Common PCI DSS Compliance Mistakes to Avoid: A Complete Guide


Introduction
Every year, businesses face devastating data breaches that could have been prevented with proper Payment Card Industry Data Security Standard (PCI DSS) compliance. Yet despite the clear guidelines, organizations continue making the same critical errors that leave them vulnerable to cyberattacks and hefty fines.
Whether you're processing ten transactions or ten million, PCI DSS compliance isn't optional—it's essential for protecting your customers' payment data and your business reputation. The stakes couldn't be higher: non-compliance can result in fines ranging from $5,000 to $100,000 per month, plus the potential for devastating data breaches that cost an average of $4.45 million to resolve.
But here's the good news: most PCI DSS compliance failures are entirely preventable. By understanding the most frequent mistakes organizations make, you can sidestep these traps and build a robust security framework that actually protects your business and customers.
Understanding PCI DSS: The Foundation of Payment Security
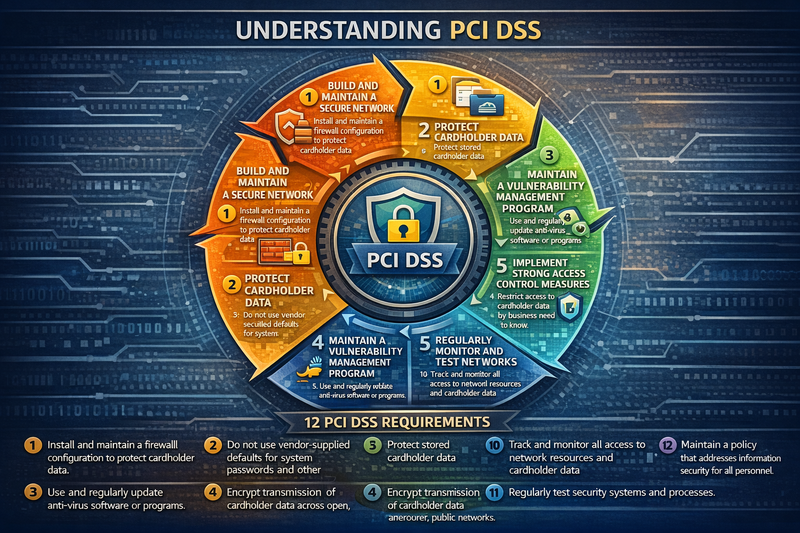
Before diving into common mistakes, let's establish what PCI DSS actually requires. The standard consists of 12 core requirements organized into six main goals:
- Build and maintain secure networks and systems
- Protect cardholder data
- Maintain a vulnerability management program
- Implement strong access control measures
- Regularly monitor and test networks
- Maintain an information security policy
These requirements apply to any organization that processes, stores, or transmits credit card information, regardless of size or transaction volume. The complexity of compliance varies based on your merchant level, but the fundamental security principles remain the same.
The Most Costly PCI DSS Compliance Mistakes
1. Misunderstanding Your Compliance Scope
Perhaps the biggest mistake organizations make is incorrectly defining their PCI DSS scope. This fundamental error cascades into every other aspect of compliance, making it our number one pitfall to avoid.
The Problem: Many businesses either cast too wide a net, unnecessarily complicating their compliance efforts, or worse, they minimize their scope and miss critical systems that handle cardholder data.
Common Scope Mistakes:
- Assuming that using a third-party payment processor eliminates all compliance requirements
- Failing to identify all systems that store, process, or transmit cardholder data
- Overlooking development and testing environments that contain real cardholder data
- Missing network connections that could provide access to cardholder data environments
The Solution: Conduct a thorough data flow analysis with qualified security assessors. Map every point where cardholder data enters, moves through, and exits your environment. Remember that PCI DSS applies to any system component that is part of or connected to the cardholder data environment.
2. Inadequate Network Segmentation
Network segmentation is one of the most effective ways to reduce PCI DSS scope and improve security, yet it's frequently implemented incorrectly or not at all.
The Problem: Without proper network segmentation, your entire network infrastructure may fall within PCI DSS scope. This dramatically increases the complexity and cost of compliance while expanding your attack surface.
Common Segmentation Failures:
- Creating logical separation without proper access controls
- Implementing segmentation that can be bypassed through alternative network paths
- Failing to regularly test segmentation effectiveness
- Using shared credentials or systems that span multiple network segments
The Solution: Implement true network isolation using firewalls, VLANs, or physical separation. Regularly test your segmentation through penetration testing and vulnerability assessments to ensure it cannot be circumvented.
