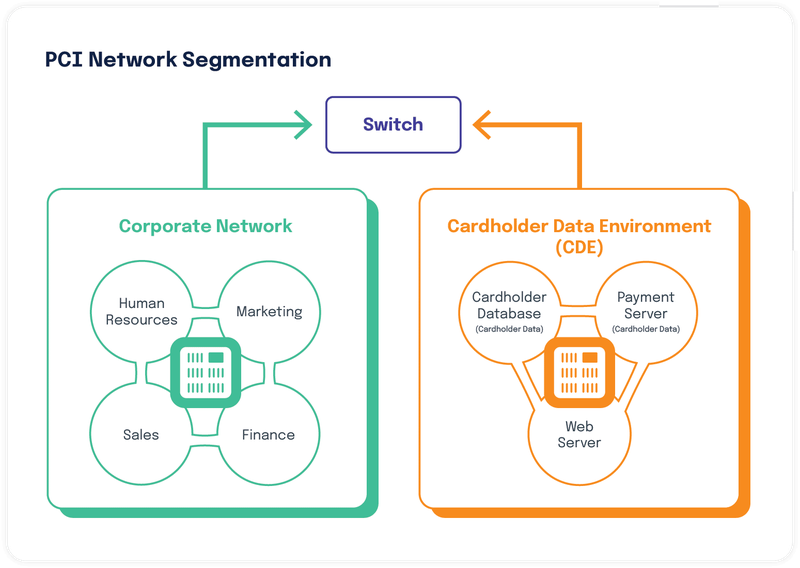
Your payment security operates through multiple defensive layers, starting with external protections like firewalls and intrusion prevention systems at your network perimeter. These outer defenses work alongside internal controls such as network segmentation, access management, encryption, and continuous monitoring systems.
However, the core principle remains simple: if your CDE isn't properly secured, all other security measures become ineffective. Even if attackers bypass your external defenses, a well-protected cardholder data environment ensures your customers' sensitive information remains safe. This is why PCI DSS standards require businesses to clearly define, properly isolate, and thoroughly secure their CDE.
Effective CDE segmentation delivers multiple business benefits beyond regulatory compliance. It reduces the number of systems requiring full PCI DSS controls, lowering both compliance costs and operational complexity. Proper segmentation also contains security incidents within specific network zones, preventing threats from spreading across your entire IT infrastructure.
This focused approach allows organizations to allocate security resources more efficiently, implementing stronger controls where they matter most. By concentrating protection efforts on the cardholder data environment, businesses create a more robust security posture that safeguards both their operations and customer trust while meeting PCI DSS requirements effectively.
Why PCI DSS Is Critical for CDE Security
Compliance with PCI DSS Cardholder Data Environment standards delivers substantial and measurable benefits that extend far beyond simple regulatory checkbox satisfaction. These benefits create tangible value for organizations while simultaneously strengthening the overall security and resilience of the global payment infrastructure.
Proactive Data Breach Prevention: The comprehensive security controls mandated by PCI DSS including advanced encryption requirements, strict access controls, network segmentation, and continuous monitoring, work synergistically to significantly reduce the likelihood of successful data breaches. By implementing these controls specifically within the Cardholder Data Environment, organizations create multiple layers of protection that make it exponentially more difficult for attackers to successfully compromise sensitive payment data. Statistical evidence consistently demonstrates that PCI DSS compliant organizations experience data breaches at substantially lower rates than non-compliant entities.
Substantial Financial Loss Mitigation: The financial impact of payment data breaches can be catastrophic, often reaching millions of dollars in direct costs including forensic investigations, legal fees, regulatory fines, customer notification expenses, credit monitoring services, and brand recovery efforts. Beyond these immediate costs, organizations often face years of increased operational expenses related to enhanced monitoring, additional security measures, and elevated cyber insurance premiums. PCI DSS compliance represents a fraction of the potential cost of a major data breach, making it one of the most cost-effective security investments an organization can make.
