Is Your Business SOC 2 Compliant in 2026? A Complete, Practical Checklist


Introduction
The modern business landscape has fundamentally changed. Enterprise clients now refuse to sign contracts without verified proof of data security, and that proof comes in one form: SOC 2 compliance. What started as a voluntary framework for tech companies has become the universal language of trust in the digital economy.
SOC 2 represents a comprehensive evaluation of how your organization protects customer data, demonstrating to the world that you've implemented rigorous security controls and actually maintain them over time. For SaaS companies, cloud service providers, and any business handling sensitive information, SOC 2 has evolved from a competitive differentiator into an absolute requirement for survival.
The numbers tell a compelling story. Companies without SOC 2 certification lose an estimated 40-60% of enterprise deals before conversations even begin. Procurement teams worldwide have standardized their vendor requirements, and SOC 2 consistently appears at the top of the list. Meanwhile, data breaches continue making headlines, costing companies millions in damages while destroying years of reputation-building in a single incident.
This article cuts through the complexity surrounding SOC 2 compliance. You'll discover exactly what SOC 2 entails, why it matters more in 2026 than ever before, and the precise steps required to achieve certification. If you're exploring SOC 2 for the first time or preparing for your next audit, this checklist provides the roadmap you need to transform compliance from an obstacle into a strategic advantage that accelerates growth and protects your business.
What is SOC 2?
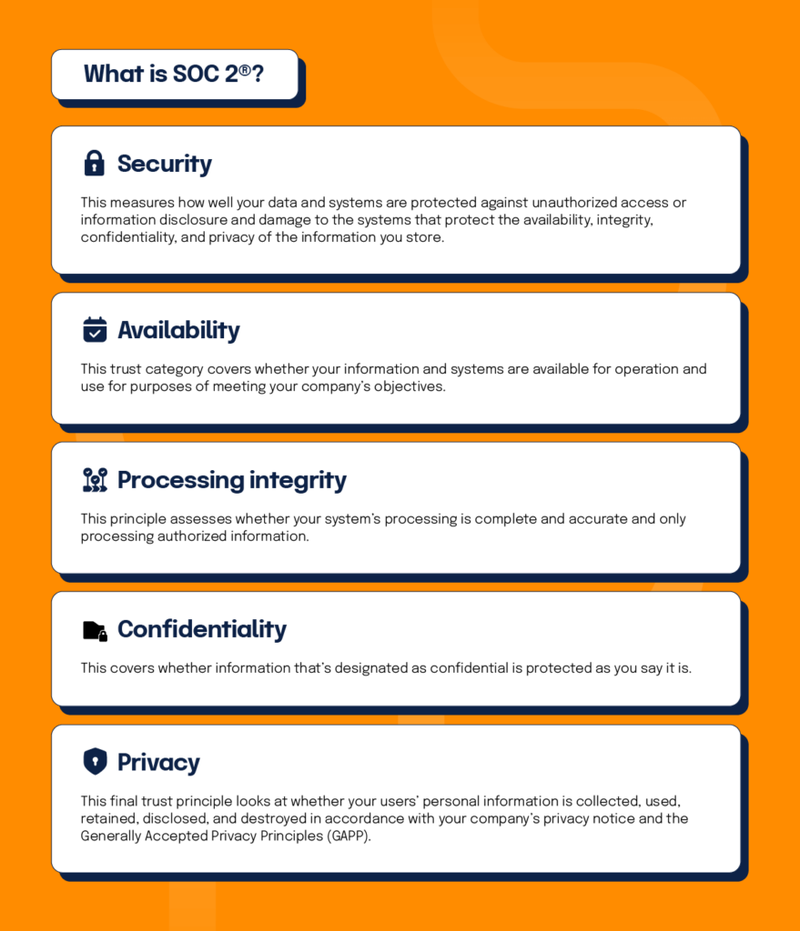
SOC 2, which stands for Service Organization Control 2, is an auditing framework developed by the American Institute of Certified Public Accountants (AICPA). Unlike its predecessor SOC 1, which focuses primarily on financial controls, SOC 2 zeroes in on how organizations manage and protect customer data based on five Trust Services Criteria: Security, Availability, Processing Integrity, Confidentiality, and Privacy.
