HIPAA Security Rule: 7 Critical Steps Every Healthcare Organization Needs


Introduction
Healthcare organizations face a cyberattack every 43 minutes, making patient data protection the industry's most urgent priority. With cyber-attacks on healthcare organizations increasing by 55% in recent years, and the average cost of a healthcare data breach reaching $10.93 million, HIPAA security compliance is about safeguarding your patients' most sensitive information and your organization's reputation.
The Health Insurance Portability and Accountability Act (HIPAA) Security Rule provides the roadmap for protecting electronic protected health information (ePHI), but navigating its requirements can feel overwhelming. Many healthcare organizations struggle to translate the rule's technical safeguards into practical, effective security measures that actually work in real-world healthcare environments.
This comprehensive guide breaks down HIPAA security compliance into seven actionable steps, helping you build a robust security framework that protects patient data while supporting efficient healthcare delivery.
HIPAA Security and Privacy Rules: The Overview
The HIPAA Security and Privacy Rules form the foundation of healthcare data protection in the United States, working together to create comprehensive safeguards for patient information. Understanding the relationship between these two rules is essential for building an effective compliance program.
The HIPAA Privacy Rule, enacted in 2003, establishes national standards for protecting individually identifiable health information in all formats; electronic, paper, and oral. This rule governs how covered entities may use and disclose protected health information (PHI), giving patients rights over their health information and setting boundaries on its use and release. The Privacy Rule applies to all forms of PHI and focuses on controlling access, use, and disclosure of patient information.
The HIPAA Security Rule, implemented in 2005, specifically addresses electronic protected health information (ePHI). While the Privacy Rule covers all PHI formats, the Security Rule provides detailed technical, administrative, and physical safeguards exclusively for electronic health information. This rule recognizes that electronic health information faces unique vulnerabilities and requires specialized protection measures.
Key differences between the rules highlight their complementary nature. The Privacy Rule is broader in scope, covering all PHI regardless of format, while the Security Rule is more specific, focusing solely on electronic information but providing detailed technical requirements. The Privacy Rule emphasizes policies and procedures for information handling, whereas the Security Rule mandates specific security controls and technologies.
Who Must Comply with the HIPAA Security Rule?
Understanding who must comply with HIPAA security requirements is crucial for determining your organization's obligations and ensuring comprehensive protection of electronic protected health information. The Security Rule's coverage extends beyond healthcare providers to include various entities that handle ePHI in the modern healthcare ecosystem.
Covered Entities form the primary compliance group and include:
- Healthcare providers (hospitals, physician practices, dentists, pharmacies, nursing homes) that conduct electronic transactions
- Health plans (insurance companies, HMOs, Medicare, Medicaid, employer-sponsored plans)
- Healthcare clearinghouses that process health information between providers and plans
Business Associates became directly subject to HIPAA security requirements under the HITECH Act of 2009. These include technology vendors, billing companies, legal firms, accountants, cloud storage providers, EHR vendors, and IT support companies that handle ePHI on behalf of covered entities.
Additional Compliance Requirements:
- Subcontractors must comply when business associates use them for services involving ePHI access
- Workforce members (employees, temporary staff, volunteers, trainees) must follow HIPAA security policies
- Hybrid entities with both healthcare and non-healthcare functions must ensure compliance for their healthcare components
Enforcement Reality: The Department of Health and Human Services Office for Civil Rights actively investigates violations and imposes substantial penalties on organizations of all sizes, making comprehensive HIPAA security compliance essential for risk management across the entire healthcare supply chain.
This broad scope means that virtually any organization handling electronic protected health information, whether directly providing healthcare services or supporting those who do, must implement appropriate HIPAA security safeguards.
The Three Standards of the HIPAA Security Rule
The HIPAA Security Rule organizes its requirements into three distinct categories of safeguards, each addressing different aspects of protecting electronic protected health information. These standards work together to create a comprehensive security framework that addresses the full spectrum of potential vulnerabilities and attack vectors.
