HIPAA Compliance Checklist 2025: Your Step-by-Step Guide


Introduction
Navigating HIPAA can feel overwhelming, but it doesn’t have to be. This HIPAA Compliance Checklist gives you a clear, human-friendly roadmap to protect patient data, avoid costly violations, and stay audit-ready year-round. In one place, you’ll find the essentials, risk assessments, policies and procedures, workforce training, Business Associate Agreements, access controls, incident response, and ongoing monitoring explained in plain language so you can act with confidence.
Whether you’re a clinic, lab, health tech startup, or billing service, this guide helps you align with the HIPAA Privacy, Security, and Breach Notification Rules while building trust with patients and partners. Use this checklist to turn compliance from a headache into a repeatable process that strengthens your security posture and keeps your organization ahead of regulators.
Understanding HIPAA: The Foundation of Healthcare Data Protection
The Health Insurance Portability and Accountability Act (HIPAA) is the cornerstone of patient privacy protection in the United States. Enacted in 1996 and significantly updated through the HITECH Act in 2009, HIPAA establishes national standards for protecting patient health information.
HIPAA applies to covered entities (healthcare providers, health plans, and healthcare clearinghouses) and their business associates who handle protected health information (PHI). The key insight many IT professionals miss is that HIPAA compliance is about building a culture of privacy and security that protects your most vulnerable stakeholders: patients.
The regulation consists of several key components, but for IT professionals, three areas demand particular attention: the Privacy Rule (governing how PHI can be used and disclosed), the Security Rule (establishing technical safeguards for electronic PHI), and the Breach Notification Rule (requiring prompt notification of data breaches).
Understanding these foundations helps frame why each item in our compliance checklist matters. Every technical control, every administrative procedure, and every security measure serves the ultimate goal of protecting patient privacy while enabling quality healthcare delivery.
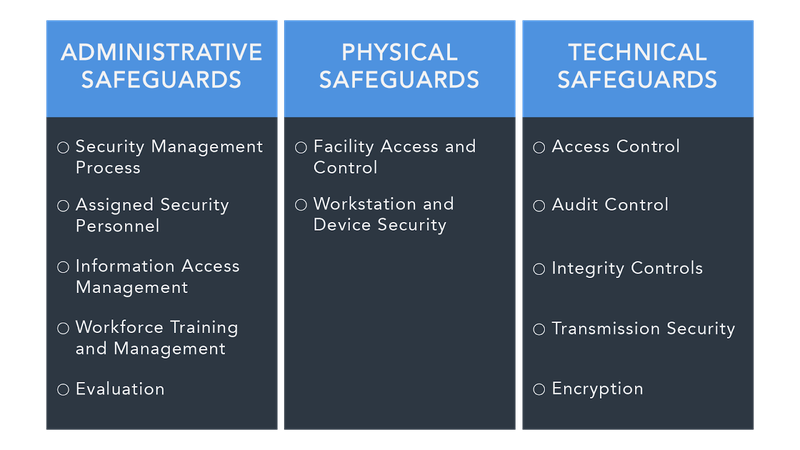
Administrative Safeguards: Building Your HIPAA Foundation
Security Officer Designation and Responsibilities Your organization must designate a HIPAA Security Officer responsible for developing and implementing security policies and procedures. This requires dedicated focus and executive support. Ensure your Security Officer has direct access to senior leadership and sufficient resources to fulfill their responsibilities effectively.
Workforce Training and Access Management Implement comprehensive HIPAA training for all workforce members who handle PHI. This includes initial training for new hires, annual refresher training, and specialized training when roles change or new technologies are introduced. Document all training activities and maintain records for at least six years.
Establish clear procedures for granting, modifying, and terminating access to PHI systems. Use role-based access controls that follow the principle of least privilege, users should have access only to the minimum PHI necessary to perform their job functions. Regularly review and update access permissions, especially during employee transitions.
Information Access Management Policies Develop formal policies governing who can access PHI under what circumstances. These policies should clearly define authorized uses and disclosures, specify approval processes for access requests, and establish audit procedures to monitor compliance. Remember that patients have the right to request restrictions on how their PHI is used and disclosed.
Security Incident Procedures Create detailed incident response procedures that address identification, containment, investigation, and reporting of potential security incidents. Your procedures should include clear escalation paths, communication protocols, and documentation requirements. Practice these procedures regularly through tabletop exercises and simulations.
Contingency Planning Develop comprehensive disaster recovery and business continuity plans that ensure PHI availability during emergencies. These plans should include data backup procedures, system recovery priorities, emergency access protocols, and alternative processing sites if needed. Test your contingency plans at least annually and update them based on lessons learned.
