Cybersecurity vs Information Security: Understanding the Key Differences and How They Protect Your Organization


Introduction
The modern enterprise operates in a digital minefield where a single security misstep can trigger serious consequences costing millions in damages, regulatory penalties, and reputation destruction. As organizations become increasingly dependent on digital infrastructure and data-driven operations, the complexity of protecting valuable assets has reached unprecedented levels. Yet despite this critical importance, widespread confusion continues to plague two fundamental security disciplines that form the backbone of organizational protection: information security and cybersecurity.
This confusion creates tangible operational challenges with serious financial consequences. Organizations frequently misallocate budgets, create redundant security roles, or leave critical gaps in their defense strategies because they lack clarity about these distinct yet interconnected fields. Recent industry surveys reveal that 68% of enterprises struggle to define clear boundaries between information security and cybersecurity responsibilities, leading to inefficient resource deployment and increased vulnerability exposure.
Cyber incidents now cost organizations an average of $4.45 million per breach, while comprehensive security programs that properly integrate both disciplines can reduce this risk by up to 80%. Companies that understand the strategic differences between information security and cybersecurity consistently outperform their peers in threat prevention, incident response, and regulatory compliance.
Information security encompasses the broad protection of all organizational data whether digital, physical, or in transit while cybersecurity focuses specifically on defending digital systems against cyber threats. Both disciplines share common goals but employ different methodologies, tools, and expertise areas.
This definitive guide will eliminate the confusion surrounding these critical security domains, providing clear frameworks for understanding their unique contributions while demonstrating how their strategic integration creates comprehensive organizational resilience in today's complex threat environment.
What is Cybersecurity?
Cybersecurity represents the practice of protecting digital systems, networks, devices, and data from cyberattacks, unauthorized access, and digital threats. This discipline focuses specifically on defending against threats that originate from or target digital environments, including the internet, computer networks, and electronic systems.
Core Components of Cybersecurity
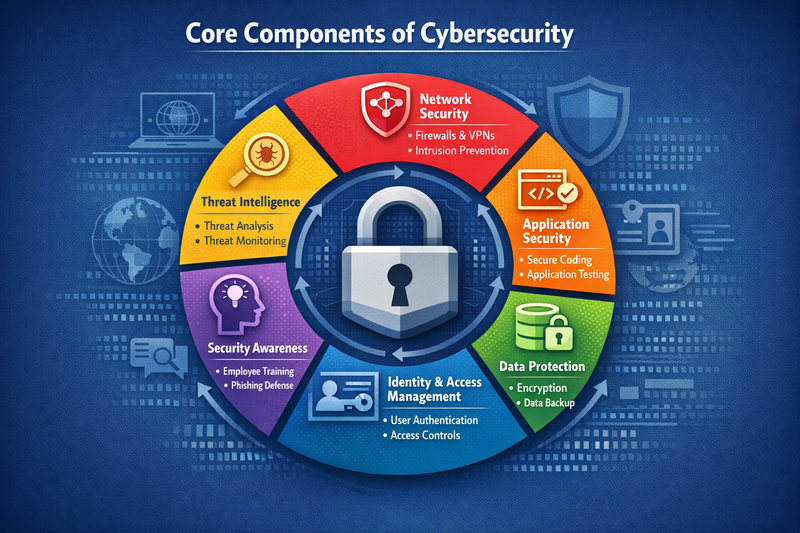
Network Security: This fundamental aspect involves protecting computer networks and network-accessible resources from unauthorized access, misuse, modification, or denial of service. Network security encompasses firewalls, intrusion detection systems, virtual private networks (VPNs), and network segmentation strategies.
Endpoint Security: With the proliferation of devices connecting to organizational networks, endpoint security has become increasingly critical. This component protects individual devices such as computers, smartphones, tablets, and IoT devices from malicious attacks and unauthorized access.
Application Security: As organizations rely heavily on software applications, application security focuses on keeping software and devices free from threats. This includes secure coding practices, regular security testing, and implementing security measures throughout the application lifecycle.
Cloud Security: With the widespread adoption of cloud computing, cloud security has emerged as a specialized cybersecurity domain. It involves protecting data, applications, and infrastructure associated with cloud computing environments.
Identity and Access Management (IAM): This component ensures that only authorized individuals can access specific resources and systems. IAM includes authentication protocols, authorization frameworks, and user access controls.
