Cybersecurity Essentials: What Every Business Should Know


Introduction
In today's interconnected digital landscape, cybersecurity has evolved from a technical afterthought to a business-critical necessity. Whether you're running a Fortune 500 company, managing a small startup, or simply navigating personal digital activities, understanding cybersecurity fundamentals is essential for survival in the digital age.
The cybersecurity landscape is constantly shifting, with new threats emerging daily and attack methods becoming increasingly sophisticated. Cybercriminals are no longer lone hackers working from basements; they're organized crime syndicates, nation-state actors, and well-funded groups targeting everything from personal bank accounts to critical infrastructure. The statistics paint a sobering picture: cyberattacks occur every 39 seconds, and the average cost of a data breach reached $4.45 million in 2023.
Most cyberattacks succeed because of preventable mistakes, not unstoppable technical wizardry. Understanding cybersecurity basics and implementing fundamental protective measures can dramatically reduce your risk profile. This comprehensive guide will demystify cybersecurity, breaking down complex concepts into actionable insights that anyone can understand and implement.
Why Cybersecurity Actually Matters
Cybersecurity is about safeguarding the three foundational pillars of digital security: confidentiality, integrity, and availability. These pillars, known as the CIA Triad in cybersecurity circles, form the backbone of every security strategy.
Confidentiality ensures that sensitive information remains accessible only to authorized individuals. When this fails, private medical records, financial data, trade secrets, or personal communications can fall into the wrong hands. Integrity guarantees that information remains accurate and unaltered during storage and transmission. Compromised integrity might mean altered financial records, modified contracts, or corrupted research data. Availability ensures that systems, applications, and data remain accessible when legitimate users need them. Availability breaches result in system downtime, service interruptions, and operational paralysis.
The Real-World Impact of Cybersecurity Failures
Personal Safety and Privacy: Identity theft affects millions annually, with victims spending an average of 16 hours and $1,343 recovering from each incident. Cybercriminals use stolen personal information to open credit accounts, file fraudulent tax returns, access medical services, and even commit crimes using your identity. The emotional toll often exceeds the financial damage, with victims reporting anxiety, depression, and long-term trust issues.
Business Continuity and Financial Stability: Ransomware attacks have brought entire city governments, hospital systems, and manufacturing plants to standstill. The average ransomware recovery cost exceeds $4.54 million, not including ransom payments. Beyond immediate costs, businesses face extended downtime, lost productivity, customer defection, and long-term reputational damage. Small businesses are particularly vulnerable—60% close permanently within six months of a significant cyberattack.
Trust and Reputation Management: Consumer trust, built over years, can evaporate overnight following a data breach. Studies show that 65% of consumers lose trust in breached organizations, and 27% stop doing business with them entirely. Professional relationships suffer similarly, with partners questioning your organization's competence and reliability. Rebuilding reputation requires years of consistent performance and transparent communication.
Legal and Regulatory Compliance: Modern businesses operate under increasingly stringent data protection regulations. The General Data Protection Regulation (GDPR) can impose fines up to 4% of annual global turnover. Healthcare organizations face HIPAA penalties reaching $1.5 million per incident. Beyond fines, regulatory investigations consume executive time, require legal counsel, and often mandate expensive remediation measures.
Competitive Advantage and Market Position: Organizations demonstrating robust cybersecurity practices win larger contracts, attract security-conscious customers, and command premium pricing for their services. Government contractors require specific cybersecurity certifications. Enterprise customers increasingly audit vendor security practices before signing agreements. Strong cybersecurity becomes a market differentiator, opening doors to opportunities unavailable to less secure competitors.
Types of Cybersecurity Tools (and what problem each one solves)
The cybersecurity tool ecosystem can seem overwhelming, with vendors offering hundreds of solutions claiming to solve every conceivable security problem. Understanding tool categories, their specific purposes, and how they work together creates a foundation for building effective security programs.