SOC 2 is a comprehensive health check for your data security practices. It's not a checkbox certification or a one-size-fits-all standard. Instead, it's a customizable framework that examines whether your company has appropriate controls in place to protect client information and whether those controls actually work as intended.
The framework operates on two levels: Type I and Type II. A SOC 2 Type I audit evaluates whether your security controls are designed appropriately at a specific point in time; essentially a snapshot of your security posture. Type II takes things further by assessing whether those controls operate effectively over a period of time, typically six to twelve months. Type II reports carry significantly more weight because they demonstrate sustained commitment to security rather than just good intentions.
Here's what makes SOC 2 unique: it's not prescriptive. Unlike ISO 27001 or HIPAA, SOC 2 doesn't dictate exactly which security measures you must implement. Instead, it requires you to establish controls that are relevant to your business model and demonstrate that these controls effectively mitigate risks. This flexibility means your SOC 2 report can be tailored to what your organization actually does, making it both more meaningful and more challenging to achieve.
The five Trust Services Criteria form the backbone of any SOC 2 audit. Security is mandatory for all audits and covers protection against unauthorized access. Availability ensures your systems are operational and usable as committed. Processing Integrity verifies that your systems process data completely, accurately, and in a timely manner. Confidentiality protects information designated as confidential, while Privacy addresses the collection, use, retention, and disposal of personal information. Your organization chooses which criteria beyond Security are relevant to your operations.
Why Does It Matter?
In 2026, SOC 2 matters because trust has become the ultimate currency in the digital economy. Every week brings news of another data breach, ransomware attack, or privacy violation. Customers are actively demanding proof that their data is protected. SOC 2 provides that proof in a language that procurement teams, legal departments, and C-suite executives universally understand.
The regulatory environment has intensified dramatically. With data protection laws like GDPR, CCPA, and numerous industry-specific regulations creating a complex compliance web, organizations need frameworks that demonstrate due diligence. SOC 2 serves as evidence that you're not just checking boxes but genuinely investing in robust data protection practices. When regulators come knocking or lawsuits arise from data incidents, having a clean SOC 2 report can be the difference between weathering the storm and facing catastrophic consequences.
Market dynamics have shifted too. Enterprise customers now routinely require SOC 2 reports before they'll even consider your product. This is table stakes. Without SOC 2 compliance, entire market segments become inaccessible. Your competitors who have achieved certification will win deals simply because they can provide the assurance that you cannot. In practical terms, lacking SOC 2 can cut your addressable market by 50% or more for B2B SaaS companies.
Beyond the defensive reasons, SOC 2 offers offensive advantages. It forces you to build a mature security program, which actually reduces your risk of experiencing a costly breach. The average data breach cost in 2026 exceeds $4.5 million, not counting reputational damage and customer churn. Implementing SOC 2 controls helps you avoid becoming a statistic. Additionally, the discipline of maintaining compliance creates operational efficiencies, better documentation, and clearer accountability across your organization.
Insurance companies have taken notice too. Cyber insurance premiums have skyrocketed, and many insurers now offer better rates or even require SOC 2 compliance for coverage. Your SOC 2 report demonstrates to insurers that you're a lower-risk client, potentially saving you tens of thousands annually on premiums while ensuring you can actually obtain coverage in an increasingly restricted market.
Why Your Business Needs It
Your business needs SOC 2 for three fundamental reasons: revenue growth, risk mitigation, and operational excellence. Let's break down each pillar.