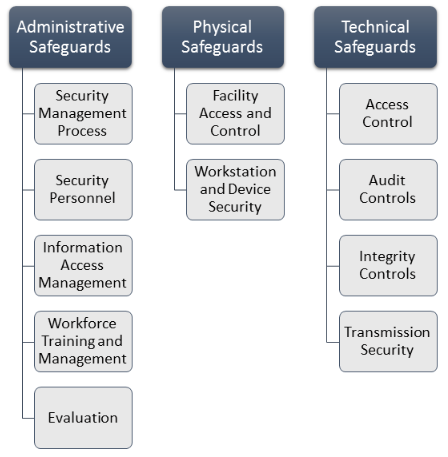
Administrative Safeguards
Administrative safeguards establish the foundation of HIPAA security compliance through policies, procedures, and management controls. These safeguards focus on the human element of security, recognizing that technology alone cannot protect ePHI without proper organizational governance and workforce management.
Key administrative safeguards include security management processes that require organizations to implement policies and procedures to prevent, detect, contain, and correct security violations. Organizations must assign security responsibility to a dedicated security officer who serves as the focal point for HIPAA security compliance. Workforce training and access management ensure that personnel understand their security responsibilities and have appropriate access to ePHI based on their job functions. Security awareness programs, incident response procedures, and contingency planning round out the administrative requirements that create the organizational foundation for effective ePHI protection.
Physical Safeguards
Physical safeguards protect electronic systems, equipment, and media containing ePHI from unauthorized physical access, theft, and environmental hazards. These measures address the physical security aspects that support electronic information protection.
Essential physical safeguards include facility access controls that limit physical access to areas where ePHI is stored or processed, including building entrances, server rooms, and clinical work areas. Workstation use controls govern how computers accessing ePHI are used and positioned to prevent unauthorized viewing. Device and media controls address the handling of electronic storage devices, backup media, and portable devices such as laptops, tablets, and smartphones that access or store ePHI.
Technical Safeguards
Technical safeguards involve technology controls that protect ePHI and control access to it. These measures leverage technical capabilities to enforce security policies and provide automated protection mechanisms.
Critical technical safeguards include access controls that ensure only authorized users can access ePHI systems through unique user identification, automatic logoff procedures, and role-based access restrictions. Audit controls provide the ability to record and examine access and activity in systems containing ePHI. Integrity controls protect ePHI from unauthorized alteration or destruction, while person or entity authentication verifies user identities through mechanisms like multi-factor authentication. Transmission security protects ePHI during electronic transmission over networks through encryption and secure communication protocols.
7 Essential Steps to Achieve HIPAA Security and Privacy Compliance
Achieving comprehensive HIPAA security compliance requires a systematic approach that addresses all aspects of protecting electronic protected health information. These seven critical steps provide a practical roadmap for building and maintaining an effective HIPAA security program that meets regulatory requirements while supporting efficient healthcare operations.

Step 1: Conduct Comprehensive Security Risk Assessments
A thorough security risk assessment forms the foundation of effective HIPAA security compliance, providing the insights needed to identify vulnerabilities and prioritize security investments. This assessment must examine all systems, processes, and practices that involve ePHI, considering both technical vulnerabilities and procedural weaknesses.
The assessment process begins with asset inventory, cataloging all systems, devices, applications, and data repositories that create, receive, maintain, or transmit ePHI. This inventory should include servers, workstations, mobile devices, network equipment, cloud services, and backup systems. Understanding what assets exist and how they interact provides the foundation for identifying potential vulnerabilities.
Threat identification examines potential sources of security incidents, including external attackers, insider threats, natural disasters, and system failures. Healthcare organizations face unique threats such as targeted ransomware attacks, business email compromise schemes, and medical identity theft. The assessment should consider both current threat levels and emerging risks that may affect the organization.
Vulnerability analysis evaluates weaknesses in systems, processes, and controls that could be exploited by identified threats. This includes technical vulnerabilities such as unpatched software, weak authentication mechanisms, and inadequate encryption, as well as procedural vulnerabilities like insufficient access controls or inadequate training.