Technical Safeguards: Securing Your Digital Infrastructure
Access Control Systems Implement robust technical controls to limit access to PHI systems and applications. This includes unique user identification for each authorized user, automatic logoff after predetermined periods of inactivity, and encryption of PHI during transmission and at rest. Deploy multi-factor authentication for all systems containing PHI, especially those accessible remotely.
Audit Controls and Monitoring Establish comprehensive logging and monitoring systems that record all access attempts, modifications, and deletions of PHI. Your audit logs should capture who accessed what information, when the access occurred, and what actions were performed. Implement automated alerting for suspicious activities and conduct regular log reviews to identify potential security incidents.
Data Integrity Controls Deploy technical controls to ensure PHI isn't improperly altered or destroyed. This includes database integrity constraints, digital signatures for critical data, version control systems, and regular data integrity checks. Implement backup and recovery procedures that maintain data integrity during restoration processes.
Transmission Security Measures Encrypt all PHI transmissions over public networks and implement secure communication protocols for internal networks. Use VPNs for remote access, secure email systems for PHI communications, and encrypted file transfer protocols for data exchanges with business associates. Regularly update encryption algorithms and key management procedures to maintain security effectiveness.
Physical Safeguards: Protecting Your Physical Infrastructure
Facility Access Controls Implement comprehensive physical security measures for areas containing PHI systems and media. This includes card access systems, security cameras, visitor management procedures, and environmental controls. Ensure that server rooms, network closets, and workstation areas have appropriate access restrictions and monitoring.
Workstation and Device Security Establish policies and procedures governing the use of workstations and mobile devices that access PHI. Implement automatic screen locks, device encryption, remote wipe capabilities, and secure disposal procedures for end-of-life equipment. Consider the physical positioning of workstations to prevent unauthorized viewing of PHI.
Media Controls and Data Disposal Develop formal procedures for handling, storing, and disposing of media containing PHI. This includes backup tapes, hard drives, USB devices, and printed materials. Implement secure destruction procedures that ensure PHI cannot be recovered from disposed media. Maintain detailed inventories of portable media and their disposal records.
Essential Security Technologies for HIPAA Compliance
Encryption and Key Management Deploy enterprise-grade encryption for PHI at rest and in transit. Use AES-256 encryption for stored data and TLS 1.3 for data transmissions. Implement robust key management practices including regular key rotation, secure key storage, and proper key escrow procedures. Consider using Hardware Security Modules (HSMs) for high-security environments.
Network Security Architecture Design your network with security in mind, implementing network segmentation to isolate PHI systems from general business networks. Deploy next-generation firewalls, intrusion detection and prevention systems, and network access control solutions. Regularly conduct vulnerability assessments and penetration testing to identify security gaps.
Identity and Access Management (IAM) Implement comprehensive IAM solutions that provide centralized user authentication, authorization, and account management. Use single sign-on (SSO) where appropriate to reduce password-related risks while maintaining audit trails. Deploy privileged access management (PAM) solutions for administrative accounts.
Backup and Recovery Solutions Implement automated, encrypted backup systems with regular testing of recovery procedures. Ensure backups are stored securely and geographically separated from primary systems. Maintain detailed recovery time objectives (RTOs) and recovery point objectives (RPOs) that align with business requirements and patient care needs.
Business Associate Management and Third-Party Risk
Business Associate Agreements (BAAs) Ensure all business associates who handle PHI on your behalf have signed compliant BAAs that clearly define their security responsibilities and your organization's requirements. Regularly review and update BAAs to reflect changing business relationships and regulatory requirements.
Vendor Risk Assessment Implement formal risk assessment procedures for all vendors who may have access to PHI or PHI systems. This includes security questionnaires, on-site assessments, penetration testing reviews, and ongoing monitoring of vendor security posture. Maintain a vendor risk registry and regularly reassess high-risk relationships.
Cloud Service Provider Evaluation When selecting cloud services for PHI storage or processing, ensure providers offer appropriate security controls, compliance certifications, and contractual protections. Evaluate their data center security, encryption capabilities, access controls, and incident response procedures. Require cloud providers to sign BAAs and provide regular compliance attestations.
Incident Response and Breach Management
Incident Detection and Classification Implement comprehensive monitoring systems that can detect potential security incidents across your infrastructure. Establish clear criteria for classifying incidents based on severity and potential impact on PHI. Train your incident response team to quickly assess whether incidents constitute reportable breaches under HIPAA.
Breach Assessment and Notification Develop detailed procedures for conducting breach risk assessments within the required 60-day discovery period. Your assessment should consider the nature and extent of PHI involved, the person who disclosed the information, whether the information was actually viewed or acquired, and the extent to which risk has been mitigated.
