How Can SOC 2 Trust Service Criteria Help You Achieve Compliance Excellence in 2025?

Introduction
The foundation of every business relationship is trust. When companies entrust their sensitive data to third-party service providers, they need concrete assurance that their information will be protected. This is where SOC 2 compliance enters the picture as the gold standard for demonstrating security and operational excellence.
SOC 2 has become an essential credential for technology companies, SaaS providers, cloud service platforms, and any organization handling customer data. If you're a startup seeking your first enterprise client or an established company maintaining competitive advantage, understanding SOC 2 trust service criteria is crucial for success in 2025's compliance landscape.
This informative guide explores everything you need to know about SOC 2 trust service criteria, from foundational concepts to practical implementation strategies. We'll break down the five essential criteria, compare different SOC report types, and provide actionable insights to help your organization achieve and maintain compliance. This guide will help you understand what SOC 2 requires, why it matters and how to leverage it as a strategic business asset.
The Overview of SOC 2
What is SOC 2?
Service Organization Control 2 (SOC 2), is an auditing framework developed by the American Institute of Certified Public Accountants (AICPA). This voluntary compliance standard evaluates how effectively service organizations manage and protect customer data based on five trust service criteria: security, availability, processing integrity, confidentiality, and privacy.
Unlike many compliance frameworks that apply broadly across industries, SOC 2 specifically targets service providers; companies that store, process, or transmit customer data through cloud-based systems. The framework recognizes that traditional financial controls alone cannot adequately assess the risks associated with modern technology services. Instead, SOC 2 provides a comprehensive methodology for evaluating operational and security controls relevant to today's digital infrastructure.
What makes SOC 2 particularly valuable is its flexibility. Organizations can choose which of the five trust service criteria are relevant to their operations, allowing for customized compliance that reflects actual business practices rather than forcing a one-size-fits-all approach. However, the Security criterion is mandatory for all SOC 2 audits, as it forms the foundation for protecting any type of customer data.
SOC 2 reports come in two types. Type I reports evaluate whether an organization's controls are properly designed at a specific point in time, essentially providing a snapshot of compliance readiness. Type II reports, considered more rigorous and valuable, assess both the design and operating effectiveness of controls over a minimum period of six months, demonstrating sustained compliance rather than momentary achievement.
SOC 1 vs SOC 2 vs SOC 3
Understanding the differences between SOC 1, SOC 2, and SOC 3 reports is essential for selecting the appropriate audit framework for your organization. While these reports share the SOC designation and AICPA oversight, they serve distinctly different purposes and audiences.
SOC 1 focuses exclusively on controls relevant to financial reporting. This audit type is designed for service organizations whose systems impact their clients' financial statements. For example, a payroll processing company would pursue SOC 1 because errors in their service could directly affect their clients' financial reporting accuracy. SOC 1 reports follow the Statement on Standards for Attestation Engagements (SSAE) No. 18 and help client organizations meet their Sarbanes-Oxley compliance requirements. If your services don't directly impact client financial reporting, SOC 1 is not the appropriate framework.
SOC 2 addresses security and operational controls beyond financial reporting. This framework evaluates how service organizations protect the confidentiality, integrity, and availability of customer data and systems. SOC 2 is ideal for technology companies, SaaS providers, data centers, cloud storage providers, and any organization handling sensitive customer information. The report is detailed and technical, intended for sophisticated audiences who understand security controls and risk management. SOC 2 reports are typically shared under non-disclosure agreements with prospects, customers, and regulators who need detailed information about your security posture.
SOC 3 is essentially a summarized, public-facing version of a SOC 2 report. It confirms that an organization has completed a SOC 2 audit and met the relevant trust service criteria, but it doesn't include the detailed control descriptions and testing procedures found in SOC 2 reports. Organizations often display SOC 3 reports or trust seals on their websites as public proof of compliance, while reserving the detailed SOC 2 reports for serious prospects during the sales process. Think of SOC 3 as the marketing version and SOC 2 as the technical documentation.
