How Can GDPR Vulnerability Management Protect Your Business in 2026?


Introduction
Data breaches make headlines almost weekly, and organizations handling European Union citizens' personal data face mounting pressure to secure their digital infrastructure. The General Data Protection Regulation (GDPR) has fundamentally transformed how businesses approach cybersecurity, making vulnerability management not just a technical necessity but a legal obligation. With potential fines reaching up to€20 million or 4% of global annual turnover, companies can no longer afford to treat security vulnerabilities as mere IT concerns.
GDPR vulnerability management represents the intersection of regulatory compliance and proactive cybersecurity. It's about identifying, assessing, and remedying security weaknesses before they become entry points for data breaches that could expose sensitive personal information. Understanding GDPR vulnerability management is essential for maintaining both legal compliance and customer trust.
This guide explores what GDPR vulnerability management entails, why it matters, and how organizations can implement effective strategies to safeguard personal data while meeting regulatory requirements.
What is GDPR Vulnerability Scanning
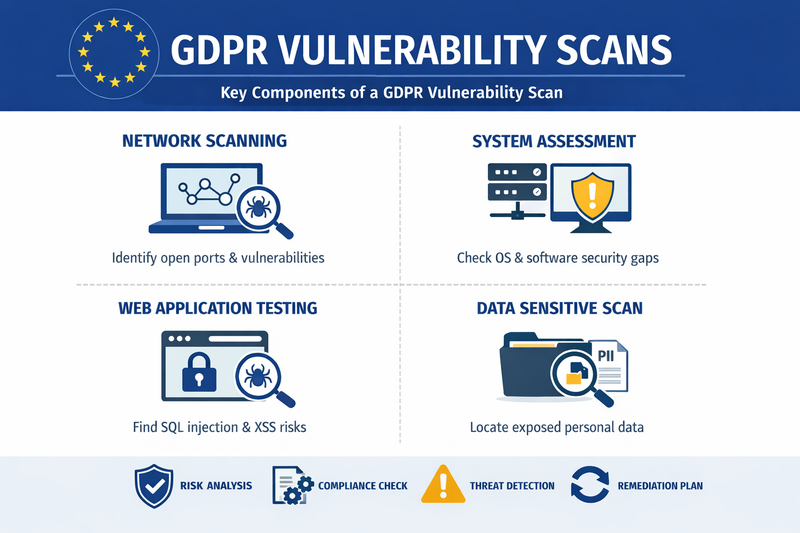
GDPR vulnerability scanning forms the foundation of effective vulnerability management. Vulnerability scanning is the systematic examination of networks, systems, and applications to identify security weaknesses that could be exploited by malicious actors. Under GDPR, this process takes on heightened significance because these vulnerabilities directly threaten the confidentiality, integrity, and availability of personal data.
The GDPR doesn't explicitly mandate vulnerability scanning in those exact terms. Instead, Article 32 requires organizations to implement "appropriate technical and organizational measures" to ensure security appropriate to the risk. This includes the ability to ensure ongoing confidentiality, integrity, availability, and resilience of processing systems and services. Vulnerability scanning emerges as a practical, industry-recognized method for meeting these requirements.
There are several types of vulnerability scans that organizations should consider. Network vulnerability scans examine the infrastructure layer, identifying weaknesses in routers, firewalls, servers, and other network devices. Application vulnerability scans focus on web applications and software, uncovering issues like SQL injection vulnerabilities, cross-site scripting flaws, and insecure authentication mechanisms. Database vulnerability scans specifically target data repositories where personal information is stored, checking for misconfigurations, weak access controls, and unpatched database management systems.
Modern vulnerability scanning tools operate both through authenticated and unauthenticated scans. Authenticated scans provide credentials to examine systems from an insider's perspective, revealing vulnerabilities that might not be visible from the outside. Unauthenticated scans simulate external attackers, showing what malicious actors could discover without legitimate access. Both approaches are valuable for comprehensive GDPR vulnerability management.
The frequency of vulnerability scanning matters significantly. Static quarterly scans no longer suffice in today's rapidly evolving threat landscape. Organizations serious about GDPR compliance typically implement continuous or, at a minimum, weekly scanning, with immediate scans triggered after significant system changes, new software deployments, or when new vulnerabilities are publicly disclosed. This proactive approach aligns with GDPR's emphasis on ongoing security rather than one-time compliance checks.