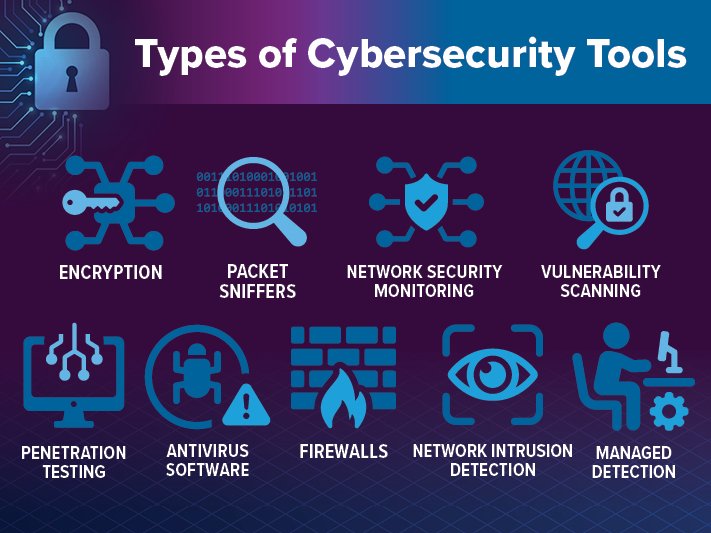
Foundation Layer Tools
Firewalls: Think of firewalls as intelligent security guards for your network perimeter. Modern firewalls examine incoming and outgoing traffic, comparing it against predefined security rules. Next-generation firewalls (NGFWs) go beyond simple port blocking, incorporating application awareness, intrusion prevention, and malware detection. They're your first line of defense, blocking obvious threats and controlling which applications can communicate across network boundaries.
Antivirus and Endpoint Protection Platforms (EPP): Traditional antivirus software has evolved into comprehensive endpoint protection platforms that combine signature-based detection with behavioral analysis, machine learning, and cloud-based threat intelligence. These tools monitor individual devices—laptops, desktops, servers, and mobile devices—scanning files, monitoring process behavior, and blocking malicious activities before they can cause damage.
Multi-Factor Authentication (MFA): MFA addresses the fundamental weakness of password-only authentication by requiring multiple verification factors. Something you know (password), something you have (smartphone or token), and something you are (biometric data) create authentication layers that are exponentially more difficult for attackers to bypass. Modern MFA solutions include push notifications, biometric authentication, and hardware security keys.
Encryption Technologies: Encryption transforms readable data into scrambled information that requires specific keys to decode. Data encryption occurs in two primary states: at rest (stored data) and in transit (data moving across networks). Modern encryption standards like AES-256 provide mathematical security that would take current computers billions of years to crack through brute force attacks.
Advanced Detection and Response Tools
Security Information and Event Management (SIEM): SIEM platforms aggregate security logs from across your entire technology infrastructure, correlating events to identify potential security incidents. They function as cybersecurity command centers, providing centralized visibility into security events, automated alerting for suspicious activities, and forensic capabilities for incident investigation.
Endpoint Detection and Response (EDR): EDR solutions provide deep visibility into endpoint activities, continuously monitoring for signs of advanced threats that traditional antivirus might miss. They record detailed system activities, enabling security teams to trace attack progression, understand threat actor techniques, and respond effectively to sophisticated attacks.
Network Monitoring and Intrusion Detection/Prevention Systems (IDS/IPS): These tools analyze network traffic patterns, identifying anomalies that might indicate cyberattacks. IDS solutions detect and alert on suspicious activities, while IPS solutions can automatically block identified threats. Modern solutions incorporate machine learning to establish baseline network behavior and identify deviations that traditional signature-based detection might miss.
Operational Security Tools
Patch Management and Update Systems: Cybercriminals frequently exploit known vulnerabilities in unpatched software. Automated patch management systems inventory software across your environment, identify available security updates, test patches in controlled environments, and deploy them systematically. Effective patch management reduces your attack surface by closing known security gaps.
Backup and Disaster Recovery Solutions: Comprehensive backup strategies protect against ransomware, hardware failures, natural disasters, and human error. Modern backup solutions provide automated scheduling, encryption in transit and at rest, immutable backup copies, and rapid recovery capabilities. Regular testing ensures backups work when needed most.