From a revenue perspective, SOC 2 directly impacts your ability to close deals and expand upmarket. Enterprise sales cycles that once took months can be dramatically shortened when you can immediately provide a SOC 2 report. Procurement teams have security questionnaires with hundreds of questions; your SOC 2 report answers most of them in one document. This accelerates deals, reduces friction, and gives your sales team a powerful credibility tool. Companies consistently report that achieving SOC 2 opens doors to 30-50% larger contract values because enterprise clients view certification as a baseline requirement for trusting you with their data.
Partner ecosystems increasingly require SOC 2 as well. If you integrate with major platforms or want to be featured in enterprise marketplaces, SOC 2 often appears on the prerequisites list. Missing this certification means missing partnership opportunities that could multiply your reach and revenue. In 2026, the network effects of B2B software mean that being locked out of key ecosystems can stunt your growth trajectory significantly.
Risk mitigation is equally compelling. Data breaches can destroy companies. SOC 2 compliance forces you to implement controls around access management, encryption, monitoring, incident response, and vendor management that substantially reduce your breach risk. You're not just getting a certificate; you're building a security program that actually protects your business. The process identifies vulnerabilities you didn't know existed and creates accountability structures that ensure security doesn't deteriorate over time.
Legal and contractual obligations increasingly mandate SOC 2 or equivalent frameworks. If you process sensitive information for clients in healthcare, finance, or government sectors, your contracts likely include security requirements that SOC 2 directly addresses. Failing to maintain compliance can trigger breach of contract claims, penalty clauses, or contract terminations. Having SOC 2 in place protects you from these contractual risks and demonstrates to legal teams on both sides that you take your obligations seriously.
Operational excellence is the often-overlooked benefit. Going through SOC 2 forces you to document processes, clarify roles, implement monitoring systems, and create a culture of security awareness. These improvements make your organization more efficient, reduce errors, and create scalability. Companies that view SOC 2 purely as a compliance burden miss the opportunity to use it as a framework for building a better, more mature organization. The controls you implement for SOC 2 often surface operational inefficiencies that, once addressed, improve your bottom line beyond just enabling sales.
Finally, employee recruitment and retention benefit from SOC 2 compliance. Top engineering and security talent wants to work for companies that take security seriously and provide environments where they can do their best work. SOC 2 signals to potential hires that you're a professional organization with mature practices, making you more attractive in a competitive talent market.
Who Conducts SOC 2 Audits?
SOC 2 audits must be conducted by independent Certified Public Accountants (CPAs) licensed in the United States who have specialized training in SOC 2 auditing. These are auditors who work for firms specializing in compliance and security assessments. The auditor's independence is crucial; they must be unbiased third parties with no vested interest in your company passing the audit.
Choosing the right auditor is one of your most important decisions in the SOC 2 process. Auditing firms range from Big Four accounting giants like Deloitte and PwC to specialized mid-sized firms and boutique practices focusing exclusively on SOC 2 and similar frameworks. Each tier offers different advantages. Big Four firms provide maximum brand recognition, which can impress the largest enterprise customers, but they typically charge premium rates and may assign junior staff to smaller clients. Mid-sized and boutique firms often provide more personalized service, deeper expertise in technology companies, and better value for growing businesses.
When evaluating auditors, look for firms with specific experience in your industry and company stage. An auditor familiar with SaaS businesses will understand your challenges better than one who primarily audits manufacturing companies. Ask for references from companies similar to yours in size and complexity. Inquire about their typical audit timelines, communication styles, and how they handle findings. The best auditors act as partners who help you understand requirements and build sustainable compliance programs, not just people who show up to find problems.
Beyond the external auditor, several internal stakeholders play critical roles in SOC 2 compliance. Your security team leads the charge, implementing controls and maintaining evidence. Engineering teams build and maintain the technical infrastructure that supports security controls. Human resources manages employee onboarding, training, and offboarding processes that are security-relevant. Legal and compliance teams ensure policies meet requirements. Operations teams handle vendor management and business continuity. Executive leadership provides sponsorship, resources, and tone-from-the-top commitment to security.