Most technology service providers in 2025 pursue SOC 2 rather than SOC 1 because their services involve data security, system availability, and privacy concerns rather than direct financial reporting impacts. However, some organizations obtain both SOC 1 and SOC 2 reports if their services span both domains.
What is SOC 2 Trust Service Criteria?
SOC 2 trust service criteria represent the specific control objectives that organizations must address during their audit. These criteria provide the framework for evaluating whether service organizations have implemented appropriate controls to protect customer data and ensure reliable service delivery. Rather than prescribing specific technologies or implementations, the trust service criteria define what outcomes organizations must achieve, allowing flexibility in how they meet these objectives.
Instead of requiring organizations to implement a checklist of mandatory controls that may not fit their unique circumstances, SOC 2 allows auditors and organizations to determine the most appropriate controls based on the specific services provided and risks involved. This flexibility ensures that SOC 2 remains relevant across diverse industries and evolving technologies.
Each trust service criterion addresses a specific aspect of service delivery and data protection. Organizations select which criteria are relevant to their operations and customer commitments, though as mentioned earlier, Security is always required. This modularity means a cloud storage provider might address all five criteria, while a data analytics platform might focus on Security, Availability, and Confidentiality depending on their service model and customer needs.
The trust service criteria establish common points of focus that enable meaningful communication between service organizations and their customers. When a company states they've achieved SOC 2 compliance for Security and Availability, customers immediately understand the scope of controls that have been independently verified. This standardization reduces the burden of responding to countless custom security questionnaires and provides assurance through recognized, professionally audited standards.
In 2025, the trust service criteria continue evolving to address emerging technologies and threats. While the five core categories remain consistent, the AICPA regularly updates guidance on how organizations should address contemporary challenges like artificial intelligence, containerization, serverless architectures, and sophisticated cyber threats within the existing framework. This living approach ensures SOC 2 remains a relevant and rigorous standard for modern service organizations.
What Are the 5 AICPA Trust Service Criteria?
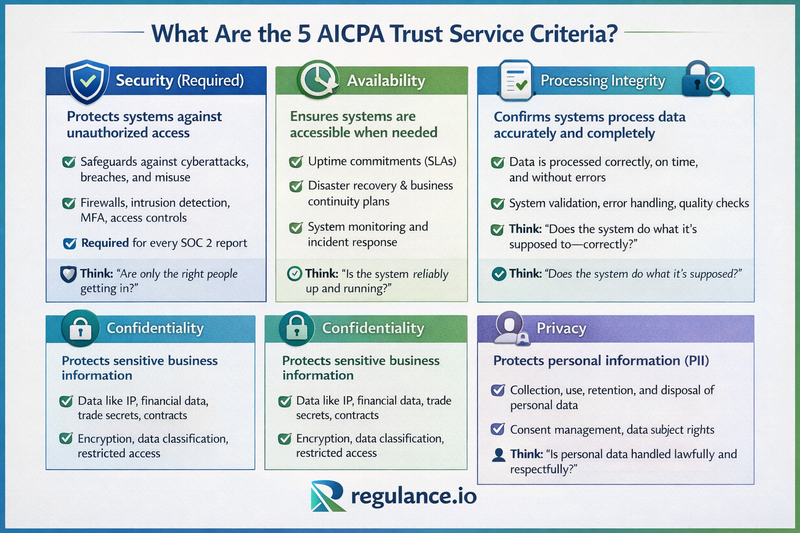
1. Security
Security forms the mandatory foundation of every SOC 2 audit. This criterion addresses how organizations protect their systems and data against unauthorized access, both physical and logical. Security encompasses everything from network defenses and access controls to vulnerability management and incident response capabilities.
The Security criterion requires organizations to implement controls across multiple domains. Logical access controls ensure that only authorized individuals can access systems and data appropriate to their roles. This includes robust authentication mechanisms, ideally incorporating multi-factor authentication for sensitive systems, regular access reviews to remove unnecessary permissions, and immediate deprovisioning when employees leave the organization.
