NIST Risk Management Framework 2025: The Complete Guide to RMF Implementation


Introduction
NIST Risk Management Framework (RMF) is the practical playbook for organizations that need to manage cybersecurity risk with discipline and confidence. In this 2025 guide, you’ll get a clear, step-by-step view of RMF implementation, what to categorize, how to select and tailor controls, ways to assess and authorize systems, and how to build continuous monitoring that actually works in cloud-first, hybrid, and DevOps environments. Written for security leaders, auditors, and busy IT teams, this intro cuts through the jargon to show how RMF turns compliance into repeatable risk management, reduces blind spots, and helps your organization make smarter security investments in an era of faster threats and tighter regulations.
What is the NIST Risk Management Framework?
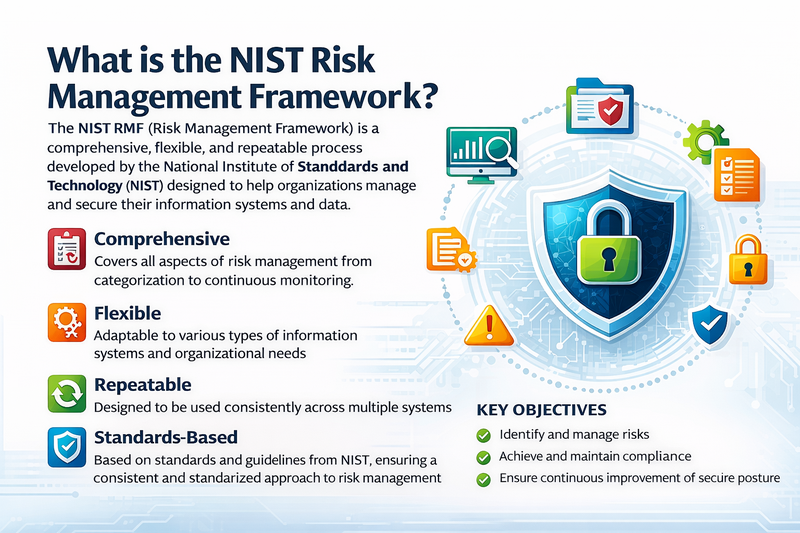
The NIST Risk Management Framework (RMF) represents a comprehensive methodology for integrating security, privacy, and cyber supply chain risk management activities into the system development life cycle. Think of it as a systematic approach that helps organizations manage information security and privacy risks in a way that's both thorough and practical.
Originally developed for federal information systems, the NIST RMF has evolved into a widely adopted standard that organizations across all sectors use to establish and maintain effective security programs. The framework provides a disciplined, structured, and flexible process for managing security and privacy risks that includes information security categorization, security control selection, implementation, assessment, authorization, and monitoring.
The foundation of NIST RMF rests on the principle that risk management is not a one-time activity but an ongoing process that must be integrated into every aspect of an organization's operations. This approach recognizes that threats evolve constantly, business requirements change, and technology landscapes shift – requiring security programs that can adapt and respond effectively.
What makes NIST RMF different from other security frameworks is its emphasis on risk-based decision making throughout the entire system lifecycle. Rather than applying a one-size-fits-all approach to security, the framework helps organizations tailor their security measures based on the actual risks they face, the value of the assets they're protecting, and the potential impact of security incidents.
The framework integrates seamlessly with other NIST publications, particularly the NIST Cybersecurity Framework (CSF) and various NIST Special Publications, creating a comprehensive ecosystem of guidance that organizations can use to build mature security programs.
The Six Steps of NIST RMF: A Detailed Breakdown
The NIST Risk Management Framework organizes risk management activities into six distinct but interconnected steps that guide organizations through the complete lifecycle of system security and privacy risk management. Each step builds upon the previous ones, creating a comprehensive approach to managing information security risks.
