Information Governance or Information Security? Understanding the Key Differences for Better Compliance


Introduction
As companies navigate the complexities of our digital-first world, organizations generate, collect, and process unprecedented amounts of information daily. This data explosion has made two critical disciplines essential for business success: information governance and information security. While these terms are often used interchangeably or confused with one another, they serve distinct yet complementary roles in protecting and managing organizational information assets.
Understanding the difference between information governance and information security is a business imperative. Companies that fail to distinguish between these approaches often find themselves with gaps in their data strategy, leaving them vulnerable to compliance violations, security breaches, and operational inefficiencies. This comprehensive guide will demystify both concepts, explore their key differences, and demonstrate how they work together to create a robust information management framework.
What Is Information Governance?
Information governance is the strategic framework that defines how organizations create, capture, manage, use, and dispose of information throughout its entire lifecycle. It serves as the master blueprint that governs every aspect of how information flows through your organization,from the moment data is created until it's ultimately destroyed or archived.
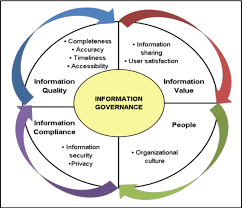
Information governance encompasses the policies, procedures, roles, and responsibilities that ensure information is managed as a valuable business asset. This discipline focuses on maximizing the value of information while minimizing associated risks and costs. It's about making sure the right people have access to the right information at the right time, while ensuring that information is accurate, complete, and appropriately protected.
Information governance operates on several key principles: First, it treats information as a strategic asset that requires active management rather than passive storage. Second, it emphasizes accountability by clearly defining who is responsible for different aspects of information management. Third, it promotes transparency by establishing clear policies and procedures that all stakeholders can understand and follow.
The scope of information governance is remarkably broad, covering everything from data quality and metadata management to records retention and privacy compliance. It includes structured data in databases as well as unstructured information like emails, documents, and multimedia files. This comprehensive approach ensures that all information, regardless of format or location, is properly managed throughout its lifecycle.
What Is Information Security?
Information security, often called InfoSec, is the practice of protecting information from unauthorized access, use, disclosure, disruption, modification, or destruction. While information governance focuses on managing information throughout its lifecycle, information security is laser-focused on protecting that information from threats, both internal and external.
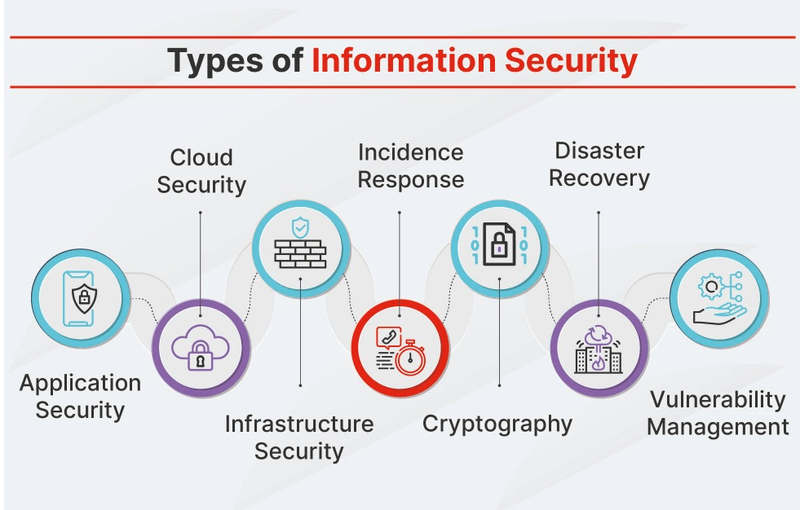
The primary objective of information security is to maintain the confidentiality, integrity, and availability of information commonly known as the CIA triad. Confidentiality ensures that sensitive information is only accessible to authorized individuals. Integrity guarantees that information remains accurate and unaltered except through authorized changes. Availability ensures that information and associated systems are accessible to authorized users when needed.
Information security employs a multi-layered approach to protection, often called defense in depth. This strategy includes technical controls like firewalls, encryption, and access management systems, as well as administrative controls such as security policies, user training, and incident response procedures. Physical controls, including secure facilities and device management, round out the comprehensive security framework.
The threat landscape that information security addresses is constantly evolving. Cybercriminals employ increasingly sophisticated techniques, from advanced persistent threats and ransomware to social engineering and insider threats. Information security professionals must stay ahead of these threats through continuous monitoring, threat intelligence, and adaptive security measures.
Risk assessment and management form the foundation of effective information security. This involves identifying potential threats, evaluating the likelihood and impact of security incidents, and implementing appropriate controls to mitigate risks to acceptable levels.
Key Differences Between Information Governance and Information Security
While information governance and information security both deal with organizational information, they approach it from fundamentally different perspectives. Understanding these distinctions is crucial for building effective information management strategies.