Physical security controls protect the infrastructure supporting digital services. For organizations operating their own data centers, this means secure facilities with appropriate access restrictions, surveillance, and environmental controls. For those using cloud providers, this involves verifying that providers maintain appropriate physical security and understanding the shared responsibility model that defines which security controls you manage versus those your provider handles.
Change management processes ensure that system modifications don't inadvertently introduce security vulnerabilities. Organizations must document and test changes before implementation, maintain segregation of duties between development and production environments, and have rollback procedures for problematic updates. In 2025's fast-paced development environments, integrating security into DevOps practices (DevSecOps) has become essential for maintaining control while supporting rapid iteration.
Vulnerability management and threat detection round out the Security criterion. Organizations must regularly scan for vulnerabilities, prioritize remediation based on risk, and monitor systems for suspicious activity. Security information and event management (SIEM) tools, intrusion detection systems, and security operations centers have become standard components of comprehensive security programs for organizations pursuing SOC 2 compliance.
2. Availability
The Availability criterion addresses whether systems are operational and accessible as committed or agreed. In an era where downtime directly translates to lost revenue and damaged reputation, demonstrating robust availability controls has become critical for service organizations.
Availability controls begin with infrastructure redundancy and resilience. Organizations must architect systems to withstand component failures without service interruption. This includes redundant servers, network paths, power supplies, and data storage systems. Cloud-native architectures with auto-scaling capabilities and multi-region deployments have made high availability more accessible, but organizations must still properly design and test these capabilities.
Disaster recovery and business continuity planning form essential components of the Availability criterion. Organizations must document recovery procedures, identify recovery time objectives (RTO) and recovery point objectives (RPO) for critical systems, and regularly test their ability to restore services after disruptions. In 2025, these plans increasingly address not just traditional disasters but also ransomware attacks, supply chain disruptions, and other contemporary threats to availability.
Performance monitoring and capacity planning ensure systems can handle expected load and growth. Organizations must track resource utilization, identify bottlenecks before they impact users, and scale infrastructure proactively. Service level agreements (SLAs) with customers create specific availability commitments that auditors verify organizations can consistently meet.
Incident response procedures specifically for availability issues demonstrate how organizations detect, escalate, and resolve service disruptions. This includes defined on-call procedures, clear communication protocols for notifying affected customers, and post-incident reviews to prevent recurrence. The Availability criterion recognizes that some downtime is inevitable but evaluates whether organizations handle it professionally and learn from each incident.
3. Processing Integrity
Processing Integrity addresses whether systems process data completely, accurately, timely, and with proper authorization. This criterion is particularly relevant for organizations providing transaction processing, data transformation, or calculations that customers depend on for their own operations.
The Processing Integrity criterion requires organizations to implement controls ensuring data isn't corrupted, duplicated, or lost during processing. This includes input validation to reject malformed or unauthorized data, error handling to catch and appropriately manage processing failures, and reconciliation procedures to verify that outputs match expected results based on inputs.
Data validation controls prevent garbage-in-garbage-out scenarios. Organizations must define expected data formats, ranges, and relationships, then enforce these rules at system boundaries. In 2025's interconnected systems, API validation has become crucial as data increasingly flows between services through programmatic interfaces rather than human-mediated entry.
Processing controls ensure transformations and calculations produce correct results. This involves algorithm testing, output verification, and maintaining processing logs that create an audit trail. For financial calculations, scientific computations, or any processing where accuracy is critical, organizations must demonstrate not just that systems work as designed but that the designs themselves are correct and thoroughly validated.
Completeness controls verify that all transactions are processed and none are lost or duplicated. Sequence number tracking, reconciliation between source and destination systems, and exception reporting when discrepancies occur all contribute to processing integrity. Organizations must also address timing, ensuring that transactions are processed within expected timeframes and that processing delays don't cascade into broader system issues.
Authorization controls ensure processing occurs only for legitimate, approved requests. This ties back to Security controls but extends beyond system access to include business process authorization. For example, a payroll system must not only restrict access to authorized personnel but also ensure that individual payment requests have been properly approved before processing.