3. Poor Vulnerability Management Practices
PCI DSS Requirement 6 mandates a formal vulnerability management process, but many organizations struggle to implement this effectively.
The Problem: Inconsistent vulnerability scanning, delayed patching, and inadequate risk assessment leave organizations exposed to known threats.
Critical Vulnerability Management Mistakes:
- Running vulnerability scans irregularly or only before audits
- Failing to address high-risk vulnerabilities within required timeframes
- Not scanning all systems within the cardholder data environment
- Ignoring vulnerabilities in third-party applications and services
The Solution: Establish automated vulnerability scanning schedules and create clear remediation timelines based on risk levels. Critical vulnerabilities should be addressed immediately, while high-risk issues must be resolved within 30 days per PCI DSS requirements.
4. Weak Access Control Implementation
Access control failures represent some of the most serious compliance violations and security risks.
The Problem: Excessive user privileges and poor access management create unnecessary risks and compliance violations.
Common Access Control Errors:
- Granting administrative access to users who don't require it
- Using shared accounts or generic login credentials
- Failing to remove access for terminated employees
- Not implementing multi-factor authentication where required
- Inadequate monitoring of privileged user activities
The Solution: Implement the principle of least privilege, ensuring users have only the minimum access necessary for their job functions. Regularly review and audit user access rights, and implement strong authentication measures for all system access.
5. Insufficient Log Monitoring and Analysis
Many organizations collect security logs but fail to actively monitor and analyze them for suspicious activities.
The Problem: Without proper log monitoring, security incidents can go undetected for months, allowing attackers to maintain persistent access to sensitive systems.
Log Management Mistakes:
- Collecting logs but not actively reviewing them
- Failing to synchronize time across all systems
- Not retaining logs for the required duration (minimum one year)
- Inadequate log protection and backup procedures
- Missing critical log events due to incomplete logging configurations
The Solution: Implement automated log monitoring tools that can detect and alert on suspicious activities. Establish clear procedures for log review and incident response, and ensure all logs are properly protected and retained.
6. Neglecting Physical Security Controls
In our digital age, physical security is often overlooked, but PCI DSS includes specific requirements for protecting physical access to sensitive systems.
The Problem: Poor physical security controls can provide attackers with direct access to systems containing cardholder data, bypassing all network security measures.
Physical Security Oversights:
- Inadequate access controls to server rooms and data centers
- Unattended workstations with access to cardholder data
- Lack of visitor monitoring and escort procedures
- Insufficient media destruction processes
- Missing video surveillance or access logging
The Solution: Implement comprehensive physical security measures including access cards, surveillance systems, and visitor management procedures. Regularly audit physical access and ensure all media containing sensitive data is properly destroyed.
7. Inadequate Vendor Management
Third-party vendors can introduce significant compliance risks if not properly managed.
The Problem: Organizations often assume vendors are responsible for their own compliance without understanding shared responsibilities or validating vendor security measures.
Vendor Management Failures:
- Not obtaining vendor compliance certifications
- Failing to include PCI DSS requirements in vendor contracts
- Inadequate assessment of vendor security practices
- Not monitoring ongoing vendor compliance status
- Assuming cloud providers handle all compliance responsibilities
The Solution: Maintain an inventory of all vendors who have access to cardholder data or systems. Require annual compliance attestations and regularly assess vendor security practices through audits or security questionnaires.
The Human Element: Training and Awareness Mistakes
8. Insufficient Security Awareness Training
Even the best technical controls can be undermined by human error, making security awareness training crucial for PCI DSS compliance.
The Problem: Employees who aren't properly trained on security policies and procedures can inadvertently create compliance violations and security vulnerabilities.
Training Deficiencies:
- Providing generic security training that doesn't address PCI DSS requirements
- Conducting training only during employee onboarding
- Failing to customize training for different roles and access levels
- Not testing employee understanding through assessments
- Inadequate documentation of training completion
The Solution: Develop role-specific security awareness training that addresses PCI DSS requirements relevant to each position. Provide regular refresher training and test employee knowledge through practical exercises and assessments.
9. Poor Documentation and Policy Management
PCI DSS requires extensive documentation of security policies, procedures, and controls, but many organizations struggle with this requirement.
The Problem: Incomplete, outdated, or inaccessible documentation can lead to audit failures and operational confusion.