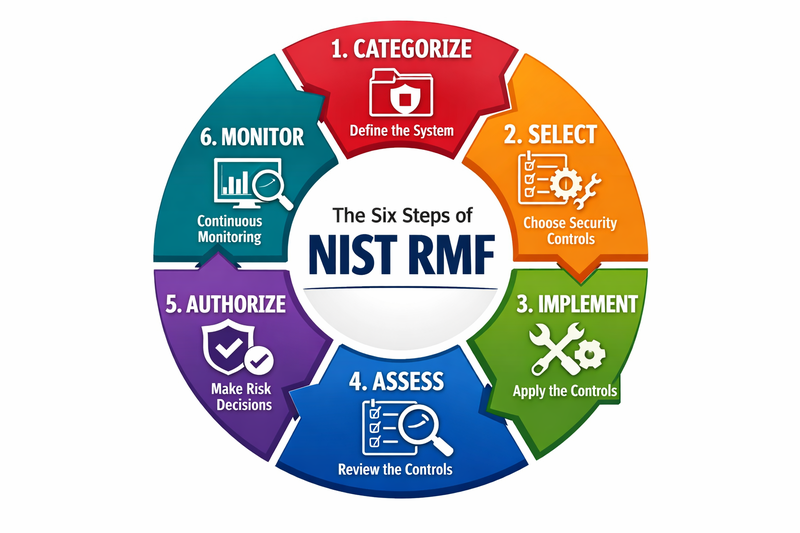
Step 1: Categorize Information Systems
The journey begins with understanding what you're protecting. System categorization involves identifying the information types processed, stored, or transmitted by the information system and determining the potential impact levels for confidentiality, integrity, and availability.
This step requires organizations to conduct thorough inventories of their information systems and data types. Teams must evaluate the potential impact of security breaches on organizational operations, assets, individuals, other organizations, and national security interests. The categorization process uses impact levels of low, moderate, or high based on Federal Information Processing Standards (FIPS) 199 guidelines.
The categorization process involves several critical activities. Organizations must identify all information types within the system, determine the impact level for each information type across the three security objectives, and establish the overall system categorization based on the highest impact level identified. This foundational step influences all subsequent risk management activities.
Step 2: Select Security Controls
Once systems are properly categorized, organizations must select appropriate security controls from the NIST Special Publication 800-53 catalog. This extensive catalog contains hundreds of security and privacy controls organized into families such as access control, incident response, system and communications protection, and risk assessment.
The control selection process begins with baseline security controls based on the system's impact categorization. Low-impact systems require fewer controls than high-impact systems, but organizations must also consider specific threat environments, business requirements, and organizational risk tolerance when making final selections.
Tailoring activities play a crucial role in this step. Organizations can modify baseline controls through scoping guidance, compensating controls, organizational parameters, and selection of alternative implementations. This flexibility allows organizations to adapt the framework to their specific operational environments while maintaining appropriate security postures.
Step 3: Implement Security Controls
Implementation transforms selected security controls from documentation into operational reality. This step involves deploying security controls within information systems and their operating environments, often requiring significant coordination between security teams, system administrators, and business stakeholders.
Successful implementation requires detailed planning and project management. Organizations must develop implementation plans that specify timelines, resource requirements, dependencies, and success criteria. Implementation often occurs in phases, with critical controls receiving priority and complex controls requiring extended deployment timelines.
Documentation becomes critical during implementation. Organizations must maintain detailed records of how controls are implemented, including any deviations from standard implementations, compensating controls, or alternative approaches. This documentation supports later assessment activities and provides evidence of due diligence in security risk management.
Step 4: Assess Security Controls
Assessment activities verify that security controls are implemented correctly and operating as intended. This step involves comprehensive testing and evaluation of security controls to determine their effectiveness in reducing or eliminating identified vulnerabilities and meeting specified security requirements.
Assessment methodologies vary based on control types and organizational preferences. Some controls require technical testing through vulnerability scans or penetration tests, while others need procedural reviews or interviews with key personnel. Assessment teams must use appropriate testing methods to validate control effectiveness accurately.
Independent assessment adds credibility and objectivity to the process. Many organizations engage third-party assessors or establish independent internal assessment teams to evaluate control implementations. These assessors must have appropriate expertise and access to conduct thorough evaluations without conflicts of interest.
Step 5: Authorize Information Systems
Authorization represents the formal decision by organizational leadership to accept the risks associated with operating an information system. This step culminates in the issuance of an Authorization to Operate (ATO), which documents management's acceptance of residual risks and commitment to ongoing risk management activities.
The authorization process involves several key stakeholders. Authorizing officials must review assessment results, risk determinations, and proposed risk mitigation strategies before making authorization decisions. These officials bear responsibility for the security risks associated with information system operations.
Risk determination activities support authorization decisions by analyzing assessment results, identifying residual risks, and proposing risk mitigation strategies. Organizations must present clear, actionable information that enables authorizing officials to make informed decisions about acceptable risk levels.