4. Confidentiality
Confidentiality focuses on protecting information designated as confidential from unauthorized disclosure. While Security addresses overall system protection, Confidentiality specifically deals with sensitive data that requires special handling beyond general security controls.
The Confidentiality criterion begins with data classification. Organizations must identify what information is considered confidential based on regulatory requirements, contractual obligations, or business needs. This includes customer proprietary information, trade secrets, personal data subject to privacy regulations, and any other sensitive information requiring special protection.
Encryption stands as a primary confidentiality control, both for data at rest and data in transit. In 2025, encryption is considered a baseline requirement rather than an advanced control. Organizations must encrypt confidential data stored in databases, file systems, and backups using strong cryptographic algorithms. Data transmitted over networks must use TLS or other encryption protocols to prevent interception.
Access restrictions for confidential data extend beyond general system access. Organizations implement need-to-know principles, ensuring that even authorized users can only access confidential information relevant to their specific responsibilities. This often involves data masking, role-based access controls, and compartmentalization of sensitive information.
Confidentiality controls also address data lifecycle management. Organizations must define retention periods for confidential data and securely dispose of information when no longer needed. This includes sanitizing or destroying storage media, securely deleting digital files, and ensuring backup systems don't indefinitely retain confidential information that should have been purged.
Non-disclosure agreements and confidentiality training ensure that personnel understand their obligations regarding confidential information. Organizations must train employees on handling sensitive data, obtain agreements acknowledging confidentiality responsibilities, and have procedures for investigating and responding to confidentiality breaches.
5. Privacy
The Privacy criterion addresses personal information collection, use, retention, disclosure, and disposal in conformity with the organization's privacy notice and applicable privacy regulations. While Confidentiality focuses on preventing unauthorized disclosure, Privacy addresses the broader lifecycle of personal information and individuals' rights over their data.
Privacy controls begin with transparent notice. Organizations must clearly communicate what personal information they collect, why they collect it, how they use it, with whom they share it, and how long they retain it. Privacy notices must be accessible, understandable, and updated when practices change. The trend in 2025 is toward just-in-time notices that inform individuals about data practices at the point of collection rather than buried in lengthy policies.
Choice and consent controls give individuals appropriate control over their personal information. This includes obtaining consent before collecting or using personal information in ways beyond original purposes, providing opt-out mechanisms for marketing communications, and respecting communication preferences. For sensitive data categories, organizations must obtain explicit opt-in consent rather than relying on pre-checked boxes or assumed consent.
Collection limitation principles require organizations to collect only personal information necessary for disclosed purposes. Organizations must justify each data element collected and avoid the temptation to gather information "just in case" it might be useful later. In 2025's privacy-conscious environment, data minimization has shifted from a best practice to an expectation.
Use, retention, and disposal controls ensure personal information is handled according to stated purposes and timeframes. Organizations must limit internal use to legitimate purposes, retain data only as long as necessary, and securely dispose of personal information when retention periods expire. This includes automated deletion workflows rather than relying on manual intervention to purge old data.
Individual rights management addresses requests from data subjects regarding their personal information. The Privacy criterion requires processes for handling access requests, correction requests, and deletion requests within appropriate timeframes. Organizations must verify requestor identity, search comprehensively across systems, and respond appropriately. The GDPR, CCPA, and similar regulations have made robust data subject request processes essential for any organization handling personal information.
FAQs
How long does it take to achieve SOC 2 compliance?
The timeline for SOC 2 compliance varies significantly based on your organization's current security maturity and the complexity of your systems. Organizations starting from scratch typically need 3-6 months to implement required controls before beginning the formal audit. The Type II audit itself requires a minimum 6-month observation period during which auditors evaluate whether controls operate effectively over time. From initial planning to receiving your Type II report, most organizations should expect 9-12 months for their first SOC 2 audit.
How much does SOC 2 compliance cost?