Vulnerability Scanners and Penetration Testing: These proactive security measures identify weaknesses before attackers can exploit them. Vulnerability scanners automatically inventory systems and identify known security weaknesses, while penetration testing involves skilled security professionals attempting to breach your defenses using real-world attack techniques.
Specialized Security Categories
Cloud Security Tools: Cloud Access Security Brokers (CASB) and Cloud Workload Protection Platforms (CWPP) address unique cloud security challenges. They provide visibility into cloud service usage, enforce security policies across cloud environments, and protect cloud-native applications and infrastructure.
Identity and Access Management (IAM): IAM systems control who can access what resources under what circumstances. They enforce the principle of least privilege, ensuring users have only the minimum access required for their job functions. Advanced IAM includes single sign-on (SSO), privileged access management (PAM), and identity governance capabilities.
Benefits of Cybersecurity
Investing in cybersecurity delivers measurable returns across multiple dimensions, transforming security from a cost center into a value generator for organizations and individuals alike.
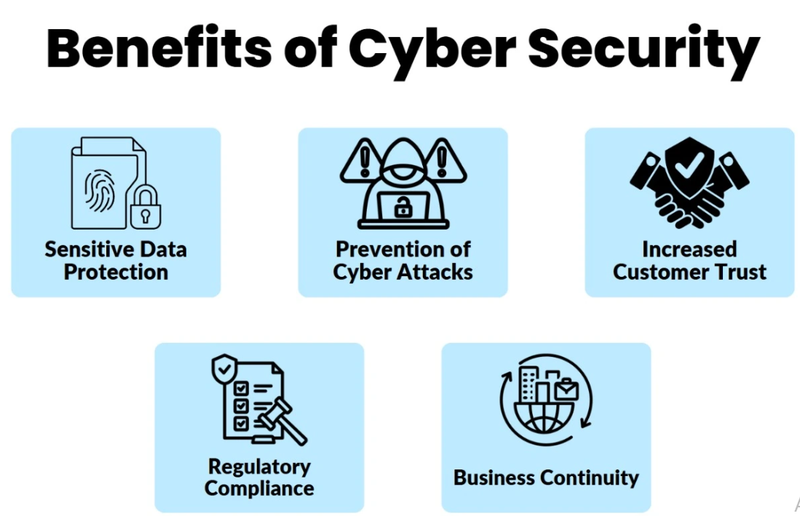
Financial Protection and Predictability
Robust cybersecurity programs dramatically reduce financial losses from cyberattacks. Organizations with comprehensive security programs experience 58% fewer high-severity incidents and recover 30% faster when incidents occur. The math is compelling: spending $1 on preventive security measures typically saves $5-7 in incident response and recovery costs.
Cybersecurity investments provide cost predictability by converting unpredictable catastrophic losses into manageable, budgeted expenses. Rather than facing surprise six-figure incident response bills, organizations can budget for security tools, training, and services. Cyber insurance premiums also decrease for well-secured organizations, further improving financial predictability.
Operational Excellence and Resilience
Strong cybersecurity foundations enable operational resilience that extends far beyond security benefits. Organizations with mature security programs report higher system availability, fewer unexpected outages, and more predictable performance. Security practices like regular backups, system monitoring, and change management improve overall operational stability.
Incident response capabilities developed for cybersecurity translate directly to faster recovery from any operational disruption. Teams trained to respond quickly to security incidents apply the same structured approaches to system failures, natural disasters, or supply chain disruptions.
Innovation Enablement and Competitive Advantage
Paradoxically, strong security enables faster innovation by providing safe frameworks for experimenting with new technologies. Organizations with robust security programs adopt cloud services, IoT devices, and emerging technologies more quickly because they have frameworks for managing associated risks.
Security becomes a competitive differentiator in business development. Enterprise customers increasingly require vendor security assessments, and many contracts include specific security requirements. Government contracts often mandate cybersecurity certifications like FedRAMP or CMMC compliance. Organizations that invest early in security capabilities access opportunities unavailable to less secure competitors.