Cybersecurity Threat Landscape
The cybersecurity threat landscape continues to evolve rapidly, with attackers employing increasingly sophisticated methods. Common cyber threats include malware, ransomware, phishing attacks, distributed denial of service (DDoS) attacks, and advanced persistent threats (APTs).
Cybersecurity professionals must stay current with emerging threats, attack vectors, and defensive technologies. This requires continuous learning, threat intelligence analysis, and adaptation of security measures to address new risks as they emerge.
What is Information Security?
Information security encompasses the broader practice of protecting information assets from unauthorized access, use, disclosure, disruption, modification, or destruction. Unlike cybersecurity, which focuses primarily on digital threats, information security addresses all forms of information, whether digital, physical, or in transit and protects against both digital and physical threats.
Fundamental Principles of Information Security
Information security is built upon three foundational principles known as the CIA Triad:
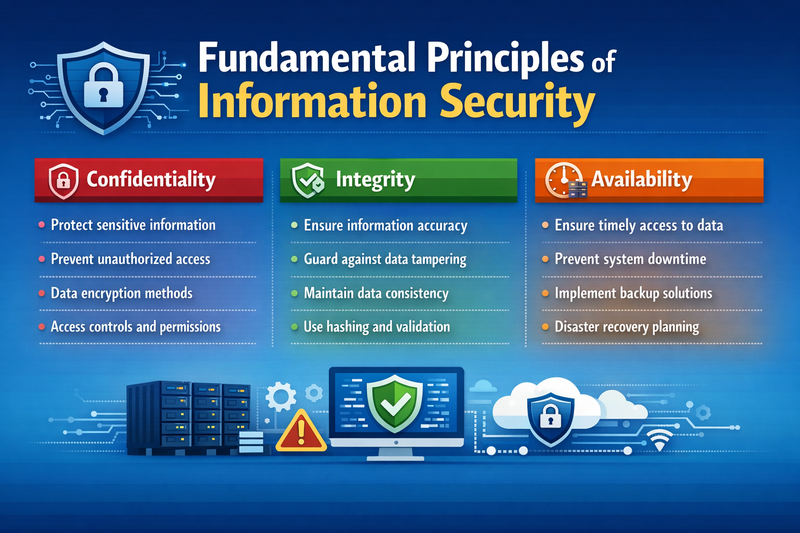
Confidentiality: Ensuring that information is accessible only to those authorized to have access. This principle protects sensitive information from unauthorized disclosure and maintains privacy requirements.
Integrity: Safeguarding the accuracy and completeness of information and processing methods. Integrity ensures that data hasn't been altered, modified, or corrupted by unauthorized parties or processes.
Availability: Ensuring that authorized users have access to information and associated assets when required. This principle focuses on maintaining system uptime and ensuring business continuity.
Information Security Domains
Physical Security: This domain addresses the protection of physical assets, facilities, and resources. It includes access controls for buildings, secure storage of physical documents, environmental controls, and personnel security measures.
Administrative Security: This encompasses the policies, procedures, and guidelines that govern information security within an organization. Administrative security includes security awareness training, incident response procedures, and compliance management.
Technical Security: This domain involves the technological measures used to protect information systems and data. Technical security includes encryption, access controls, authentication systems, and security monitoring tools.
Operational Security: This focuses on the processes and procedures for handling and protecting sensitive information during daily operations. Operational security includes data classification, secure communication protocols, and information handling procedures.
Information Assets and Classification
Information security recognizes that organizations possess various types of information assets, each requiring different levels of protection. These assets include intellectual property, customer data, financial records, strategic plans, and employee information.
Effective information security requires classifying these assets based on their sensitivity, value to the organization, and potential impact if compromised. This classification drives the implementation of appropriate security controls and protection measures.
Information Security vs Cybersecurity: Key Differences
Understanding the distinctions between information security and cybersecurity is essential for developing comprehensive organizational protection strategies. While these disciplines overlap significantly, they have distinct focuses, scopes, and methodologies.
Scope and Coverage
Information Security Scope: Information security takes a holistic approach, addressing all forms of information regardless of format or storage method. This includes digital files, printed documents, verbal communications, and any other form of information that has value to the organization.
Information security considers threats from multiple vectors, including physical theft, social engineering, insider threats, natural disasters, and human error. The scope extends beyond technology to encompass people, processes, and physical environments.
Cybersecurity Scope: Cybersecurity focuses specifically on protecting digital assets and defending against cyber threats. The scope is primarily technological, addressing threats that target computer systems, networks, and digital data.
