CAVP or CMVP? Understanding the Key Differences That Impact Compliance


Introduction
Cyber threats evolve at an alarming pace daily and cryptographic security has become the backbone of data protection. If you're transmitting financial information, storing sensitive healthcare records, or securing government communications, the strength of your cryptographic modules can make or break your security posture. But how do you know if your cryptographic implementations are truly secure?
CAVP and CMVP are two critical validation programs that serve as the gold standard for cryptographic security in the United States and beyond. While these acronyms might sound similar and are often mentioned in the same breath, they represent distinctly different validation processes that work together to ensure comprehensive cryptographic security. Understanding the difference between CAVP and CMVP is essential for organizations seeking to achieve compliance with federal regulations, win government contracts, or simply demonstrate robust security practices to their customers.
This guide will demystify CAVP and CMVP, explain their key differences, and show you why they matter for your organization's compliance journey. If you're a security professional, compliance officer, or business leader, you'll walk away with a clear understanding of how these validation programs protect data and support regulatory requirements.
What is CAVP?
The Cryptographic Algorithm Validation Program (CAVP) is a validation program jointly run by the National Institute of Standards and Technology (NIST) and the Communications Security Establishment (CSE) of Canada. At its core, CAVP validates the correctness of cryptographic algorithm implementations within cryptographic modules.
Think of CAVP as a rigorous testing process that ensures individual cryptographic algorithms like AES (Advanced Encryption Standard), SHA (Secure Hash Algorithm), or RSA are implemented correctly according to their specifications. When a vendor develops software or hardware that includes cryptographic functions, CAVP testing verifies that these specific algorithms work exactly as they should, with no implementation errors that could create security vulnerabilities.
Key Aspects of CAVP
Focus on Algorithms: CAVP concentrates solely on the mathematical correctness of cryptographic algorithms. It doesn't evaluate the entire module or product but rather the specific algorithm implementations within it.
Testing Process: Vendors submit their algorithm implementations to NIST-accredited Cryptographic and Security Testing (CST) laboratories. These labs conduct extensive testing using standardized test vectors provided by NIST to verify that the algorithms produce correct outputs for given inputs.
CAVP Certificates: Upon successful validation, the algorithm implementation receives a CAVP certificate with a unique certificate number. This certificate confirms that the specific algorithm version has been tested and validated.
Prerequisite for CMVP: CAVP validation is actually a prerequisite for CMVP validation. You cannot validate an entire cryptographic module under CMVP without first having the algorithms within it validated through CAVP.
Scope: CAVP covers a wide range of cryptographic algorithms including symmetric encryption algorithms (like AES, Triple-DES), asymmetric algorithms (like RSA, ECDSA), hash functions (like SHA-256, SHA-3), message authentication codes (like HMAC), and key derivation functions.
The CAVP process ensures that when you implement AES-256 encryption, for example, it actually provides the security strength that AES-256 is mathematically designed to deliver. A single implementation error could reduce a theoretically strong algorithm to something far weaker, making CAVP validation a critical foundation for cryptographic security.
What is CMVP?
The Cryptographic Module Validation Program (CMVP) is also jointly operated by NIST and CSE, but it takes a much broader approach than CAVP. CMVP validates entire cryptographic modules; the complete hardware, software, or firmware products that implement cryptographic functions against the Federal Information Processing Standard (FIPS) 140-2 or FIPS 140-3 requirements.
While CAVP ensures individual algorithms work correctly, CMVP evaluates the security of the entire cryptographic boundary. This includes not just the algorithms themselves but also physical security, key management, authentication mechanisms, self-tests, and many other security requirements.
Key Aspects of CMVP
Comprehensive Security Evaluation: CMVP testing examines eleven security requirement areas under FIPS 140-2 (or the updated sections under FIPS 140-3), including cryptographic module specification, module ports and interfaces, roles and services, finite state model, physical security, operational environment, cryptographic key management, electromagnetic interference/electromagnetic compatibility, self-tests, design assurance, and mitigation of other attacks.
Security Levels: CMVP validation assigns one of four security levels (Level 1 through Level 4) to validated modules. Level 1 provides the most basic security requirements, while Level 4 offers the highest level of security suitable for operation in physically unprotected environments. Organizations choose the appropriate level based on their security needs and regulatory requirements.
FIPS 140 Compliance: CMVP is the formal mechanism for achieving FIPS 140 compliance, which is mandatory for federal agencies and their contractors when using cryptographic-based security systems to protect sensitive but unclassified information.