Risk calculation combines threat likelihood with potential impact to prioritize risks for remediation. High-likelihood, high-impact risks require immediate attention, while lower-priority risks can be addressed through longer-term planning. This prioritization helps organizations allocate limited security resources effectively.
Step 2: Develop and Implement Administrative Safeguards
Administrative safeguards establish the organizational foundation for HIPAA security compliance through policies, procedures, and governance structures. These measures address the human elements of security and ensure that organizational processes support effective protection of ePHI.
Security management structure includes appointing a qualified security officer and establishing clear security governance. The security officer should have appropriate authority and resources to implement security measures and coordinate compliance activities across the organization. Clear reporting relationships and accountability structures support effective security management.
Workforce security procedures govern personnel access to ePHI throughout the employment lifecycle. This includes background check procedures, access authorization processes, security training requirements, and access termination procedures. Regular access reviews ensure that access rights remain appropriate as job responsibilities change.
Access management policies define how access to ePHI is granted, modified, and revoked. These policies should implement role-based access controls, establish approval procedures for access requests, and define regular review processes. Automated access management systems can help enforce policies consistently and reduce administrative burden.
Security training programs ensure that all workforce members understand their security responsibilities and know how to protect ePHI. Training should cover security policies, threat awareness, incident reporting, and specific procedures relevant to job functions. Regular training updates help address emerging threats and reinforce security awareness.
Step 3: Establish Physical Safeguards
Physical safeguards protect the electronic systems, equipment, and media containing ePHI from unauthorized physical access and environmental threats. These measures complement technical controls by addressing physical vulnerabilities that could compromise electronic security measures.
Facility access controls restrict physical access to areas containing ePHI systems and data. This includes implementing access controls at building entrances, server rooms, and clinical areas. Access controls should include visitor management procedures, area access restrictions based on job functions, and monitoring systems to detect unauthorized access attempts.
Workstation security measures protect individual workstations and devices that access ePHI. This includes positioning workstations to prevent unauthorized viewing, implementing automatic screen locks, and establishing procedures for workstation access and use. Physical security measures should complement technical access controls to provide comprehensive protection.
Device and media management addresses the handling of portable devices, storage media, and backup materials containing ePHI. This includes implementing procedures for device inventory, secure storage, transportation, and disposal. Organizations should also address the use of personal devices for accessing ePHI through bring-your-own-device policies.
Environmental protections address threats from natural disasters, power outages, and other environmental hazards. This includes implementing fire suppression systems, environmental monitoring, backup power systems, and physical security measures such as locks and surveillance systems.
Step 4: Implement Technical Safeguards
Technical safeguards leverage technology capabilities to protect ePHI and enforce security policies through automated mechanisms. These measures provide the technological foundation for HIPAA security compliance and help ensure consistent protection of electronic health information.
Access control systems ensure that only authorized users can access ePHI and that access is limited to information necessary for job functions. This includes implementing unique user identification, strong authentication mechanisms, automatic logoff procedures, and role-based access controls. Multi-factor authentication provides additional security for high-risk access scenarios.
Audit logging and monitoring systems record access and activity involving ePHI to support security monitoring and compliance verification. Comprehensive audit logs should capture user access, data modifications, system administration activities, and security events. Regular log review helps identify potential security incidents and demonstrates compliance with HIPAA requirements.
Data integrity controls protect ePHI from unauthorized alteration or destruction through technical measures such as checksums, digital signatures, and version controls. These measures help ensure that ePHI remains accurate and complete throughout its lifecycle and provide mechanisms for detecting unauthorized changes.
Encryption and data protection measures protect ePHI during storage and transmission using cryptographic controls. Encryption should be implemented for data at rest on servers, workstations, and portable devices, as well as data in transit over networks. Key management procedures ensure that encryption remains effective and that encrypted data can be recovered when necessary.
Step 5: Create Comprehensive Policies and Procedures
Comprehensive policies and procedures translate HIPAA security requirements into specific, actionable guidance that workforce members can follow in their daily activities. These documents provide the operational framework for maintaining HIPAA security compliance and help ensure consistent implementation of security measures.
