Automated Vulnerability Management: Transforming Cybersecurity Through Intelligent Automation


Introduction
In today's rapidly evolving digital landscape, organizations face an unprecedented challenge: managing an ever-growing number of security vulnerabilities across increasingly complex IT infrastructures. With cyber threats becoming more sophisticated and frequent, traditional manual approaches to vulnerability management are no longer sufficient. Enter automated vulnerability management – a game-changing approach that leverages artificial intelligence and machine learning to streamline, accelerate, and enhance the entire vulnerability management process.
This comprehensive guide explores how automated vulnerability management is revolutionizing cybersecurity, helping organizations stay ahead of threats while optimizing their security resources and reducing operational overhead.
What is Vulnerability Management?
Vulnerability management is a systematic, continuous process of identifying, evaluating, prioritizing, and addressing security vulnerabilities within an organization's IT infrastructure. This critical cybersecurity discipline encompasses everything from network devices and servers to applications, databases, and cloud services.

Vulnerability management serves as an organization's early warning system against potential cyber attacks. It involves scanning systems for known vulnerabilities, assessing their potential impact, and implementing appropriate remediation strategies. The process requires constant vigilance, as new vulnerabilities are discovered daily, and threat actors continuously develop new attack vectors.
Effective vulnerability management goes beyond simply finding security flaws. It requires understanding the broader context of each vulnerability, including its exploitability, the value of affected assets, and the potential business impact of a successful attack. This comprehensive approach ensures that organizations can make informed decisions about resource allocation and risk mitigation strategies.
The traditional vulnerability management approach typically involves manual processes, periodic scans, and human-driven analysis. While these methods have served organizations well in the past, the sheer volume of vulnerabilities and the speed of modern cyber threats have created significant challenges that demand more sophisticated solutions.
What is Risk-Based Vulnerability Management?
Risk-based vulnerability management represents an evolution in how organizations approach cybersecurity threats. Unlike traditional methods that treat all vulnerabilities equally, this approach prioritizes vulnerabilities based on their actual risk to the organization.
This methodology considers multiple factors when assessing vulnerability risk, including the likelihood of exploitation, the potential impact on business operations, the criticality of affected systems, and the current threat landscape. By incorporating these variables, organizations can focus their limited resources on addressing the most dangerous vulnerabilities first.
Risk-based vulnerability management also takes into account environmental factors such as network segmentation, existing security controls, and asset criticality. A high-severity vulnerability on an isolated system may pose less immediate risk than a medium-severity vulnerability on a critical, internet-facing server.
This approach enables organizations to move beyond CVSS scores alone and develop a more nuanced understanding of their security posture. It helps security teams make strategic decisions about remediation priorities, ensuring that the most critical threats are addressed promptly while less dangerous vulnerabilities are managed according to available resources and timelines.
What is Automated Vulnerability Management?
Automated vulnerability management leverages advanced technologies, including artificial intelligence, machine learning, and orchestration tools, to streamline and enhance the traditional vulnerability management process. This approach automates key aspects of vulnerability identification, assessment, prioritization, and remediation, significantly reducing the manual effort required while improving accuracy and response times.
Unlike traditional vulnerability management, which relies heavily on manual processes and human intervention, automated systems can continuously monitor environments, detect new vulnerabilities in real-time, and provide intelligent recommendations for remediation. These systems can process vast amounts of data quickly, correlating vulnerability information with threat intelligence, asset criticality, and business context.
Automated vulnerability management platforms integrate with existing security tools and infrastructure, creating a unified ecosystem that can respond to threats more efficiently. They can automatically trigger scans, analyze results, generate reports, and even initiate remediation actions based on predefined rules and policies.
The automation extends to communication and workflow management, ensuring that relevant stakeholders are notified of critical vulnerabilities and that remediation efforts are tracked and managed effectively. This comprehensive automation reduces the time between vulnerability discovery and remediation, significantly improving an organization's security posture.
Key Benefits of Automating Vulnerability Management
Enhanced Speed and Efficiency
Automated vulnerability management dramatically accelerates the entire security process. While manual vulnerability scans might be conducted weekly or monthly, automated systems can perform continuous monitoring, identifying new vulnerabilities within hours or even minutes of their disclosure. This rapid detection capability is crucial in today's threat landscape, where attackers often exploit vulnerabilities within days of their public disclosure.
