8 Common Security Frameworks and Standards to Consider - A Complete Guide


Getting the right common security frameworks you need to protect your business can be a challenge. Discover essential standards that will help you safeguard your organization effectively.
Importance of Security Frameworks in Cybersecurity
In today’s digital and AI era, cybersecurity has become a critical concern for organizations worldwide. The increasing frequency and sophistication of cyber threats necessitate the adoption of robust security measures. Security frameworks provide structured guidance to help organizations establish and maintain effective security programs. These frameworks offer a comprehensive approach to managing cybersecurity risks by defining best practices, policies, and procedures.
Implementing a security framework helps organizations to systematically address their security needs. It ensures that all aspects of information security are covered, from risk assessment and management to incident response and recovery. Moreover, security frameworks facilitate compliance with legal and regulatory requirements, which is essential in avoiding penalties and maintaining customer trust.
By adopting a security framework, organizations can also enhance their ability to detect and respond to security incidents. The structured approach ensures that all security measures are aligned with the organization’s objectives and risk tolerance. It also fosters a culture of security awareness and continuous improvement, which is crucial in the ever-evolving landscape of cyber threats. In essence, security frameworks act as a blueprint for developing a resilient cybersecurity strategy.
Overview of the NIST Cybersecurity Framework
The National Institute of Standards and Technology (NIST) Cybersecurity Framework is one of the most common security frameworks and a widely recognized and adopted framework in the cybersecurity domain. It was developed to improve the security and resilience of the critical infrastructure in the United States. However, its applicability extends to organizations of all sizes and sectors. The NIST Cybersecurity Framework provides a set of guidelines, best practices, and standards to help organizations manage and reduce cybersecurity risks.
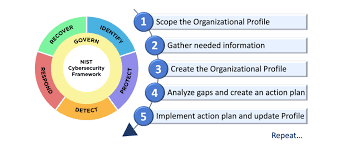
The framework is built around five core functions: Identify, Protect, Detect, Respond, and Recover. These functions represent the key areas that organizations need to address to ensure comprehensive cybersecurity. The Identify function focuses on developing an understanding of the organization’s cybersecurity risks, assets, and vulnerabilities. The Protect function involves implementing safeguards to ensure the delivery of critical services.
The Detect function emphasizes the importance of timely discovery of cybersecurity events. The Respond function outlines the steps to take in the event of a security incident, including communication, analysis, and mitigation. Finally, the Recover function focuses on restoring normal operations and improving security measures based on lessons learned. The NIST Cybersecurity Framework is highly flexible and can be tailored to meet the specific needs of any organization, making it an invaluable tool for enhancing cybersecurity posture.
Understanding ISO/IEC 27001: Information Security Management
ISO/IEC 27001 is an international standard for information security management systems (ISMS). It provides a systematic approach to managing sensitive company information, ensuring its confidentiality, integrity, and availability. The standard is part of the ISO/IEC 27000 family of standards, which focuses on various aspects of information security. ISO/IEC 27001 is designed to help organizations manage their information security risks through a comprehensive set of controls and best practices.
One of the key components of ISO/IEC 27001 is the establishment of an ISMS, which is a framework of policies and procedures for managing information security. The ISMS ensures that security risks are identified, assessed, and mitigated in a structured manner. It also promotes continuous improvement through regular monitoring, review, and updates. The standard requires organizations to systematically examine their information security risks, taking into account the threats, vulnerabilities, and impacts.
ISO/IEC 27001 also emphasizes the importance of leadership and commitment from top management. It requires organizations to define their information security policy, set objectives, and allocate resources for implementing and maintaining the ISMS. By achieving ISO/IEC 27001 certification, organizations demonstrate their commitment to information security and gain a competitive advantage. The certification provides assurance to customers, partners, and regulators that the organization follows internationally recognized best practices for information security management.
The CIS Controls: Best Practices for Cyber Defense
The Center for Internet Security (CIS) Controls are a set of best practices for cyber defense that help organizations protect themselves against the most common cyber threats. The CIS Controls are developed by a global community of cybersecurity experts and are continuously updated to address emerging threats. They are designed to be practical, actionable, and effective, making them an essential resource for organizations seeking to enhance their cybersecurity posture.
The CIS Controls are divided into three categories: Basic, Foundational, and Organizational. The Basic Controls focus on essential cyber hygiene practices that provide a strong foundation for any cybersecurity program. These include inventory and control of hardware and software assets, continuous vulnerability management, and controlled use of administrative privileges. Implementing these basic controls helps organizations address the most common and pervasive cybersecurity threats.
The Foundational Controls build on the basic controls and provide additional layers of security. These include email and web browser protections, malware defenses, secure configuration for hardware and software, and boundary defense. The Organizational Controls focus on the policies, procedures, and processes that support effective cybersecurity management. These include incident response and management, security awareness and training, and application software security.
