Common Security Frameworks: Your Complete Guide to Protecting Your Business in 2025


Introduction
Cybersecurity isn't just an IT concern, it's a business imperative. With cyber attacks costing companies an average of $4.45 million per breach, implementing robust security frameworks has become crucial for survival. But with dozens of frameworks available, how do you choose the right one for your organization?
This comprehensive guide breaks down the most effective security frameworks, explaining what they are, how to implement them, and why they're essential for your business success.
What Are Security Frameworks?
Security frameworks are structured sets of guidelines, best practices, and standards designed to help organizations manage cybersecurity risks effectively. They are blueprints that provide a systematic approach to identifying vulnerabilities, implementing controls, and maintaining security posture.
These frameworks serve as roadmaps, helping businesses navigate the complex world of cybersecurity without having to reinvent the wheel. They offer proven methodologies developed by security experts and tested across thousands of organizations worldwide.
The Top Security Frameworks Every Business Should Know
1. NIST Cybersecurity Framework (CSF)
Developed by the National Institute of Standards and Technology, the NIST CSF is arguably the most widely adopted security framework globally. It provides a flexible, risk-based approach to cybersecurity that works for organizations of all sizes.
The Five Core Functions:
- Identify: Understand your business context, resources, and risks
- Protect: Implement safeguards to ensure critical services
- Detect: Develop activities to identify cybersecurity events
- Respond: Take action when incidents occur
- Recover: Maintain resilience and restore capabilities
How to achieve it: Start by conducting a comprehensive asset inventory and risk assessment. Map your current security practices to the framework's subcategories, identify gaps, and create a prioritized implementation plan. Focus on quick wins first—like employee training and basic access controls—before tackling more complex requirements.
Why it's important: The NIST CSF's flexibility makes it perfect for businesses just starting their security journey. It's industry-agnostic, cost-effective, and provides a common language for discussing cybersecurity across your organization. Plus, many compliance requirements reference NIST standards, making it a smart foundation choice.
2. ISO 27001
ISO 27001 is an international standard that provides requirements for establishing, implementing, maintaining, and continually improving an Information Security Management System (ISMS). It's the gold standard for information security certification.
How to achieve it: Begin with leadership commitment and appoint an information security officer. Conduct a thorough risk assessment, develop security policies and procedures, and implement appropriate controls from the ISO 27001 Annex A catalog. Regular internal audits and management reviews are essential for maintaining certification.
Why it's important: ISO 27001 certification demonstrates to customers, partners, and stakeholders that you take security seriously. It's often required for government contracts and can provide competitive advantages in B2B markets. The systematic approach also helps reduce insurance premiums and regulatory compliance costs.
3. SOC 2 (Service Organization Control 2)
SOC 2 is an auditing procedure that ensures service providers securely manage data to protect client organizations and their customers' interests. It focuses on five trust service criteria: security, availability, processing integrity, confidentiality, and privacy.
How to achieve it: Start by defining your system boundaries and selecting relevant trust service criteria. Implement appropriate controls, document your processes thoroughly, and engage a qualified CPA firm to conduct the audit. Type I reports assess design effectiveness, while Type II reports evaluate operational effectiveness over time.
Why it's important: SOC 2 compliance is increasingly mandatory for SaaS companies and cloud service providers. It builds customer trust, enables enterprise sales, and demonstrates your commitment to protecting sensitive data. Many large organizations won't work with vendors who lack SOC 2 certification.
4. PCI DSS (Payment Card Industry Data Security Standard)
PCI DSS is a comprehensive security standard designed to protect cardholder data. Any organization that processes, stores, or transmits credit card information must comply with these requirements.