Many companies also engage compliance consultants or readiness assessors before their formal audit. These professionals conduct pre-audit assessments, identify gaps, recommend controls, and help you prepare evidence. While this adds cost, it dramatically increases your chances of passing on the first attempt and can actually save money by reducing audit time and avoiding failed audits. Consultants prove especially valuable for first-time SOC 2 candidates who lack internal expertise.
The relationship with your auditor extends beyond the formal audit period. Smart companies maintain regular communication with their auditors throughout the year, seeking guidance on new controls, changes to systems, or ambiguous situations. While auditors can't pre-approve specific implementations (that would compromise independence), they can provide general guidance that helps you stay on track.
5 Steps to Achieve a Successful SOC 2 Audit
Achieving SOC 2 certification requires methodical preparation and execution. Here's your roadmap broken into five comprehensive steps.
Step 1: Scoping and Planning (Weeks 1-4)
Your SOC 2 journey begins with defining exactly what the audit will cover. Scoping determines which systems, processes, and locations fall within your SOC 2 boundary. This entails auditing the systems and processes that are relevant to the services you provide to customers. Work with stakeholders across your organization to map out your technology stack, identify where customer data flows, and determine which Trust Services Criteria beyond Security apply to your business model.
Create a detailed system description document that explains your services, the infrastructure supporting them, security measures in place, and boundaries of the audit. This document becomes the foundation of your SOC 2 report. During scoping, also decide between Type I and Type II and establish your audit period. Most first-timers start with Type I to validate their control design, then proceed to Type II after operating those controls for the required period.
Assemble your compliance team and assign clear roles. Designate a SOC 2 program manager who owns the overall initiative. Identify control owners for each area, someone must be responsible for ensuring each control operates effectively. Establish a timeline with milestones, and most importantly, secure executive sponsorship and budget. SOC 2 isn't cheap; factor in auditor fees ($15,000-$75,000+ depending on scope and firm), consultant costs if applicable, tool investments, and significant internal time.
Step 2: Gap Assessment and Remediation (Weeks 5-16)
Once you understand what you're auditing, assess your current state against SOC 2 requirements. Conduct a thorough gap assessment comparing your existing controls to what SOC 2 demands. This involves reviewing policies, examining technical configurations, interviewing personnel, and testing whether controls actually work. Most organizations discover significant gaps, this is normal and expected.
Prioritize remediation based on risk and effort. Some gaps like missing policies can be resolved quickly by documentation. Others like implementing multi-factor authentication or encryption might require substantial engineering work. Create a remediation roadmap with owners, deadlines, and dependencies. Common gaps include incomplete access reviews, insufficient logging and monitoring, missing vendor management processes, inadequate incident response plans, and lack of formal risk assessments.
Implement missing controls systematically. For policies, develop a comprehensive information security policy suite covering access control, encryption, change management, incident response, vendor management, business continuity, and acceptable use. Ensure policies aren't just documents collecting dust; they must reflect actual practices. For technical controls, implement tools for security monitoring, access management, vulnerability scanning, and backup verification. For operational controls, establish processes for employee onboarding and offboarding, security training, access reviews, and management oversight.
Don't overlook evidence collection procedures. SOC 2 audits require extensive documentation proving your controls operated throughout the audit period. Set up systems now to automatically capture logs, track policy acknowledgments, document change management approvals, record security training completion, and maintain vendor security assessments. The companies that struggle most with SOC 2 have good controls but poor evidence collection.
Step 3: Implementing Controls and Collecting Evidence (Weeks 17-38 for Type II)
With gaps remediated, shift focus to consistent operation of controls and meticulous evidence collection. Type II audits typically require six to twelve months of evidence, so this phase takes time. For each control, ensure you understand what evidence the auditor expects and that you're capturing it appropriately.