Step 6: Monitor Security Controls
Continuous monitoring maintains awareness of threats, vulnerabilities, and security control effectiveness throughout the system lifecycle. This ongoing process ensures that security measures remain effective as systems evolve, threats change, and business requirements shift.
Monitoring strategies must address multiple dimensions of security risk. Organizations need to monitor for new vulnerabilities in system components, changes in threat environments, modifications to system configurations, and updates to security requirements. Automated tools can support many monitoring activities, but human analysis remains essential for interpreting results and making risk decisions.
Ongoing authorization decisions may be required when monitoring activities identify significant changes in risk posture. Organizations must establish clear criteria for when system changes require authorization review and implement processes for managing continuous authorization in dynamic environments.
Key Benefits of Implementing NIST RMF
Organizations that successfully implement the NIST Risk Management Framework typically experience significant improvements across multiple dimensions of their security programs. These benefits extend beyond simple compliance to encompass operational efficiency, risk reduction, and business enablement.
Enhanced Risk Visibility and Management stands as perhaps the most significant benefit. The framework provides organizations with systematic approaches to identifying, assessing, and managing information security risks. This comprehensive visibility enables more informed decision-making about security investments and risk acceptance. Organizations can prioritize security efforts based on actual risk levels rather than assumptions or generic best practices.
Improved Security Control Effectiveness results from the framework's emphasis on tailored control selection and rigorous assessment processes. Rather than implementing generic security measures, organizations select and implement controls specifically designed to address their identified risks. The assessment and monitoring processes ensure these controls continue operating effectively over time.
Stronger Compliance Posture emerges from the framework's systematic approach to documenting security practices and maintaining evidence of due diligence. Many regulatory requirements align well with NIST RMF processes, making compliance easier to achieve and maintain. The framework's documentation requirements create comprehensive audit trails that support compliance demonstrations.
Better Resource Allocation and Cost Management becomes possible through the framework's risk-based approach. Organizations can justify security investments more effectively by tying them to specific risk reduction objectives. The framework helps prevent both over-investment in low-risk areas and under-investment in high-risk areas.
Enhanced Stakeholder Communication improves significantly through the framework's structured approach to risk communication. Technical security teams can articulate security needs and achievements in business terms that executive leadership understands. The framework's common vocabulary facilitates better coordination between different organizational functions.
Scalability and Flexibility allow organizations to adapt the framework to their specific needs and maturity levels. Small organizations can implement basic RMF processes while large enterprises can develop sophisticated continuous monitoring programs. The framework grows with organizations as their security programs mature.
NIST RMF Implementation Challenges and Solutions
While the NIST Risk Management Framework provides tremendous value, implementation isn't without challenges. Understanding common obstacles and proven solutions helps organizations navigate implementation more successfully.
Resource and Expertise Requirements often present the first major hurdle. Implementing NIST RMF requires significant time investments from qualified personnel who understand both technical security controls and business operations. Many organizations struggle to find staff with appropriate expertise or to allocate sufficient time for thorough implementation.
Solution approaches include phased implementation strategies that spread resource requirements over time, strategic use of external consultants for specialized expertise, and investment in staff training and development. Organizations should also consider starting with pilot implementations on less critical systems to build internal expertise before tackling mission-critical systems.
Documentation and Process Overhead can overwhelm organizations, particularly those with limited administrative resources. The framework requires extensive documentation of systems, controls, assessments, and ongoing monitoring activities. This documentation burden can seem overwhelming and may create resistance to implementation.
Effective solutions focus on automation and process efficiency. Modern governance, risk, and compliance (GRC) tools can automate much of the documentation and workflow management required by the framework. Organizations should also focus on creating reusable documentation templates and standardizing processes to reduce duplicated effort.
Integration with Existing Processes often proves challenging when organizations have established IT and security practices that don't align well with RMF requirements. Forcing artificial alignment between existing processes and RMF can create inefficiencies and resistance.
Successful integration strategies involve mapping existing processes to RMF requirements to identify gaps and overlaps, modifying existing processes gradually rather than replacing them wholesale, and ensuring that RMF implementation enhances rather than duplicates existing risk management activities.
Stakeholder Buy-in and change management become critical when RMF implementation requires significant changes to established practices. Without strong leadership support and clear communication about benefits, implementation efforts often stall or fail to achieve desired outcomes.