The 12 Core Requirements:
- Install and maintain firewalls
- Avoid default passwords and security parameters
- Protect stored cardholder data
- Encrypt data transmission across public networks
- Use and regularly update anti-virus software
- Develop and maintain secure systems
- Restrict access by business need-to-know
- Assign unique IDs to each computer user
- Restrict physical access to cardholder data
- Track and monitor all network access
- Regularly test security systems
- Maintain information security policies
How to achieve it: Begin with a detailed scope assessment to understand which systems handle cardholder data. Implement network segmentation to isolate payment processing systems, deploy appropriate security controls, and establish regular vulnerability scanning and penetration testing programs.
Why it's important: PCI DSS compliance isn't optional—it's legally required for payment processing. Non-compliance can result in hefty fines, increased processing fees, and potential loss of payment processing privileges. A single data breach can cost millions in fines and reputation damage.
5. HIPAA Security Rule
The Health Insurance Portability and Accountability Act (HIPAA) Security Rule establishes national standards for protecting electronic health information. It applies to covered entities and their business associates in the healthcare industry.
How to achieve it: Conduct a comprehensive risk assessment of all systems handling PHI (Protected Health Information). Implement administrative safeguards like security officer designation and workforce training, physical safeguards such as facility access controls, and technical safeguards including access control and audit controls.
Why it's important: HIPAA violations can result in fines ranging from $100 to $50,000 per violation, with annual maximums reaching $1.5 million. Beyond financial penalties, breaches damage patient trust and can lead to lawsuits and reputation destruction in the healthcare industry.
6. CIS Controls (Center for Internet Security)
The CIS Controls are a prioritized set of 18 security safeguards designed to stop the most common cyber attacks. They're organized into Implementation Groups based on organizational size and resources.
The Top 6 CIS Controls:
- Inventory and control of enterprise assets
- Inventory and control of software assets
- Data protection
- Secure configuration of enterprise assets
- Account management
- Access control management
How to achieve it: Start with Implementation Group 1 (IG1) controls if you're a small organization, focusing on basic cyber hygiene. Gradually progress to IG2 and IG3 as your security maturity increases. Use the CIS-RAM (Risk Assessment Method) to prioritize implementations based on your specific risk profile.
Why it's important: CIS Controls provide the highest-impact security practices in a prioritized, easy-to-follow format. They're developed by practitioners for practitioners, making them practical and actionable for organizations with limited security resources.
7. GDPR Compliance Framework: Respecting Privacy Rights
The General Data Protection Regulation (GDPR) isn't just a European concern—it applies to any business processing EU residents' personal data, regardless of where your company is located. With fines reaching 4% of annual revenue or €20 million (whichever is higher), GDPR compliance is serious business.
How to Achieve It
GDPR compliance requires a privacy-by-design approach:
Data Mapping: Document what personal data you collect, where it's stored, how it's processed, and who has access to it.
Legal Basis: Establish lawful grounds for processing personal data, whether through consent, contract necessity, or legitimate interests.
Privacy Controls: Implement technical and organizational measures to protect personal data, including encryption, access controls, and data minimization.
Rights Management: Create processes to handle data subject requests for access, rectification, erasure, and portability within required timeframes.
Breach Response: Develop procedures to detect, report, and investigate personal data breaches within 72 hours.
Documentation: Maintain records of processing activities and conduct privacy impact assessments for high-risk processing.
Why Your Business Needs It
GDPR compliance isn't just about avoiding fines—it builds customer trust and provides competitive advantages. Studies show 86% of consumers care about data privacy, and GDPR-compliant businesses see 23% higher customer retention rates. The framework also prepares you for similar privacy regulations emerging worldwide.
8. COBIT: Governance and Management Excellence
Control Objectives for Information and Related Technologies (COBIT) bridges the gap between technical security measures and business objectives. It's particularly valuable for organizations needing to demonstrate IT governance to stakeholders, regulators, and auditors.
How to Achieve It
COBIT implementation follows a holistic approach:
Governance Framework: Establish clear roles, responsibilities, and decision-making processes for IT governance at board and executive levels.
Management Practices: Implement 40 management practices across five domains: Evaluate, Direct and Monitor (EDM), Align, Plan and Organize (APO), Build, Acquire and Implement (BAI), Deliver, Service and Support (DSS), and Monitor, Evaluate and Assess (MEA).