By implementing the CIS Controls, organizations can significantly reduce their risk of cyber incidents and improve their overall security posture. The controls provide a prioritized, measurable approach to cybersecurity, enabling organizations to focus their resources on the most critical areas.
Exploring PCI DSS: Payment Card Industry Data Security Standard
The Payment Card Industry Data Security Standard (PCI DSS) is a set of security standards designed to protect cardholder data and ensure secure payment processing. It was developed by the Payment Card Industry Security Standards Council (PCI SSC), which is composed of major credit card companies, including Visa, MasterCard, American Express, Discover, and JCB. PCI DSS applies to all entities that store, process, or transmit cardholder data, including merchants, payment processors, and service providers. It is a common security framework that must be deployed by any financial institution that intends to handle and process cards data.
PCI DSS consists of 12 requirements grouped into six control objectives. These requirements cover various aspects of information security, including network security, data protection, access control, monitoring, and testing. For example, Requirement 1 focuses on building and maintaining a secure network, while Requirement 3 addresses the protection of stored cardholder data. Other requirements include implementing strong access control measures, regularly monitoring and testing networks, and maintaining an information security policy.
Compliance with PCI DSS is mandatory for organizations that handle payment card data. Non-compliance can result in fines, penalties, and loss of the ability to process card payments. To achieve compliance, organizations must undergo regular assessments by a Qualified Security Assessor (QSA) or complete a self-assessment questionnaire. They must also conduct regular vulnerability scans and penetration tests to identify and address security weaknesses.
Implementing PCI DSS not only helps organizations protect cardholder data but also enhances their overall security posture. The standard provides a comprehensive framework for managing information security risks and ensures that organizations follow best practices for protecting sensitive data.
The Role of GDPR in Data Protection and Privacy
The General Data Protection Regulation (GDPR) is a landmark data protection law implemented by the European Union (EU) to safeguard the privacy and personal data of EU citizens. GDPR came into effect on May 25, 2018, and it applies to all organizations that process the personal data of individuals residing in the EU, regardless of the organization's location. The regulation aims to give individuals greater control over their personal data and to harmonize data protection laws across EU member states.
GDPR defines personal data as any information that relates to an identified or identifiable natural person. This includes names, email addresses, IP addresses, and even online identifiers. The regulation imposes strict requirements on how organizations collect, process, store, and transfer personal data. Key principles of GDPR include data minimization, accuracy, storage limitation, integrity and confidentiality, and accountability.
One of the most significant aspects of GDPR is the requirement for organizations to obtain explicit consent from individuals before collecting their personal data. Organizations must also provide clear and transparent information about how the data will be used and processed. Additionally, individuals have the right to access their data, request corrections, and demand the deletion of their data under certain circumstances.
Non-compliance with GDPR can result in severe penalties, including fines of up to €20 million or 4% of the organization's annual global turnover, whichever is higher. To comply with GDPR, organizations must implement robust data protection measures, conduct regular data protection impact assessments, and appoint a Data Protection Officer (DPO) if necessary. GDPR has set a new global standard for data protection and privacy, and its influence extends beyond the EU, prompting organizations worldwide to adopt stronger data protection practices.
Overview of SOC 2 Compliance for Service Organizations
SOC 2, or Service Organization Control 2, is a framework developed by the American Institute of CPAs (AICPA) to help service organizations manage and report on their security controls. SOC 2 compliance is particularly important for organizations that provide cloud-based services, data storage, and other IT-related services. The framework focuses on ensuring that service providers maintain a high level of security, availability, processing integrity, confidentiality, and privacy for their clients' data.
SOC 2 compliance is based on the Trust Services Criteria (TSC), which are organized into five categories: Security, Availability, Processing Integrity, Confidentiality, and Privacy. The Security category addresses the protection of systems against unauthorized access and other threats. The Availability category ensures that systems are available for operation and use as committed or agreed upon. The Processing Integrity category focuses on ensuring that system processing is complete, valid, accurate, timely, and authorized.
The Confidentiality category addresses the protection of information designated as confidential, while the Privacy category focuses on the collection, use, retention, and disposal of personal information. To achieve SOC 2 compliance, organizations must undergo a thorough audit conducted by an independent Certified Public Accountant (CPA) or a CPA firm. The audit assesses the design and effectiveness of the organization's controls based on the TSC.
SOC 2 reports come in two types: Type I and Type II. A Type I report evaluates the design of controls at a specific point in time, while a Type II report assesses the operational effectiveness of controls over a defined period. SOC 2 compliance provides assurance to clients that the service organization has implemented robust controls to protect their data, making it a valuable differentiator in the competitive marketplace.
