ISO 27001 Compliance Requirements: Your Complete Guide to Information Security Success


Introduction
ISO 27001 is the international standard that defines how organizations should manage and protect their information assets. Think of it as a comprehensive blueprint for building an impenetrable fortress around your most valuable data. Whether you're a startup handling customer emails or a multinational corporation managing millions of records, ISO 27001 provides the roadmap to information security excellence.
What makes ISO 27001 particularly powerful is its risk-based approach. Rather than applying a one-size-fits-all security blanket, the standard requires organizations to identify their unique risks and implement appropriate safeguards. This means a small accounting firm and a multinational tech company will have different compliance paths, but both will achieve robust security tailored to their specific needs.
Why ISO 27001 Compliance Matters More Than Ever

In today's digital landscape, data breaches cost companies an average of $4.45 million per incident. ISO 27001 compliance isn't just about checking boxes - it's about building trust, reducing risk, and creating competitive advantage. Organizations with ISO 27001 certification demonstrate to customers, partners, and regulators that they take information security seriously.
The Business Benefits That Drive Success
Enhanced Customer Trust: When prospects see your ISO 27001 certification, they know their sensitive information is in safe hands. This trust translates directly into increased sales and customer retention.
Competitive Advantage: Many RFPs now require ISO 27001 compliance. Certification opens doors to lucrative contracts and partnerships that would otherwise remain closed.
Regulatory Alignment: ISO 27001 helps organizations meet requirements under GDPR, HIPAA, SOX, and other regulatory frameworks, reducing compliance complexity and costs.
Risk Reduction: Systematic risk management processes help prevent costly security incidents and business disruptions.
Core ISO 27001 Compliance Requirements: The Essential Framework
1. Information Security Management System (ISMS)
The heart of ISO 27001 compliance lies in establishing a robust ISMS. This isn't just documentation - it's a living, breathing system that continuously monitors and improves your security posture.
Leadership and Governance: Top management must demonstrate commitment through policy establishment, resource allocation, and regular review of security objectives. This includes appointing competent personnel and ensuring information security considerations are integrated into business processes.
Risk Management Process: Organizations must identify information assets, assess threats and vulnerabilities, evaluate risks, and implement appropriate controls. This systematic approach ensures no critical assets fall through the cracks.
Performance Monitoring: Regular internal audits, management reviews, and performance measurements ensure the ISMS remains effective and aligned with business objectives.
2. The 93 Security Controls: Your Defense Arsenal
ISO 27001 Annex A outlines 93 security controls across four categories. While not all controls apply to every organization, understanding these categories is crucial for comprehensive protection.
Organizational Controls (37 controls): These establish the governance foundation, including security policies, incident response procedures, supplier relationship security, and information security in project management.
People Controls (8 controls): Focus on human factors, covering background verification, terms and conditions of employment, disciplinary processes, and remote working guidelines.
Physical and Environmental Controls (14 controls): Protect physical assets through secure areas, equipment protection, secure disposal, and clear desk policies.
Technological Controls (34 controls): Address technical security measures including access control management, cryptography, systems security, network security, and application security.
3. Documentation Requirements: Building Your Evidence Base
Effective documentation proves compliance and guides consistent implementation. ISO 27001 requires specific documented information, including:
Policy Framework: Information security policy, risk management procedures, and control implementation guidance must be clearly documented and accessible to relevant personnel.
Risk Assessment Records: Comprehensive documentation of risk identification, analysis, evaluation, and treatment decisions provides the foundation for control selection.
Training and Awareness Materials: Evidence of security awareness programs and competency development ensures personnel understand their responsibilities.
Incident Response Procedures: Detailed procedures for detecting, reporting, and responding to security incidents minimize impact and ensure consistent handling.
Step-by-Step Implementation: Your Path to Certification
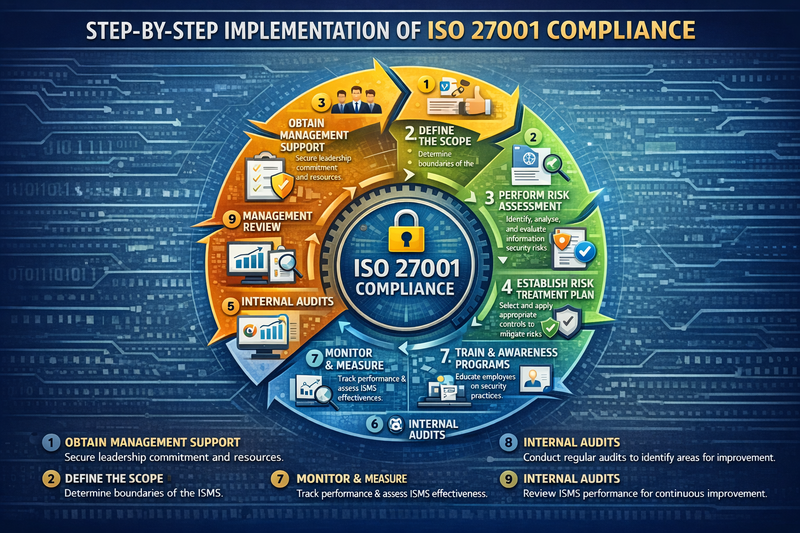
Phase 1: Foundation Building (Months 1-3)
Management Commitment: Secure visible leadership support through executive sponsorship, budget allocation, and policy approval. This commitment must be communicated throughout the organization.