Capability Assessment: Regularly assess the maturity of your IT processes using COBIT's capability model, identifying areas for improvement.
Performance Management: Define key performance indicators (KPIs) and metrics that align IT performance with business objectives.
Risk Optimization: Balance IT risk, resource investment, and value creation through structured decision-making processes.
Why Your Business Needs It
COBIT helps organizations optimize IT investments and demonstrate value to stakeholders. Companies implementing COBIT report 30% better IT project success rates and 25% improved regulatory compliance scores. It's particularly valuable for publicly traded companies needing to satisfy Sarbanes-Oxley requirements or similar governance regulations.
9. Zero Trust Architecture: Never Trust, Always Verify
Zero Trust isn't a single product or technology—it's a security philosophy that assumes no user or device should be trusted by default, regardless of location or credentials. In an era of remote work and cloud computing, Zero Trust represents the future of cybersecurity.
How to Achieve It
Implementing Zero Trust requires a fundamental shift in security thinking:
Identity Verification: Implement strong authentication mechanisms, including multi-factor authentication (MFA) and risk-based authentication for all users and devices.
Least Privilege Access: Grant users the minimum access necessary to perform their jobs, regularly reviewing and adjusting permissions based on role changes.
Network Segmentation: Create micro-segments within your network to limit lateral movement if attackers gain initial access.
Continuous Monitoring: Deploy advanced analytics and AI-powered tools that continuously assess user behavior, device health, and network traffic for anomalies.
Encryption Everywhere: Encrypt data at rest, in transit, and in use, ensuring information remains protected even if perimeter defenses are breached.
Device Trust: Implement device management solutions that ensure only compliant, managed devices can access corporate resources.
Why Your Business Needs It
Zero Trust architecture reduces breach impact by 90% and detection time by 200 days compared to traditional perimeter-based security. With remote work becoming permanent for many organizations, Zero Trust enables secure access from anywhere while maintaining strict security controls. Forward-thinking companies implementing Zero Trust report 50% fewer successful attacks and 40% lower security operational costs.
The Business Case: Why Security Frameworks Aren't Just IT's Problem
Risk Reduction That Actually Works
Security frameworks provide a systematic approach to identifying and mitigating risks. Instead of playing cybersecurity whack-a-mole, you're building comprehensive defenses based on proven methodologies.
Competitive Advantage in Disguise
While your competitors are scrambling to answer security questionnaires, you'll be confidently sharing compliance certificates and detailed security reports. Framework compliance often becomes a differentiator in competitive sales situations.
Cost Savings Through Prevention
The average cost of a data breach in 2024 reached $4.45 million. Compare that to the cost of framework implementation (typically $50,000-$200,000 for mid-sized companies), and the ROI becomes crystal clear.
Regulatory Readiness
Many regulations reference established frameworks. GDPR, HIPAA, and state privacy laws often require "appropriate technical and organizational measures"—frameworks provide the roadmap for achieving compliance.
Insurance Benefits
Cyber insurance providers increasingly offer premium discounts for framework compliance. Some policies even require specific certifications, making frameworks not just protective but financially beneficial.