Cybersecurity concentrates on threats originating from or targeting digital environments, including malware, hacking attempts, cyber espionage, and online fraud. The discipline is inherently technical and technology-focused.
Threat Focus and Attack Vectors
Information Security Threats: Information security addresses a broad spectrum of threats, including both intentional and unintentional risks. These threats encompass cyber attacks, physical theft, natural disasters, human error, insider threats, and social engineering attacks.
The discipline recognizes that information can be compromised through various means, not just digital attacks. For example, sensitive information can be exposed through dumpster diving, shoulder surfing, or inadequate physical security measures.
Cybersecurity Threats: Cybersecurity specifically targets digital threats and attack vectors. These include malware infections, network intrusions, data breaches through digital means, denial of service attacks, and exploitation of software vulnerabilities.
Cybersecurity threats are typically characterized by their digital nature and often involve sophisticated technical methods to compromise systems or steal digital information.
Methodological Approaches
Information Security Methodology: Information security employs comprehensive risk management approaches that consider all aspects of information protection. This includes conducting thorough risk assessments that evaluate physical, technical, and administrative risks.
The methodology emphasizes policy development, procedure implementation, and creating comprehensive security frameworks that address all information assets and potential threats.
Cybersecurity Methodology: Cybersecurity methodologies focus on technical implementation and digital threat response. This includes continuous monitoring of digital systems, threat intelligence analysis, and rapid response to cyber incidents.
The approach is often more tactical and technical, emphasizing real-time threat detection, incident response, and technical countermeasures.
Regulatory and Compliance Considerations
Information Security Compliance: Information security must address a broad range of regulatory requirements that govern information protection across various industries. This includes privacy regulations like GDPR and CCPA, industry-specific requirements like HIPAA for healthcare, and financial regulations like SOX and PCI DSS.
Compliance considerations extend beyond technical controls to include administrative procedures, physical security measures, and comprehensive documentation requirements.
Cybersecurity Compliance: While cybersecurity also addresses regulatory requirements, the focus is primarily on technical controls and digital security measures. Cybersecurity compliance often centers on specific technical standards and frameworks designed to address cyber threats.
How Cybersecurity and Information Security Work Together to Protect Your Organization
Rather than competing disciplines, cybersecurity and information security function as complementary components of a comprehensive organizational protection strategy. Their integration creates layered defense mechanisms that address both digital and physical threats while ensuring comprehensive information protection.
Creating Comprehensive Defense Strategies
Layered Security Architecture: The most effective organizational protection combines information security's comprehensive risk management approach with cybersecurity's technical expertise. This creates multiple layers of protection that address various threat vectors and attack methods.
For example, protecting customer data requires technical cybersecurity measures like encryption and access controls, combined with information security elements like employee training, physical security controls, and comprehensive policies and procedures.
Risk Management Integration: Information security's broad risk management perspective provides the framework for identifying and assessing all potential threats to organizational information. Cybersecurity contributes specialized knowledge about digital threats and technical countermeasures.
This integration ensures that organizations don't overlook either traditional security risks or emerging cyber threats. The combination provides a more complete picture of the organization's risk landscape.
Organizational Structure and Team Collaboration
Unified Security Teams: Many organizations are moving toward unified security teams that combine information security and cybersecurity expertise. This approach ensures that security professionals understand both the broad organizational context and specific technical threats.
Specialized Roles with Shared Objectives: Organizations may maintain separate information security and cybersecurity teams while ensuring close collaboration and shared objectives. This structure allows for specialized expertise while maintaining comprehensive protection coverage.
Cross-Training and Knowledge Sharing: Successful organizations invest in cross-training their security professionals to understand both information security principles and cybersecurity technical details. This creates more versatile teams capable of addressing complex, multi-faceted security challenges.
Technology and Process Integration
Unified Security Platforms: Modern security technologies increasingly integrate both information security and cybersecurity capabilities. Security information and event management (SIEM) systems, for example, can monitor both physical access controls and network security events.
Integrated Incident Response: Effective incident response procedures must address both information security and cybersecurity aspects of security incidents. A data breach, for instance, may involve both technical cybersecurity response and broader information security considerations like regulatory notification requirements.
Comprehensive Governance: Organizations benefit from governance frameworks that address both information security and cybersecurity requirements. This ensures consistent policies, procedures, and standards across all security domains.