Business Continuity Assurance: The loss of payment processing capabilities represents an existential threat to most modern businesses. Payment card brands and acquiring banks can immediately suspend an organization's ability to accept card payments following a data breach or compliance violation. For many businesses, this suspension effectively halts revenue generation and can lead to permanent closure within days or weeks. Maintaining PCI DSS compliance ensures uninterrupted payment processing capabilities and protects against this critical business risk.
Enhanced Customer Confidence and Competitive Advantage: In a marketplace where consumers are increasingly concerned about data privacy and security, demonstrating genuine commitment to protecting customer information provides significant competitive advantages. PCI DSS compliance serves as tangible proof of an organization's dedication to data protection, often influencing customer purchasing decisions and loyalty. Many B2B customers now require proof of PCI DSS compliance before entering into business relationships, making compliance a prerequisite for accessing certain markets and opportunities.
Improved Overall Security Posture: The security measures required for PCI DSS compliance often strengthen an organization's defenses against a wide range of cyber threats beyond just payment data breaches. The network security, access controls, monitoring systems, and security policies required by the standard create a more robust and resilient IT infrastructure that better protects all organizational assets and data types.
Key PCI DSS Requirements for Securing the CDE
The PCI DSS framework consists of 12 fundamental requirements organized into six logical control categories, each designed to address specific aspects of Cardholder Data Environment security. These requirements work together to create a comprehensive security program that protects cardholder data throughout its entire lifecycle within the organization.
Build and Maintain Secure Networks and Systems: This foundational category requires organizations to install and maintain properly configured firewalls to protect the CDE, eliminate default passwords and security settings on all system components, and maintain secure configurations across all network devices and systems. These controls establish the basic security infrastructure necessary to protect cardholder data from network-based attacks and unauthorized access attempts.
Protect Stored Cardholder Data: When organizations must store cardholder data, PCI DSS mandates robust protection measures including strong encryption of stored data, proper key management practices, masking of primary account numbers (PANs) in displays and reports, and secure data retention and disposal procedures. These requirements ensure that even if attackers gain access to storage systems, the cardholder data remains protected and unusable.
Encrypt Transmission of Cardholder Data Across Public Networks: All cardholder data transmitted across untrusted networks must be protected using strong encryption protocols and proper key management practices. This requirement addresses the significant risks associated with data interception during transmission and ensures end-to-end protection of sensitive information as it moves through the payment processing chain.
Restrict Access to Cardholder Data by Business Need-to-Know: PCI DSS requires organizations to implement strict access controls that limit who can access cardholder data based on legitimate business requirements. This includes role-based access controls, unique user identification systems, proper authentication mechanisms, and regular access reviews to ensure access privileges remain appropriate over time.
Regularly Monitor and Test Networks: Continuous monitoring and testing requirements include comprehensive logging of all access to system components and cardholder data, deployment of intrusion detection systems, regular vulnerability assessments, and penetration testing. These controls enable organizations to detect and respond to security incidents quickly while proactively identifying and addressing potential vulnerabilities.
Maintain Information Security Policies: Organizations must establish, maintain, and regularly update comprehensive information security policies that address all aspects of cardholder data protection. These policies must be communicated to all personnel and regularly reviewed to ensure they remain current with evolving threats and business requirements.
Together, these requirements create a robust, multi-layered defense system that significantly strengthens the security of the entire PCI DSS Cardholder Data Environment while providing clear guidance for implementation and ongoing maintenance.
What Data Falls Under Protection in the CDE?
The PCI DSS Cardholder Data Environment is specifically designed to protect two distinct categories of sensitive information, each presenting unique risks and requiring different levels of protection.
Cardholder Data (CHD): This category includes the Primary Account Number (PAN), which serves as the unique identifier for each payment card and represents the core element that must be protected in all cardholder data scenarios. Additionally, when stored together with the PAN, sensitive elements such as the cardholder’s name, expiration date, and service code also fall under protection requirements. The PAN alone is sufficient to define data as cardholder data requiring full PCI DSS protection, even when other elements are not present.