Prepare breach notification templates and procedures for notifying patients, the Department of Health and Human Services, and potentially the media, depending on breach severity. Maintain detailed documentation of all breach-related activities to demonstrate compliance with notification requirements.
Regular Assessments and Continuous Improvement
Annual Risk Assessments Conduct comprehensive risk assessments at least annually or when significant changes occur to your environment. These assessments should identify potential threats and vulnerabilities, evaluate existing safeguards, and prioritize remediation activities based on risk levels. Document assessment findings and remediation plans with clear timelines and accountability.
Audit and Monitoring Programs Implement ongoing audit programs that regularly review access logs, security controls, and policy compliance. Use both automated tools and manual reviews to identify potential compliance gaps or security incidents. Maintain audit documentation for at least six years and ensure audit findings are promptly addressed.
Policy Review and Updates Regularly review and update HIPAA policies and procedures to reflect changes in technology, business processes, and regulatory requirements. Ensure all workforce members are notified of policy changes and receive appropriate training on updates. Maintain version control for all policies and document the rationale for changes.
Training and Awareness: Your Human Firewall
Comprehensive Training Programs Develop role-specific HIPAA training programs that address the unique responsibilities and risks associated with different job functions. Include practical scenarios, real-world examples, and hands-on exercises that help workforce members understand how HIPAA applies to their daily activities.
Ongoing Awareness Campaigns Implement regular security awareness campaigns that keep HIPAA compliance top-of-mind for all workforce members. Use newsletters, lunch-and-learn sessions, phishing simulations, and other engaging methods to reinforce security principles and share lessons learned from incidents or near-misses.
Testing and Validation Regularly test your workforce's understanding of HIPAA requirements through assessments, simulated incidents, and practical exercises. Use testing results to identify knowledge gaps and adjust training programs accordingly. Consider implementing gamification elements to increase engagement and retention.
Technology Implementation Best Practices
Staged Implementation Approach When implementing new HIPAA compliance technologies, use a phased approach that allows for testing and validation before full deployment. Start with pilot programs in low-risk environments and gradually expand based on lessons learned. This approach minimizes disruption to patient care while ensuring security controls are properly implemented.
Integration and Interoperability Ensure new security technologies integrate effectively with existing systems and don't create operational barriers that could lead to workarounds or security gaps. Consider the user experience impact of security controls and design implementations that enhance rather than hinder workflow efficiency.
Performance Monitoring and Optimization Continuously monitor the performance and effectiveness of your HIPAA compliance technologies. Establish key performance indicators (KPIs) and metrics that help you measure compliance posture and identify areas for improvement. Regularly review and optimize security controls to maintain effectiveness while minimizing operational impact.
Preparing for HIPAA Audits and Investigations
Documentation and Record Keeping Maintain comprehensive documentation of all HIPAA compliance activities, including risk assessments, training records, incident reports, and remediation activities. Organize documentation in a manner that facilitates quick retrieval during audits or investigations. Consider using compliance management platforms to centralize documentation and automate record-keeping processes.
Audit Readiness Procedures Develop procedures for responding to HIPAA audits or investigations from the Office for Civil Rights (OCR). These procedures should include designation of audit response team members, communication protocols, and document production processes. Conduct mock audits to identify potential issues and improve your readiness posture.
Corrective Action Planning Establish procedures for developing and implementing corrective action plans when compliance gaps are identified. Ensure corrective actions address root causes rather than just symptoms and include measures to prevent recurrence. Track corrective action completion and effectiveness through ongoing monitoring.
Conclusion
HIPAA compliance is an ongoing commitment to protecting patient privacy and maintaining the trust placed in healthcare organizations. The checklist items outlined in this guide provide a comprehensive framework for building and maintaining effective HIPAA compliance programs.
Success requires more than just checking boxes; it demands a culture of security awareness, continuous improvement, and genuine commitment to patient privacy. Start with the fundamentals;administrative safeguards, technical controls, and physical security measures, then build upon that foundation with advanced technologies and comprehensive risk management practices.
Remember that HIPAA compliance is ultimately about people: the patients who trust you with their most sensitive information and the workforce members who handle that information daily. By implementing robust compliance programs, you're not just avoiding regulatory penalties, you're upholding the fundamental ethical obligations of healthcare and contributing to a more secure, trustworthy healthcare system.
The investment in HIPAA compliance may seem substantial, but the cost of non-compliance in terms of financial penalties, reputational damage, and patient trust far exceeds the investment required to get it right. Use this checklist as your roadmap, adapt it to your organization's unique needs, and commit to the ongoing vigilance that effective HIPAA compliance requires.
Your patients' privacy and your organization's future depend on the choices you make today. Make them count.Simplify HIPAA compliance today. With Regulance, following the checklist becomes easier, faster, and fully aligned with healthcare regulations.