Technical controls need automated evidence where possible. Configure your systems to retain logs showing who accessed what and when, changes to production environments, firewall rules and updates, vulnerability scan results, backup success confirmations, and monitoring alerts. Manual evidence like screenshots becomes outdated quickly and is harder to trust; automation provides more reliable proof.
Operational controls require different evidence. Maintain records of employee security training completion and dates, access review sign-offs by managers, vendor security assessments and due diligence, incident response activities and resolutions, management review meeting minutes, and policy updates and acknowledgments. Create templates and checklists so evidence collection becomes routine rather than chaotic scrambles before the audit.
Establish internal audit processes to verify controls work correctly. Monthly or quarterly, have someone independent of the control owner test whether the control operates as designed. This internal testing identifies problems early while there's time to fix them before the formal audit. Many companies discover during their formal audit that controls they thought were working had gaps, internal audits prevent these surprises.
Step 4: Formal Audit Execution (Weeks 39-46)
When your evidence collection period completes and you've verified all controls operate effectively, engage your auditor for the formal assessment. The audit typically begins with planning meetings where the auditor reviews your scope and system description, explains their methodology, and requests initial documentation. They'll want to see your policies, org charts, vendor lists, system architecture diagrams, and evidence catalogs.
The fieldwork phase involves the auditor testing your controls. They'll review evidence samples, interview personnel responsible for controls, observe processes in action, and test technical configurations. For a Type II audit, they'll examine evidence across the entire audit period looking for consistent operation. They're not just checking whether controls exist but whether they operate effectively throughout.
Be prepared for findings. Even well-prepared organizations receive observations or exceptions. Findings fall into categories: control deficiencies (controls aren't designed properly), exceptions (controls exist but didn't operate correctly in specific instances), and observations (suggestions that aren't quite problems but could improve your program). Respond to findings professionally with remediation plans and evidence that issues have been addressed.
The audit concludes with an exit meeting where the auditor presents preliminary findings and discusses the report structure. This is your opportunity to clarify any misunderstandings and provide additional context. After this meeting, the auditor drafts the final SOC 2 report.
Step 5: Receiving Your Report and Maintaining Compliance (Ongoing)
Your SOC 2 report arrives typically two to four weeks after fieldwork concludes. The report includes your system description, auditor's opinion on whether controls achieved the relevant Trust Services Criteria, detailed description of controls tested, and results of testing including any exceptions. An unqualified opinion means you passed; qualified opinions indicate significant issues.
Distribute your report strategically. SOC 2 reports contain sensitive details about your security practices, so they're confidential documents shared under NDA with prospects and customers who need them. Create a secure process for report sharing that tracks who received copies and when. Many companies use secure data rooms or compliance platforms that allow controlled access without distributing actual PDFs.
Understand that SOC 2 is an ongoing commitment. Your controls must continue operating effectively after the audit ends. Most companies pursue annual SOC 2 audits to maintain current reports, since reports over a year old lose credibility with customers. Maintaining compliance means continuing evidence collection, performing regular control testing, updating policies as your business evolves, managing new vendors appropriately, training new employees, and conducting annual risk assessments.
Build compliance into your culture. The companies that succeed with SOC 2 long-term treat it as part of their operational DNA rather than an annual fire drill. Assign ongoing ownership, integrate security into product development, automate wherever possible, and celebrate compliance milestones to keep your team engaged.
FAQs
How long does SOC 2 certification take?
SOC 2 Type I can be achieved in three to six months from start to finish if you're well-prepared. Type II requires an additional six to twelve months of operating your controls before the audit, meaning your total timeline runs nine to eighteen months for first-time Type II certification. Companies with mature security programs move faster; startups building programs from scratch need the longer timeline.
How much does SOC 2 cost?
Auditor fees range from $15,000 to $75,000+ depending on your company's complexity, scope, and chosen auditing firm. Beyond auditor costs, budget for consulting help ($20,000-$50,000 if needed), compliance and security tools ($5,000-$30,000 annually), and substantial internal time investment. All-in, first-time SOC 2 costs typically run $50,000-$150,000 for mid-sized SaaS companies when including both hard costs and internal effort.