Scope and Focus
Information governance takes a holistic, lifecycle approach to information management. It's concerned with the entire journey of information within an organization, from creation to disposal. This includes questions like: What information do we have? Where is it stored? Who can access it? How long should we keep it? When should we delete it? Information governance professionals think strategically about information as a business asset.
Information security, conversely, has a narrower but deeper focus on protection. It concentrates specifically on safeguarding information from threats and ensuring that security controls are effective. Security professionals ask different questions: What are the threats to our information? How can we prevent unauthorized access? What happens if a breach occurs? How do we detect and respond to security incidents?
Objectives and Goals
The primary objective of information governance is to maximize the business value of information while minimizing associated risks and costs. This involves ensuring information quality, enabling efficient access and use, maintaining compliance with regulations, and optimizing storage and management costs. Governance seeks to turn information into a competitive advantage.
Information security's main goal is protection, ensuring that information remains confidential, maintains its integrity, and stays available to authorized users. Security professionals are primarily concerned with preventing, detecting, and responding to threats that could compromise information assets. Their success is often measured by the absence of security incidents rather than the presence of business value.
Timeframe and Perspective
Information governance operates with a long-term, strategic perspective. It involves creating policies and procedures that will guide information management for years to come. Governance decisions consider the entire information lifecycle and often require significant organizational change management.
Information security, while certainly having strategic elements, often operates with a more immediate, tactical focus. Security teams must respond quickly to emerging threats and vulnerabilities. While security strategy is important, much of the day-to-day work involves monitoring, incident response, and implementing immediate protective measures.
Stakeholders and Ownership
Information governance typically involves a broad range of stakeholders across the organization. Legal teams ensure regulatory compliance, IT manages technical infrastructure, business units provide requirements, and executive leadership provides strategic direction. The Chief Data Officer or Chief Information Officer often leads governance initiatives.
Information security is usually more centralized, often under the leadership of a Chief Information Security Officer (CISO) or security team. While security certainly involves stakeholders across the organization, the ownership and decision-making authority is typically more concentrated in specialized security roles.
Metrics and Success Criteria
Success in information governance is measured through metrics like data quality scores, compliance audit results, cost savings from improved information management, and user satisfaction with information access. These metrics often focus on efficiency, compliance, and business value.
Information security success is typically measured through different metrics: number of security incidents, mean time to detection and response, vulnerability assessment results, and compliance with security frameworks. These metrics focus on protection and risk reduction.
How Information Governance and Information Security Work Together
Despite their differences, information governance and information security are not competing disciplines; they're complementary approaches that work best when properly integrated. Their collaboration creates a comprehensive framework for managing and protecting organizational information assets.
Shared Foundation of Risk Management
Both disciplines are fundamentally concerned with managing risk, albeit from different angles. Information governance addresses risks related to compliance, data quality, and business continuity, while information security focuses on threats like cyberattacks and data breaches. When these risk management approaches are coordinated, organizations can develop more comprehensive and effective risk mitigation strategies.
A shared risk register that includes both governance and security risks enables better prioritization and resource allocation. For example, a governance risk related to unclear data retention policies might create security vulnerabilities if sensitive information is kept longer than necessary, increasing exposure in case of a breach.
Policy Integration and Alignment
Effective information management requires policies that address both governance and security concerns. Data classification schemes, for instance, serve both purposes by identifying sensitive information that requires special handling (governance) and stronger protection (security). Access control policies must balance business needs for information access (governance) with security requirements for protection.
When developing information policies, organizations benefit from involving both governance and security stakeholders. This ensures that policies are practical, comprehensive, and don't create conflicts between governance and security objectives. For example, data retention policies must consider both regulatory requirements (governance) and the security principle of minimizing data exposure.
Technology and Infrastructure Synergies
Many technology solutions serve both governance and security purposes. Data loss prevention (DLP) systems, for example, help enforce governance policies about appropriate information use while simultaneously providing security protection against data exfiltration. Identity and access management (IAM) systems support governance by ensuring proper information access controls while providing security through authentication and authorization.
Master data management and data catalog solutions provide governance benefits by improving data quality and discoverability, while also supporting security through better visibility into information assets and their sensitivity levels. When organizations coordinate their technology investments, they can achieve both governance and security objectives more efficiently.
Incident Response and Business Continuity
When information-related incidents occur, whether they're governance failures like compliance violations or security events like data breaches, response efforts benefit from coordination between both disciplines. Security teams bring expertise in threat analysis and technical remediation, while governance teams contribute knowledge of regulatory requirements and business impact assessment.
Business continuity planning must address both governance and security scenarios. A comprehensive plan considers not just how to recover from cyberattacks, but also how to maintain compliance during recovery and ensure that information governance processes continue to function during disruptions.
Compliance and Regulatory Alignment
Modern regulations increasingly address both governance and security requirements. The General Data Protection Regulation (GDPR), for example, includes governance requirements like data subject rights and retention limitations, as well as security requirements like breach notification and privacy by design. Organizations that coordinate their governance and security compliance efforts avoid duplication and ensure comprehensive regulatory adherence.