Improved Accuracy and Consistency
Human error is a significant factor in traditional vulnerability management processes. Automated systems eliminate many sources of error, providing consistent, repeatable results. Advanced algorithms can accurately assess vulnerability severity, reduce false positives, and ensure that no critical vulnerabilities are overlooked due to human oversight or fatigue.
Intelligent Prioritization
Modern automated vulnerability management platforms use sophisticated algorithms to prioritize vulnerabilities based on multiple factors, including exploitability, asset criticality, and current threat intelligence. This intelligent prioritization ensures that security teams focus their efforts on the most dangerous vulnerabilities first, maximizing the impact of their remediation efforts.
Resource Optimization
By automating routine tasks such as scanning, analysis, and reporting, organizations can redirect their security personnel toward more strategic activities. This optimization is particularly valuable given the global shortage of cybersecurity professionals, allowing teams to accomplish more with existing resources.
Comprehensive Coverage
Automated systems can maintain continuous visibility across entire IT environments, including cloud services, mobile devices, and IoT systems. This comprehensive coverage ensures that no assets are overlooked and that the organization maintains a complete understanding of its security posture.
Regulatory Compliance
Many compliance frameworks require regular vulnerability assessments and documented remediation efforts. Automated systems can generate detailed reports, maintain audit trails, and ensure that compliance requirements are consistently met without additional manual effort.
4-Step Vulnerability Management Process
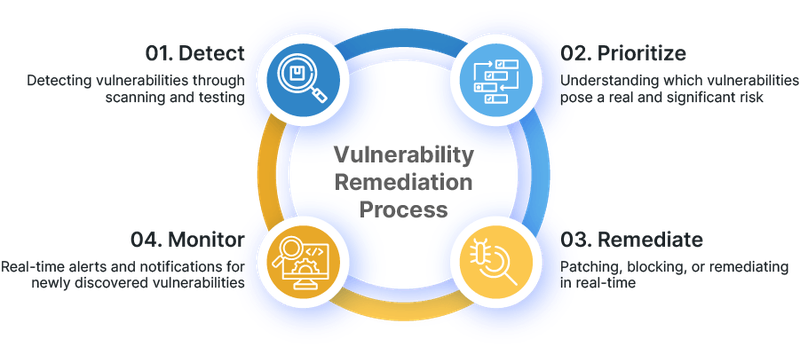
Step 1: Discovery and Asset Inventory
The foundation of effective vulnerability management begins with comprehensive asset discovery and inventory management. Automated systems continuously scan network environments to identify all connected devices, systems, and applications. This process includes mapping network topology, identifying operating systems and software versions, and cataloging all discoverable assets.
Modern automated discovery tools can identify assets across diverse environments, including on-premises infrastructure, cloud services, and hybrid deployments. They maintain real-time inventories that automatically update as new assets are added or existing ones are modified. This dynamic approach ensures that vulnerability assessments cover the entire attack surface.
Asset classification is another critical component of this step. Automated systems can categorize assets based on their function, criticality to business operations, and data sensitivity. This classification becomes crucial for risk assessment and prioritization in subsequent steps.
Step 2: Vulnerability Assessment and Scanning
Once assets are identified and cataloged, automated vulnerability management systems conduct comprehensive security assessments. These assessments involve multiple scanning techniques, including network-based scans, agent-based assessments, and application security testing.
Automated scanners can identify a wide range of vulnerabilities, including missing security patches, misconfigurations, weak passwords, and application-specific flaws. Advanced systems integrate with vulnerability databases and threat intelligence feeds to ensure that scans detect the latest known vulnerabilities.
The scanning process is optimized to minimize disruption to business operations while maintaining comprehensive coverage. Intelligent scheduling algorithms can distribute scan loads across time periods, prioritize critical systems, and adjust scan intensity based on system capacity and business requirements.