Sensitive Authentication Data (SAD): This highly sensitive category encompasses security-related information used to authenticate cardholders and authorize transactions. This includes full magnetic stripe data, card verification codes (CVV/CVC), PIN numbers, and PIN blocks. Notably, PCI DSS strictly prohibits the storage of sensitive authentication data after transaction authorization, even by compliant organizations, due to the extreme risk these data elements present if compromised.
The value of this protected information on illegal markets cannot be overstated. Complete payment card profiles can sell for hundreds of dollars per record on dark web marketplaces, while bulk databases containing thousands of records can generate millions in illegal profits. This economic reality explains why cardholder data remains one of the most actively targeted types of information by cybercriminals worldwide.
Organizations must also be aware that cardholder data protection requirements extend to any systems or processes that handle this information, even temporarily. This includes backup systems, log files, temporary processing files, development and testing environments, and any other locations where protected data might reside during normal business operations or system maintenance activities.
Components and Systems That Form the CDE
The modern PCI DSS Cardholder Data Environment encompasses a diverse and complex array of interconnected systems, applications, and infrastructure components.
Transaction Processing Systems: Point-of-sale (POS) devices, payment terminals, mobile payment readers, and kiosks represent the primary entry points where cardholder data first enters the organizational environment. These systems often operate in public or semi-public spaces, making them particularly vulnerable to physical tampering and requiring specialized security measures including tamper-evident seals, encryption of stored data, and secure communication protocols.
Payment Processing Applications: Software applications that facilitate payment processing, including e-commerce platforms, mobile payment apps, recurring billing systems, and custom payment applications. These systems often integrate with multiple other components and may process high volumes of transactions, requiring robust application security measures and regular security testing.
Data Storage and Management Systems: Databases, file servers, data warehouses, cloud storage platforms, and backup systems where cardholder data is stored, whether permanently or temporarily. These systems often contain the largest concentrations of sensitive data and require the strongest protection measures including encryption, access controls, and monitoring.
Network Infrastructure Components: Routers, switches, firewalls, load balancers, wireless access points, and other network equipment that carry or control access to cardholder data. These components form the digital pathways through which sensitive information flows and require careful configuration and monitoring to prevent unauthorized access or data interception.
Security and Monitoring Systems: SIEM platforms, intrusion detection systems, vulnerability scanners, log management tools, and other security technologies deployed specifically to protect the CDE. While these systems typically don't process cardholder data directly, they require access to network traffic and system logs that may contain sensitive information.
Supporting Infrastructure: Endpoints such as workstations, laptops, and mobile devices used by personnel who access cardholder data, as well as supporting systems like identity management platforms, patch management systems, and configuration management tools that maintain CDE security.
Third-Party Services and Cloud Platforms: External vendors, service providers, cloud platforms, and managed service providers that store, process, or transmit cardholder data on behalf of the organization. These relationships require careful due diligence, contractual protections, and ongoing monitoring to ensure compliance throughout the service provider ecosystem.
Every component within the PCI DSS Cardholder Data Environment must meet the relevant PCI DSS security requirements based on how it handles or interacts with cardholder data. This comprehensive approach ensures that there are no weak links in the security chain that could be exploited by attackers to compromise sensitive payment information.
Conclusion
The PCI DSS Cardholder Data Environment serves as the fundamental backbone of secure payment processing in our increasingly digital and interconnected global economy. As cyber threats continue to evolve in sophistication and frequency, and as consumers become more aware of their privacy rights and security expectations, the importance of properly understanding, implementing, and maintaining a secure CDE cannot be overstated.
The benefits of robust CDE security extend far beyond simple compliance checkbox satisfaction. Organizations with strong payment security programs enjoy enhanced customer trust, competitive advantages in the marketplace, reduced operational risks, lower insurance costs, and greater resilience against the ever-present threat of cyberattacks. In contrast, organizations that neglect their PCI DSS Cardholder Data Environment obligations face escalating risks including devastating data breaches, massive financial penalties, loss of payment processing capabilities, and potentially irreparable damage to their reputation and brand value.
Secure your PCI DSS Cardholder Data Environment today with Regulance AI—turn compliance into a business advantage.