How Information Governance and Information Security Affect Compliance
In today's regulatory environment, compliance is a business imperative that can make the difference between success and catastrophic failure. Both information governance and information security play crucial roles in achieving and maintaining compliance, but they address different aspects of regulatory requirements.
Regulatory Landscape Overview
The modern regulatory landscape is complex and constantly evolving. Organizations must comply with industry-specific regulations like HIPAA in healthcare, PCI-DSS in payment processing, and SOX in financial reporting, as well as cross-industry regulations like GDPR for privacy and various data localization requirements. Each regulation includes both governance and security elements, making coordination between these disciplines essential for compliance success.
Regulatory requirements often overlap and sometimes conflict, creating additional complexity. For example, data retention requirements for legal purposes might conflict with privacy regulations that mandate data deletion. Organizations need integrated governance and security approaches to navigate these complexities effectively.
Governance's Role in Compliance
Information governance directly supports compliance through several key mechanisms. First, it establishes the policies and procedures necessary to meet regulatory requirements. This includes data retention schedules that ensure information is kept for required periods and deleted when permitted, data classification schemes that identify regulated information, and privacy procedures that protect individual rights.
Second, governance provides the accountability structures necessary for compliance. This includes defining roles and responsibilities for compliance activities, establishing oversight and audit procedures, and creating documentation that demonstrates compliance efforts. Many regulations require organizations to show not just that they're compliant, but that they have processes in place to maintain compliance over time.
Third, governance enables the transparency and reporting that regulators demand. This includes maintaining records of data processing activities, providing individuals with access to their personal information, and generating reports that demonstrate compliance with specific regulatory requirements.
Security's Contribution to Compliance
Information security supports compliance primarily through protective controls that prevent violations and limit the impact of incidents. Security measures like encryption, access controls, and monitoring systems help ensure that regulated information is protected according to regulatory standards.
Security incident response capabilities are particularly important for compliance. Many regulations require organizations to detect and report breaches within specific timeframes; GDPR requires breach notification within 72 hours, for example. Effective security monitoring and incident response procedures are essential for meeting these requirements.
Security also contributes to compliance through risk assessment and vulnerability management. Many regulations require organizations to regularly assess security risks and implement appropriate controls. Security professionals bring the technical expertise necessary to conduct these assessments and implement effective controls.
Coordinated Compliance Strategies
The most effective compliance programs integrate governance and security approaches. This starts with compliance risk assessment that considers both governance and security risks. For example, inadequate data retention practices (governance risk) might increase the likelihood of retaining information beyond regulatory limits, while weak access controls (security risk) might allow unauthorized individuals to access regulated information.
Coordinated compliance monitoring provides better visibility into compliance status. This might involve combining governance metrics like data retention compliance rates with security metrics like access review completion rates to provide a comprehensive view of regulatory compliance.
Integrated audit preparation ensures that organizations are ready to demonstrate compliance across all regulatory requirements. This involves coordinating between governance teams that maintain compliance documentation and security teams that can demonstrate the effectiveness of protective controls.
Emerging Compliance Challenges
Several emerging trends are making compliance even more challenging and increasing the need for coordinated governance and security approaches. Data sovereignty requirements are forcing organizations to carefully track where information is stored and processed, requiring both governance visibility and security controls.
Artificial intelligence and automated decision-making are creating new regulatory requirements that span both governance and security. Organizations must govern AI systems to ensure fairness and transparency while securing them against adversarial attacks and data poisoning.
The increasing use of cloud services and third-party providers is creating shared responsibility models for compliance. Organizations must coordinate governance and security approaches to ensure that compliance requirements are met across their entire technology ecosystem.
Conclusion
In the present information-centric business environment, the distinction between information governance and information security is both critical and nuanced. While information governance provides the strategic framework for managing information as a valuable business asset throughout its lifecycle, information security focuses on protecting that information from an ever-evolving landscape of threats. Both disciplines are essential, and their effectiveness is maximized when they work together in harmony.
The key to success lies in understanding that information governance and information security are not competing priorities but complementary approaches that strengthen each other. Governance provides the structure and policies that enable effective security implementation, while security provides the protective controls that ensure governance objectives can be achieved safely. Organizations that recognize this synergy and invest in coordinated approaches will find themselves better positioned to extract value from their information assets while managing associated risks.
Looking forward, the convergence of governance and security will only become more important. Emerging technologies like artificial intelligence, the continued expansion of cloud computing, and increasingly complex regulatory requirements all demand integrated approaches that leverage the strengths of both disciplines. The organizations that thrive will be those that break down silos between governance and security teams, creating unified strategies that address the full spectrum of information management challenges.
The investment in both information governance and information security is not just about compliance or risk mitigation, it's about creating sustainable competitive advantages through superior information management. In a world where information is often an organization's most valuable asset, the ability to govern it effectively while securing it comprehensively represents a fundamental business capability that will determine long-term success.
Need help balancing information governance and security? Our compliance experts are ready to design your perfect data protection strategy. Contact us now.