Choosing the Right Framework for Your Business
The best security framework depends on your industry, size, regulatory requirements, and risk tolerance. Many organizations successfully combine multiple frameworks:
- Startups and SMBs: Begin with NIST CSF for foundational security, add industry-specific requirements as needed
- Healthcare organizations: HIPAA compliance is mandatory, supplemented with NIST CSF for comprehensive coverage
- Financial services: Combine SOC 2, PCI DSS, and industry-specific regulations
- Government contractors: NIST frameworks with additional federal requirements
- SaaS companies: SOC 2 Type II with NIST CSF for operational security
Getting Started: Your Framework Implementation Roadmap
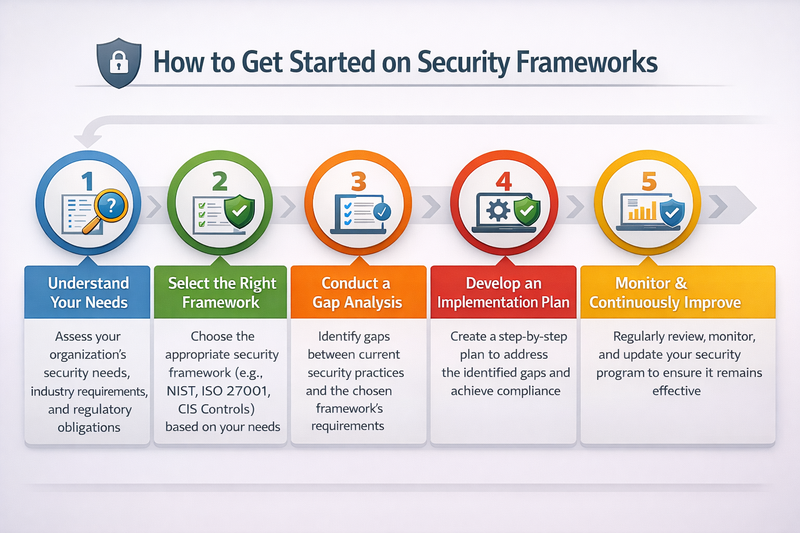
Step 1: Assess Your Current State
Before choosing a framework, understand where you stand today. Conduct a security assessment to identify existing controls, gaps, and risks. This baseline helps you choose the most appropriate framework and measure progress.
Step 2: Choose Your Framework
Consider your industry, customer requirements, regulatory obligations, and resources. Many organizations start with NIST CSF for its flexibility, then layer on specific requirements like SOC 2 or ISO 27001 as needed.
Step 3: Build Your Team
Framework implementation isn't a solo journey. You'll need executive sponsorship, dedicated project management, and involvement from IT, legal, HR, and operations teams. Consider hiring external consultants for specialized expertise.
Step 4: Create a Realistic Timeline
Framework implementation takes time—typically 6-18 months depending on complexity and starting point. Rushing leads to gaps and compliance failures. Build in buffer time for unexpected challenges and stakeholder alignment.
Step 5: Monitor and Maintain
Frameworks aren't "set it and forget it" solutions. They require ongoing monitoring, regular assessments, and continuous improvement. Schedule annual reviews and stay current with framework updates and industry changes.
Common Pitfalls to Avoid
Treating Frameworks as Checklists: Frameworks are living, breathing systems that require ongoing attention and adaptation. Checkbox compliance without understanding the underlying security principles leaves you vulnerable.
Underestimating Resource Requirements: Framework implementation requires significant time, money, and human resources. Underestimating these requirements leads to project delays and incomplete implementations.
Ignoring Company Culture: The best frameworks fail without organizational buy-in. Invest in training, communication, and change management to ensure adoption across all levels of your organization.
Focusing Only on Technical Controls: Modern security frameworks emphasize people and processes as much as technology. Don't neglect the human element of cybersecurity.
Conclusion
In 2025, cybersecurity isn't a cost center, it's a business enabler. The right security framework provides the foundation for sustainable growth, customer trust, and competitive advantage. While implementation requires investment and commitment, the cost of inaction far exceeds the price of protection.
Whether you choose NIST CSF for its flexibility, ISO 27001 for international credibility, or industry-specific frameworks for compliance, the key is starting your security journey today. Your customers, partners, and stakeholders are counting on you to protect their trust and data.
Don't wait for a breach to prioritize security. Choose your framework, create your plan, and begin building the secure foundation your business deserves. The investment you make today in security frameworks will pay dividends in reduced risk, enhanced reputation, and accelerated growth for years to come.
Ready to strengthen your security foundation? Contact our cybersecurity experts today for a complimentary framework assessment and discover which security standard best fits your business needs.