Vulnerability scanning under GDPR also requires proper documentation. Organizations must maintain records of their scanning activities, including what was scanned, when scans occurred, what vulnerabilities were discovered, and how they were addressed. This documentation serves dual purposes: it demonstrates due diligence to supervisory authorities and provides an audit trail for internal security improvement efforts.
How to Achieve GDPR Vulnerability Management
Achieving effective GDPR vulnerability management requires a structured, multi-layered approach that extends beyond simply running scanning tools. Organizations must develop comprehensive programs that integrate technical measures, organizational processes, and ongoing improvement mechanisms.
Establish a Vulnerability Management Policy
The first step is creating a formal vulnerability management policy that defines your organization's approach to identifying, assessing, and remediating security weaknesses. This policy should specify scanning frequencies, define severity classifications for vulnerabilities, establish remediation timelines based on risk levels, and assign clear responsibilities for each phase of the process. The policy must align with your organization's overall data protection strategy and risk assessment under GDPR Article 32.
Implement Asset Discovery and Inventory
Comprehensive asset discovery identifies all systems, applications, databases, and network devices that process, store, or transmit personal data. This inventory should be continuously updated as your IT environment evolves. Each asset should be classified based on the sensitivity of personal data it handles, with higher-risk assets receiving more frequent and intensive vulnerability assessments.
Deploy Appropriate Scanning Tools
Select vulnerability scanning tools that match your technical environment and compliance needs. Enterprise-grade solutions like Qualys, Tenable Nessus, Rapid7, or open-source alternatives like OpenVAS provide different capabilities. The right choice depends on your infrastructure complexity, budget, and technical expertise. Many organizations use multiple tools to achieve comprehensive coverage, as no single scanner detects every possible vulnerability.
Regulance provides scanning services outside the box so that you don't have to deploy any of these solutions yourself. With the Regulance compliance management solution, you will be able to maintain compliance through continuous monitoring and vulnerability management.
Prioritize Vulnerabilities Using Risk-Based Approaches
Implement a risk-based prioritization system that considers vulnerability severity, exploitability, the sensitivity of data at risk, and potential business impact. The Common Vulnerability Scoring System (CVSS) provides a standardized framework, but contextualizes these scores with your specific environment. A critical vulnerability in a system isolated from personal data processing might rank lower than a moderate vulnerability in your customer database server.
Establish Clear Remediation Workflows
Create systematic processes for addressing discovered vulnerabilities. Critical vulnerabilities affecting systems processing personal data should typically be remediated within days, high-severity issues within weeks, and medium and low-severity vulnerabilities on longer timelines. Document remediation actions, including patch applications, configuration changes, compensating controls, or accepted risks with justification. This documentation is crucial for demonstrating GDPR compliance.
Integrate Vulnerability Management with Change Management
Coordinate vulnerability management with your broader IT change management processes. New systems should undergo vulnerability assessments before deployment. Regular patching schedules should be established and adhered to. When patches cannot be immediately applied due to operational constraints, temporary compensating controls should be implemented and documented.
Conduct Regular Penetration Testing
Beyond automated vulnerability scanning, periodic penetration testing provides deeper insights into how vulnerabilities might be chained together for exploitation. GDPR Article 32 specifically mentions "a process for regularly testing, assessing and evaluating the effectiveness of technical and organisational measures." Annual or bi-annual penetration tests by qualified professionals supplement continuous vulnerability scanning and demonstrate regulatory compliance.
Train Your Team
Ensure that IT staff, security teams, and even general employees understand their roles in maintaining security. Developers should be trained in secure coding practices. System administrators need to understand secure configuration standards. Even non-technical staff should recognize social engineering attempts that could bypass technical controls.
Monitor Threat Intelligence
Stay informed about emerging threats and newly discovered vulnerabilities. Subscribe to security bulletins from software vendors, follow advisories from national cybersecurity agencies, and participate in industry-specific information sharing forums. This intelligence allows you to proactively scan for and address new vulnerabilities before they're widely exploited.
Establish Metrics and Continuous Improvement
Track key performance indicators like mean time to detect vulnerabilities, mean time to remediate, percentage of systems with outstanding critical vulnerabilities, and vulnerability recurrence rates. Regular reviews of these metrics help identify process improvements and demonstrate to leadership and regulators that your vulnerability management program is mature and effective.
What is the Importance of GDPR Vulnerability Management?
The importance of GDPR vulnerability management extends far beyond avoiding regulatory fines, though the financial implications alone warrant serious attention. Understanding why vulnerability management matters helps organizations build commitment at all levels and allocate appropriate resources to these critical activities.