HIPAA (Health Insurance Portability and Accountability Act)
The Health Insurance Portability and Accountability Act (HIPAA) is a U.S. federal law enacted in 1996 to protect the privacy and security of individuals' health information. HIPAA applies to covered entities, including healthcare providers, health plans, and healthcare clearinghouses, as well as their business associates who handle protected health information (PHI). The law sets national standards for the protection of health information and promotes the secure and confidential handling of patient data.
HIPAA consists of several rules, including the Privacy Rule, Security Rule, Breach Notification Rule, and Enforcement Rule. The Privacy Rule establishes standards for the protection of PHI and grants individuals rights over their health information, such as the right to access and request corrections. The Security Rule sets standards for safeguarding electronic protected health information (ePHI) and requires covered entities to implement administrative, physical, and technical safeguards.
The Breach Notification Rule mandates that covered entities notify affected individuals, the Department of Health and Human Services (HHS), and, in some cases, the media in the event of a data breach involving unsecured PHI. The Enforcement Rule outlines the penalties for non-compliance with HIPAA, which can include substantial fines and corrective action plans.
To comply with HIPAA, organizations must conduct regular risk assessments, implement appropriate security measures, and provide training to their workforce on HIPAA requirements. They must also establish policies and procedures for the secure handling of PHI and ensure that their business associates comply with HIPAA standards. HIPAA compliance is crucial for protecting patient privacy, maintaining trust, and avoiding legal and financial repercussions.
The OWASP Top Ten: Web Application Security Risks
The Open Web Application Security Project (OWASP) Top Ten is a widely recognized list of the most critical web application security risks. OWASP is a global nonprofit organization dedicated to improving software security through community-driven projects, tools, and resources. The OWASP Top Ten is updated periodically based on data from security experts and organizations worldwide, and it serves as a valuable resource for developers, security professionals, and organizations seeking to secure their web applications.
The OWASP Top Ten categorizes the most prevalent and severe security risks into ten categories, each representing a specific type of vulnerability or attack. These categories include Injection, Broken Authentication, Sensitive Data Exposure, XML External Entities (XXE), Broken Access Control, Security Misconfiguration, Cross-Site Scripting (XSS), Insecure Deserialization, Using Components with Known Vulnerabilities, and Insufficient Logging and Monitoring.
Injection attacks, such as SQL injection, occur when untrusted data is sent to an interpreter as part of a command or query, allowing attackers to execute malicious commands. Broken Authentication involves weaknesses in authentication mechanisms that can be exploited to gain unauthorized access. Sensitive Data Exposure occurs when sensitive information, such as personal data or financial information, is not adequately protected. XXE vulnerabilities arise when XML processors evaluate external entities within XML documents, leading to potential data breaches or system compromise.
Implementing the OWASP Top Ten recommendations helps organizations identify and mitigate common security risks in their web applications. This includes using secure coding practices, conducting regular security assessments, and employing security testing tools. By addressing these risks, organizations can significantly enhance the security of their web applications and protect against potential attacks.
Conclusion: Choosing the Right Framework for Your Organization
Selecting the appropriate security framework for your organization is a critical decision that requires careful consideration of your specific needs, industry requirements, and risk profile. Each security framework and standard has its strengths and areas of focus, and the right choice will depend on various factors, including the nature of your business, regulatory obligations, and the sensitivity of the data you handle.
For organizations seeking a comprehensive and flexible approach to cybersecurity, the NIST Cybersecurity Framework offers a solid foundation. It is particularly well-suited for organizations that need to address a wide range of cybersecurity risks and want to align their security measures with best practices. On the other hand, ISO/IEC 27001 is ideal for organizations looking for a systematic approach to information security management and seeking to achieve international certification.
The CIS Controls provide a practical and prioritized set of actions that can help organizations of all sizes enhance their cybersecurity posture. They are especially valuable for organizations with limited resources or those looking to implement foundational security measures. For entities handling payment card data, PCI DSS compliance is mandatory and provides a comprehensive framework for protecting cardholder information.
Organizations that process personal data of EU residents must comply with GDPR to avoid severe penalties and ensure the protection of individuals' privacy rights.
Service organizations providing cloud-based or IT-related services should consider SOC 2 compliance to demonstrate their commitment to security and gain a competitive advantage. Healthcare organizations must adhere to HIPAA regulations to protect patient information and maintain compliance with federal law.
Lastly, the OWASP Top Ten provides essential guidance for securing web applications and mitigating common security risks. It is an invaluable resource for developers and security professionals working to protect web applications from potential attacks.
Ultimately, the right security framework for your organization will depend on your specific requirements and objectives. By understanding the key features and benefits of each framework, you can make an informed decision and implement a robust security program that safeguards your organization's assets and data.
Regulance compliance management system helps businesses like yours to manage all these common security frameworks in one place. Regulance helps in policies management, gap analysis, risks management, vendor analysis, cybersecurity scans, auditing, and so much more. Sign up for a free trial here.