Step 3: Risk Assessment and Prioritization
Following vulnerability identification, automated systems perform sophisticated risk analysis to prioritize remediation efforts. This analysis considers multiple factors, including vulnerability severity scores, exploitability metrics, asset criticality, and current threat intelligence.
Advanced prioritization algorithms can correlate vulnerability data with external threat feeds, identifying vulnerabilities that are actively being exploited in the wild. This correlation helps organizations understand which vulnerabilities pose immediate threats versus those that might become problematic in the future.
The risk assessment also considers environmental factors such as network segmentation, existing security controls, and compensating measures. This contextual analysis provides a more accurate picture of actual risk, helping organizations make informed decisions about remediation priorities.
Step 4: Remediation and Verification
The final step involves coordinating remediation efforts and verifying their effectiveness. Automated systems can integrate with patch management tools, configuration management platforms, and other remediation systems to streamline the fix deployment process.
Workflow automation can automatically assign remediation tasks to appropriate teams, track progress, and send notifications about critical vulnerabilities requiring immediate attention. Integration with ticketing systems ensures that remediation efforts are properly documented and managed through completion.
After remediation actions are completed, automated systems conduct verification scans to confirm that vulnerabilities have been successfully addressed. This verification step is crucial for maintaining accurate security posture assessments and ensuring that remediation efforts are effective.
Challenges with Traditional Vulnerability Management
Volume and Complexity Overload
Traditional vulnerability management approaches struggle with the sheer volume of vulnerabilities discovered across modern IT environments. Security teams often find themselves overwhelmed by thousands of vulnerabilities, making it difficult to prioritize effectively and allocate resources appropriately. This volume problem is compounded by the complexity of modern IT infrastructures, which may include diverse technologies, cloud services, and interconnected systems.
Manual Process Inefficiencies
Manual vulnerability management processes are inherently slow and prone to errors. Scanning schedules may be infrequent due to resource constraints, leaving significant gaps in security coverage. Manual analysis of vulnerability data is time-consuming and may miss critical relationships between vulnerabilities or fail to consider important contextual factors.
The manual approach also creates bottlenecks in the remediation process. Coordinating between different teams, tracking remediation progress, and verifying fixes requires significant administrative overhead that delays the resolution of critical security issues.
Limited Contextual Analysis
Traditional approaches often rely on generic vulnerability severity scores without considering the specific context of the organization's environment. A high-severity vulnerability may pose little actual risk if the affected system is properly isolated, while a medium-severity vulnerability on a critical, internet-facing system might represent a significant threat.
Inconsistent Coverage
Manual vulnerability management often results in inconsistent coverage across the IT environment. Some systems may be scanned regularly while others are overlooked or assessed infrequently. This inconsistency creates blind spots that attackers can exploit.
Lack of Integration
Traditional vulnerability management tools often operate in isolation, lacking integration with other security systems, threat intelligence feeds, and business systems. This isolation limits the effectiveness of vulnerability assessments and makes it difficult to maintain a comprehensive view of the organization's security posture.
How to Implement and Optimize Automated Vulnerability Management
Assessment and Planning Phase
Successful implementation begins with a thorough assessment of the organization's current vulnerability management practices, IT infrastructure, and business requirements. This assessment should identify existing tools, processes, and pain points that automated solutions need to address.
Organizations should define clear objectives for their automated vulnerability management program, including coverage goals, response time targets, and integration requirements. These objectives will guide tool selection and implementation strategies.
Tool Selection and Architecture Design
Choosing the right automated vulnerability management platform requires careful consideration of technical requirements, scalability needs, and integration capabilities. Organizations should evaluate platforms based on their ability to discover assets across diverse environments, perform comprehensive vulnerability assessments, and integrate with existing security infrastructure.
The architecture design should consider factors such as network topology, security requirements, and performance constraints. Distributed scanning architectures may be necessary for large or geographically dispersed environments.
Deployment and Configuration
Phased deployment approaches typically yield the best results, allowing organizations to validate functionality and refine configurations before full-scale implementation. Initial deployments should focus on critical systems and gradually expand coverage across the entire environment.
Configuration optimization is crucial for maximizing the effectiveness of automated systems while minimizing false positives and performance impacts. This includes tuning scanning parameters, customizing risk assessment criteria, and configuring integration points with other security tools.
