Data Privacy vs Data Security: What’s the Difference And Which One Does Your Business Need Most?


Introduction
We live in an era where data has become the world's most valuable resource. Every click, purchase, message, and interaction generates information that businesses collect, store, and analyze. But with this digital gold rush comes enormous responsibility. Headlines about data breaches, privacy violations, and cyberattacks have become disturbingly common, leaving both businesses and consumers anxious about the safety of their information.
Many people use "data privacy" and "data security" interchangeably, assuming they mean the same thing. While these concepts are closely related and work together to protect information, they address fundamentally different aspects of data protection. Understanding this distinction is essential for compliance, customer trust, and business survival.
This applies to startup founders, an IT manager, or a business executive, therefore, grasping the nuances between data privacy and data security will help you build stronger protection systems, avoid costly regulatory fines, and earn the trust of your customers. This article explains what sets these two concepts apart and why your business needs both.
What is Data Privacy and Data Security?
Understanding Data Privacy
Data privacy is about rights, consent, and control. It focuses on who has access to data, how that data can be used, and giving individuals control over their personal information. Think of data privacy as the rulebook that governs proper data handling.
Data privacy addresses questions like: Who can see my information? What can they do with it? Can I request its deletion? How long will it be stored? Did I give permission for this use?
Data privacy encompasses several key principles:
Consent and Transparency: Organizations must inform individuals about what data they're collecting and obtain explicit permission before gathering or using it. This is why you see cookie consent banners and privacy notices everywhere online.
Purpose Limitation: Data should only be collected for specific, legitimate purposes and not used for anything beyond what was originally stated. If a company collects your email for shipping notifications, they shouldn't use it for marketing without separate consent.
Data Minimization: Businesses should only collect the minimum amount of data necessary to accomplish their stated purpose. Just because you can collect information doesn't mean you should.
Individual Rights: Data privacy gives people rights over their information, including the ability to access, correct, delete, or transfer their data. These rights are enshrined in regulations like the GDPR and CCPA.
Accountability: Organizations must demonstrate compliance with privacy principles and be held accountable for how they handle personal information.
Real-world data privacy considerations include anonymizing customer information before analysis, allowing users to opt out of data collection, providing clear privacy policies, and honoring deletion requests. Privacy is fundamentally about respecting individual autonomy and building trust.
Understanding Data Security
Data security, on the other hand, is about protection against threats. It's the set of technical and organizational measures designed to safeguard data from unauthorized access, corruption, theft, or loss. If data privacy is the rulebook, data security is the fortress that enforces those rules.
Data security focuses on the "how" of protection: How do we prevent hackers from stealing information? How do we ensure data isn't corrupted? How do we maintain availability while preventing unauthorized access?
Data security involves three fundamental principles, known as the CIA triad:
Confidentiality: Ensuring that data is accessible only to authorized individuals. This involves encryption, access controls, and authentication measures to keep sensitive information away from prying eyes.
Integrity: Guaranteeing that data remains accurate, complete, and unaltered except by authorized parties. Security measures must prevent both accidental corruption and malicious tampering.
Availability: Making sure that authorized users can access data when they need it. This includes protecting against attacks that might take systems offline and implementing backup systems for continuity.
Data security employs various technical safeguards:
Encryption: Converting data into coded formats that only authorized parties with the decryption key can read, protecting information both in storage and during transmission.
Access Controls: Implementing authentication systems, passwords, multi-factor authentication, and role-based permissions to ensure only the right people can access specific data.
Firewalls and Network Security: Creating barriers between trusted internal networks and untrusted external networks to prevent unauthorized intrusions.
Security Monitoring: Continuously watching for suspicious activities, potential breaches, and vulnerabilities that could be exploited.
Backup and Recovery: Maintaining copies of data and having plans to restore information if it's lost, corrupted, or encrypted by ransomware.
Physical Security: Protecting the hardware and infrastructure where data resides, including server rooms, data centers, and employee devices.
Data security is reactive and proactive simultaneously preventing attacks before they happen while also responding effectively when threats materialize.
Key Differences Between Data Privacy and Data Security
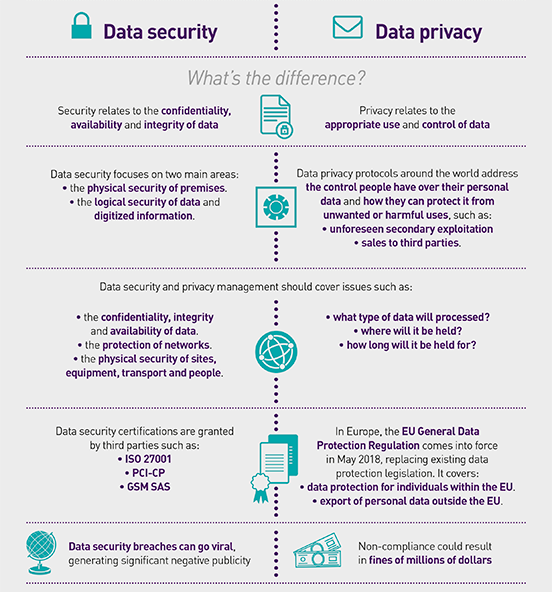
Focus and Objective: Data privacy concerns itself with the appropriate use and governance of personal information. It asks "Should we collect this data?" and "Are we using it properly?" Data security focuses on protecting data from threats and unauthorized access. It asks "Is this data safe?" and "Can we prevent breaches?"
