NIST 800-53: The Ultimate Cybersecurity Framework Every Business Needs to Know


Introduction
NIST SP 800-53 is the gold standard for building secure, compliant information systems. This widely adopted framework maps out comprehensive security and privacy controls, covering access management, incident response, encryption, continuous monitoring, and more to help organizations reduce risk and meet regulatory requirements. Whether you’re aiming for FedRAMP, FISMA, or strengthening your cybersecurity posture, NIST 800-53 offers a clear, scalable roadmap you can tailor to your environment. In this guide, we break down core control families, implementation tips, and best practices so you can accelerate compliance and protect sensitive data with confidence.
What Is NIST 800-53?
NIST Special Publication 800-53, officially titled "Security and Privacy Controls for Federal Information Systems and Organizations," is a comprehensive cybersecurity framework developed by the National Institute of Standards and Technology. Think of it as your organization's security blueprint – a detailed roadmap containing over 1,000 security and privacy controls designed to protect information systems from the ground up.

Originally created for federal agencies, this framework has become the go-to standard for organizations across industries who take their cybersecurity seriously. It's not just another compliance checkbox; it's a living, breathing system that adapts to emerging threats while maintaining rock-solid fundamentals.
Why Your Business Can't Afford to Ignore NIST 800-53
The statistics are sobering: the average cost of a data breach in 2024 reached $4.88 million, with small businesses often unable to recover from major incidents. Here's why NIST 800-53 is essential for your business survival:
Regulatory Compliance Made Simple
If you work with federal agencies, handle sensitive data, or operate in regulated industries like healthcare or finance, NIST 800-53 compliance isn't optional. It's often a requirement for contracts, certifications, and maintaining customer trust. The framework aligns with major regulations including FISMA, HIPAA, and SOX, making compliance management significantly easier.
Risk Management That Actually Works
Unlike generic security checklists, NIST 800-53 uses a risk-based approach. You're not implementing controls because someone said so, you're strategically addressing your organization's specific vulnerabilities and threats. This targeted approach maximizes security investment while minimizing operational disruption.
Competitive Advantage in the Marketplace
Organizations with robust cybersecurity frameworks win more business. Period. When clients see NIST 800-53 implementation on your credentials, they know you're serious about protecting their data. It's become a differentiator that can make or break contract negotiations.
Future-Proofing Your Security Posture
Cyber threats don't stand still, and neither does NIST 800-53. The framework receives regular updates to address emerging threats, new technologies, and evolving attack vectors. By adopting this framework, you're not just solving today's problems – you're preparing for tomorrow's challenges.
How to Achieve NIST 800-53 Compliance: A Strategic Roadmap
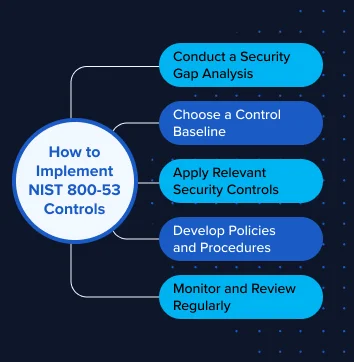
Implementing NIST 800-53 might seem overwhelming, but breaking it down into manageable phases makes the process achievable for organizations of any size.
Phase 1: Assessment and Planning (Months 1-2)
Start by conducting a comprehensive security assessment to understand your current posture. Map your existing controls against NIST 800-53 requirements to identify gaps. This baseline assessment becomes your implementation roadmap, helping you prioritize high-impact, low-effort improvements first.
Create a cross-functional team including IT, security, compliance, and business stakeholders. NIST 800-53 implementation isn't just a technical project – it requires organizational buy-in and cultural change.
Phase 2: Control Selection and Tailoring (Months 2-3)
NIST 800-53 includes three impact levels: Low, Moderate, and High. Determine which level applies to your organization based on the sensitivity of your data and systems. Most commercial organizations start with Moderate impact controls, which provide robust protection without excessive overhead.
Tailor the controls to your specific environment. The beauty of NIST 800-53 lies in its flexibility, you can adjust controls based on your organization's size, industry, and risk tolerance while maintaining the framework's integrity.
Phase 3: Implementation and Documentation (Months 3-12)
Begin implementing controls systematically, starting with foundational elements like access management, system hardening, and incident response procedures. Document everything meticulously – proper documentation is often required for compliance verification.
Focus on automation wherever possible. Modern security tools can help implement and monitor many NIST controls automatically, reducing manual overhead and improving consistency.
Phase 4: Monitoring and Continuous Improvement (Ongoing)
NIST 800-53 compliance isn't a destination – it's an ongoing journey. Establish continuous monitoring processes to ensure controls remain effective as your environment evolves. Regular assessments help identify drift and maintain compliance over time.
The Business Case: Return On Investment (ROI) That Makes Sense
Implementing NIST 800-53 requires investment, but the returns are substantial and measurable:
Direct Cost Savings: Organizations with mature cybersecurity frameworks experience 58% fewer security incidents and recover from breaches 200 days faster than those without frameworks.
Revenue Growth: Companies with strong security postures win 23% more new business opportunities, particularly in sectors where security is a primary concern.
Insurance Benefits: Many cyber insurance providers offer premium discounts of 10-25% for organizations with documented security frameworks like NIST 800-53.
Operational Efficiency: Standardized security processes reduce manual effort, minimize human error, and free up IT resources for strategic initiatives.
Common Implementation Challenges And How to Overcome Them
Resource Constraints: Start small and build momentum. Implement high-impact controls first to demonstrate value and secure additional resources.
Cultural Resistance: Frame security as business enablement, not restriction. Show how proper controls actually improve operational efficiency and reduce friction.
Technical Complexity: Partner with experienced consultants or managed security providers who understand NIST 800-53 implementation. Their expertise can accelerate your timeline and avoid common pitfalls.
Documentation Overhead: Invest in tools that automate documentation and evidence collection. The initial setup pays dividends during audits and assessments.
Conclusion
Success with NIST 800-53 comes down to treating it as a business strategy, not just a compliance exercise. Organizations that view the framework as an investment in their future, rather than a cost center, consistently achieve better outcomes.
The cybersecurity landscape will continue evolving, but the fundamental principles underlying NIST 800-53 defense in depth, continuous monitoring, risk-based decision making remain timeless. By implementing this framework today, you're not just protecting your organization; you're positioning it for sustainable growth in an increasingly digital world.
Ready to transform your cybersecurity posture? NIST 800-53 provides the roadmap – all you need to do is take the first step.
Don't let compliance gaps put your business at risk. Schedule a compliance assessment today with Regulance and protect your organization from costly penalties.