Testing Duration: CMVP validation is significantly more complex and time-consuming than CAVP. The process typically takes 6-12 months or longer, depending on the module's complexity and security level.
Validated Modules List: Successfully validated modules are listed on NIST's public Validated Modules List, which includes details about the module, its security level, tested algorithms, and operational environments.
Real-World Security: Unlike CAVP, which focuses on theoretical correctness, CMVP evaluates practical security implementation. This includes testing physical tamper evidence, role-based authentication, secure key generation and storage, and the module's ability to enter an error state if tampering is detected.
CMVP validation provides assurance that the entire cryptographic module, meets stringent security requirements and can protect sensitive information in real-world conditions.
What is the Difference Between CAVP and CMVP?
Understanding the distinction between CAVP and CMVP is crucial for anyone involved in cryptographic security or compliance. While they're complementary programs, they serve different purposes and validate different aspects of cryptographic security.
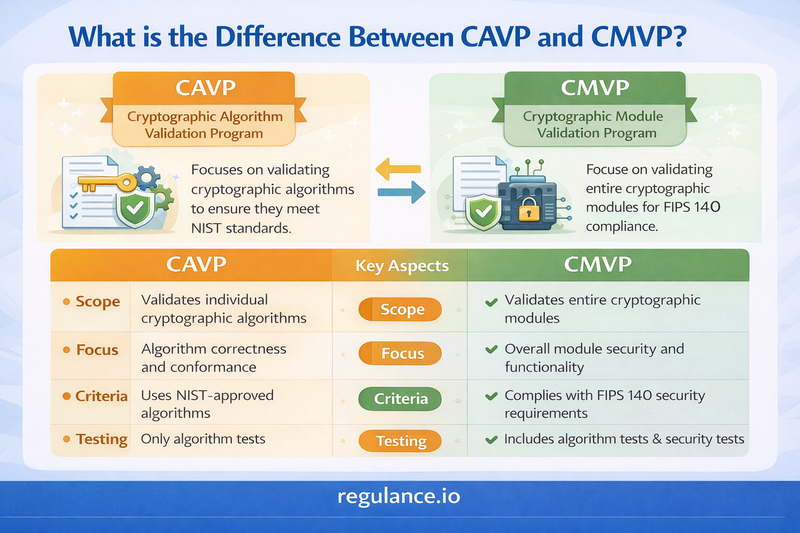
Scope of Validation
CAVP validates individual cryptographic algorithm implementations. It asks: "Does this specific implementation of AES or SHA work correctly?"
CMVP validates entire cryptographic modules. It asks: "Is this complete product secure across all its security requirements?"
CAVP ensures the engine components work correctly, while CMVP ensures the entire vehicle is safe to operate.
Testing Focus
CAVP focuses purely on the mathematical correctness of algorithm implementations. The testing verifies that inputs produce the expected outputs according to algorithm specifications.
CMVP evaluates comprehensive security across multiple dimensions; physical security, key management, authentication, interfaces, documentation, and more. It considers how the module operates in real-world conditions.
Validation Process
CAVP is a relatively streamlined process where algorithm implementations are tested against standard test vectors. Vendors can often complete CAVP validation in weeks to a few months.
CMVP is an extensive process requiring detailed documentation, comprehensive testing, and often physical inspection of modules. The process typically takes 6-12 months or longer.
Certificate Granularity
CAVP issues certificates for individual algorithm implementations. A single product might have dozens of CAVP certificates, one for each algorithm implementation it contains.
CMVP issues a single certificate for the entire cryptographic module, covering all its validated algorithms and security features.
Regulatory Recognition
CAVP certificates demonstrate algorithm correctness but don't typically satisfy federal compliance requirements on their own.
CMVP certificates are specifically required for FIPS 140 compliance, which is mandatory for federal government use and many regulated industries.
Dependency Relationship
CAVP is a prerequisite for CMVP. You cannot achieve CMVP validation without first having CAVP-validated algorithms within your module.
CMVP cannot be achieved without CAVP, but CAVP can exist independently for vendors who want to validate algorithms before pursuing full module validation.
Cost and Resources
CAVP generally requires less investment in time, resources, and costs compared to full module validation.
CMVP requires substantial investment in engineering resources, testing lab fees, and often module redesign to meet all security requirements.