Scope Definition: Clearly define what information assets, processes, and locations are included in your ISMS. A well-defined scope ensures focused efforts and clear certification boundaries.
Gap Analysis: Compare current security practices against ISO 27001 requirements to identify improvement areas and resource needs.
Phase 2: Implementation (Months 4-8)
Risk Assessment: Conduct comprehensive risk assessments using standardized methodologies. Document all identified risks, their potential impact, and likelihood of occurrence.
Control Implementation: Deploy selected controls based on risk assessment results and business requirements. Prioritize high-risk areas and critical business processes.
Training and Awareness: Develop comprehensive security awareness programs ensuring all personnel understand their roles in maintaining information security.
Phase 3: Testing and Refinement (Months 9-10)
Internal Audits: Conduct thorough internal audits to identify non-conformities and improvement opportunities. Use qualified internal auditors or external consultants.
Management Review: Hold formal management reviews to evaluate ISMS performance, review audit results, and approve corrective actions.
Continuous Improvement: Implement corrective actions and process improvements based on audit findings and performance monitoring results.
Phase 4: Certification (Months 11-12)
Stage 1 Audit: External certification body reviews documentation and readiness for full assessment. Address any identified issues promptly.
Stage 2 Audit: Comprehensive on-site assessment evaluating ISMS implementation and effectiveness. Demonstrate control operation and evidence gathering.
Certificate Issuance: Upon successful completion, receive your ISO 27001 certificate valid for three years with annual surveillance audits.
Common Implementation Challenges and Solutions
Resource Constraints
Many organizations struggle with limited budgets and personnel for ISO 27001 implementation. Address this by phasing implementation, leveraging existing security investments, and demonstrating ROI through risk reduction and business opportunities.
Technical Complexity
Complex technical requirements can overwhelm teams lacking specialized expertise. Consider engaging qualified consultants for technical assessments and control implementation while building internal capabilities.
Cultural Resistance
Security requirements sometimes conflict with operational convenience, creating resistance. Overcome this through clear communication of benefits, user-friendly procedures, and visible management support.
Documentation Overhead
Extensive documentation requirements can seem burdensome. Streamline by integrating with existing processes, using templates and automation tools, and focusing on practical, usable documentation.
Maintaining Compliance: Beyond Initial Certification
ISO 27001 compliance is an ongoing journey requiring continuous attention and improvement. Annual surveillance audits ensure continued compliance, while three-yearly recertification audits provide comprehensive reassessment.
Continuous Monitoring: Implement continuous monitoring processes for security controls, performance indicators, and emerging threats. Regular assessments identify degradation before it becomes problematic.
Change Management: Ensure all organizational changes are evaluated for security impact. New technologies, processes, and personnel changes can affect ISMS effectiveness.
Threat Intelligence: Stay informed about emerging threats, vulnerabilities, and attack techniques. Update risk assessments and controls based on evolving threat landscape.
Performance Measurement: Establish meaningful metrics for ISMS performance including incident response times, control effectiveness, and stakeholder satisfaction.
The Future of ISO 27001
The information security landscape continues evolving with cloud computing, artificial intelligence, and Internet of Things creating new challenges. ISO 27001's risk-based approach ensures organizations can adapt to emerging threats while maintaining certification.
Recent updates to ISO 27001:2022 reflect these changes with enhanced focus on cloud security, privacy protection, and supply chain security. Organizations maintaining current compliance benefit from these updates through improved security posture and stakeholder confidence.
Conclusion
ISO 27001 compliance represents a significant investment in your organization's security posture and business reputation. Begin with management commitment and scope definition, then systematically work through risk assessment and control implementation.
Consider engaging experienced consultants for initial guidance while building internal capabilities for long-term success. Remember that ISO 27001 compliance is not a destination but a continuous journey toward information security excellence.
The benefits of ISO 27001 compliance - enhanced trust, competitive advantage, risk reduction, and regulatory alignment—far outweigh the implementation costs. Organizations that embrace this standard position themselves for sustained success in an increasingly security-conscious marketplace.
Start your ISO 27001 journey today and join the ranks of organizations worldwide that have made information security a cornerstone of their business strategy.
Regulance uses AI to automate compliance and helps you to get things done properly and faster. Ready to get started? Contact us today.