Legal Compliance and Regulatory Obligations
The most direct importance is legal compliance. GDPR Article 32 explicitly requires appropriate security measures, and supervisory authorities consistently cite inadequate security as a factor in data breach penalties. When the British Airways breach resulted in a £20 million fine, poor security practices including unaddressed vulnerabilities were central to the regulatory action. Similarly, Marriott International faced significant penalties partly because acquired systems contained security weaknesses that went unaddressed. Vulnerability management provides demonstrable evidence that your organization takes its Article 32 obligations seriously.
Prevention of Data Breaches
The vast majority of data breaches exploit known vulnerabilities that organizations failed to patch. According to cybersecurity research, over 60% of breaches involve vulnerabilities for which patches were available but not applied. GDPR vulnerability management directly addresses this issue by systematically identifying and closing these security gaps before attackers exploit them. Given that GDPR data breaches must be reported to supervisory authorities within 72 hours and potentially to affected individuals, prevention is infinitely preferable to breach response.
Protection of Data Subject Rights
GDPR enshrines multiple rights for data subjects, including rights to access, rectification, erasure, and data portability. When systems are compromised through unpatched vulnerabilities, organizations may lose the ability to guarantee these rights. Compromised systems might contain modified data, rendering rectification rights meaningless. Breached systems might expose data that subjects believed had been erased. Vulnerability management protects not just data itself but the rights framework GDPR establishes.
Maintaining Business Continuity
Cyberattacks exploiting vulnerabilities threaten data confidentiality, and they can disrupt business operations entirely. Ransomware attacks that encrypt entire systems often enter through known, unpatched vulnerabilities. For organizations whose business models depend on processing personal data, such disruptions can be existential. Vulnerability management ensures system availability, one of the three pillars of information security, alongside confidentiality and integrity.
Preserving Customer Trust and Brand Reputation
In the GDPR era, consumers are increasingly aware of data protection issues. High-profile breaches result in lasting reputational damage that extends far beyond regulatory fines. Studies consistently show that customers avoid businesses after data breaches, with some surveys indicating over 80% of consumers would stop engaging with breached organizations. Proactive vulnerability management demonstrates to customers that you take their privacy seriously, building trust that translates to a competitive advantage.
Reducing Financial Risk
Beyond regulatory fines, data breaches carry substantial financial costs. These include forensic investigation expenses, customer notification costs, credit monitoring services, legal fees, potential civil litigation, and business disruption losses. Industry analyses place the average cost of a data breach at millions of dollars, with costs varying based on breach size and industry. Investment in vulnerability management represents insurance against these far higher potential costs.
Enabling Digital Transformation
Organizations increasingly rely on digital services, cloud computing, and interconnected systems. This digital transformation creates immense business value but also expands the attack surface. Vulnerability management enables organizations to pursue digital innovation confidently, knowing that new systems and services are continuously monitored and secured. Without effective vulnerability management, digital transformation initiatives introduce unacceptable risk.
Supporting Accountability Principle
GDPR's accountability principle requires organizations to demonstrate compliance. Comprehensive vulnerability management programs with proper documentation provide concrete evidence of security efforts. When supervisory authorities investigate or when customers request information about security practices, documented vulnerability management processes demonstrate accountability and good faith efforts to protect personal data.
FAQs
What is the difference between vulnerability scanning and penetration testing under GDPR?
Vulnerability scanning is an automated process that identifies known security weaknesses in systems and applications. It's typically performed frequently, even continuously, and covers broad infrastructure. Penetration testing is a manual, goal-oriented simulation of real-world attacks conducted by security professionals to exploit vulnerabilities and assess actual impact. GDPR Article 32 references both concepts through requirements for security measures and regular testing of their effectiveness. Organizations should implement continuous vulnerability scanning supplemented by periodic penetration testing for comprehensive security assurance.
How often should vulnerability scans be conducted to maintain GDPR compliance?
GDPR doesn't specify exact scanning frequencies, instead requiring "appropriate" measures based on risk. However, best practices and regulatory guidance suggest continuous or at minimum weekly automated vulnerability scanning for systems processing personal data. Critical systems or those facing the internet should be scanned more frequently. Additionally, scans should be triggered after significant system changes, new deployments, or when new critical vulnerabilities are publicly disclosed. The specific frequency should be documented in your vulnerability management policy and justified based on your risk assessment.
Do small businesses need vulnerability management for GDPR compliance?