The fundamental difference comes down to this: CAVP proves your cryptographic algorithms are implemented correctly, while CMVP proves your entire cryptographic module is secure and suitable for protecting sensitive information in compliance with federal standards.
Why Do CAVP and CMVP Matter in Compliance?
For organizations operating in regulated industries or seeking to do business with the federal government, understanding how CAVP and CMVP support compliance efforts is essential. These validation programs are foundational requirements for numerous compliance frameworks and regulatory mandates.
Federal Government Requirements
The most direct compliance connection is with federal agencies. Federal Information Processing Standard (FIPS) 140-2 and its successor FIPS 140-3 mandate that federal agencies use only CMVP-validated cryptographic modules when protecting sensitive but unclassified information. This requirement, codified in the Federal Information Security Management Act (FISMA), applies to all federal agencies and extends to contractors and service providers handling federal data.
If you're bidding on government contracts or providing services to federal agencies, CMVP validation is mandatory. Without CMVP-validated cryptographic modules, your solution cannot be deployed in federal environments, immediately disqualifying you from significant market opportunities.
FedRAMP Compliance
The Federal Risk and Authorization Management Program (FedRAMP) requires cloud service providers serving federal agencies to use FIPS 140-validated cryptographic modules. FedRAMP's security controls explicitly reference FIPS 140-2 validation, making CMVP validation a prerequisite for FedRAMP authorization. Given that FedRAMP authorization opens doors to the federal cloud marketplace, CMVP validation becomes a business imperative for cloud service providers.
State and Local Government
While CMVP validation is federally mandated, many state and local government agencies have adopted similar requirements. States increasingly require FIPS 140-validated cryptography for their own systems and often extend these requirements to vendors and contractors. This trend reflects a broader recognition that FIPS 140 represents a proven security standard worth emulating.
Healthcare and HIPAA
In healthcare, the Health Insurance Portability and Accountability Act (HIPAA) requires appropriate safeguards for protecting electronic protected health information (ePHI). While HIPAA doesn't explicitly mandate CMVP validation, the NIST Cybersecurity Framework and security guidelines for healthcare organizations recommend FIPS 140-validated cryptography as a best practice. Healthcare organizations increasingly view CMVP validation as a key component of demonstrating HIPAA compliance.
Financial Services
Financial institutions face multiple regulatory requirements around data security. The Payment Card Industry Data Security Standard (PCI DSS) references strong cryptography, and while it doesn't explicitly require CMVP validation, using FIPS 140-validated modules provides strong evidence of implementing industry-standard cryptography. Similarly, financial regulators increasingly expect banks and financial services firms to implement FIPS 140-validated cryptography when protecting customer data.
Defense and Intelligence
The Department of Defense (DoD) and intelligence community have even stricter requirements. DoD systems must use FIPS 140-validated cryptographic modules, and many DoD programs require Level 3 or Level 4 validation for higher security classifications. The National Security Agency (NSA) Commercial Solutions for Classified (CSfC) program incorporates FIPS 140 validation as a foundational requirement.
International Recognition
CMVP validation also matters for international compliance. Through the Cryptographic Module Validation Program International Arrangement, CMVP validation is recognized by multiple countries including Canada, which operates the program jointly with the United States. For organizations operating internationally, CMVP validation provides credentials recognized across borders.
Procurement Requirements
Beyond direct regulatory requirements, CMVP validation has become a de facto standard in procurement processes. Many organizations, even those without explicit regulatory requirements specify FIPS 140-validated cryptography in their requests for proposals (RFPs). This reflects an industry-wide recognition that CMVP validation represents a credible security standard.
Audit and Assessment
During security audits and assessments, auditors frequently verify that cryptographic modules are CMVP-validated. Having this validation in place streamlines audit processes and demonstrates security due diligence. Conversely, lacking CMVP validation often triggers audit findings and requires remediation plans.
The bottom line is that CAVP and CMVP validation have evolved from technical certifications to essential compliance credentials that open market opportunities, satisfy regulatory requirements, and demonstrate organizational commitment to security best practices.
What Are The Benefits CAVP And CMVP to Cybersecurity?
Beyond compliance requirements, CAVP and CMVP validation deliver substantial cybersecurity benefits that strengthen an organization's security posture and protect against evolving threats.
Assurance of Cryptographic Correctness
The primary security benefit of CAVP validation is the assurance that cryptographic algorithms are implemented correctly. Even small implementation errors can catastrophically weaken cryptography. A single bit flip in an algorithm implementation could reduce a theoretically unbreakable cipher to something vulnerable to trivial attacks. CAVP testing catches these errors before they're deployed in production environments, preventing vulnerabilities that attackers could exploit.