Documentation Mistakes:
- Creating policies that don't reflect actual practices
- Failing to update documentation when systems or processes change
- Not making policies easily accessible to relevant personnel
- Inadequate change management for policy updates
- Missing required documentation for specific PCI DSS requirements
The Solution: Establish a formal documentation management process with regular review cycles. Ensure all policies and procedures accurately reflect current practices and are easily accessible to employees who need them.
Building a Sustainable Compliance Program
10. Treating Compliance as a One-Time Project
One of the most dangerous misconceptions about PCI DSS is viewing it as a one-time implementation rather than an ongoing program.
The Problem: Organizations that focus solely on passing their annual assessment often neglect ongoing maintenance of security controls, leading to compliance gaps throughout the year.
Project-Based Thinking Errors:
- Implementing controls just before audits
- Neglecting security measures between assessments
- Not maintaining compliance evidence throughout the year
- Failing to adapt to changes in business processes or technology
- Inadequate change management processes
The Solution: Develop a continuous compliance program with regular monitoring, testing, and improvement of security controls. Treat PCI DSS as an ongoing business process rather than an annual hurdle.
Practical Steps to Avoid These Mistakes
Start with a Comprehensive Gap Analysis
Before implementing any security controls, conduct a thorough assessment of your current environment against PCI DSS requirements. This analysis should identify all systems, processes, and personnel involved in handling cardholder data.
Implement a Risk-Based Approach
Not all compliance requirements carry the same risk level for your organization. Focus your resources on the areas that pose the greatest risk to cardholder data security while ensuring you meet all mandatory requirements.
Establish Clear Governance and Accountability
Assign specific ownership for each PCI DSS requirement and establish regular reporting mechanisms to track compliance status. Executive leadership should receive regular updates on compliance posture and emerging risks.
Invest in the Right Tools and Resources
While compliance doesn't require specific technologies, the right tools can significantly simplify ongoing maintenance and monitoring. Consider investing in:
- Automated vulnerability scanning solutions
- Log monitoring and analysis tools
- Access management systems
- Configuration management tools
- Compliance management platforms
Plan for Regular Testing and Validation
PCI DSS requires regular testing of security controls through internal audits, penetration testing, and vulnerability assessments. Build these activities into your annual compliance calendar and use the results to continuously improve your security posture.
The Cost of Getting It Wrong vs. Getting It Right
The financial impact of PCI DSS non-compliance can be devastating. Beyond direct fines and penalties, organizations face costs related to:
- Forensic investigations following data breaches
- Legal fees and litigation expenses
- Customer notification and credit monitoring services
- Loss of business due to reputational damage
- Increased payment processing fees
- Regulatory enforcement actions
In contrast, organizations with mature compliance programs often find that their PCI DSS investments pay dividends beyond regulatory requirements. Strong security controls protect against various cyber threats, not just payment card fraud, and can actually reduce overall security costs by preventing costly incidents.
Moving Forward: Your Compliance Action Plan
Avoiding these common PCI DSS compliance mistakes requires commitment, resources, and expertise. Here's how to get started:
Immediate Actions:
- Conduct a comprehensive scope assessment of your cardholder data environment
- Review and update your vulnerability management processes
- Audit current access controls and implement necessary improvements
- Establish or enhance your log monitoring capabilities
Short-term Goals (3-6 months):
- Implement proper network segmentation
- Develop comprehensive security awareness training programs
- Establish vendor management procedures
- Create or update all required documentation
Long-term Objectives (6-12 months):
- Build a continuous compliance monitoring program
- Implement advanced threat detection capabilities
- Establish regular third-party security assessments
- Create a mature incident response program
Conclusion: Turning Compliance into Competitive Advantage
PCI DSS compliance doesn't have to be a burden on your organization. When implemented thoughtfully, these security requirements can actually strengthen your overall cybersecurity posture and provide competitive advantages in the marketplace.
Customers are increasingly concerned about data security, and demonstrating strong payment security practices can differentiate your business from competitors. Organizations that avoid the common mistakes outlined in this guide often find that their compliance programs evolve into comprehensive security frameworks that protect against a wide range of threats.
Remember that PCI DSS compliance is not a destination but a journey. The threat landscape continues to evolve, and your security measures must adapt accordingly. By understanding and avoiding these common mistakes, you're taking the first step toward building a resilient, compliant, and secure payment environment that serves your business and protects your customers for years to come.
The investment in proper PCI DSS compliance pays dividends not just in regulatory adherence, but in customer trust, operational efficiency, and long-term business sustainability.
Don't let a simple oversight turn into a costly breach—reach out to our team today and we'll help you navigate PCI DSS compliance the right way, because your customers' trust is worth getting it right the first time.