Change management best practices include securing executive sponsorship early in implementation, communicating benefits clearly to all stakeholder groups, providing adequate training and support during transitions, and celebrating early wins to build momentum for broader implementation.
NIST RMF vs. Other Risk Management Approaches
Understanding how the NIST Risk Management Framework compares to other risk management approaches helps organizations make informed decisions about which methodologies best fit their needs and circumstances.
NIST RMF vs. ISO 27001 presents an interesting comparison between American and international approaches to information security management. ISO 27001 focuses on establishing, implementing, maintaining, and improving information security management systems, while NIST RMF provides a more detailed process for managing security risks throughout system lifecycles.
The key differences lie in scope and approach. ISO 27001 takes an organizational view of information security management, emphasizing policy, procedures, and management systems. NIST RMF focuses more specifically on system-level risk management with detailed technical guidance for security control implementation and assessment.
Many organizations successfully combine elements from both approaches, using ISO 27001 for overarching security management and NIST RMF for detailed system-level risk management processes.
NIST RMF vs. NIST Cybersecurity Framework often creates confusion because both frameworks come from the same organization and address cybersecurity risks. However, they serve different purposes and operate at different levels of detail.
The NIST Cybersecurity Framework provides a high-level, outcomes-based approach to cybersecurity program management organized around five core functions: Identify, Protect, Detect, Respond, and Recover. It's designed to be flexible and applicable across all industries and organization sizes.
NIST RMF provides much more detailed, prescriptive guidance for managing information security risks throughout system lifecycles. It's particularly valuable for organizations that need rigorous, systematic approaches to security control implementation and assessment.
NIST RMF vs. COBIT represents a comparison between security-focused and IT governance-focused frameworks. COBIT provides comprehensive guidance for IT governance and management, including information security as one component of broader IT risk management.
NIST RMF focuses specifically on information security and privacy risks with detailed technical guidance, while COBIT addresses broader IT governance concerns including strategic alignment, value delivery, resource management, and performance measurement.
Getting Started with NIST RMF Implementation
Beginning a NIST Risk Management Framework implementation requires careful planning and realistic expectations about timelines and resource requirements. Successful implementations typically follow proven approaches that build momentum through early wins while establishing foundations for long-term success.
Assessment and Planning should be your first step. Conduct honest evaluations of your current security practices, available resources, and organizational readiness for RMF implementation. This assessment should identify existing processes that align with RMF requirements, gaps that need addressing, and potential obstacles to implementation.
Start by reviewing your current system inventories, security documentation, and risk management processes. Identify which systems would benefit most from RMF implementation and which might serve as good pilot candidates. Consider factors like system criticality, existing documentation quality, stakeholder support, and resource availability when making these decisions.
Building Organizational Support becomes critical for long-term implementation success. Secure executive sponsorship early and maintain regular communication about implementation progress and benefits. Identify champions within different organizational functions who can support implementation efforts and help address resistance or obstacles.
Develop clear communication strategies that articulate RMF benefits in terms that resonate with different stakeholder groups. Technical teams need to understand how RMF improves security effectiveness, while business stakeholders need to see connections to business risk reduction and regulatory compliance.
Pilot Implementation Approach allows organizations to build expertise and demonstrate value before committing to enterprise-wide implementations. Select pilot systems carefully, choosing ones that are important enough to demonstrate value but not so critical that implementation problems could cause significant business disruption.
Use pilot implementations to develop documentation templates, establish workflows, identify needed tools and resources, and train staff on RMF processes. Document lessons learned and best practices that can be applied to broader implementation efforts.
Tool Selection and Process Development support scalable implementation efforts. Evaluate available governance, risk, and compliance (GRC) tools that can automate RMF documentation and workflow requirements. While tools aren't required for RMF implementation, they can significantly reduce administrative overhead and improve process consistency.
Develop standardized processes and procedures that can be applied consistently across different systems and implementation teams. Focus on creating efficient workflows that minimize duplicated effort while maintaining thorough documentation and assessment practices.
Training and Capability Development ensure your organization has the expertise needed for successful implementation. Invest in training for key personnel on RMF concepts, processes, and tools. Consider both formal training programs and hands-on learning through pilot implementations.
Build internal communities of practice that can share experiences, solve common problems, and maintain expertise as implementation progresses. External partnerships with consultants or other organizations implementing RMF can provide valuable learning opportunities and support.