Defense Against Implementation Attacks
Cryptographic algorithms can be mathematically sound but poorly implemented in ways that leak information through side channels. CMVP validation, particularly at higher security levels evaluates resistance to implementation attacks like timing attacks, power analysis, and electromagnetic emanations. These tests ensure that modules don't inadvertently reveal cryptographic keys or sensitive data through observable physical characteristics.
Key Management Security
Weak key management undermines even the strongest cryptography. CMVP validation rigorously evaluates key generation, storage, distribution, and destruction mechanisms. This ensures that cryptographic keys, the most critical security elements are protected throughout their lifecycle. Validated modules implement secure random number generation, prevent key disclosure, and ensure keys are zeroized when no longer needed.
Physical Security Assurance
For hardware cryptographic modules, physical security is paramount. CMVP validation at Level 2 and above requires physical tamper evidence or tamper detection and response. Level 3 adds tamper resistance, while Level 4 demands tamper detection with immediate zeroization of security parameters. These physical security measures protect against sophisticated attackers who gain physical access to devices.
Reduced Attack Surface
CMVP validation requires clear documentation of cryptographic boundaries, interfaces, and roles. This process often reveals unnecessary complexity or overlooked attack vectors. By rigorously defining what enters and leaves the cryptographic boundary and what operations are permitted in which roles, validation helps organizations minimize their attack surface and implement defense-in-depth strategies.
Supply Chain Security
Using CAVP and CMVP-validated modules provides supply chain security benefits. When you deploy validated cryptographic modules, you're using components that have undergone independent third-party testing by accredited laboratories. This reduces the risk of backdoors, undocumented features, or substandard implementations that could compromise security. In an era of sophisticated supply chain attacks, this independent validation provides critical assurance.
Proactive Vulnerability Detection
The validation process often uncovers security vulnerabilities before products reach customers. Labs test modules against security requirements that vendors might have overlooked. Finding and fixing these issues during validation rather than after deployment prevents security incidents and reduces remediation costs.
Operational Security Confidence
Security teams operating CMVP-validated modules can have confidence that these modules will operate securely under specified conditions. The validation documentation clearly states the module's capabilities, limitations, and security parameters. This clarity enables security teams to properly configure and deploy modules, reducing the risk of misconfiguration, a leading cause of security breaches.
Defense Against Quantum Threats
As quantum computing advances threaten current cryptographic algorithms, NIST is developing quantum-resistant algorithms through its post-quantum cryptography (PQC) standardization process. These new algorithms will require CAVP validation, and modules implementing them will need CMVP validation. Organizations using validated modules today are positioned to adopt quantum-resistant cryptography as it becomes available, future-proofing their security infrastructure.
Cryptographic Agility
Validated modules typically support multiple cryptographic algorithms, enabling cryptographic agility, the ability to quickly switch algorithms if vulnerabilities are discovered. This flexibility, combined with the assurance that all supported algorithms are correctly implemented, allows organizations to respond rapidly to emerging threats without compromising security.
Security by Design
Perhaps the most significant benefit is that pursuing CAVP and CMVP validation encourages security by design. Vendors building products for validation must consider security requirements from the beginning, not bolt them on afterward. This results in inherently more secure products with security integrated into their architecture.
Trust and Transparency
Finally, validation provides transparency that builds trust. The public validation certificates detail exactly what has been tested and validated. This transparency allows security professionals to make informed decisions about which modules meet their security requirements, rather than relying solely on vendor claims.
In summary, CAVP and CMVP validation deliver cybersecurity benefits that extend far beyond regulatory compliance. They provide assurance of cryptographic correctness, protect against implementation attacks, strengthen key management, and enable organizations to deploy cryptography with confidence that it will protect their most sensitive information.
FAQs
Q: Do I need both CAVP and CMVP validation?
A: If you're seeking CMVP validation for your cryptographic module, you'll need CAVP validation for the algorithms within it, as CAVP is a prerequisite for CMVP. However, if you're simply implementing cryptographic algorithms in software and want to validate their correctness without pursuing full module validation, CAVP alone may be sufficient. For federal compliance, CMVP validation is required.
Q: How long does the validation process take?