Regulatory Compliance and Risk Management
Comprehensive cybersecurity programs simplify regulatory compliance across multiple frameworks. Security controls implemented for GDPR compliance often satisfy HIPAA, SOX, or industry-specific requirements. Mature security programs include documentation, monitoring, and reporting capabilities that streamline audit processes and reduce compliance costs.
Beyond avoiding penalties, proactive compliance positions organizations for international expansion and partnership opportunities. Many global markets require specific privacy and security certifications, making compliance investments enablers for growth rather than mere cost centers.
Customer Confidence and Brand Value
Security transparency builds customer confidence and brand value. Organizations that openly discuss their security practices, obtain relevant certifications, and demonstrate commitment to protection attract security-conscious customers willing to pay premiums for trusted providers.
Customer data protection becomes a brand differentiator in competitive markets. Companies known for strong security practices enjoy higher customer retention rates, positive word-of-mouth marketing, and reduced customer acquisition costs. Security incidents that might destroy lesser-prepared organizations become manageable events for those with strong security reputations.
Frequently Asked Questions
Q: Is antivirus enough to protect me?
A: No. While antivirus remains important, modern threats require layered defenses. Sophisticated attacks often bypass traditional antivirus through social engineering, zero-day exploits, or living-off-the-land techniques. Combine antivirus with MFA, regular patching, secure backups, user training, and behavioral monitoring for comprehensive protection.
Q: What's the most common way attackers gain access?
A: Password-related attacks represent the most common entry point, including credential stuffing (using leaked passwords), phishing to steal credentials, and brute force attacks against weak passwords. Email phishing remains highly effective, with 83% of organizations reporting phishing attempts in 2023. Unpatched software vulnerabilities provide another common attack vector, particularly in internet-facing applications.
Q: How often should I back up?
A: Backup frequency depends on data change rates and recovery tolerance. Most businesses should backup daily, with critical systems requiring more frequent backups. The 3-2-1 rule provides a good framework: maintain 3 copies of important data, store them on 2 different media types, and keep 1 copy offsite. Always test restore procedures regularly, untested backups often fail when needed most.
Q: Are cloud services secure?
A: Cloud services follow a shared responsibility model. Cloud providers secure the underlying infrastructure, but customers remain responsible for configuring services securely, managing access controls, and protecting their data. Major cloud providers invest billions in security and often provide better protection than most organizations could achieve independently, but proper configuration and management remain customer responsibilities.
Q: How much should a small business spend on cybersecurity?
A: Small businesses typically spend 3-9% of IT budgets on cybersecurity, varying by industry and risk profile. Start with essential controls: MFA for all accounts, regular automated backups, endpoint protection, regular patching, and basic security training. These fundamentals provide significant protection at relatively low cost. Scale spending based on risk assessment, compliance requirements, and the value of protected assets.
Q: What is ransomware and how do I defend against it?
A: Ransomware encrypts your files and demands payment for decryption keys. However, paying ransoms doesn't guarantee data recovery and funds criminal organizations. Defense requires multiple layers: regular tested backups stored offline, employee training to recognize phishing, prompt patching, endpoint detection and response tools, network segmentation, and incident response planning. Cyber insurance can help with recovery costs but shouldn't replace preventive measures.
Conclusion
Cybersecurity effectiveness stems from integration into daily operations rather than treatment as a separate, technical concern. The most successful security programs focus on reducing easy wins for attackers through consistent application of fundamental security practices. Strong unique passwords, multi-factor authentication, timely software updates, regular backups, and security-aware behavior provide substantial protection against the vast majority of cyber threats.
As organizations mature, they layer additional capabilities like continuous monitoring, advanced threat detection, identity management, and formal incident response processes. However, advanced tools should complement, not replace, security fundamentals. Many organizations with expensive security technologies fall victim to attacks that basic security hygiene would have prevented.
The cybersecurity landscape will continue evolving, with artificial intelligence, quantum computing, and emerging technologies creating new opportunities and threats. But the core principles remain constant: understand your valuable assets, know your threats, implement appropriate controls, and continuously improve your security posture.
Ready to protect your business? Start applying Cybersecurity Essentials today with Regulance and stay ahead of threats.