Regulatory vs Technical: Data privacy is heavily regulated by laws like GDPR, CCPA, HIPAA, and other regional regulations that dictate how organizations must handle personal information. Data security, while influenced by regulations, is primarily implemented through technical controls, protocols, and best practices.
Scope of Application: Data privacy specifically deals with personally identifiable information (PII) and sensitive personal data about individuals. Data security applies to all types of data personal, financial, intellectual property, trade secrets, and operational data regardless of whether it relates to individuals.
User Control vs System Protection: Data privacy emphasizes giving individuals control over their information, including the ability to view, correct, or delete it. Data security emphasizes maintaining system integrity and protecting data from external and internal threats, with or without user involvement.
Compliance vs Implementation: Privacy compliance involves policies, procedures, documentation, and demonstrating adherence to legal frameworks. Security implementation involves deploying technologies, configuring systems, and maintaining defenses against evolving threats.
Perspective: Data privacy is often viewed from the data subject's perspective; what rights do individuals have regarding their information? Data security is typically viewed from the organization's perspective, how do we protect our assets and systems?
What Are The Similarities Between Data Privacy and Data Security?
Despite their differences, data privacy and data security are deeply interconnected:
Shared Goal: Both ultimately aim to protect information and maintain trust. Privacy without security is meaningless; if data is easily stolen, privacy rights become theoretical. Similarly, security without privacy considerations can lead to compliant breaches where data is secure but improperly used.
Legal Requirements: Many privacy regulations mandate specific security measures. GDPR, for instance, requires "appropriate technical and organizational measures" to ensure data security. You cannot achieve privacy compliance without implementing proper security.
Risk Management: Both require ongoing risk assessment, identifying vulnerabilities, and implementing controls to mitigate threats; whether those threats come from hackers or from internal misuse of data.
Organizational Culture: Success in both areas requires building a culture of awareness throughout the organization. Employees must understand both their security responsibilities and their privacy obligations.
Continuous Evolution: Both data privacy and data security are moving targets. New threats emerge, regulations evolve, technologies advance, and best practices develop. Organizations must continuously adapt their approaches to both.
Business Impact: Failures in either area can result in significant consequences; financial penalties, reputational damage, loss of customer trust, legal liability, and operational disruption.
Which is More Important to Your Business?
Why You Cannot Choose Just One
Legal Compliance Requires Both: GDPR mandates both appropriate security measures and respect for privacy rights. The California Consumer Privacy Act (CCPA) requires businesses to implement reasonable security procedures while also honoring consumer privacy requests. Violating either aspect can result in substantial fines.
Customer Expectations Have Evolved: Today's consumers expect comprehensive data protection. They want assurance that their information won't be stolen (security) and that it won't be misused or sold without permission (privacy). Meeting only one expectation while failing at the other will erode trust just as quickly.
Breach Impact is Multidimensional: When a data breach occurs, the damage isn't just from the security failure. The privacy implications of whose data was exposed, what information was compromised, how it might be misused often cause the most significant harm to individuals and the most severe consequences for businesses.
Competitive Advantage Demands Both: In industries where trust is paramount; healthcare, finance, legal services and education demonstrating robust data privacy and security practices can differentiate your business from competitors. Conversely, weaknesses in either area can disqualify you from opportunities.
Situational Priorities
While both are essential, certain business contexts may emphasize one aspect more heavily:
Privacy-Focused Scenarios: If you handle sensitive personal information like medical records, financial data, or children's information, privacy compliance becomes especially critical. Healthcare providers under HIPAA, for example, must prioritize patient privacy rights alongside security measures. Marketing companies collecting consumer data must prioritize consent management and purpose limitation.
Security-Focused Scenarios: If you're in critical infrastructure, defense contracting, or handle valuable intellectual property, security often takes center stage because the primary threat is theft or sabotage rather than privacy violations. However, privacy still matters when personal data is involved.
Small Business Considerations: Smaller businesses with limited resources might need to prioritize based on their specific regulatory obligations and risk profile. However, basic security hygiene and privacy-respecting practices should always be baseline requirements, regardless of size.
The Integrated Approach
The most successful organizations recognize that data privacy and data security are complementary, not competing priorities. They implement an integrated approach:
Privacy by Design: Build privacy considerations into systems from the ground up, which naturally incorporates security measures as well.