Addressing Modern Threat Landscapes
Hybrid Threats: Modern threats often combine both digital and physical elements, requiring coordinated information security and cybersecurity responses. Social engineering attacks, for example, may use both digital and physical tactics to compromise organizational information.
Supply Chain Security: Protecting organizational information in complex supply chain environments requires both cybersecurity measures to secure digital connections and information security controls to manage information sharing with third parties.
Remote Work Security: The shift to remote work has created new security challenges that require both information security and cybersecurity solutions. Organizations must address both the technical security of remote connections and the broader information security implications of distributed work environments.
Frequently Asked Questions (FAQs)
Is cybersecurity part of information security?
Cybersecurity is generally considered a subset of information security, focusing specifically on digital threats and technical protection measures. Information security encompasses cybersecurity while also addressing physical security, administrative controls, and non-digital information protection. However, cybersecurity has grown into a specialized discipline with its own expertise, tools, and methodologies.
Which career path offers better opportunities: information security or cybersecurity?
Both fields offer excellent career opportunities, but they appeal to different skill sets and interests. Cybersecurity careers tend to be more technical and specialized, often offering higher starting salaries for technical roles. Information security careers often provide broader organizational exposure and may lead to senior management positions. The best choice depends on your interests, technical aptitude, and career goals.
Do I need both information security and cybersecurity for my small business?
Small businesses need elements of both disciplines, though they may not require separate specialists. Start by understanding your information assets and potential threats, then implement appropriate technical cybersecurity measures and broader information security policies. Many small businesses benefit from managed security services that provide both cybersecurity monitoring and information security guidance.
How do compliance requirements differ between information security and cybersecurity?
Information security compliance typically addresses broader regulatory requirements that govern all forms of information protection, including privacy laws, industry-specific regulations, and comprehensive security frameworks. Cybersecurity compliance often focuses on technical standards and specific security controls. However, most modern compliance requirements integrate both perspectives.
What's the difference between information security and data security?
Data security specifically focuses on protecting data assets, whether digital or physical. Information security is broader, encompassing all information assets and considering people, processes, and technology. Data security is essentially a component of information security, while cybersecurity addresses the technical aspects of protecting digital data.
Can artificial intelligence help with both information security and cybersecurity?
Yes, AI technologies are increasingly valuable for both disciplines. In cybersecurity, AI helps with threat detection, malware analysis, and automated incident response. For information security, AI can assist with risk assessment, compliance monitoring, and identifying potential information security policy violations. The key is implementing AI solutions that address your specific security challenges.
How do I know which security framework is right for my organization?
The choice depends on your industry, regulatory requirements, organizational size, and risk profile. Frameworks like ISO 27001 address comprehensive information security, while others like NIST Cybersecurity Framework focus more on cybersecurity. Many organizations benefit from hybrid approaches that incorporate elements from multiple frameworks to address their specific needs.
Conclusion
The distinction between information security and cybersecurity has practical implications for how organizations protect their most valuable assets. Understanding these differences enables better resource allocation, more effective security strategies, and comprehensive risk management.
Information security provides the broad foundation for protecting all organizational information assets, establishing policies, procedures, and frameworks that address comprehensive risk management. Cybersecurity contributes specialized technical expertise essential for defending against sophisticated digital threats in our interconnected world.
The most successful organizations recognize that information security and cybersecurity are complementary disciplines that work together to create comprehensive protection strategies. Rather than choosing between these approaches, forward-thinking organizations integrate both perspectives to address the full spectrum of modern security challenges.
As threats continue to evolve and organizations become increasingly digital, the lines between information security and cybersecurity may continue to blur. However, the fundamental principles of each discipline remain valuable. Information security's comprehensive risk management approach provides essential organizational context, while cybersecurity's technical focus addresses the sophisticated digital threats that define modern risk landscapes.
The key to success lies in understanding both disciplines, recognizing their unique contributions, and implementing integrated approaches that leverage the strengths of each. Whether you're a small business owner seeking to protect customer information or a large organization managing complex security challenges, combining information security principles with cybersecurity expertise provides the comprehensive protection necessary for today's threat environment.
By embracing both information security and cybersecurity as essential components of organizational protection, you can build resilient defenses that protect your information assets, maintain stakeholder trust, and ensure business continuity in an increasingly complex and threatening digital world
Still Managing Information Security and Cybersecurity Separately? Start integrating your information security and cybersecurity with Regulance today.