What's the difference between SOC 2 Type I and Type II?
Type I audits assess whether your security controls are designed appropriately at a specific point in time, it's a snapshot. Type II evaluates whether those controls operated effectively over an extended period (usually six to twelve months). Type II reports carry more weight because they demonstrate sustained commitment to security, not just proper design. Most enterprise customers require Type II.
Do I need SOC 2 if I already have ISO 27001?
ISO 27001 and SOC 2 overlap significantly but aren't identical. ISO 27001 is an international standard focusing on information security management systems, while SOC 2 is US-centric and emphasizes the five Trust Services Criteria. Many US customers specifically require SOC 2 reports regardless of other certifications. However, if you have ISO 27001, achieving SOC 2 is easier since much of your security program already exists. Some companies maintain both certifications to address different market requirements.
Can small companies achieve SOC 2?
Absolutely. SOC 2 is achievable for companies of any size, including startups with lean teams. The key is scoping appropriately for your complexity and using automation and tools to make compliance manageable. Small companies often find SOC 2 easier in some ways because they have fewer systems and simpler processes to audit. Many compliance platforms and consultants specialize in helping smaller companies achieve SOC 2 efficiently.
How often do I need to renew SOC 2?
SOC 2 isn't technically renewed, instead, companies undergo annual audits to produce updated reports. Since reports become less relevant as they age, most organizations conduct audits annually to maintain current reports that customers will accept. The audit period for your second and subsequent reports typically picks up where your previous report ended, creating continuous coverage.
What happens if I fail a SOC 2 audit?
A failed audit means you receive a qualified opinion or the auditor declines to issue a report because your controls didn't meet the Trust Services Criteria. This isn't catastrophic, you can remediate the issues and undergo a new audit. However, it delays your timeline, costs additional auditor fees, and means you still can't provide a passing report to customers. This is why pre-audit readiness assessments and internal testing are crucial; they help you avoid failed audits by identifying problems before the formal audit begins.
Conclusion
SOC 2 compliance has transformed from a niche requirement into a fundamental business necessity for any company handling customer data in 2026. The stakes have never been higher; enterprises won't buy without it, partners won't integrate without it, and investors increasingly expect it. But beyond being a barrier to overcome, SOC 2 represents an opportunity to build a genuinely secure, well-managed organization that protects customer trust and operates with excellence.
The journey to SOC 2 certification demands commitment, resources, and discipline. It will expose weaknesses in your systems and processes that you didn't know existed. It will require cross-functional collaboration and cultural shifts around security. It will consume time and budget that could be spent on feature development or go-to-market activities. Yet companies that embrace this challenge consistently find that the benefits of accelerated sales, reduced risk, operational improvements, and competitive advantages far exceed the costs.
Success with SOC 2 comes down to treating it as a program rather than a project. One-time fire drills might get you through an initial audit, but sustainable compliance requires embedding security into your organizational DNA. Start early, engage experts when needed, automate relentlessly, and view compliance as an investment in your company's foundation rather than a tax on doing business.
The regulatory environment will only intensify, customer demands will grow more sophisticated, and the cost of security failures will continue climbing. Companies that achieve SOC 2 compliance now position themselves to thrive in this landscape, while those who delay increasingly find themselves locked out of market opportunities and vulnerable to risks they can't afford.
Your path forward begins with a single step; defining your scope, assessing your readiness, and committing to the journey. The checklist provided here gives you the roadmap. What happens next depends on your willingness to prioritize security, invest in the necessary controls, and maintain the discipline that SOC 2 demands.
Take the Next Step with Regulance. Contact Regulance today to schedule a consultation and discover how we can accelerate your path to SOC 2 certification while turning compliance into a competitive advantage. Your future customers are waiting, let's give them the assurance they need to choose you.