SOC 2 costs vary widely based on company size, system complexity, and the number of trust service criteria addressed. Audit fees typically range from $20,000 to $100,000+ for the formal examination. However, audit fees represent only part of the total investment. Organizations must also budget for control implementation, security tool acquisition, consulting services if needed, and internal staff time. First-time compliance efforts generally cost more than renewal audits as the foundational work is completed. Smaller organizations with simpler systems might achieve SOC 2 for $30,000-50,000 total, while enterprises with complex, distributed systems could invest $200,000 or more.
Do I need SOC 2 Type I or Type II?
Most customers and stakeholders prefer SOC 2 Type II reports because they demonstrate sustained compliance over time rather than just a point-in-time snapshot. Type II provides evidence that controls are not only properly designed but actually operated effectively for at least six months. While Type I reports can be useful as a stepping stone or proof of readiness before the Type II observation period completes, they carry significantly less weight in the market. Unless you have a specific reason to pursue Type I, plan for Type II from the beginning.
Can small companies achieve SOC 2 compliance?
Absolutely. SOC 2 is achievable for organizations of all sizes, though the specific controls implemented will vary based on company scale and resources. Small companies often leverage cloud infrastructure and managed services to meet SOC 2 requirements without building extensive in-house capabilities. The key is implementing controls appropriate to your environment rather than trying to match enterprise-level security programs. Many auditors and consultants specialize in helping startups and small businesses achieve their first SOC 2 certification efficiently.
How often must SOC 2 audits be renewed?
SOC 2 reports are typically valid for one year, after which organizations undergo renewal audits to maintain their compliance status. The renewal audit evaluates whether controls continued operating effectively during the new observation period. Some organizations choose to maintain continuous coverage by starting the next observation period before the previous report expires, ensuring they always have a current report available for customers and prospects.
What's the difference between SOC 2 and ISO 27001?
SOC 2 and ISO 27001 both address information security but differ in approach and recognition. SOC 2 is primarily used in North America and focuses specifically on service organizations, with flexible criteria selection. ISO 27001 is an international standard providing a comprehensive information security management system (ISMS) framework with broader applicability beyond service providers. ISO 27001 certification is often preferred for global businesses, particularly in Europe, while SOC 2 dominates in U.S. technology markets. Some organizations pursue both to satisfy different customer and regional requirements.
What happens if you fail a SOC 2 audit?
SOC 2 audits don't technically result in pass/fail determinations. Instead, auditors issue opinions ranging from unqualified (clean) to qualified (controls have exceptions) or adverse (controls are insufficient). If significant issues are identified, auditors will document them in the report. Organizations can remediate identified issues and undergo re-examination. Most auditors work collaboratively with clients during readiness assessments to identify and fix problems before the formal audit begins, minimizing the risk of unfavorable opinions.
Conclusion
SOC 2 trust service criteria provide a comprehensive framework for building security, reliability, and trust into the core of your service organization. In 2025's competitive landscape, where data breaches make headlines daily and customers demand transparency about how their information is protected, SOC 2 compliance has evolved from a competitive differentiator into a fundamental business requirement.
Understanding the five trust service criteria; Security, Availability, Processing Integrity, Confidentiality, and Privacy empowers organizations to build robust control environments that not only satisfy auditors but genuinely protect customer data and ensure reliable service delivery. The flexibility of SOC 2 allows organizations to tailor compliance efforts to their specific services and risks while maintaining the rigor necessary to earn stakeholder confidence.
The journey to SOC 2 compliance demands significant investment of time, resources, and organizational commitment. However, the benefits extend far beyond satisfying customer requirements. Organizations that embrace SOC 2 as a strategic initiative rather than a burden discover operational improvements, enhanced security postures, and clearer risk management practices that strengthen their businesses fundamentally.
As technology continues evolving and new threats emerge, the trust service criteria framework adapts to address contemporary challenges while maintaining consistent foundational principles. Organizations that view SOC 2 as an ongoing commitment to excellence rather than a one-time project position themselves for long-term success in the trust economy.
Stay compliant, secure, and competitive. Discover how Regulance can help you achieve SOC 2 excellence in 2025 and beyond.