Policy development process should involve stakeholders from across the organization, including clinical staff, IT personnel, administration, and legal counsel. Policies should be written in clear, understandable language and address specific organizational circumstances while meeting HIPAA requirements. Regular policy reviews ensure that procedures remain current with changing regulations and technology.
Incident response procedures define how the organization will identify, respond to, and recover from security incidents involving ePHI. These procedures should establish clear roles and responsibilities, communication protocols, containment measures, and recovery processes. Incident response plans should be tested regularly to ensure effectiveness during actual security incidents.
Business associate management procedures govern relationships with third-party vendors and service providers that access ePHI. This includes due diligence processes for vendor selection, business associate agreement requirements, ongoing monitoring of vendor security measures, and incident response coordination with business associates.
Training and awareness programs ensure that all personnel understand their HIPAA security responsibilities and receive regular updates on security threats and procedures. Training should be tailored to specific job roles and include both initial orientation and ongoing security awareness activities.
Step 6: Establish Business Associate Management
Effective business associate management extends HIPAA security protections throughout the healthcare ecosystem by ensuring that third-party vendors and service providers implement appropriate safeguards for ePHI. This comprehensive approach addresses the expanded attack surface created by modern healthcare's reliance on external service providers.
Vendor assessment procedures evaluate potential business associates' security capabilities before entering into service relationships. This assessment should examine the vendor's security policies, technical safeguards, incident response capabilities, and compliance track record. Due diligence activities help ensure that business associates can meet HIPAA security requirements.
Business associate agreements establish contractual obligations for protecting ePHI and define responsibilities for security incidents. These agreements should specify required safeguards, permitted uses and disclosures, incident notification requirements, and audit rights. Regular agreement reviews ensure that terms remain current with evolving regulations and business relationships.
Ongoing monitoring activities verify that business associates maintain appropriate security measures throughout the service relationship. This includes regular security assessments, review of compliance documentation, and monitoring of security incidents involving business associates. Continuous monitoring helps identify potential issues before they become compliance violations.
Incident coordination procedures establish processes for managing security incidents that involve business associates. This includes notification requirements, joint investigation procedures, containment measures, and recovery coordination. Clear procedures help ensure that incidents involving business associates receive appropriate attention and response.
Step 7: Maintain Ongoing Compliance Monitoring
Sustainable HIPAA security compliance requires ongoing monitoring, assessment, and improvement activities that address evolving threats, changing regulations, and organizational growth. This continuous improvement approach helps ensure that security measures remain effective and compliant over time.
Regular compliance assessments evaluate the effectiveness of implemented safeguards and identify areas for improvement. These assessments should examine all aspects of the HIPAA security program, including policies, technical controls, training programs, and business associate relationships. Assessment frequency should reflect organizational risk levels and regulatory requirements.
Security metrics and reporting provide visibility into security program performance and compliance status. Key metrics include security incident rates, training completion rates, audit finding resolution times, and risk assessment results. Regular reporting to senior management demonstrates security program value and supports resource allocation decisions.
Continuous improvement processes incorporate lessons learned from security incidents, compliance assessments, and industry best practices into ongoing security program enhancements. This includes updating policies and procedures, implementing new security technologies, and refining training programs based on identified needs.
Regulatory monitoring activities track changes in HIPAA requirements, enforcement actions, and industry guidance to ensure that security programs remain current. This includes monitoring OCR guidance, reviewing enforcement actions against other organizations, and participating in healthcare security communities to stay informed about emerging threats and best practices.
Conclusion
Success in HIPAA security compliance isn't measured by passing audits, it's proven through unbreached patient trust, seamless operations, and sustainable growth. The seven-step framework presented here empowers healthcare organizations to transform security from a necessary expense into a strategic asset that strengthens every aspect of their mission to deliver exceptional patient care.
Turn HIPAA security rules compliance from nightmare to advantage. Regulance automates protection, prevents breaches. Start your transformation today!