A: CAVP validation typically takes weeks to a few months, depending on the number of algorithms and implementation complexity. CMVP validation is more extensive, usually requiring 6-12 months or longer. Factors affecting duration include module complexity, security level, laboratory workload, and how well the module meets security requirements on the first review.
Q: How much does CAVP and CMVP validation cost?
A: Costs vary significantly based on module complexity, security level, and laboratory fees. CAVP validation might cost tens of thousands of dollars for multiple algorithms. CMVP validation can range from $50,000 to several hundred thousand dollars, especially for Level 3 or Level 4 validation. Additional costs include engineering time for documentation, potential module modifications, and maintenance of validation.
Q: What happens if my validated module needs updates?
A: Minor updates might be handled through the revalidation process, which is faster and less expensive than initial validation. Significant changes may require full revalidation. NIST provides guidance on what constitutes a minor versus significant change. Organizations must maintain validation by revalidating when changes exceed the minor change threshold.
Q: Can software-only modules achieve CMVP validation?
A: Yes, software-only modules can achieve CMVP validation, typically at Level 1. Higher security levels (Level 2 and above) require physical security features that are more easily achieved in hardware or firmware modules, though some software modules have achieved Level 2 validation in restricted operational environments.
Q: Is FIPS 140-3 replacing FIPS 140-2?
A: Yes, FIPS 140-3 is the current standard, though FIPS 140-2 validations are still recognized. CMVP began accepting FIPS 140-3 validation requests in 2020. Organizations with FIPS 140-2 validated modules can continue using them, but new validations follow FIPS 140-3 requirements. The transition period allows organizations time to upgrade.
Q: Do commercial organizations need CMVP validation?
A: CMVP validation isn't legally required for purely commercial organizations, but it's increasingly expected as a security best practice. Organizations selling to federal agencies or regulated industries must have CMVP-validated modules. Even without regulatory requirements, many companies pursue validation to demonstrate security leadership and meet customer security expectations.
Q: Can I use open-source cryptographic libraries instead of validated modules?
A: Some open-source cryptographic libraries have undergone CAVP and CMVP validation (like OpenSSL FIPS modules). However, not all implementations are validated, and even validated open-source modules must be deployed correctly in their validated configuration. For federal compliance, you must use specifically validated builds, not arbitrary versions of open-source libraries.
Q: What's the difference between FIPS 140-2 and FIPS 140-3?
A: FIPS 140-3 is the updated version of the cryptographic module validation standard. Key differences include alignment with international standard ISO/IEC 19790, modified security requirements, new testing requirements, and updated algorithm requirements. FIPS 140-3 also introduces the concept of "Security Level vs Security Strength," recognizing that not all security requirements need to be at the same level.
Q: How do I find validated modules?
A: NIST maintains public searchable databases of CAVP-validated algorithms and CMVP-validated modules on its Computer Security Resource Center (CSRC) website. These databases allow you to search by vendor, algorithm, module name, or validation number to verify validation status and review validation certificates.
Conclusion
In the complex landscape of cybersecurity and compliance, CAVP and CMVP stand as essential pillars supporting cryptographic security. While they serve different purposes, CAVP validating individual algorithm implementations and CMVP validating complete cryptographic modules; they work together to provide comprehensive assurance that cryptography is both correctly implemented and securely deployed.
For organizations navigating federal compliance requirements, CMVP validation is a mandatory gateway to government markets and regulated industries. Even beyond explicit regulatory requirements, these validation programs have become de facto industry standards that demonstrate security commitment and technical excellence.
CAVP and CMVP validation catch implementation errors, protect against sophisticated attacks, strengthen key management, and provide the assurance that cryptographic modules will protect sensitive information under real-world conditions. In an era of escalating cyber threats and increasing regulatory scrutiny, this assurance is invaluable.
Understanding the difference between CAVP and CMVP, their scopes, processes, and roles empowers security professionals, compliance officers, and business leaders to make informed decisions about cryptographic security. Whether you're developing cryptographic modules, procuring security solutions, or building compliance programs, knowing how these validation programs work and why they matter is essential to success.
As cryptographic threats evolve and quantum computing looms on the horizon, CAVP and CMVP will continue adapting to ensure cryptographic security keeps pace with technological change. Organizations that embrace these validation programs today are investing in security foundations that will protect their most valuable assets tomorrow.
Take Control of Your Compliance Journey with Regulance: Contact us today for a consultation. Let us help you navigate CAVP and CMVP validation, accelerate your time to compliance, and build security foundations that protect your organization and unlock new market opportunities.