Yes, though the scope may differ from large enterprises. GDPR applies to organizations of all sizes that process EU residents' personal data. Article 32 requires security measures "appropriate to the risk," meaning small businesses must assess their specific risks and implement proportionate controls. A small business with limited IT infrastructure might use simpler, more affordable scanning tools and less frequent assessments than a multinational corporation, but systematic vulnerability identification and remediation remain necessary. Demonstrating appropriate efforts relative to your size and resources is key.
What happens if a vulnerability is exploited before it can be patched?
If a vulnerability exploitation results in a personal data breach, GDPR's breach notification requirements apply. Organizations must notify their supervisory authority within 72 hours if the breach poses risk to individuals' rights and freedoms. Affected individuals must be notified if the breach poses high risk. However, if the organization can demonstrate that appropriate security measures were in place, including active vulnerability management, risk-based prioritization, and compensating controls for unpatched vulnerabilities, this may mitigate regulatory consequences. Documentation of security efforts is crucial in these situations.
Can vulnerability management be outsourced while maintaining GDPR compliance?
Yes, organizations can engage external security firms or managed service providers like Regulance for vulnerability management activities. However, GDPR's accountability principle means the data controller remains ultimately responsible for compliance. When outsourcing, ensure contracts clearly define the provider's responsibilities, security obligations, and reporting requirements per GDPR Article 28. Conduct due diligence on providers' competence and reliability. Remember that outsourcing execution doesn't eliminate your obligation to oversee the process, review findings, and ensure vulnerabilities are appropriately addressed.
How does vulnerability management relate to GDPR's data protection by design and by default?
Article 25 requires organizations to implement appropriate technical and organizational measures to integrate data protection into processing activities from the outset. Vulnerability management directly supports this requirement by ensuring systems are designed, deployed, and maintained securely throughout their lifecycle. Conducting vulnerability assessments before deploying new systems identifies security weaknesses during development rather than after personal data is at risk. This proactive approach embodies data protection by design, while ongoing vulnerability management ensures systems remain secure by default over time.
What should be included in vulnerability management documentation for GDPR purposes?
Comprehensive documentation should include your vulnerability management policy defining processes and responsibilities, asset inventories identifying systems processing personal data, vulnerability scan reports showing what was scanned and when, risk assessments explaining how vulnerabilities were prioritized, remediation records documenting how vulnerabilities were addressed and timelines, exception justifications for accepted risks or delayed patches, and testing results from penetration tests or security assessments. This documentation demonstrates accountability and provides evidence of ongoing compliance efforts to supervisory authorities.
Are there specific vulnerabilities that GDPR particularly concerns itself with?
While GDPR doesn't specify particular vulnerabilities, it emphasizes protecting confidentiality, integrity, and availability of personal data. Vulnerabilities that pose the greatest GDPR risk are those enabling unauthorized access to personal data, such as authentication bypasses or privilege escalation flaws; those allowing data exfiltration like SQL injection or insecure APIs; those threatening data integrity such as vulnerabilities enabling unauthorized modification; and those affecting availability, such as denial of service vulnerabilities. Vulnerabilities in systems processing special category data under Article 9 warrant particular attention due to heightened sensitivity.
Conclusion
GDPR vulnerability management represents a critical convergence of regulatory compliance, cybersecurity best practices, and organizational accountability. As data breaches continue making headlines and supervisory authorities demonstrate willingness to impose substantial fines, organizations can no longer treat vulnerability management as an optional IT activity. It has become a fundamental legal obligation and a cornerstone of responsible data stewardship.
The comprehensive approach outlined in this guide emphasizes that effective GDPR vulnerability management requires establishing formal policies, implementing systematic processes, maintaining thorough documentation, and fostering organization-wide commitment to security. From initial asset discovery through risk-based remediation prioritization to continuous monitoring and improvement, each component plays a vital role in protecting personal data and demonstrating regulatory compliance.
The importance of vulnerability management manifests across multiple dimensions: legal compliance that avoids crippling fines, breach prevention that protects both data subjects and organizational interests, maintenance of customer trust that drives competitive advantage, and enablement of digital innovation without unacceptable risk. These benefits far outweigh the investments required, particularly when considering the catastrophic costs of major data breaches.
For organizations seeking to streamline their GDPR compliance journey, solutions like Regulance offer integrated approaches that connect vulnerability management to broader data protection requirements. By automating technical assessments, contextualizing findings within regulatory frameworks, and maintaining comprehensive documentation, such platforms reduce compliance complexity while enhancing security effectiveness.
Stay ahead of GDPR risks. Partner with Regulance to secure your systems and ensure full compliance in 2025.