Security that Enables Privacy: Implement security controls that also facilitate privacy rights; for instance, encryption that protects data while access controls ensure only authorized personnel can view it for legitimate purposes.
Unified Governance: Establish data governance frameworks that address both privacy and security under coordinated leadership, often bringing together Chief Information Security Officers (CISOs) and Data Protection Officers (DPOs).
Holistic Risk Assessment: Evaluate risks from both security and privacy perspectives simultaneously, understanding how threats in one area affect the other.
Combined Training: Educate employees on both security protocols and privacy principles, helping them understand how their daily actions impact both areas.
Integrated Compliance: Develop compliance programs that address both privacy regulations and security standards, avoiding duplicative efforts and ensuring consistency.
The bottom line: prioritize both. Allocate resources to each based on your specific risk profile, regulatory environment, and business model, but never neglect either area. The businesses that thrive in the data-driven economy are those that build comprehensive protection programs encompassing both privacy and security.
Frequently Asked Questions
Q: Can data be secure but not private?
A: Yes, absolutely. Imagine a company that implements strong encryption, firewalls, and access controls (excellent security) but then sells customer data to third parties without consent or uses it for purposes customers didn't agree to (poor privacy). The data is protected from hackers but not from misuse by the company itself.
Q: What happens if my business violates data privacy or security regulations?
A: Consequences vary by jurisdiction and severity but can include substantial fines (GDPR fines can reach up to 4% of annual global revenue), lawsuits from affected individuals, mandatory breach notifications, regulatory audits, injunctions to change practices, reputational damage, and loss of business opportunities. Repeated violations often carry escalating penalties.
Q: How do I know which data privacy laws apply to my business?
A: This depends on where your business operates, where your customers are located, and what type of data you collect. GDPR applies if you have EU customers regardless of where your business is based. CCPA applies to California residents' data. Industry-specific regulations like HIPAA apply based on business type. Consulting with legal experts or compliance specialists is advisable to understand your specific obligations.
Q: Is encryption required for data privacy compliance?
A: While not all privacy laws explicitly mandate encryption, most require "appropriate" or "reasonable" security measures to protect personal data, and encryption is generally considered a fundamental security control. GDPR, for instance, specifically mentions encryption as an example of appropriate security. Many data breach notification laws provide safe harbors if data was encrypted, making it practically essential.
Q: What's the difference between data privacy and data protection?
A: "Data protection" is often used as an umbrella term that encompasses both data privacy and data security. In Europe, data protection legislation (like GDPR) covers both the privacy rights of individuals and the security measures organizations must implement. The terms are sometimes used interchangeably, though data privacy typically has a more specific meaning related to appropriate use and individual rights.
Q: Do small businesses need to worry about data privacy and security?
A: Absolutely. While some regulations have thresholds that exempt very small businesses, most privacy laws apply regardless of size. Small businesses are also increasingly targeted by cybercriminals precisely because they often have weaker security. Additionally, customers expect responsible data handling regardless of business size, and a single breach can be devastating for a small business's reputation and finances.
Q: How often should we review our data privacy and security practices?
A: Regular reviews should occur at least annually, but you should also conduct reviews whenever there are significant changes: implementing new technologies, launching new products or services, entering new markets, experiencing security incidents, or when regulations change. Continuous monitoring of security systems should happen in real-time.
Q: What's the first step in improving our data privacy and security?
A: Start with a comprehensive data inventory and assessment. Understand what data you collect, where it's stored, who has access, how it's used, and what protections are in place. This forms the foundation for identifying gaps, prioritizing improvements, and building a roadmap for enhanced privacy and security.
Conclusion
Data privacy and data security represent two sides of the same coin in our digital economy. While data security builds the protective walls around your information assets, data privacy ensures you're using those assets responsibly and ethically. One without the other leaves your business vulnerable either to external attacks or to regulatory penalties and trust erosion.
The modern business landscape doesn't allow the luxury of choosing between privacy and security. Regulations demand both. Customers expect both. Business resilience requires both. The most successful organizations recognize this reality and build integrated programs that address privacy and security as complementary elements of comprehensive data protection.
As technology evolves and data becomes increasingly central to business operations, the importance of getting both privacy and security right will only intensify. Artificial intelligence, Internet of Things devices, cloud computing, and emerging technologies create new opportunities but also new risks and privacy considerations.
The journey toward robust data privacy and security is an ongoing process of assessment, improvement, and adaptation. It requires leadership commitment, resource investment, cultural change, and continuous vigilance. But the rewards are substantial: compliance with regulations, protection from breaches, customer trust, competitive advantage, and the peace of mind that comes from knowing you're handling one of your most valuable assets with the care and responsibility it deserves.
Ready to strengthen your data protection strategy? Contact Regulance today for a consultation and discover how we can help you build a comprehensive approach to data privacy and security that meets regulatory requirements, protects against threats, and positions your business for success in the data-driven economy.