Advanced NIST RMF Topics
As organizations mature in their NIST Risk Management Framework implementations, several advanced topics become relevant for optimizing effectiveness and addressing complex environments.
Continuous Monitoring and Automation represent the next evolution of RMF implementation. Traditional approaches to continuous monitoring often rely heavily on manual processes that don't scale well in dynamic environments. Advanced implementations leverage automated tools and processes to maintain real-time awareness of security control effectiveness.
Modern continuous monitoring approaches integrate multiple data sources including vulnerability scanners, security information and event management (SIEM) systems, configuration management databases, and threat intelligence feeds. Machine learning and artificial intelligence technologies can help analyze this data to identify meaningful changes in risk posture and recommend appropriate responses.
Cloud and Hybrid Environment Considerations require adaptations to traditional RMF approaches. Cloud service models introduce shared responsibility considerations where traditional control implementations may not be feasible or appropriate. Organizations must adapt RMF processes to address inherited controls from cloud providers while maintaining appropriate oversight and governance.
Hybrid environments that combine on-premises and cloud components create additional complexity for system boundary definitions, control implementation, and assessment approaches. Advanced RMF practitioners develop specialized approaches for managing risks in these complex environments.
Supply Chain Risk Management Integration becomes increasingly important as organizations rely more heavily on third-party products and services. NIST has enhanced RMF guidance to address supply chain risks more comprehensively, but implementation requires careful attention to vendor management, product evaluation, and ongoing monitoring processes.
Advanced organizations integrate supply chain risk considerations into all RMF steps, from initial system categorization through ongoing monitoring. This integration requires close coordination between procurement, risk management, and security teams.
Risk-Based Security Control Tailoring allows mature organizations to optimize their security investments by customizing control implementations based on specific threat environments and business requirements. This advanced approach requires deep understanding of both security controls and organizational risk contexts.
Effective tailoring balances security effectiveness with operational efficiency, ensuring that control implementations provide maximum risk reduction while minimizing negative impacts on business operations.
Future of NIST Risk Management Framework
The NIST Risk Management Framework continues evolving to address emerging technologies, changing threat landscapes, and lessons learned from widespread implementation across diverse organizations and sectors.
Emerging Technology Integration represents a key area of ongoing development. Technologies like artificial intelligence, machine learning, Internet of Things devices, and quantum computing introduce new categories of risks that may require enhanced RMF approaches. NIST continues developing guidance for applying RMF principles to these emerging technology areas.
Enhanced Automation and Intelligence will likely characterize future RMF implementations. Automated control assessment, intelligent risk analysis, and predictive security analytics are becoming more sophisticated and accessible. Future versions of RMF guidance will likely provide more detailed recommendations for leveraging these advanced technologies.
International Harmonization efforts continue as organizations operating globally seek consistency between different national and international risk management standards. NIST collaborates with international standards bodies to identify opportunities for harmonization while maintaining the framework's effectiveness and flexibility.
Industry-Specific Adaptations may emerge as different sectors develop specialized approaches to implementing RMF in their unique operating environments. Healthcare, financial services, critical infrastructure, and other sectors have specific requirements that may benefit from tailored guidance.
Conclusion
The NIST Risk Management Framework stands as one of the most comprehensive and practical approaches available for managing information security and privacy risks in today's complex threat environment. While implementation requires significant commitment and resources, the benefits, enhanced security, improved compliance, better risk visibility, and more effective resource allocation, make the investment worthwhile for most organizations.
Success with NIST RMF doesn't happen overnight, and it doesn't require perfect implementation from day one. The most successful organizations approach RMF implementation as a journey of continuous improvement, starting with solid foundations and gradually building more sophisticated capabilities over time.
Whether you're just beginning to explore risk management frameworks or looking to enhance existing security programs, the NIST Risk Management Framework provides battle-tested approaches that can adapt to your organization's unique needs and circumstances. The key is getting started with realistic expectations, adequate resources, and commitment to long-term success.
In our increasingly connected and threat-rich digital world, systematic approaches to risk management aren't just best practices - they're business necessities. The NIST Risk Management Framework provides the roadmap for building security programs that protect what matters most while enabling the innovation and growth that drive organizational success.
Simplify compliance with Regulance. Leverage the NIST Risk Management Framework to confidently implement RMF in 2025 and protect your business against evolving risks. Start building a resilient compliance strategy today.