Process Integration and Workflow Automation
Automated vulnerability management systems must integrate seamlessly with existing security operations workflows. This integration includes connecting with incident response processes, change management procedures, and compliance reporting requirements.
Workflow automation should be configured to handle routine tasks such as vulnerability notifications, remediation tracking, and progress reporting. Custom workflows may be necessary to accommodate specific organizational requirements and approval processes.
Continuous Improvement and Optimization
Automated vulnerability management programs require ongoing optimization to maintain effectiveness. Regular reviews of scanning coverage, risk assessment accuracy, and remediation efficiency help identify areas for improvement.
Organizations should establish metrics and key performance indicators to measure program effectiveness, including metrics such as mean time to detection, mean time to remediation, and vulnerability backlog trends.
Why Automate Vulnerability Management with Regulance AI?
Regulance AI represents the next generation of automated vulnerability management, combining advanced artificial intelligence with deep cybersecurity expertise to deliver unprecedented capabilities in vulnerability detection, assessment, and remediation.
Advanced AI-Driven Analysis
Regulance AI leverages sophisticated machine learning algorithms to provide intelligent vulnerability analysis that goes far beyond traditional signature-based detection. The platform continuously learns from global threat intelligence, organizational data, and security events to improve its accuracy and effectiveness over time.
The AI-driven approach enables more accurate risk assessment by considering complex relationships between vulnerabilities, assets, and environmental factors. This intelligent analysis reduces false positives while ensuring that critical vulnerabilities receive appropriate attention.
Comprehensive Integration Capabilities
Regulance AI is designed to integrate seamlessly with existing security infrastructure, including SIEM systems, threat intelligence platforms, and remediation tools. This comprehensive integration creates a unified security ecosystem that can respond to threats more effectively and efficiently.
The platform's API-first architecture enables custom integrations and workflow automation, allowing organizations to tailor the solution to their specific requirements and existing processes.
Scalable Cloud-Native Architecture
Built on modern cloud-native technologies, Regulance AI can scale dynamically to accommodate organizations of any size, from small businesses to large enterprises. The platform's architecture ensures consistent performance and reliability regardless of the size or complexity of the IT environment being managed.
Real-Time Threat Intelligence
Regulance AI incorporates real-time threat intelligence from multiple sources, enabling the platform to identify and prioritize vulnerabilities based on current threat activities. This intelligence-driven approach ensures that organizations can respond quickly to emerging threats and focus their efforts on the most dangerous vulnerabilities.
Automated Remediation Orchestration
The platform includes advanced remediation orchestration capabilities that can automatically coordinate fix deployment across diverse IT environments. This automation significantly reduces the time between vulnerability identification and remediation, improving overall security posture.
Conclusion
Automated vulnerability management represents a fundamental shift in how organizations approach cybersecurity, moving from reactive, manual processes to proactive, intelligent automation. As cyber threats continue to evolve and IT environments become increasingly complex, the need for sophisticated, automated security solutions becomes ever more critical.
The benefits of implementing automated vulnerability management extend far beyond simple efficiency gains. Organizations that embrace automation can achieve better security outcomes with existing resources, maintain comprehensive visibility across their entire attack surface, and respond to threats more quickly and effectively.
The journey toward automated vulnerability management requires careful planning, tool selection, and implementation, but the results justify the investment. Organizations that successfully implement automated vulnerability management programs position themselves to better defend against current threats while building the foundation for future security challenges.
As we look toward the future of cybersecurity, automated vulnerability management will continue to evolve, incorporating new technologies such as artificial intelligence, machine learning, and advanced analytics. Organizations that begin this transformation today will be better positioned to leverage these advancing capabilities and maintain strong security postures in an increasingly dangerous threat landscape.
The choice is clear: organizations can continue to struggle with manual, inefficient vulnerability management processes, or they can embrace automation to transform their security operations. Those who choose automation will find themselves better equipped to protect their assets, maintain compliance, and support business objectives in our interconnected digital world.
Strengthen your defenses today! Unlock the power of automation in Vulnerability Management and safeguard your business with speed and precision.